Intrusion Detection For PHP Applications With PHPIDS
This article will show how to configure PHPIDS . PHPIDS (PHP-Intrusion Detection System) is an easily used, well-structured, fast interlayer for analyzing the security of your applications. IDS is not a layer for analyzing user input; it only recognizes when they try to attack your site. based on a set of tested and tested rules, each attack is assigned a hazard rating. This will allow you to easily save attack statistics or send notifications to the development team.
Foreword
Examples for this article were made on Debian Etch LAMP with Apache version 2 and PHP5, IP - 192.168.0.100.
Apache user and group - www-data. The path to php.ini is /etc/php5/apache2/php.ini. The / var / www / web1 / web was used as the document root for the virtual host.
Installing PHPIDS
From the security images, I installed PHPIDS beyond document root, so I created / var / www / web1 / phpids:
')
Then I installed PHPIDS (at the time of installation, the latest version was 0.4.7).
Next, I reconfigured Config.ini:
I use the default configuration, and all I have to do is change the paths.
Foreword
Examples for this article were made on Debian Etch LAMP with Apache version 2 and PHP5, IP - 192.168.0.100.
Apache user and group - www-data. The path to php.ini is /etc/php5/apache2/php.ini. The / var / www / web1 / web was used as the document root for the virtual host.
Installing PHPIDS
From the security images, I installed PHPIDS beyond document root, so I created / var / www / web1 / phpids:
')
Then I installed PHPIDS (at the time of installation, the latest version was 0.4.7).
cd / tmp
wget php-ids.org/files/phpids-0.4.7.tar.gz
tar xvfz phpids-0.4.7.tar.gz
cd phpids-0.4.7
mv lib / / var / www / web1 / phpids /
cd / var / www / web1 / phpids / lib / IDS
chown -R www-data: www-data tmp /
Next, I reconfigured Config.ini:
cd config /
vi Config.ini
I use the default configuration, and all I have to do is change the paths.
; PHPIDS Config.ini
; General configuration settings
; !!! DO NOT PLACE THIS FILE INSIDE THE WEB-ROOT IF DATABASE CONNECTION DATA WAS ADDED !!!
[General]
filter_type = xml
filter_path = /var/www/web1/phpids/lib/IDS/default_filter.xml
tmp_path = / var / www / web1 / phpids / lib / IDS / tmp
scan_keys = false
exceptions [] = __utmz
exceptions [] = __utmc
; If you use the PHPIDS logger you can define specific configuration here
[Logging]
; file logging
path = /var/www/web1/phpids/lib/IDS/tmp/phpids_log.txt
; email logging
; spam attempts,
; see documentation
recipients [] = test@test.com.invalid
subject = "PHPIDS detected an intrusion attempt!"
header = "From: info@php-ids.org"
safemode = true
allowed_rate = 15
; database logging
wrapper = "mysql: host = localhost; port = 3306; dbname = phpids"
user = phpids_user
password = 123456
table = intrusions
; If you would like
[Caching]
; caching: session | file | database | memcached | none
caching = file
expiration_time = 600
; file cache
path = /var/www/web1/phpids/lib/IDS/tmp/default_filter.cache
; database cache
wrapper = "mysql: host = localhost; port = 3306; dbname = phpids"
user = phpids_user
password = 123456
table = cache
; memcached
; host = localhost
; port = 11211
; key_prefix = PHPIDS
; tmp_path = /var/www/web1/phpids/lib/IDS/tmp/memcache.timestamp
Using PHPIDS
Now we will create /var/www/web1/web/phpids.php that will use PHPIDSset_include_path (
get_include_path ()
. PATH_SEPARATOR
. '/ var / www / web1 / phpids / lib'
);
require_once 'IDS / Init.php';
$ request = array (
'REQUEST' => $ _REQUEST,
'GET' => $ _GET,
'POST' => $ _POST,
'COOKIE' => $ _COOKIE
);
$ init = IDS_Init :: init ('/ var / www / web1 / phpids / lib / IDS / Config / Config.ini');
$ ids = new IDS_Monitor ($ request, $ init);
$ result = $ ids-> run ();
if (! $ result-> isEmpty ()) {
// Take a look at the result object
echo $ result;
require_once 'IDS / Log / File.php';
require_once 'IDS / Log / Composite.php';
$ compositeLog = new IDS_Log_Composite ();
$ compositeLog-> addLogger (IDS_Log_File :: getInstance ($ init));
$ compositeLog-> execute ($ result);
}
After that enter 192.168.0.100/phpids.php in your browser and you will see a blank page.
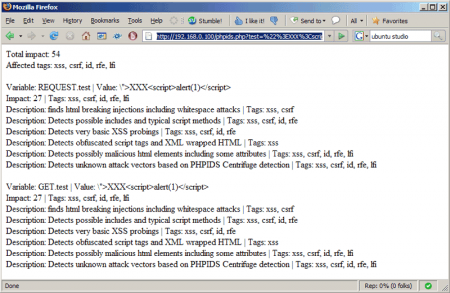
However, if you add different parameters, for example 192.168.0.100/phpids.php?test=%22%3EXXX%3Cscript%3Ealert (1)% 3C / script% 3E, PHPIDS will determine them and print the result in the browser
We will now make PHPIDS use in every script you make. Of course, you do not have to modify every php file on your system. We will tell php to run PHPIDS every time the script starts. We do this using the auto_prepend_file parameter. To do this, we will make a modification in php.ini or .htaccess fileauto_prepend_file = /var/www/web1/web/phpids.php
or for .htaccess
php_value auto_prepend_file /var/www/web1/web/phpids.php
Restart your Apache (for the case with the modification of php.ini)
Create an info.php file with contentsphpinfo ();
Write in the browser 192.168.0.100/info.php and you will see the normal output of the phpinfo () command
now add parameters, for example 192.168.0.100/info.php?test=%22%3EXXX%3Cscript%3Ealert (1)% 3C / script% 3E
and you will see
PHPIDS will write this data to /var/www/web1/phpids/lib/IDS/tmp/phpids_log.txt“192.168.0.200”, 2008-06-04T17: 36: 08 + 02: 00,54, “xss csrf id rfe lfi”, “REQUEST.test =% 5C% 22% 3EXXX% 3Cscript% 3Ealert% 281% 29% 3C% 2Fscript% 3E GET.test =% 5C% 22% 3EXXX% 3Cscript% 3Ealert% 281% 29% 3C% 2Fscript% 3E ",
"% 2Finfo.php% 3Ftest% 3D% 2522% 253EXXX% 253Cscript% 253Ealert% 281% 29% 253C% 2Fscript% 253E"
Now, looking through the records. You will see that the hacker was trying to do something with your application.
To add another security level for your application, you can stop the script if PHPIDS detects an attack:
we can add something like this
die ('Go away!
');
to the if (! $ result-> isEmpty ()) {} section in the /var/www/web1/web/phpids.php script fileset_include_path (
get_include_path ()
. PATH_SEPARATOR
. '/ var / www / web1 / phpids / lib'
);
require_once 'IDS / Init.php';
$ request = array (
'REQUEST' => $ _REQUEST,
'GET' => $ _GET,
'POST' => $ _POST,
'COOKIE' => $ _COOKIE
);
$ init = IDS_Init :: init ('/ var / www / web1 / phpids / lib / IDS / Config / Config.ini');
$ ids = new IDS_Monitor ($ request, $ init);
$ result = $ ids-> run ();
if (! $ result-> isEmpty ()) {
// Take a look at the result object
echo $ result;
require_once 'IDS / Log / File.php';
require_once 'IDS / Log / Composite.php';
$ compositeLog = new IDS_Log_Composite ();
$ compositeLog-> addLogger (IDS_Log_File :: getInstance ($ init));
$ compositeLog-> execute ($ result);
die ('Go away!
');
}
If there is no attack, the script will continue execution, otherwise the hacker will see it.
translator comment
The above examples can be used on combat systems. However, this would require some kind of conversion.$ init = IDS_Init :: init ('/ var / www / web1 / phpids / lib / IDS / Config / Config.ini');
since every time there is no need to load the settings file from the file, and replace it with the class written in advance
Source: https://habr.com/ru/post/31617/
All Articles