Monopoly on DDoS: Two hackers have created a botnet of 1 million devices based on Mirai

Last month, attacks were launched on large sites like Twitter or Spotify, which temporarily disabled them. For this, the Mirai botnet was used, uniting 400-500 thousand Internet of Things devices. Now Motherboard reporters became aware of the fact that two hackers managed to seize control of the botnet and create a new version of it - it already brings together a million devices. The subscribers of the German provider Deutsche Telekom, whose network did not work last weekend, had time to test its power.
The Mirai Hunt
The journalists managed to talk to one of these two mysterious hackers - he uses the nickname BestBuy. In an encrypted online chat, he told them that there was a real battle for control of Mirai among the crackers. A vulnerability has recently been discovered in his software. Its use, coupled with speed, could allow BestBuy and its partner, Popopret, to take control of most of the botnet and add new devices to it.
')
Earlier, Positive Technologies experts studied the Mirai botnet code - it turned out that it was not created specifically for Internet of Things devices. The malicious software is looking for devices connected to the network with default login passwords (admin: admin, root: password, etc.). This means that theoretically, it can include any device, including home computers and servers or routers.
IoT devices — usually routers — are part of the Mirai botnet before they reboot — then the worm is erased from their memory. However, the botnet constantly scans the Internet for vulnerable devices, so that a “cured” device can quickly become part of it again. Among the hackers, the real race unfolded to be the first to infect as many devices as possible.
Information about how the creators of the new Mirai have time to overtake competitors there. However, they told reporters that they use their own botnet to scan potentially vulnerable devices, including those that were also part of the botnet before.
“Why not force Mirai to hunt Mirai and devour the original,” says BestBuy.
Not only Mirai
However, the new botnet not only swallowed old devices from Mirai and new ones with default passwords. Its creators also use 0-day vulnerabilities in firmware IoT devices. Experts at Positive Technologies previously predicted the imminent emergence of such "combined" botnets.
The fight against them becomes much more complicated - if to confront Mirai with the end-user, all that is needed is to change the username and password to access it, then the gadget’s vulnerabilities will not be able to cope on their own.
700 Gbps DDoS
Hackers BestBuy and Popopret have begun to advertise their services - they offer access to their new version of Mirai, sending spam messages via XMPP / Jabber,
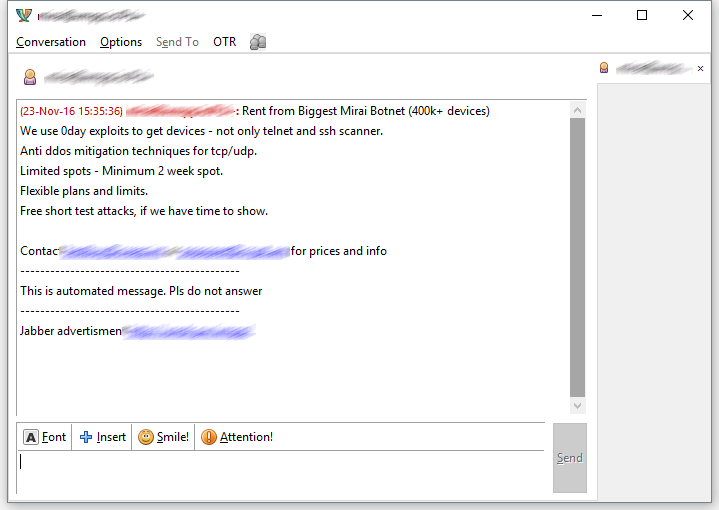
According to the hacker, they offer the customer several packages of services. A cheaper one costs $ 2,000 - for this money, customers can rent from 20,000 to 25,000 botnet nodes to launch one-hour DDoS attacks in a period of up to two weeks with a break of fifteen minutes between attacks. For $ 15,000 or $ 20,000, customers can already rent 600,000 bots to launch two-hour attacks with 30 or 15-minute interruptions. In the second case, the attack power will be 700 Gbit / s or more.
Perspectives
Security of IoT devices is often at a rather low level - this is because vendors are often not interested in introducing additional information security measures. They advertise the ease of use of their products, and all additional measures of information security impose restrictions and require resources.
As stated above, only end-device developers or providers providing them (in the case of routers) can protect users from more advanced botnets. German provider Deutsche Telekom, who suffered from the attack of Mirai, has already announced that it will “reconsider business relations” with suppliers of vulnerable Speedport routers, Arcadyan.
Improving the security of the Internet of things will ultimately be possible through the introduction of tighter control devices by providers on the one hand, and the development of standards and regulatory documentation for IoT on the other. Similar measures have already been taken in many countries regarding the safety of the process control system. The first steps in this direction have already been taken - for example, several IT vendors in September published a document called The Industrial Internet Security Framework (IISF) - it proposes to consider the Internet of things as part of the “industrial Internet”.
However, until the final resolution of the issue is still far away, BestBuy and Popopret hackers can get a monopoly on conducting major DDoS attacks on the network. This is a rather sad fact, but the hackers themselves during the conversation with the Motherboard stated that they would be guided in their activities not only by profit, but also by moral principles. So BestBuy said that they would not allow customers to attack the IP addresses of companies operating with critical infrastructure.
“Business is business, but there is a limit to everything. Some things on the Internet don't need to be attacked. ”
PS We remind you that very soon, with the support of Positive Technologies, Moscow will take a course on asyncio + aiohttp from Core developer Python Andrei Svetlov.
We want to offer one free ticket to the seminar to the author of the best question for Andrei - the question he chooses himself and will answer it during the course. Send your questions to: asyncio2016@ptsecurity.com .
Source: https://habr.com/ru/post/316648/
All Articles