Domain-Driven Design: tactical design. Part 2

Hello, dear users! In a previous article, we looked at strategic modeling using the DDD approach. It showed how to highlight conceptual boundaries within which individual tasks of the subject domain are solved —
To implement a specific
- , ')
It is important to understand that with proper design, a
Traditionally, starting with the book of E. Evans, the DDD pattern is first considered - the
Entity
If a notion of a domain is unique and different from all other objects in the system, then an
- can differ greatly in their form over the entire life cycle, however, they can always be uniquely identified and found upon request. For this purpose, unique identifiers are used, the creation of which must be considered first of all when designing an There are several strategies for creating identifiers:
User input of a unique value
This approach should be used if the identifiers in the application should be readable. However, it is necessary to ensure that the identifier is checked for correctness and uniqueness in the application itself. Often, the cost of identifier changes is high, and users do not have to change them. Therefore, you need to use methods that will guarantee the quality of this identifier.
ID generated by the application
There are fast and highly reliable generators that can be used in applications to automatically create a unique identifier. For example, in the Java environment, there is a
java.util.UUID class that allows you to generate a so-called universally unique identifier in four different ways (time-based, DCE security, name-based, randomly generated UUIDs).An example of such a UUID is:
046b6c7f-0b8a-43b9-b35d-6489e6daee91 . That is 36 byte string.Such large identifiers are not profitable to store due to memory overload. Depending on the level of confidence in the uniqueness of individual segments of the hexadecimal text of the UUID identifier, one or more segments of the whole identifier can be used. The shortened identifier is better protected if it is used as a local identifier of the
For example, consider the following identifier:
APM-P-08-14-2016-046B6C7F .Here:
PM is a separate design management context; P - project; 08-14-2016 - the date of creation; 046B6C7F- is the first segment of the UUID. When such identifiers come across in various ID is generated by persistent storage.
To create an identifier you can refer to the database. This way you can be sure that the unique value will definitely return. However, it will be quite short and it can also be used for a composite identifier.
The disadvantage of this approach is performance. Accessing a database for each value can take much longer than generating identifiers in an application.
Identifiers that are assigned to other restricted contexts.
It is possible that in order to obtain an identifier it is necessary to integrate various
To find a specific identifier in another
For an entity, usually, besides the main identifier of the subject area, a surrogate identifier is used. The first submits to the requirements of the subject area, and the second is already intended for the ORM tool itself (as Hibernate). To create a surrogate key, an
long or int is usually created, a unique identifier is created in the database, and it is used as the primary key. Then the display of this key in the attribute is enabled using ORM tools. Such a surrogate identifier is usually hidden from the outside world, since it is not part of the domain model.It is also important to say that in order to preserve uniqueness throughout the existence of an object, its identifier must be protected from modification. This is done mainly by hiding identifier setters, or by creating state change checks in setter methods to prevent such changes. For example, consider the same PFM system as in the previous article.
First you need to select
PFM-A-424214343245-046b6c7f , where:PFM- context nameA- Account424214343245- account number accountnumber046b6c7f- part of the UUID

The identifier can be specified as
- . It is necessary to examine in detail this very important DDD pattern.Object Value (Value Object)
If individuality is not important for an object, if it is completely defined by its attributes, it should be considered an
- . To find out if a concept is a - It measures, evaluates, or describes a subject area object;
- It can be considered immutable;
- It models something conceptually holistic by combining related attributes into one;
- If you change the method of measurement or description, you can completely replace it;
- It can be compared with other objects using the equality relation;
- It provides related objects with a
.
It must be said that such objects should be encountered much more often than it seems at first glance. They are easier to create, test, and maintain, so you should try to use
- instead of Very rarely
- are made mutable. To deny access to fields, the setters methods are usually made private, and the object's constructor is made public, into which all objects that are attribute - must be an atomic operation.For a
- it is very important to define an equality check operation. In order for two - be equal, it is necessary that all types and values of attributes be equal.It is also very important to say that all methods
- must be Consider the classic example of an object of value money (in many examples on the Internet this class is found):
public class Money implements Serializable { private BigDecimal amount; private String currency; public Money (BigDecimal anAmount, String aCurrency) { this.setAmount(anAmount); this.setCurrency(aCurrency); } … } The setters methods here are made hidden, creating a value object is an atomic operation. An example of a specific value is
{50 000 } . Individually, these attributes either describe something else or do not mean anything concrete. This is particularly the case for 50,000 and to some extent for dollars. That is, these attributes form a conceptually Let's move on to the next important tactical simulation pattern.
Domain Service (Domain Service)
Using a
- . If there is such an operation in the domain, it is declared as - The operation performed by the service refers to the concept of the domain, which does not belong to any of the existing
; - The operation is performed on various objects of the domain model;
- The operation has no status.
No need to abuse the use of
For example, you can take the money transfer

Event (Domain Event)
Studying the subject area, there are facts that are of particular importance to experts in the subject area. For example, from experts you can hear the following key phrases:
- "When ..."
- "If this happens ..."
- “Tell me if ...” or “Notify me if ...”
- "When… "
That is, if something should happen as a result of another separate action, it is likely that modeling of a specific
When modeling it is necessary to take into account that the
- , their functions are For example, consider the event FundsDeposited:
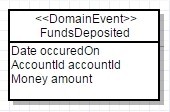
occuredOn is the
In this case, an event is modeled that occurs when funds are credited to a particular account. As a result, you can send an SMS about enrollment, send mail or perform another operation.
In order for
- .If an event is processed within the same
Thus, it is enough to create a
DomainEventPublisher object that will store, register all subscribers and publish the It is important to emphasize that
There are many message passing components that belong to the middleware class (for example, RabbitMQ, NServiceBus). You can also do messaging using REST resources, where autonomous systems access the publishing system, requiring notification of events that have not yet been processed.
The RESTful approach to publishing
It is important to understand that it is necessary to achieve consistency between what the messaging infrastructure publishes and between the current state in the domain model. It is necessary to guarantee the delivery of the
There are various ways to achieve such consistency. The most commonly used method is to use
In both cases — when subscribers use middleware for messaging, or when notification clients use REST — it is important that tracking of the identity of the processed messages is recorded along with any changes in the local state of the domain model.
Let's look at the following DDD pattern.
Module
It is necessary to design loosely coupled
There are certain rules for naming modules. Module names (in many programming languages) display their hierarchical form of organization. The name hierarchy usually begins with the domain name of the organization that develops the module (to avoid conflicts). For example:
com.bankingsystems The next segment of the module name identifies the
com.bankingsystes.pfm The following is the qualifier that identifies the module of the subject area:
com.bankingsystems.pfm.domain All
com.bankingsystems.pfm.domain.account <<Entity>>BankingAccount <<ValueObject>>AccountId In a well-known
om.bankingsystems.resourcesom.bankingsystems.resources.view - om.bankingsystems.applicationom.bankingsystems.application.account - Aggregate
Everyone
All calls
An invariant is a business rule that always maintains its consistency. This phenomenon is called transactional consistency, which is atomic. There is also a final consistency. In the case of invariants, we are talking about transactional consistency.
- , Everyone
Within one transaction
Links are best done by global identifiers
If the client's request affects several
:

.
ustomerId . ustomer – , , , –
Inquiry- a specific request for a credit report from other organizations. When deleting a
Factory (Factory)
- ) . .- (Repository)
, . - .
- ;
- .
HashMap<ObjectId,Object> . . , , ., . :
- (implicity copy-on-read) ( );
- ( -).
, Hibernate,
, - .
save() . For example:
save() put() . .Conclusion
DDD.
- . , DDD! , . . .
: greebn9k ( ), wa1one ( ), silmarilion ( ).
Source: https://habr.com/ru/post/316890/
All Articles