Windows 10 Update System Discovers a Simple but Potentially Dangerous Excess of Authorization Vulnerability
Information security specialist Sami Laiho recently published a blog entry in his win-fu blog that tells about a simple but potentially dangerous vulnerability in the Windows 10 update system “Feature Update” used for major OS updates.
The vulnerability is relevant for assemblies of Windows 10 RTM -> 1511 or 1607, as well as in later insider assemblies until October. In further patches, the vulnerability was closed. Layho positions himself as White Hat, so he was waiting for a fix before publishing information, but the vulnerability may be relevant on systems that are not automatically updated.
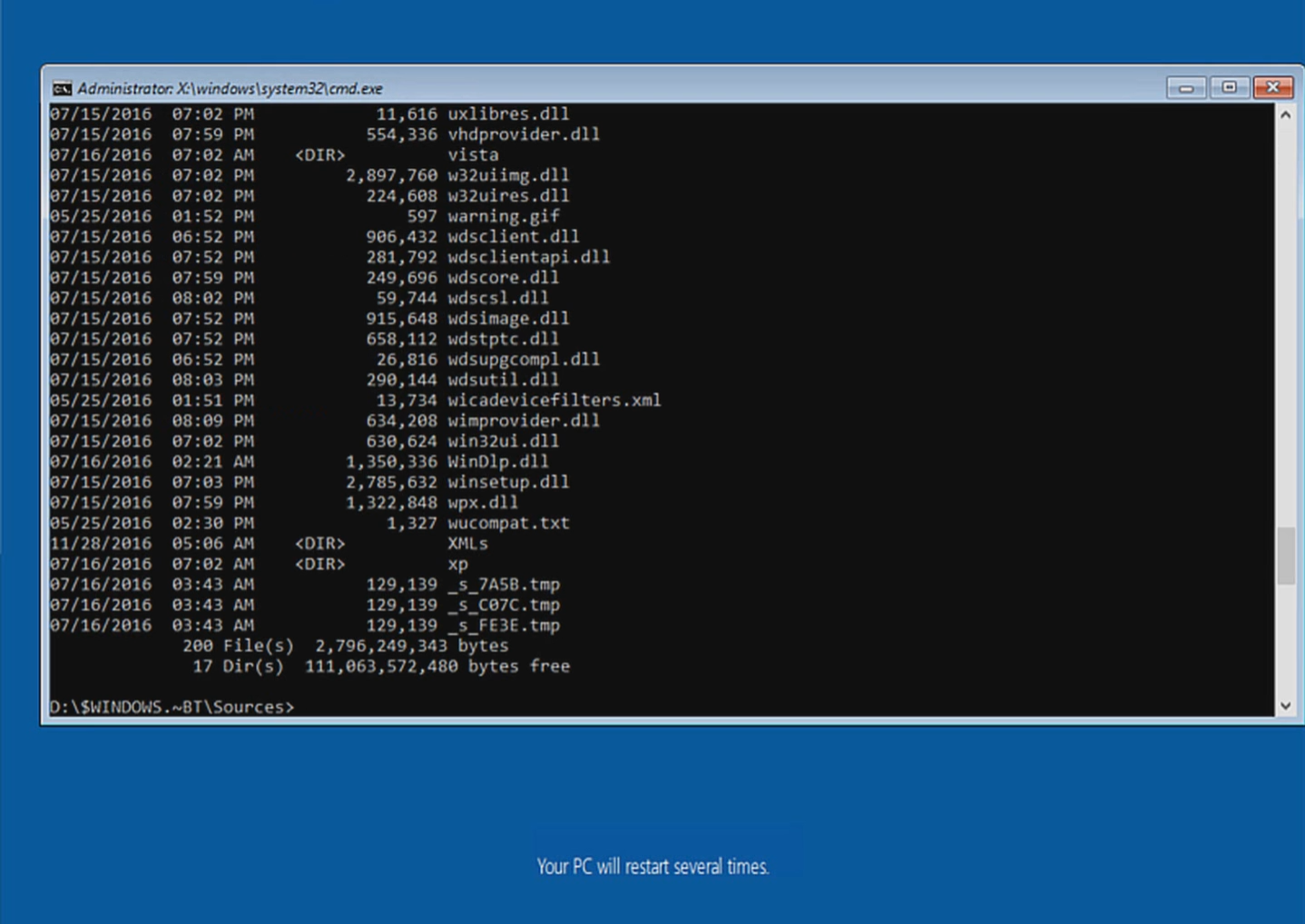
The essence of the vulnerability lies in gaining superuser-level access through the Windows PE update installation environment. There is a debugging mode in it, which can be called up using the Shift + F10 key combination, which brings up the command line.
')
Through it, the user can access the hard disk during the system update, since BitLocker is currently disabled.
The whole danger of this vulnerability lies not only in the non-working BitLocker, but also in the maximum level of rights and access that the user gets. Called via Shift + F10, the console accepts any requests, regardless of the status of the user in the system.
Layho himself designates two potential threat vectors: internal and external. In both cases, the attacker can wait for the moment of updating (automatic or scheduled) the outdated version of the system and get full access to the hard disk and the files on it.
Source: https://habr.com/ru/post/316576/
All Articles