Dual authentication Vkontakte - sex or imitation?
Hello! Recently I decided to test a hardware OTP token with the possibility of flashing over NFC by connecting it to my account in vk.com. At the same time I came across flaws in the two-factor authentication system of Vkontakte, which seemed to me quite significant. I want to share my observations with you, because I didn’t recognize errors in VK itself. Maybe I'm a little paranoid? I wonder what you say, habrovchane.

I will make a reservation that before starting to work on an article, I made all my observations on HackerOne. None of the described bugs Vkontakte not recognized. But when, before publishing the article, I decided to make confirming screenshots, it turned out that one of the bugs was fixed. That listened to my words, can not but rejoice. The only pity is that the guys didn't even say “thank you”.
So, the error number 1. Static secret key.

In order to connect an application for generating OTP to your account, the user enters a password, before which a page opens with a secret key needed to issue a software token. So far, everything is correct.
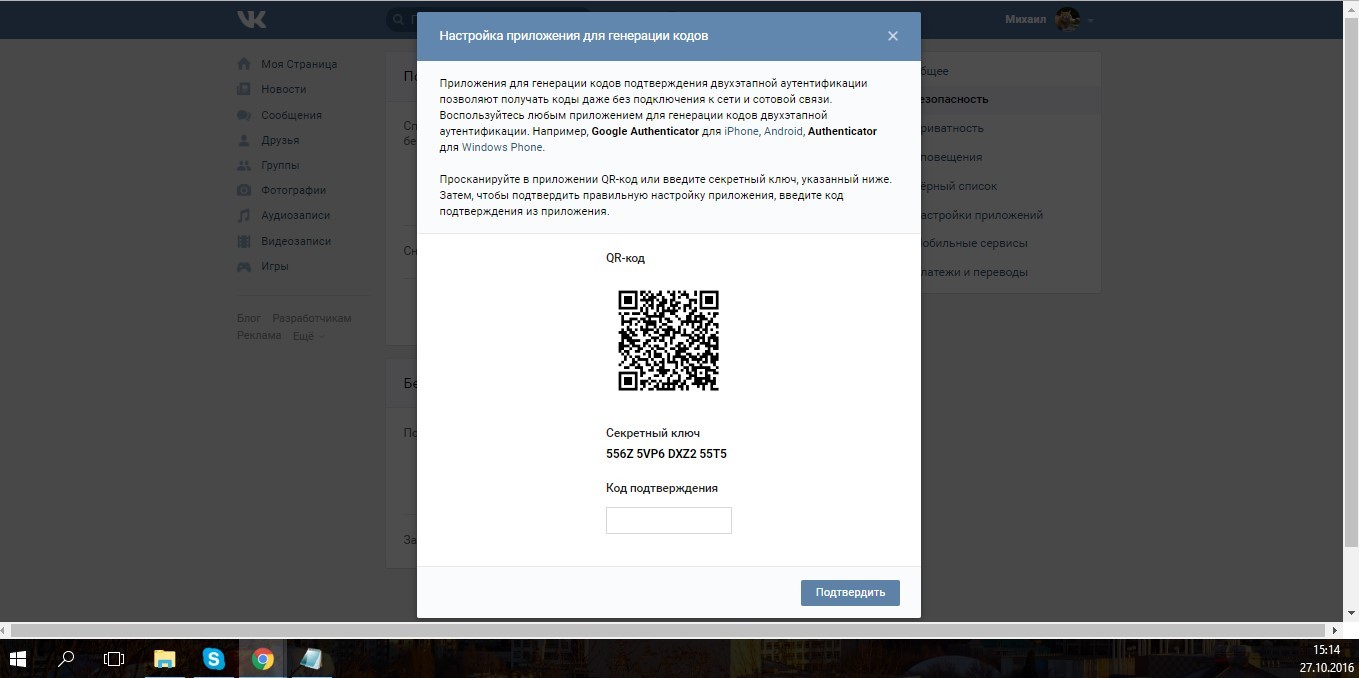
But if for any reason the user did not activate the software token right away (for example, he was distracted by an important call, or simply changed his mind and returned to the main page), then after a while he would decide to get the token, he would again be offered the same secret key.
The situation is aggravated by the fact that within half an hour after entering the password, even if you went to the main page or logged out of your account, and then logged in again, before displaying the QR code with a secret, no password is requested again.


')
Why is this dangerous?
The Vkontakte Token, like any other TOTP token, works according to a fairly simple principle: it generates one-time passwords using an algorithm based on two parameters — time and secret key. As you understand, the only thing that is needed to compromise the second factor of authentication is to know the SECRET KEY.
Such a vulnerability leaves the attacker two loopholes:
- If the user moves away from the computer, the attacker will have enough time to compromise his secret key.
- Having seized the user's password, the attacker can easily peep his secret key in advance.

Solving the problem is simple. The secret key should change every time after refreshing the page, as it happens, for example, in Facebook.
Error number 2. A new token after reissue uses the same secret key.

At the time of publication of the article, this flaw was eliminated.
The situation described above is aggravated by the fact that when you re-issue a token, Vkontakte will not offer you a new secret key. In fact, one secret key is tied to your page and you can no longer change it.
Why is this dangerous?
If you find out that your secret key is compromised (for example, when you first issued a token, as described in the first paragraph), you no longer need double authentication of Vkontakte. Feel free to turn off the second factor and pick up a better password. Re-issue a token with a new secret is not possible.
If you lost the phone on which the token was installed, you can do the same. The one who got your smartphone in his hands will be able to safely use it to log into your account. It remains to find out only the password. In this case, the whole essence of two-factor authentication is lost. It is clear that if the user notices the discredit of his account, he can contact the caliper, but this will spend valuable time, which he may not have.
Mistake number 3. Disabling the second factor without asking for a one-time password.
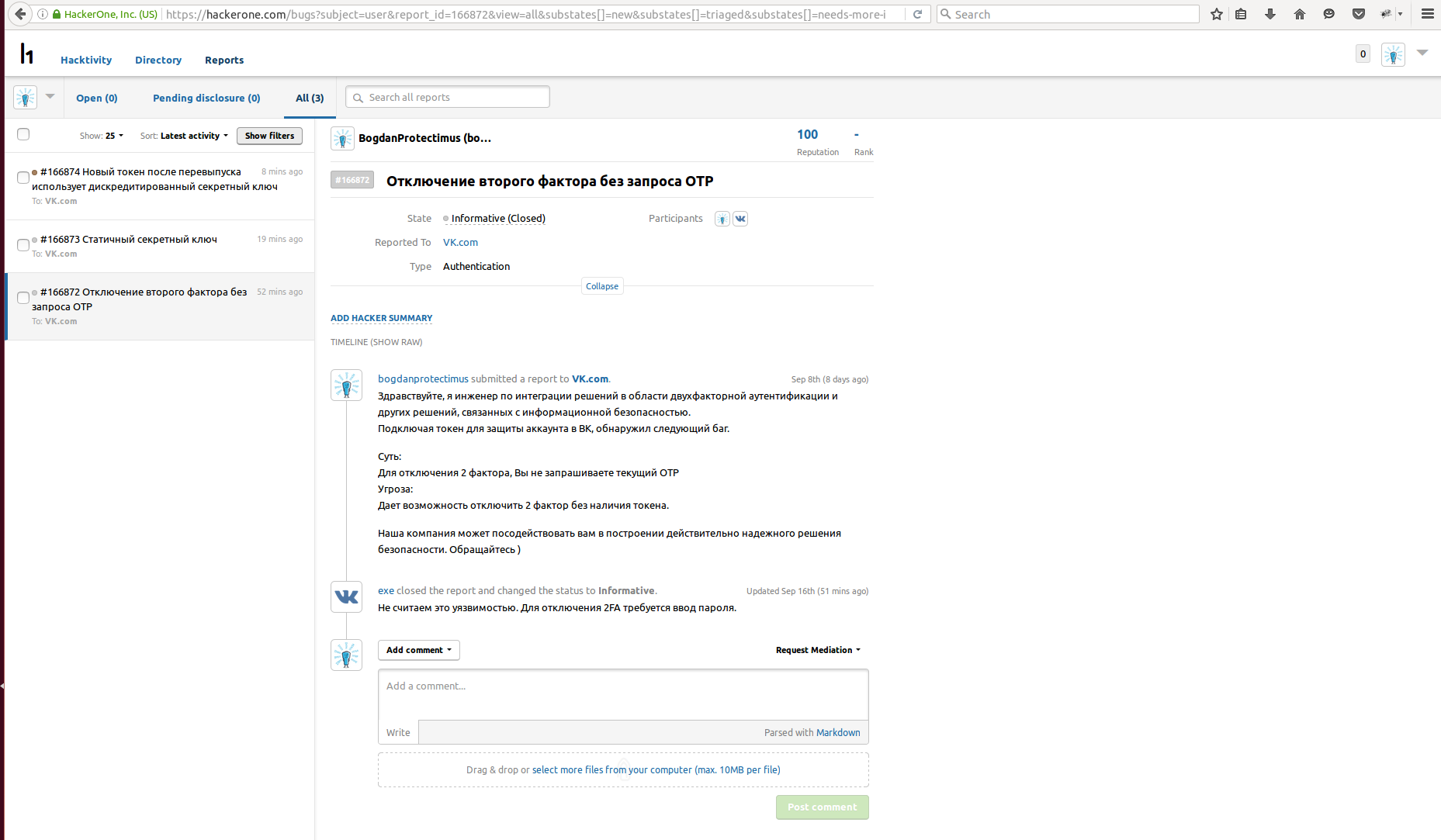
Here everything is clear from the name. When you disable the second factor, just enter the password, OTP is not requested.
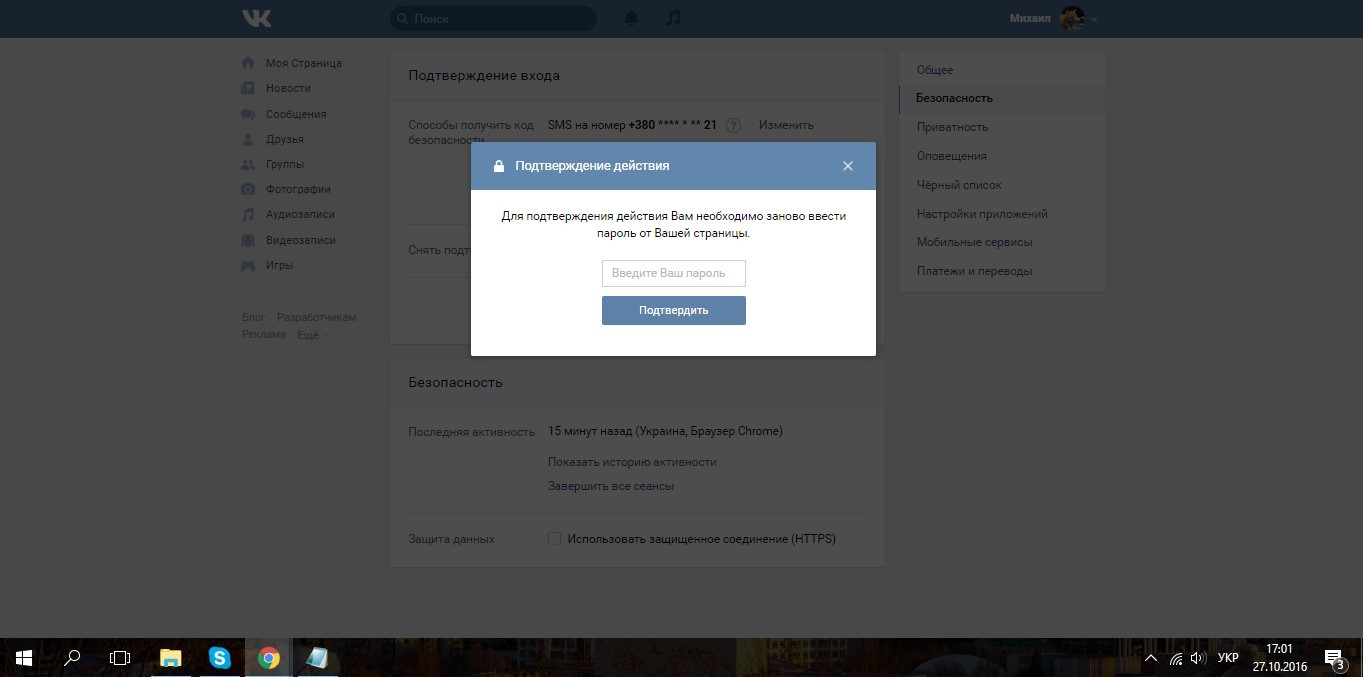

Why is this dangerous?
If only a password entry is enough to disable double authentication of Vkontakte, the essence of two-factor authentication is lost. And the essence of two-factor authentication is that the disadvantages of one factor overlap with the advantages of another. In vk.com, this is the knowledge factor (password) and the ownership factor (phone). This was invented so that the compromise of one of the factors was not enough to gain access to the account. If an intruder has your password, he will not have a one-time password to break into his account, and vice versa, if he takes possession of your phone, he will need to know the password additionally.
It also turns out that it is enough to know the user's password in order to simply disable the second authentication factor. In fact, this turns Vkontakte two-factor authentication into one-factor authentication.
Vkontakte offers its users a very convenient feature “Remove confirmation from the current browser”. I am sure that the feature is popular and users turn off the confirmation at least at home and at work. Moreover, most users have their passwords stored in browsers, where they can be easily viewed and copied.
Imagine this situation, your colleague decided to make fun of you. While you were not at work, he went to your computer, looked at the saved passwords in the browser, logged into VK and disconnected 2FA. Now he will be able to log into your account until you notice a change, which may not happen soon. You have never entered a one-time password on the devices you use most often, so nothing will change for you. A joker colleague will have full access to your account, and no one knows what this may lead to.
If the bug with the token re-issue had not been fixed, when the secret key did not change when the token was re-released, the situation could have become even more interesting! Your colleague, already knowing the password, could have disabled 2FA, after which he connected the two-factor authentication again, he would have seen the secret key, issued himself a token identical to yours, and could read your messages as long as your account is alive.
findings
When you connect two-step authentication to your Vkontakte account, a reminder appears that says, “Even if an attacker finds out your login, password, and verification code used, he will not be able to get to your page from his computer."
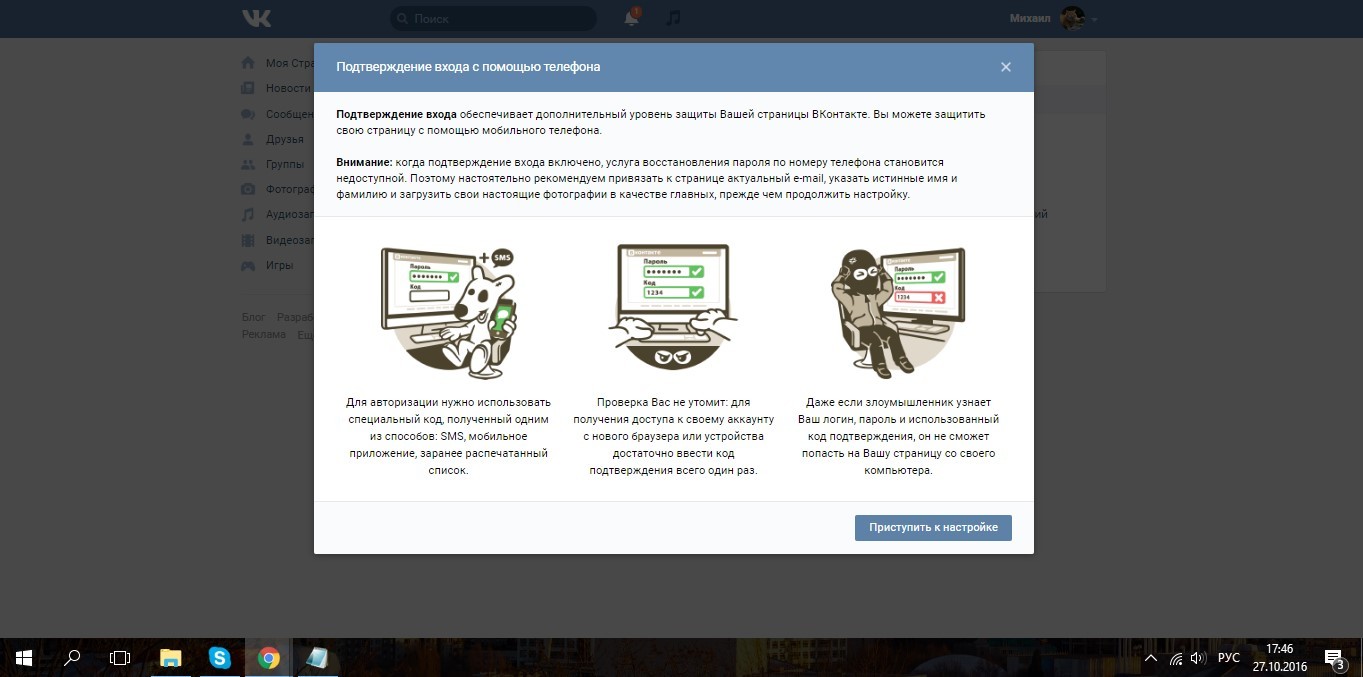
Unfortunately, it turned out that this is not entirely true. Under certain circumstances, an outsider will be able to recognize someone else's token on Vkontakte, or even completely disable the second factor, knowing your password. Waiting for your opinions.
Source: https://habr.com/ru/post/315862/
All Articles