A bit about Deep Packet Inspection systems
A fairly strong areola of myths has formed around the in -depth analysis of traffic systems , which hinders the understanding of the functional capabilities and solutions for technology adaptation. In our today's material we want to talk about these doubts and try to dispel some of them.

/ Flickr / pascal / PD
Many people argue and at the same time fear that the in-depth analysis of traffic is an unreliable postman who examines the contents of each package he delivers. However, this analogy is inappropriate. A more accurate analogy would be a postman who carries greeting cards or postcards, because the data packets on the Web are just like them - their content is accessible to everyone.
')
DPI-systems are not used to read forwarded messages, for example, by e-mail, they only analyze and establish the nature of the transmitted content - voice, letter, and malicious software. Based on the data, they decide what to do with the content. This allows you to protect against DDoS-attacks, work with advertising, optimize access channels, collect analytics and prioritize traffic. Note that all these functions are implemented by the SCAT system from VAS Experts.
This myth is a consequence of the previous one. There is an opinion that a network device that explores user content violates the privacy of communication, as if “listening” to calls. But this is not entirely true. Following this logic, antiviruses, antispam protection, and intrusion detection systems, which are important for ensuring the safety of work on the Internet, will also fall under the definition of “listening”.
An automated computer system that scans files for known patterns of malware or spam is not a violation of privacy. In fact, this procedure is less thorough than the inspection of baggage at the airport. The scanners are controlled by people who study the contents of the luggage and bags and accurately identify the objects inside, while the DPI-system responds only to the programmed scenarios. It turns out that the DPI-solution at the airport would “see” in the baggage only those items that are forbidden to carry on board the aircraft.
I would also like to note that DPI systems, on the contrary, help prevent incidents of “eavesdropping” on the line. We are talking about the so-called MITM-attacks. This term refers to a network attack when an attacker connects between the user and the application with the help of special software, simulating working with him and creating the impression of a normal process of information exchange. The purpose of such an attack can be very different - the theft of personal data of users, personal correspondence or bank details, etc.
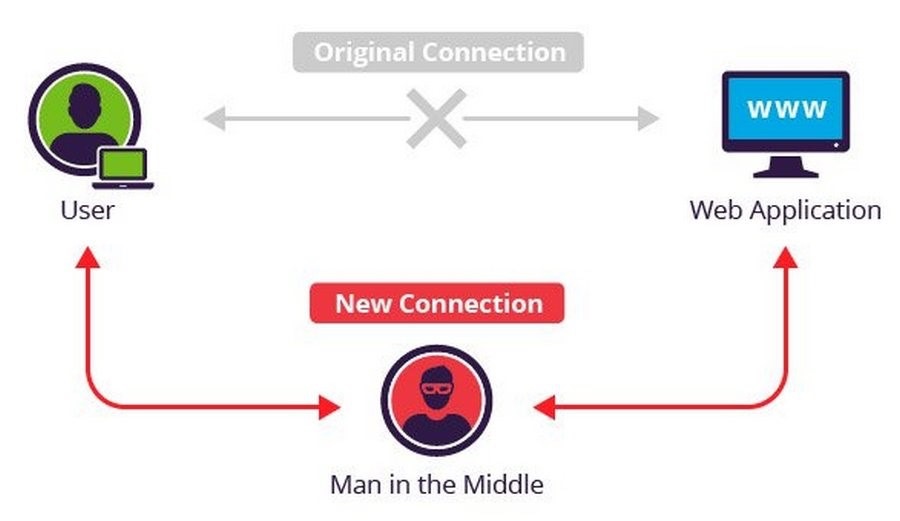
Usually the MITM attack takes place in two stages. First, traffic from the user to the target application is intercepted. The easiest way to intercept remains a passive attack, when an attacker creates open wireless points. At the time of connecting the user to the network, the attacker gets access to all transmitted data. As for other methods of intercepting –active, here options such as IP-spoofing, ARP-spoofing and DNS-spoofing are used, consisting in changing the IP-address, MAC-address or DNS infection, respectively.
After interception, two-way SSL traffic is decrypted, so that the user and the requested resource do not notice external interference. There are also several techniques for this: HTTPS spoofing, SSL Beast attack, SSL hijacking.
Therefore, to protect against MITM attacks, developers of web applications and websites should use secure TLS and HTTPS protocols, which complicate spoofing attacks and traffic interception. Telecom operators use the Deep Packet Inspection system to detect anomalies in data networks and prevent spoofing.
There is an opinion that DPI solutions will start to encourage the adaptation of encryption technologies, as more and more users will try to prevent the provider from “reading” their mail. However, the growing popularity of encryption will only be useful. After all, the real threat to consumers is access to unencrypted sites. In this case, they become easy "prey" for intruders.
For example, Netflix is the largest video content provider in the world. The service has about 60 million subscribers, and at the beginning of 2016, users “watched” 10 billion hours. The company generates more than a third of all incoming traffic in North America in the evening.
Recently, Netflix announced that the service will begin to encrypt all transmitted traffic, changing the data transfer protocol from HTTP to secure HTTPS. Such a solution should ensure client confidentiality and protect the intellectual property of content owners.
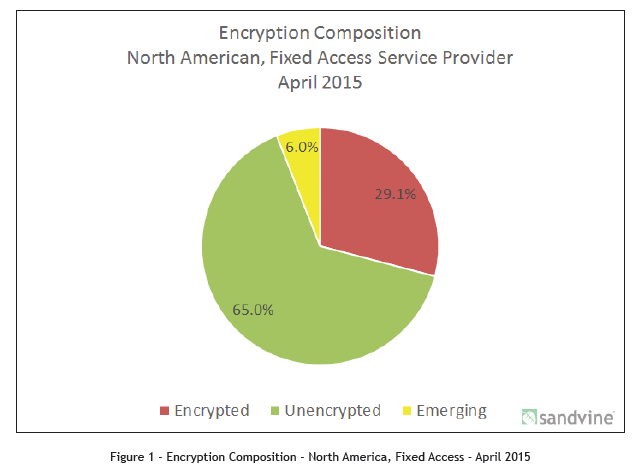
Now the bulk of encrypted traffic on the Internet comes from Google, Facebook and Twitter. In the image below, they represent most of the red sector. After Netflix switches to HTTPS, the red and green sectors will be swapped.
With the proliferation of traffic encryption protocols, telecom operators using in-depth analysis systems will face the challenge of not studying the data inside an encrypted packet. However, company representatives say that they never had a goal to spy on the actions of users.
The DPI technology is fairly neutral in itself. It is just a tool that can be used in different ways. The negative color of the DPI-systems acquired due to a misunderstanding of the principles of work and purpose of decisions. But DPI is not necessarily a violation of someone’s privacy or an invasion of privacy, it also accelerates the network, improves security and analyzes the necessary statistics.
Additional reading: DPI-digest - Analysis of traffic, blocking, platforms and manufacturers of Deep Packet Inspection systems .

/ Flickr / pascal / PD
Myth # 1: DPI as a postman looking in envelopes
Many people argue and at the same time fear that the in-depth analysis of traffic is an unreliable postman who examines the contents of each package he delivers. However, this analogy is inappropriate. A more accurate analogy would be a postman who carries greeting cards or postcards, because the data packets on the Web are just like them - their content is accessible to everyone.
')
DPI-systems are not used to read forwarded messages, for example, by e-mail, they only analyze and establish the nature of the transmitted content - voice, letter, and malicious software. Based on the data, they decide what to do with the content. This allows you to protect against DDoS-attacks, work with advertising, optimize access channels, collect analytics and prioritize traffic. Note that all these functions are implemented by the SCAT system from VAS Experts.
Myth number 2: DPI is a violation of privacy
This myth is a consequence of the previous one. There is an opinion that a network device that explores user content violates the privacy of communication, as if “listening” to calls. But this is not entirely true. Following this logic, antiviruses, antispam protection, and intrusion detection systems, which are important for ensuring the safety of work on the Internet, will also fall under the definition of “listening”.
An automated computer system that scans files for known patterns of malware or spam is not a violation of privacy. In fact, this procedure is less thorough than the inspection of baggage at the airport. The scanners are controlled by people who study the contents of the luggage and bags and accurately identify the objects inside, while the DPI-system responds only to the programmed scenarios. It turns out that the DPI-solution at the airport would “see” in the baggage only those items that are forbidden to carry on board the aircraft.
I would also like to note that DPI systems, on the contrary, help prevent incidents of “eavesdropping” on the line. We are talking about the so-called MITM-attacks. This term refers to a network attack when an attacker connects between the user and the application with the help of special software, simulating working with him and creating the impression of a normal process of information exchange. The purpose of such an attack can be very different - the theft of personal data of users, personal correspondence or bank details, etc.

Usually the MITM attack takes place in two stages. First, traffic from the user to the target application is intercepted. The easiest way to intercept remains a passive attack, when an attacker creates open wireless points. At the time of connecting the user to the network, the attacker gets access to all transmitted data. As for other methods of intercepting –active, here options such as IP-spoofing, ARP-spoofing and DNS-spoofing are used, consisting in changing the IP-address, MAC-address or DNS infection, respectively.
After interception, two-way SSL traffic is decrypted, so that the user and the requested resource do not notice external interference. There are also several techniques for this: HTTPS spoofing, SSL Beast attack, SSL hijacking.
Therefore, to protect against MITM attacks, developers of web applications and websites should use secure TLS and HTTPS protocols, which complicate spoofing attacks and traffic interception. Telecom operators use the Deep Packet Inspection system to detect anomalies in data networks and prevent spoofing.
Myth number 3: DPI will be "out of work" in the dissemination of encryption
There is an opinion that DPI solutions will start to encourage the adaptation of encryption technologies, as more and more users will try to prevent the provider from “reading” their mail. However, the growing popularity of encryption will only be useful. After all, the real threat to consumers is access to unencrypted sites. In this case, they become easy "prey" for intruders.
For example, Netflix is the largest video content provider in the world. The service has about 60 million subscribers, and at the beginning of 2016, users “watched” 10 billion hours. The company generates more than a third of all incoming traffic in North America in the evening.
Recently, Netflix announced that the service will begin to encrypt all transmitted traffic, changing the data transfer protocol from HTTP to secure HTTPS. Such a solution should ensure client confidentiality and protect the intellectual property of content owners.
Now the bulk of encrypted traffic on the Internet comes from Google, Facebook and Twitter. In the image below, they represent most of the red sector. After Netflix switches to HTTPS, the red and green sectors will be swapped.

With the proliferation of traffic encryption protocols, telecom operators using in-depth analysis systems will face the challenge of not studying the data inside an encrypted packet. However, company representatives say that they never had a goal to spy on the actions of users.
DPI is just a tool
The DPI technology is fairly neutral in itself. It is just a tool that can be used in different ways. The negative color of the DPI-systems acquired due to a misunderstanding of the principles of work and purpose of decisions. But DPI is not necessarily a violation of someone’s privacy or an invasion of privacy, it also accelerates the network, improves security and analyzes the necessary statistics.
Additional reading: DPI-digest - Analysis of traffic, blocking, platforms and manufacturers of Deep Packet Inspection systems .
Source: https://habr.com/ru/post/316270/
All Articles