Five aspects of information security that will change with the development of fifth-generation mobile networks
Consisting of various industry organizations, Gemalto is actively involved in shaping the fifth-generation mobile communication standards (5G), discussing these issues with other GSMA and NGMN participants. As we approach the commercial launch of 5G networks, which is supposed to happen in the next few years (by 2020 in Russia), we are seeing many interesting discussions, we are witnessing new trends and new circumstances that need to be taken into account. Fifth generation networks will simultaneously look like any previous generation of mobile networks, and at the same time they will differ significantly from them - and there are a number of explanations that become more obvious if you think about how these changes affect the principles of user and equipment safety in the ecosystem of networks of the fifth generation.

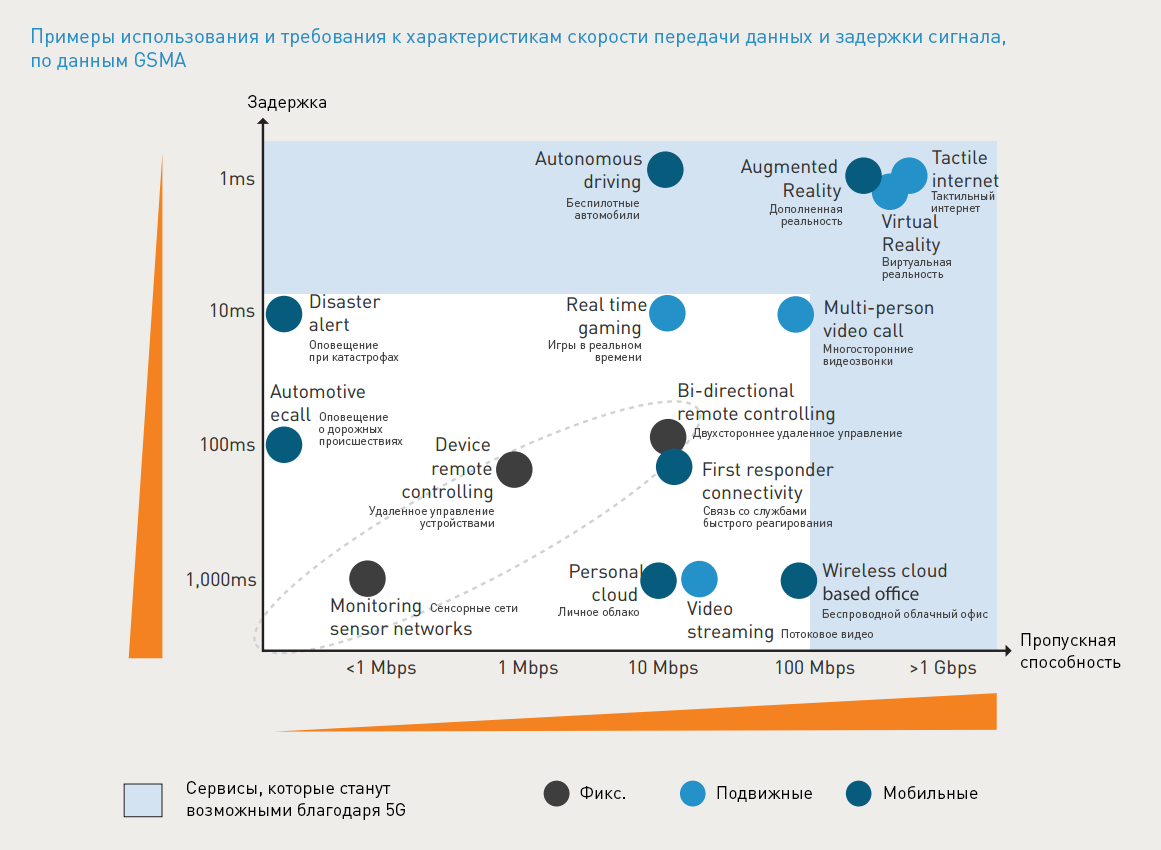
5G is built around the following 8 requirements:
Unlike existing solutions that have to sacrifice performance when using current wireless technologies (3G, 4G, WiFi, Bluetooth, Zigbee, etc.), 5G networks are created for real mass adoption of the “Internet of things” and other speed-sensitive networks and availability of services.
')
We decided to look at 5 security highlights for which mobile network operators should review their approach in the coming months and years, in anticipation of the commercial launch of 5G mobile networks.
We are gradually moving away from the model when mobile network operators immediately received a set of hardware and software from trusted vendors, and we find ourselves in a new world of virtualized infrastructure that uses a whole “zoo” of software built on the basis of open source codes and base of closed technologies. And this means that the potential “attack surface” in the new generation of mobile networks will have much more similarity to that in a classic enterprise, since standard virtualized technologies are more accessible and better known to attackers than proprietary network technologies that are typical of current cellular networks.
Fifth-generation networks provide a much greater degree of freedom in the use of "peripheral" resources, which make it possible to remove some of the load from the network "core" - and this is really important given the fact that more and more applications appear in cellular networks, suggesting a minimum network delay starting from high-resolution games and ending with such critical applications as unmanned vehicles, where human lives are at stake. For example, 5G networks allow content to be cached locally - and if you want to watch a movie on demand, the application can take the stream from the local cache and not transfer it to the core of the network directly from the content provider's servers ... which in turn requires changing security approaches data and cellular communications.
Currently, the main task in ensuring security in cellular communications is to protect against eavesdropping. However, in the future world of smartphones and the Internet of things, in environments with a large number of mechanisms, the probability of listening is likely to fade into the background. Instead, we will have to think about such things as data manipulation attacks, which, for example, can be used to command the mechanisms to perform certain actions (for example, open the door or take control of an unmanned vehicle). Mobile network operators, like consumer electronics manufacturers, will be able to offer “security as a service”, with the result that application providers will be able to apply additional levels of security over existing protected channels of the cellular network when transferring certain types of data.
Today, the responsibility of encrypting and protecting data lies with the application provider. In 5G networks, a certain role in this process will also be assigned to network operators - especially with the advent of IoT devices that do not have enough computing power to sufficiently encrypt communications. Security providers as a service can offer three different security options in addition to what the network provides by default:
All this will allow application developers not to be limited to smartphone platforms alone, and if necessary they will be able to implement an additional level of security.
The expected growth in the number of devices that will be connected to the network in the next decade is amazing. Under these conditions, ensuring the confidentiality and integrity of data transferred between devices is of great importance, since such environments allow new types of vulnerabilities. Recently we have seen successful attacks with data manipulation, as a result of which, under laboratory conditions, the Keen Security Lab researchers managed to intercept the control of a Tesla unmanned vehicle. We should think about how to protect such data from such attacks in all fragments of the chain, both in the cellular network and beyond. Even with secure communication channels, you may need to encrypt the data transmitted over the public IP network when this data leaves the mobile network and leaves the operator's gateway.
Before we see the commercial launch of the first networks of the fifth generation, we still have a lot to determine in the field of 5G technology, and there will be a lot of discussion of security issues. From now on, instead of large-scale and expensive upgrades at the core level of the network to get 6G networks and newer technologies, we will probably deal with a software-defined environment in which very different rules apply. Operators have a lot to rethink, and we look forward to the opportunity to interact with them in order to identify and identify those new threats - as well as new opportunities - that fifth generation networks can offer us.

5G is built around the following 8 requirements:
- Data transfer speeds of up to 10 Gb / s, which exceeds the speeds of 4G and 4.5G networks by 10-100 times
- Delays at 1 millisecond
- 1000 times more bandwidth per unit area
- Up to 100 times more connected devices per unit area (compared to 4G LTE)
- Service availability 99.999%
- Coverage 100%
- Reduce power consumption of network devices by 90%
- Up to 10 years of battery life for low-power IoT devices
Unlike existing solutions that have to sacrifice performance when using current wireless technologies (3G, 4G, WiFi, Bluetooth, Zigbee, etc.), 5G networks are created for real mass adoption of the “Internet of things” and other speed-sensitive networks and availability of services.

')
We decided to look at 5 security highlights for which mobile network operators should review their approach in the coming months and years, in anticipation of the commercial launch of 5G mobile networks.
1. 5G networks have a greater attack surface than current cellular networks.
We are gradually moving away from the model when mobile network operators immediately received a set of hardware and software from trusted vendors, and we find ourselves in a new world of virtualized infrastructure that uses a whole “zoo” of software built on the basis of open source codes and base of closed technologies. And this means that the potential “attack surface” in the new generation of mobile networks will have much more similarity to that in a classic enterprise, since standard virtualized technologies are more accessible and better known to attackers than proprietary network technologies that are typical of current cellular networks.
2. The development of mobile peripherals leads to changes in the security perimeter.
Fifth-generation networks provide a much greater degree of freedom in the use of "peripheral" resources, which make it possible to remove some of the load from the network "core" - and this is really important given the fact that more and more applications appear in cellular networks, suggesting a minimum network delay starting from high-resolution games and ending with such critical applications as unmanned vehicles, where human lives are at stake. For example, 5G networks allow content to be cached locally - and if you want to watch a movie on demand, the application can take the stream from the local cache and not transfer it to the core of the network directly from the content provider's servers ... which in turn requires changing security approaches data and cellular communications.
3. The emergence of new opportunities to create additional levels of security in cellular channels
Currently, the main task in ensuring security in cellular communications is to protect against eavesdropping. However, in the future world of smartphones and the Internet of things, in environments with a large number of mechanisms, the probability of listening is likely to fade into the background. Instead, we will have to think about such things as data manipulation attacks, which, for example, can be used to command the mechanisms to perform certain actions (for example, open the door or take control of an unmanned vehicle). Mobile network operators, like consumer electronics manufacturers, will be able to offer “security as a service”, with the result that application providers will be able to apply additional levels of security over existing protected channels of the cellular network when transferring certain types of data.
4. Application of various security mechanisms depending on the type of data
Today, the responsibility of encrypting and protecting data lies with the application provider. In 5G networks, a certain role in this process will also be assigned to network operators - especially with the advent of IoT devices that do not have enough computing power to sufficiently encrypt communications. Security providers as a service can offer three different security options in addition to what the network provides by default:
- traffic transmission without encryption (for data that does not have great value, which, in the case of their interception, will be virtually useless for attackers, for example, data ping requests)
- medium level of protection (as an option - for IoT sensors, data from which can be used for attacks with fraud of this data, for example, when an attacker can distort such data, showing the water level in the floodplain below the real value and thus disable protection operation)
- high level of security (where higher confidentiality and personal data protection are required, which are relevant for high-value data, for example, when transferring credit card data in trade transactions).
All this will allow application developers not to be limited to smartphone platforms alone, and if necessary they will be able to implement an additional level of security.
5. Ensuring security in the growth of M2M communications
The expected growth in the number of devices that will be connected to the network in the next decade is amazing. Under these conditions, ensuring the confidentiality and integrity of data transferred between devices is of great importance, since such environments allow new types of vulnerabilities. Recently we have seen successful attacks with data manipulation, as a result of which, under laboratory conditions, the Keen Security Lab researchers managed to intercept the control of a Tesla unmanned vehicle. We should think about how to protect such data from such attacks in all fragments of the chain, both in the cellular network and beyond. Even with secure communication channels, you may need to encrypt the data transmitted over the public IP network when this data leaves the mobile network and leaves the operator's gateway.
Before we see the commercial launch of the first networks of the fifth generation, we still have a lot to determine in the field of 5G technology, and there will be a lot of discussion of security issues. From now on, instead of large-scale and expensive upgrades at the core level of the network to get 6G networks and newer technologies, we will probably deal with a software-defined environment in which very different rules apply. Operators have a lot to rethink, and we look forward to the opportunity to interact with them in order to identify and identify those new threats - as well as new opportunities - that fifth generation networks can offer us.
Source: https://habr.com/ru/post/316522/
All Articles