The loudest cyber attacks on critical infrastructures

One of the greatest strengths of our modern, developed society is also one of its main drawbacks. In today's interconnected world, developed and high-tech societies are highly dependent on the work of a number of services and services that have now become vital.
A certain infrastructure ensures the normal operation of basic services and production systems in any society. Therefore, the failure of their work due to natural causes, technical problems or deliberate actions can have serious consequences for the supply of resources or the work of critical services, not to mention a security risk.
')
In recent years, cyber-crime has been steadily increasing worldwide.
The development of the Internet and the digital transformation of society is a “double-edged sword” because All this provides certain opportunities for criminals. But what can happen if critical networks become a target for a criminal community?
The PandaLabs anti-virus laboratory of Panda Security has published a white paper entitled “Critical Infrastructure: Cyber Attacks on the Foundations of the Modern Economy” with a chronology of the loudest attacks in the world against the information security of critical infrastructure and recommendations for their protection.

Important Sectors and Critical Infrastructure
Protecting critical infrastructure is an important issue for all countries. The high level of development of modern society depends largely on a number of basic and important services, largely provided by private businesses.
The infrastructure ensures the normal operation of services and systems that are extremely important for the development of the state: government bodies, water supply, financial and tax systems, energy, space, nuclear power plants and transport systems, large industrial enterprises.
As critical infrastructure, we include facilities, networks, services, and systems whose failure in any way affects the health, safety, and welfare of citizens.
Guaranteed provision of vital services in the face of new threats is not only the responsibility of government agencies, but also private companies at the national and international levels.
Specifications
Certain technical characteristics and the level of vulnerability of critical data in such networks mean that their protection is not a trivial task.
New intrusions into the cyber-physical systems of production processes running in critical infrastructure have created a need for new strategies adapted to detect such threats without hindering the operation of the infrastructure itself.

Hybrid architecture
The various critical infrastructures are based on a hybrid architecture that combines classic IT networks and industrial OT networks that manage components that interact with physical objects (cyber-physical systems).

Isolation from the Internet
This aspect deserves special attention, since The growing trend towards interoperability of all types of infrastructure also expands the number of available attack vectors. Control systems for such infrastructures are usually isolated from the Internet and connected to
internal network limits.

SCADA
However, there are such SCADA control systems that are visible and even accessible via the Internet. Most of these systems do not have direct communication with systems that manage critical infrastructure, but they can be used as a gateway so that hackers can receive confidential information to plan more complex attacks.
Strategic priority to solve problems
Modern nations face many challenges related to national security. In this regard, strategic priorities are aimed at protecting critical infrastructure, which may be subject to a number of new threats. To protect it, it is important to draw up a plan that offers prevention and protection against potential threats, both in terms of physical security and the protection of technology and communications.
In recent years, a number of key events have taken place, such as 9/11, which have become a turning point in global security. Since then, the world has developed a situation where the failure of certain critical infrastructure can affect the health, safety and well-being of not only individuals, but also entire nations.
The approach to ensuring the safety of such facilities has also changed. Previously, security was the exclusive prerogative of state bodies. Now the objects of critical infrastructure are mainly in the hands of private business, and therefore it also has a serious responsibility for their security. After the September 11 tragedy, the United States created the Department of Homeland Security and adopted a number of relevant laws and regulations.
In Europe, a similar initiative appeared after its key event: March 11, 2004, the train explosions in Madrid.
The European Commission has developed a global strategy for the protection of critical infrastructure (“The European Program for Critical Infrastructure Protection”), which includes a set of measures to prevent, prevent and respond to terrorist attacks in Europe.
Among other things, the directive states that the main and ultimate responsibility for the protection of critical infrastructures lies with the EU member states and the operators of such infrastructure, and it urges all EU countries to implement a number of measures and initiatives in their national legislation.
Attack history
In general, the public, while admitting certain risks, nevertheless believes that in reality it can be a question of a small number of cyber-attacks on critical infrastructure. Unfortunately, everything is much sadder: we already know hundreds of documented cases of such attacks all over the world. Attacks on such networks have been going on for decades, and below you can get acquainted with the history of these attacks.
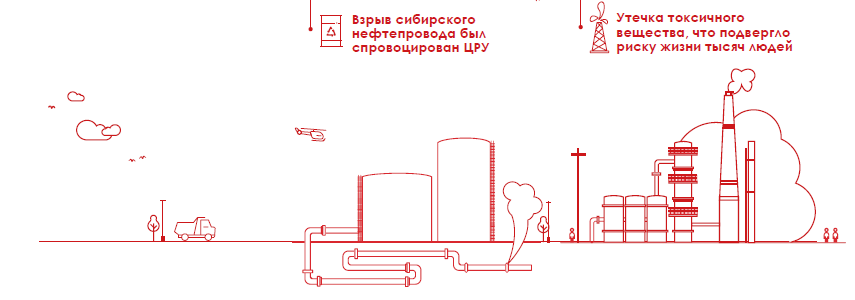
Siberian oil pipeline
The term “Internet” comes to mind whenever we think about cyber attacks on critical infrastructure.
But the first such cyber attack occurred even before the advent of the Internet - in 1982 .
Then a group of hackers was able to install the Trojan in the SCADA system, which controlled the work of the Siberian oil pipeline, which led to a powerful explosion. The attack was organized by the CIA, although this was not known until 2004, when the former Secretary of the Department of Defense and Counselor R. Reagan, Thomas Reed, published his book “At the Abyss: History of the Cold War”.
Chevron
The next incident occurred ten years later, in 1992, when a worker at the Chevron oil company was fired, who hacked into computers at the company's offices in New York and San Jose, who were responsible for warning systems, reconfiguring them for an accident after the system was launched. This sabotage was not disclosed until a toxic substance was leaked in Redmond, California, and the system did not issue appropriate warnings. As a result, thousands of people were at great risk for 10 hours while the system was shut down.
Salt river project
In August 1994, Lane Jarrett Davis managed to hack the Salt River Project network, gaining access to information and removing files from the system responsible for monitoring and supplying water and electricity. He also managed to get access to personal and financial data of clients and employees of the company.
Worcester Airport
Other key sectors also suffered from targeted attacks. On March 10, 1997, the hacker entered the control system used for communications of the air traffic control system in Worcester (Mass. USA), causing a system crash that turned off the telephone for six hours. This particularly affected the telephone system of the control tower, the airport’s fire service and
airlines based at the airport.
Gazprom
In 1999, hackers disrupted the security systems of the Russian energy giant Gazprom. With the help of an insider, they used a trojan to be able to control the SCADA system that controls the gas supply. Fortunately, this did not lead to serious consequences, and the normal operation of the system was restored as soon as possible.

Maroochy Water System
A former employee of the Maroochy Water System (Australia) received a two-year prison sentence for breaking into the water management system in 2000, resulting in millions of liters of wastewater entering the nearby river, which also led to the flooding of a local hotel.
Gas Processing Plant
A gas processing plant built by one American company was also attacked in 2001. A 6-month investigation revealed that the attack was carried out by one of the suppliers, who, in order to conceal the mistake made by him, decided to divert attention by hacking three company PCs and causing a gas shut-off for domestic and corporate clients in one of the European countries.
PDVSA
In December 2002, the oil company PDVSA from Venezuela was attacked, as a result of which oil production decreased from 3 million to 370 thousand barrels per day. During the attack, several corporate computers were hacked.
It was carried out during the strike of the employees of the enterprise, so that their involvement could be assumed.

Traffic lights in los angeles
In 2006, two Los Angeles traffic control engineers broke into traffic lights in protest. They managed to change the program of work of some traffic lights placed on important areas, after which they began to glow red, which led to serious traffic jams.
Tram network in Lodz
In 2008, a 14-year-old student hacked into the tram network system in the Polish city of Lodz, leaving 4 trams out of the way, and 12 people were injured. The student created an infrared remote control, like TVs, with which he was able to control the tram intersections.
Saudi aramco
In 2012, Saudi Aramco, the world's largest oil company, fell victim to a targeted attack on its offices. Hackers gained access to the network due to an attack on one of the company's employees, through which they were able to access 30,000 computers on the network. At some point, hackers managed to remove the contents of all computers, while the screens showed a burning American flag.
Responsibility for the attack claimed a group of hackers, who called themselves the “Sword of Justice”.

Ram gas
Just two weeks after the attack on Saudi Aramco, the Qatari company RamGas, the world's second largest producer of liquefied natural gas, was attacked by the same malware that was used to attack the oil company from Saudi Arabia. For several days, the internal corporate network and the company's website did not work.
Metallurgical plant in Germany
In 2014, one of the metallurgical plants fell victim to the attack in Germany. Using social engineering, hackers managed to gain access to the computer of a single employee, from which they were able to gain access to the internal network of the management system. As a result, it became impossible to shut down one of the domains, which caused enormous damage to the enterprise.
Electric network of Ukraine
At the end of 2015, Ukraine underwent a cyber-attack on its national power grid, with the result that over 600,000 residents were left without electricity.

The first ever cyber attack against Internet infrastructure
Despite a long list of incidents, the first ever cyber attack on Internet infrastructure occurred on April 27, 2007, when a series of attacks in Estonia brought down the websites of various organizations, including the parliament, various ministries, banks, newspapers and various media, etc.
 However, the attack was also directed at certain non-public addresses, including the national financial order processing system and telecommunications services. Urmas Paet, the Estonian Foreign Minister, publicly accused the Russian authorities of involvement in these attacks, although he could not provide any evidence of this.
However, the attack was also directed at certain non-public addresses, including the national financial order processing system and telecommunications services. Urmas Paet, the Estonian Foreign Minister, publicly accused the Russian authorities of involvement in these attacks, although he could not provide any evidence of this.The most famous case of cyber attacks on critical infrastructure: Stuxnet
In 2008, we witnessed one of the most notorious cases in the history of cyber attacks on critical infrastructures: Stuxnet. It is now known that this was a coordinated attack by the Israeli and American intelligence services, aimed at disrupting the Iranian nuclear program.
 They created a worm that infected computers running uranium centrifuges at the Iranian plant at Natanz, as a result of which they began to work at full speed, while the engineers on their monitors observed normal operation. This caused physical damage to all uranium centrifuges in the plant. After this incident, the public learned of such threats.
They created a worm that infected computers running uranium centrifuges at the Iranian plant at Natanz, as a result of which they began to work at full speed, while the engineers on their monitors observed normal operation. This caused physical damage to all uranium centrifuges in the plant. After this incident, the public learned of such threats.Attacks in other companies also affected critical infrastructure.
In addition to attacks specifically designed to damage this type of infrastructure, attacks such as those faced by other companies also adversely affect critical objects, and the consequences were sometimes just as serious. Similar problems mainly began at the end of the last decade, since network worms began to spread on the web by themselves.
For example, a case at a leading US food factory when a viral infection caused damage, measured in thousands of dollars. One employee remotely connected from a home PC that was infected with the Nimda virus. As soon as he entered the corporate network, the worm spread to all management systems.
In 2003, a US oil company suffered from the SQLSlammer worm, which penetrated the internal network. Although this did not stop production, it affected internal communications.
We had to spend several days to completely remove the worm from the network and update the systems to prevent further attacks. By the way, this worm was one of the most destructive for companies.
For distribution, he used a vulnerability in SQL database servers (a standard tool in corporate networks). The vulnerability was fixed by Microsoft in January 2003. By the way, another American oil company began updating all of its facilities immediately after the appearance of this patch, in order to protect itself from this worm. However, to complete the upgrade, it was necessary to reboot the servers on which this patch was installed, while some of them were located on oil platforms where there was no dedicated IT staff. For this, we had to send specialists by helicopter. And while they did not have time to come, the worm penetrated into some corporate systems and infected those that had not yet been updated.
Also in 2003, one of the largest automakers in the United States also suffered from an attack by the SQLSlammer worm, which instantly spread to its 17 factories. The total damage to the company amounted to $ 150 million. Although the patch has already been available for six months, the company's IT managers have not yet installed it.
In the same year, Air Canada’s computer responsible for flight information, fuel refueling, etc. suffered from a malicious infection (that malware was not public). As a result of the infection, 200 flights were delayed or canceled.
In 2005, in Japan, a Mitsubishi Electric employee’s computer was infected with a malware program, which resulted in a leak of confidential inspection documents about two nuclear power plants owned by the company.
In 2006, two computers in a hospital (United Kingdom) responsible for managing a complex of radiotherapy for people with cancer were infected with a malware program. As a result, 80 patients had to be postponed. Two years later, three more hospitals in the UK were infected with a variant of the Mytob worm, after which they had to disconnect all computers from the network for 24 hours to resolve the incident.
In 2013, 200 computers of the Department of Highways and Transportation in Cook County (Illinois, USA) were infected. These systems were responsible for maintaining hundreds of kilometers of roads in the suburbs of Chicago. As a result, the attack had to turn off the network for 9 days to cure all computers.
This list of incidents shows that the danger of cyber attacks on critical infrastructures is very real, and today all governments are aware of these risks.
Additional protection for critical infrastructure
Given the reality that we see and in which we live, it is necessary to regulate the protection of critical infrastructure in order to provide it with a higher level of protection against all types of threats.
In May 2016, after the G7 countries ’energy ministers’ meeting, a joint declaration was adopted, which, among other things, emphasized the importance of building resilient energy systems (including gas, electricity and oil) in order to effectively respond to emerging cyber threats and maintain normal the work of vital services.
In order to improve measures to prevent and respond to logical attacks, national governments implement a number of measures at the global level. These measures are aimed at creating centers for collecting all the necessary information to improve the protection of critical infrastructures. As a result, a comprehensive strategy was developed to solve this problem, which should be included in the national legislation of these countries .
It is not easy to answer the question of how adequate the security of critical infrastructure is at present, because unknown information or technology that can be used by cyber-criminals, and therefore can not be 100% safe. What can be improved is protection against known attacks, to prevent which it is necessary to apply a series of effective measures:
1. Checking systems for vulnerabilities, especially those on which security holes have already been fixed and have been known for some time.
2. Adequate monitoring of networks used to control such critical infrastructure facilities, and, if necessary, their complete isolation from external connections, which will allow detecting external attacks and preventing access to systems controlled from the internal network.
3. Control over removable devices, which is important in any infrastructure, not only because they are the direction of such attacks, as is the case with Stuxnet. When protecting such critical infrastructure facilities, it is imperative that malware does not penetrate the internal network through removable devices, which can also be used to steal confidential information.
4. Monitoring of PCs to which programmable logic controllers (or PLCs) are connected. These Internet-connected devices are the most sensitive, because they can provide hackers with access to critical management systems. Even if they cannot gain control of the system, they will be able to gain valuable information for other lines of attack.
Decision
The solution is to protect against modern threats and targeted attacks, which should also allow detecting unusual or suspicious behavior. A system that must ensure the confidentiality of data, protection of assets and reputation of the company.
An intelligent platform that can help critical infrastructure security professionals respond quickly to threats and get all the information they need to prepare an adequate response.
The Adaptive Defense 360 solution is an advanced IT security system that combines the latest defense technologies and advanced attack detection and response technologies with the ability to classify 100% of the processes performed.
Adaptive Defense 360 classifies absolutely all active processes on computers, providing protection against known malware and zero-day attacks, persistent threats of increased complexity (ART) and targeted attacks.
The platform uses contextual logic to identify malicious behaviors and generate enhanced information protection actions against known and unknown threats.
The solution analyzes, classifies and compares all collected data on cyber threats in order to perform prevention, detection, response and recovery tasks.
The decision determines how and by whom the data was accessed, and also controls data leakage as a result of the work of malicious programs or actions of employees.
The solution detects and eliminates system vulnerabilities and holes in installed programs, and also prevents the use of unwanted applications (toolbars, adware, add-ons, etc.).
Source: https://habr.com/ru/post/316500/
All Articles