Richard Zvinenberg (AMTSO): “Cybercrime has no borders, but we are stuck with national laws ...”

Our today's interview with Richard Zvinenberg (the developer of one of the first antivirus programs in the world), who has been in the IT security world since the late 80s, and began to “play” with computers back in the 70s of the last century.
Luis Corrons (LK): In the beginning, computer viruses were almost like a myth. However, over time, computer attacks have become a reality, and they have evolved significantly with security solutions. How well do we all do? It seems that today there are a lot more attacks than ever before ...
')
Richard Zvinenberg (R.T.): Obviously, there are more attacks than before. At the very beginning, the presence of a computer was a wonder, in addition to this, the base operating system was very diverse. Nowadays, almost everyone has one or more computers or devices. The more devices, the more interesting the attack vectors (cyber criminals have more chances for success). Since now more people use computers, then more people automatically use it for some malicious purposes. It's unavoidable. As in the business, where there are opportunities, there are entrepreneurs, and in cyber crime: if you can take advantage of some vulnerabilities, then someone will do it.
The growth and development of the operating system is followed by security solutions. In fact, not only security solutions, but also the general ideas of people about security. Perhaps banking trojans and cryptographers have become useful in raising people's awareness.

LK: You developed your first antivirus in 1988. Then the number of viruses that were required to detect, was negligible, despite the fact that even then they used some really complex techniques. Given the development of computer threats, does anyone have the opportunity today to develop an effective security solution yourself?
R.TS .: Why not? All you need is a good (new) idea and its implementation. This may be the holy grail of heuristics and proactive blocking of an entirely new type of threat, or even several threats. Modern anti-malware products also started from the same in the late 80s. Of course, nowadays, a solution that will fight with one thing is no longer enough, as consumers expect to get a multi-level solution with full protection functions, and a huge number of new malicious programs appearing daily make it impossible to develop it only on our own. Therefore, it seems more reasonable if you sell your technology to a larger company, or become a niche player in the “second opinion” market. But ... there is nothing wrong!
LK: You worked on projects that collaborated with government agencies, institutions and companies. In your opinion, who should be more interested in improving their knowledge of IT security? Government? Companies? Public organizations?
R.TS .: Unfortunately, all of the above. Education and Awareness are key points here. New threats appear constantly, and you need to know about them in order to protect yourself. Or at least be able to check if your security solution maker is protecting you from them.
Governments are trying to make all people use digital systems, while ensuring their confidentiality, but what can they do? They say they are doing this, but then, even at such major public events as the election of the President of the United States in 2016, where all security measures must be taken, security flaws surfaced.
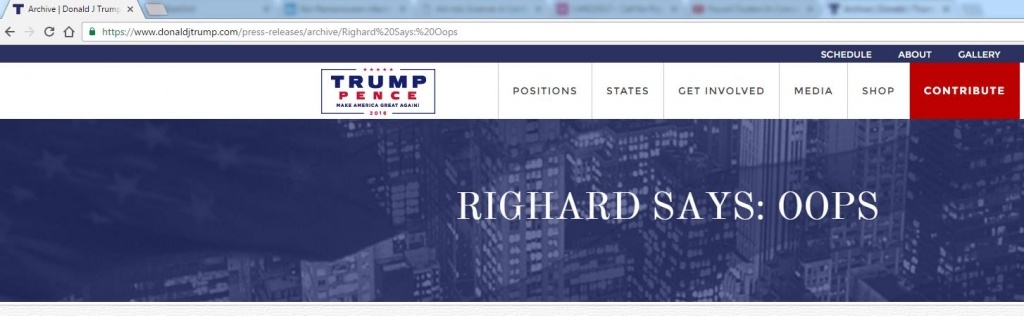 In the example above, the official site of the now elected Donald Trump allowed the use of an arbitrary URL to display the headline above the news archive. This can be used for a funny joke, but most likely it can be used in cases where such an arbitrary URL is supplemented, for example, with a script.
In the example above, the official site of the now elected Donald Trump allowed the use of an arbitrary URL to display the headline above the news archive. This can be used for a funny joke, but most likely it can be used in cases where such an arbitrary URL is supplemented, for example, with a script.LK: You have collaborated with law enforcement agencies to investigate numerous cases of cybercrime. In your opinion, are law enforcement agencies ready to fight cybercrime? Do they have enough resources?
R.TS .: They are well prepared and in most cases have enough resources to combat cybercrime. You will be surprised at what they really know and can do. But what is usually a problem is international law. Cybercrime has no boundaries, but we are stuck with national laws that do not contribute to combating it. In addition, cybercrime is digital, and it is swift. Too many laws impede immediate action. Politicians must catch up with more adequate laws to “keep up with the times” and not spend years developing the required measures against modern threats. All this should allow law enforcement agencies to fully act against cybercrime in accordance with the law, and not end up with a situation where the case collapses in court due to outdated legislation.
LK: Have we achieved a proper level of interaction between law enforcement agencies and security solutions experts / manufacturers, or do you think there is something else to improve?
R.TS .: There is always room for improvement. But law enforcement agencies and private business are already working together (although, as already mentioned, local laws do not contribute much to this). By the way, at the initiative of law enforcement agencies some new areas of cooperation are being prepared for launch. This clearly shows that working together it will be much easier to achieve a common goal: “drive into a corner” of cybercriminals and destroy shelters for them.
LK: Encryption attacks can have disastrous consequences for home users, employees of enterprises and companies themselves. The cost of recovering from such security incidents can be quite high for businesses. However, what do you think about the costs that companies must face in preventing such attacks?
R.TS .: They should be considered as a preventive measure, something like insurance. You spend money on a lock for your door, although the door can be closed anyway, right? And when you compare the cost of preventive measures with the amount of damage from cryptographers (idle time, lost time, checking and cleaning the entire network, because you don’t know, perhaps there are some open source executable files left or backdoor installed etc., negative PR, etc.), then you will see that it is not so expensive. Awareness (and, therefore, correct education) is a key point for all people to understand that early warning of suspicious activity can save a lot of money for a company. In this case, the damage from the notification of suspicious activity, which actually does not exist, is leveled by the amount of money saved thanks to the notification of suspicious activity, which actually turned out to be a real threat.
LK: Richard, you have been working with the AMTSO ( Anti-Malware Testing Standards Organization ) since its inception. During this time, you had the opportunity to work in various positions within the organization: the CEO, CTO, and now you are a member of the Board. What impact does AMTSO have on security testing testing? How did this affect?
R.TS .: In my perception, AMTSO had a serious impact on the scope of testing security solutions in the world. Yes, of course, at first it was a struggle, mistakes were made, but now, after the elimination of organizational shortcomings, AMTSO has drawn up Principles and Recommendations adapted for testers and manufacturers, which allows us to ensure that testing is done fairly and adequately. It is also striking that other organizations now recommend AMTSO and “compatible” with AMTSO tests or product certification by a tester in accordance with AMTSO Principles and Recommendations.
LK: What challenges will AMTSO face in the near future?
R.TS .: AMTSO is growing, and it turns the Principles and Recommendations into real standard documents. This is a delicate procedure, but when it is completed and correctly executed, a big step will be made. AMTSO attracts more and more participants from different industries, and there are companies from the same industries, but their motivations and ways of thinking are different from those that were established in the industry before, there are old and young companies - all together they continue to expand AMTSO and together go to achieve the goals set before AMTSO. That will be the challenge. But I am confident that the new leadership will be able to cope with it.
Article author: Louis Corrons (PandaLabs anti-virus laboratory)
Source: https://habr.com/ru/post/316952/
All Articles