How can you centrally manage all mobile devices in a company?
In the modern era of BYOD and enterprise employee mobility, MDM issues are becoming ever more relevant. How can this issue be solved with the help of RMM solutions?
Consider possible solutions for the example of Panda Systems Management .
Challenge: how to monitor and manage corporate mobile devices
The rapid spread of mobile devices in recent years has seriously affected the daily lives of many people. In addition to a number of advantages that mobile devices give us, it is worth highlighting mobility itself: now people can read news, play online games, chat, listen to music and watch videos anytime, anywhere. For many people, a mobile device (for example, a tablet) has generally replaced the traditional computer or laptop in our understanding.
Moreover, such mobile devices, which is quite natural, have become increasingly used at work for corporate purposes: contacts with customers and partners, e-mail, video conferences, work with documents, etc.
And it is here that certain difficulties and problems begin for enterprise IT specialists: the mobility of modern employees and the wide range of available platforms for mobile devices make the control and management much more difficult.
Indeed, if different security and privacy policies are applied to traditional workstations in the enterprise, then what about mobile devices? After all, employees also work on them with corporate documents, have access to corporate resources, etc. Therefore, it is also necessary to manage and control mobile devices. And it is desirable to do it centrally. But how?
In addition, the presence of various mobile platforms, competing among themselves for the same market niche, further complicated the network management processes and forced the emergence of fragmented management solutions with very different functional capabilities.
So what to do and how to be?
Solution: a single RMM solution for managing all corporate mobile devices
Yes, for centralized mobile device management, you should use integrated RMM solutions that provide MDM (Mobile Devices Management) capabilities.
Such solutions, as a rule, allow you to centrally manage various mobile devices (for example, based on iOS and / or Android), including also tablets, netbooks, laptops, smartphones, etc., regardless of their physical location from a single centralized console management.
Thanks to such solutions, you can monitor the status of these devices (hardware and software, change logs, operating system version, mobile operator, total and free disk space, etc.), apply appropriate security and confidentiality policies to them, and also apply the necessary actions in case of their theft or loss. Depending on the functionality of the RMM system, there may be additional features: remote software installation, remote management and support, a wide range of reports, etc.
One of these suitable solutions is the cloud RMM service of Panda Systems Management, which, in addition to the wide functionality typical of integrated RMM systems, also offers the advantages that are characteristic of cloud services: simple and easy implementation and maintenance without a local infrastructure in the enterprise; control anytime, anywhere from any device, easier administration of mobile devices.
We have previously written a review article about Panda Systems Management , where, in addition to all its advantages, we talked about how you can easily and easily implement it in the enterprise, and also wrote separately about the monitoring system monitors . Today we will focus on how you can easily and easily manage mobile devices with this solution.
So today consider the following questions:
- What platforms are supported
- Installing the agent on mobile devices with Android and iOS
- MDM policies and their types
- Tools for remote mobile device management
You can register a trial version of Panda Systems Management on the website for free and test the service in your IT environment.
Supported Platforms
Panda Systems Management, not to mention the ability to manage laptops and netbooks / ultrabooks running Windows and Mac, also supports tablets and smartphones with iOS and Android.
IOS Devices
• iPhone 4, 4S
• iPhone 5, 5c, 5s
• iPhone 6, 6 Plus
• iPhone 6s, 6s Plus
• Ipod Touch 5 and 6 generation
• iPad 2, 3, 4, Air, Air 2, Mini, Mini 2, Pro
Android devices
• Android 2.3.3 version (Gingerbread) and higher.
Agent installation on Android and iOS mobile devices
In order to manage mobile devices with Adnroid and iOS through the Panda Systems Management centralized web console, an agent must be installed on them, as described below.
Enable MDM in the management console
In order for you to interact with your mobile devices from a centralized management console, you need to enable the MDM function. To do this, you need to import the free Mobile Device Management component from the Comstore section.
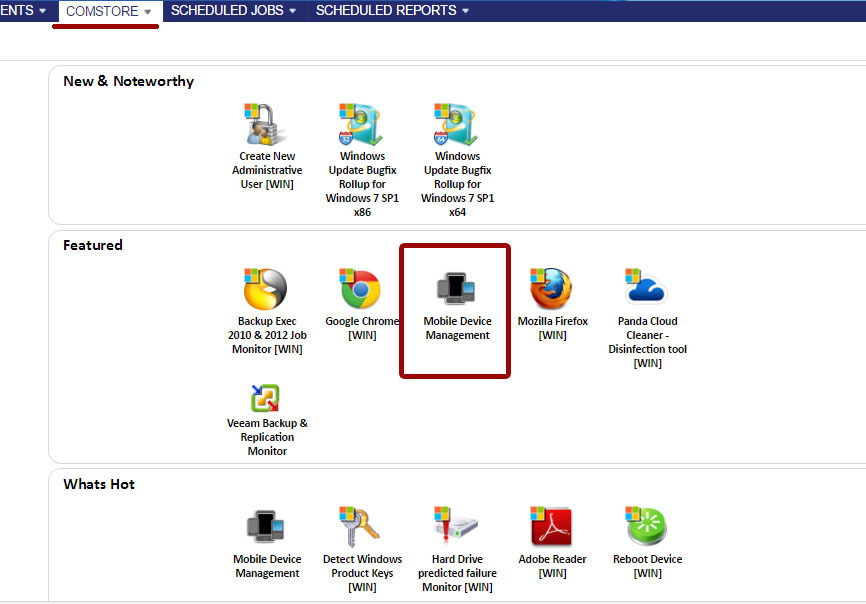
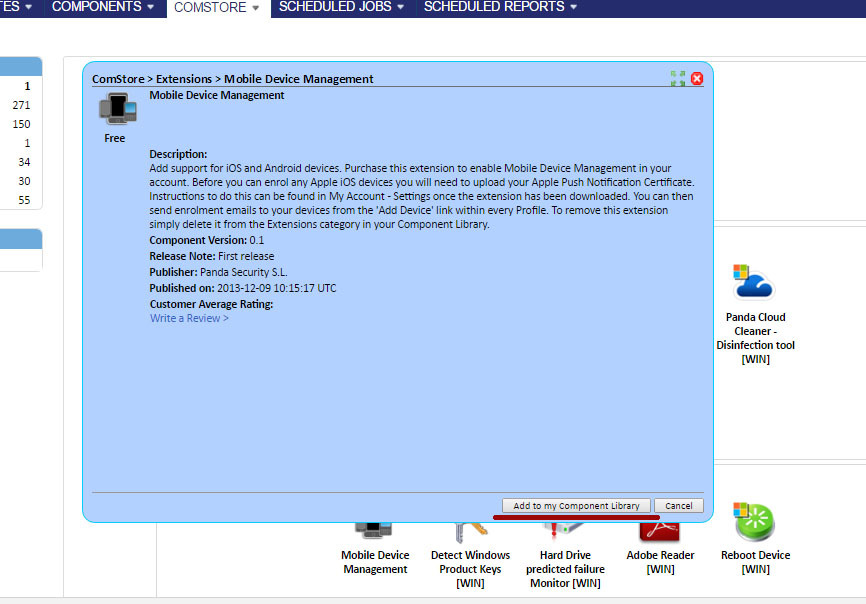
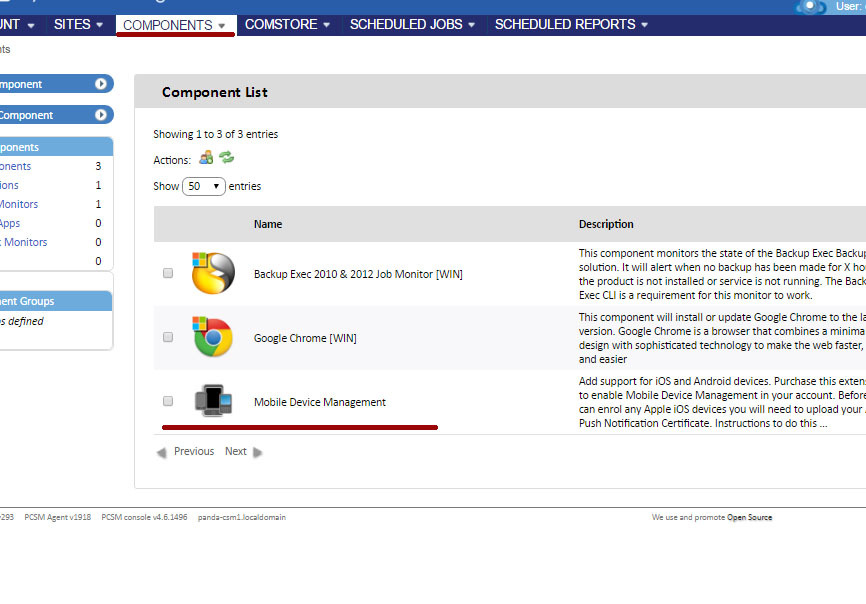
If this component is correctly loaded into your management console, then you can see it in the list of your components in the Components section.
Import Apple Certificate to Console
If you want to manage mobile devices with iOS, then you need to integrate into the management console a certificate generated by Apple for iOS devices, so that you can communicate with the server.
Importing a certificate is a mandatory one-time process. Certificate installation is a requirement from Apple to ensure data integrity, accuracy and confidentiality of all communications between the server and the user's device.
To do this, follow these steps:
- Go to Setup → Account Settings to access Apple certificate settings (Apple Push Certificate section)


Download the certificate signing request (CSR) signed by Panda Security (* _Apple_CSR.csr)
- Upload the CSR file to the Apple Push Certificate Portal .
To access the Apple Push Certificate Portal , you must have an Apple account. Any iTunes account will suffice for this. However, if you want to generate new Apple credentials, go to https://appleid.apple.com/ , click Create an Apple ID, and follow the on-screen instructions.
Go to https://identity.apple.com/pushcert and log in with your Apple credentials. Click Create Certificate and follow the on-screen instructions. Download the CSR file that you downloaded in the Panda Systems Management management console.

Download the new Apple signed certificate (.PEM) to your computer.
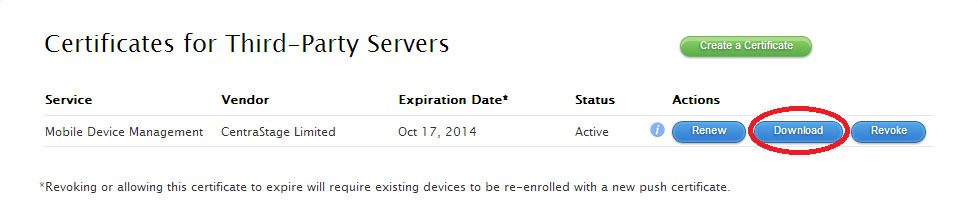
Return to the Panda Systems Management management console. Select the Apple signed certificate (.PEM) stored on your computer and upload it to the management console.
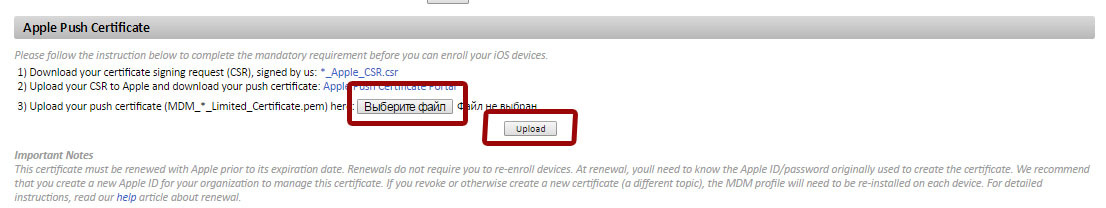
After this, you will receive the following message in the management console:

Adding mobile devices to the management console
Send download link by email
For security reasons, in order to install the Panda Systems Management agent on mobile devices with Android and iOS, you can only send an email to the users of these devices with a direct link to download the agent to Google Play or the Apple Store, respectively, as well as an MDM file containing information about the site ( project) with which this device is connected.
The presence of a separate MDM file is due to the fact that the agent is downloaded for each mobile device from the official store (Google Play or Apple Store), so to place a link to the site in the installation package, you would have to dynamically change the package in the store.
To add devices with Android and iOS in the management console, go to the Sites section, select the desired site (project) and click the New Device button in it.

When you click on the appropriate icon with the name of the operating system, a window opens in which you need to specify the email address of the user of the mobile device where you should send an email to install the agent. You can specify multiple mail addresses separated by a semicolon.
By the way, there is an alternative method for mass installation of the agent on iOS devices using Apple Configurator. But this is a reason for a separate article, but here we will not consider this method.
Device binding to the site
After the Panda Systems Management agent is installed on the user's device, it needs to perform certain actions to bind to the site (project). And there are two options for how this can be done.
Option 1. Scan a QR code
On a PC with the Panda Systems Management management console open with an open site to which the mobile device should be associated, click on the QR code to enlarge it.
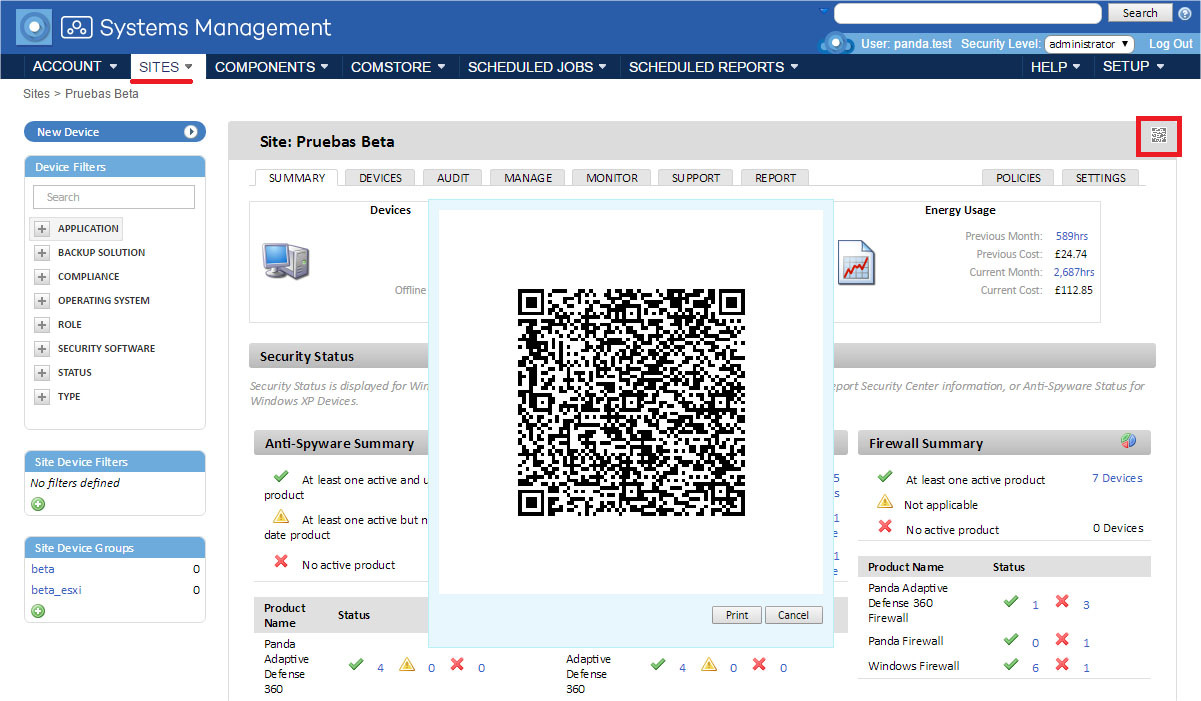
This code can be printed or saved as a file and mailed to the desired users.
In turn, the user must launch the installed agent on his device, click on the wheel icon to initialize the camera and scan the QR code.
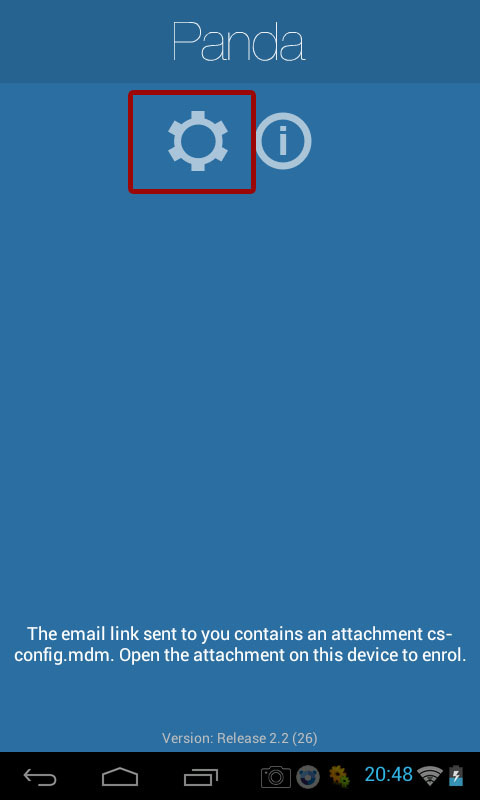
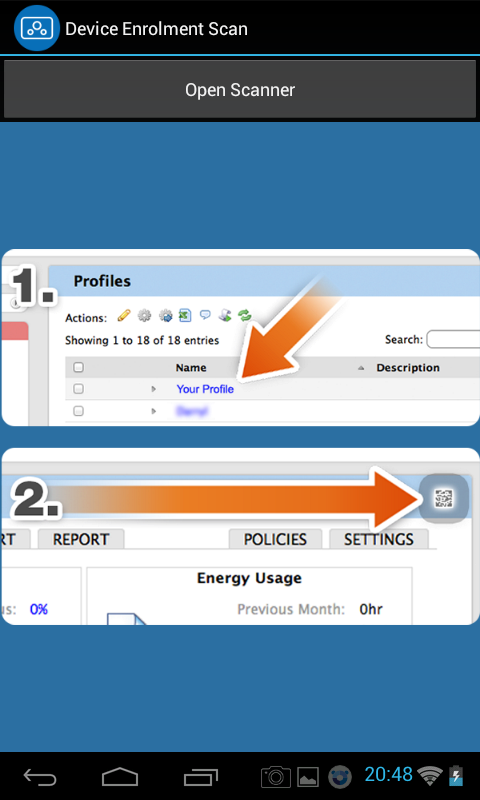

After reading the code, the agent will show the message Connected on the user's device, and the device will appear in the Panda Systems Management management console.
Option 2. Import the embedded MDM file into the installed agent
Remote users or those who do not have a built-in camera on their cell phones can open the MDM file from a letter with a link to the agent installation. After it is downloaded, the agent will show the message Connected on the user's device, and the device itself will appear in the centralized Panda Systems Management management console.
By the way, please note that importing an MDM file is possible only through the email client built into the device.
After performing the above actions, the required mobile devices will appear in your Panda Systems Management console. Now you can apply the corresponding MDM-policy of using mobile devices to them.
Mobile Device Management Policies
To manage and control the use of mobile devices, Panda Systems Management offers a set of policies that allow you to customize tablets and smartphones in such a way as to ensure that users have mobile devices that are ready for use in a corporate environment and that can be integrated into a corporate environment. infrastructure.
During the creation of the MDM policy, the administrator needs to decide whether this policy is mandatory or not. In the latter case, you can allow the user to manually disable the policy from his mobile device. But if the policy is mandatory, then without knowing a special password, the user cannot disable it.
MDM Policy Types
There are four types of MDM policies available in Panda systems Management, each of which affects certain functions and settings of a mobile device:
• Passcode: characteristics of passwords entered by the user on the mobile device to lock / unlock the device, etc.
• Restriction: control access to mobile device resources. Applies only to devices with iOS, because they are not embedded in Android devices
• VPN: VPN settings
• Wi-Fi: Wi-Fi connection settings.
Passcode
| Field | Description |
|---|---|
| Passcode strength | Allows you to set the password difficulty level |
| Minimum passcode length | Allows you to set the minimum length of user passwords. |
| Minimum Number Of Complex Characters | Allows you to set the minimum number of non-alphanumeric characters to be used in passwords. |
| Maximum Passcode Age | Allows you to set a maximum password expiration date. |
| Auto lock | Allows you to configure the time interval after which the automatic blocking of the mobile device is activated. |
| Passcode History | The device keeps a history of passwords used by the user to prevent the user from reusing the old password when creating a new one. |
Restriction
| Field | Description |
|---|---|
| Restrictions on using devices with iOS | |
| Allow use of camera | Allows use of the camera. If you turn off this option, the cameras will be completely disabled, and the icons will be removed from the main page. Users will not be able to take photos, videos or use FaceTime. |
| Allow installing apps | Allows installation of applications. If you turn off this option, the application store will be disabled, and its icon will be removed from the main page. Users will not be able to install or update any applications using the Apple app store. |
| Allow screen capture | Allows users to take screenshots of the display. |
| Allow voice dialing | Allows users to use voice dialing. |
| Allow facetime | Allows users to make or make FaceTime video calls. |
| Allow automatic sync when roaming | Devices in roaming will be synchronized only when the account is available to the user. |
| Allow siri | Permits use of Siri. |
| Allow Siri while locked | Allows you to use Siri when the device is locked. |
| Allow Passbook notifications while locked | Allows you to use Passbook when the device is locked. |
| Allow in-app purchases | Includes the ability to purchase from applications |
| ITunes users password for all purchases | Requests an iTunes password for each download. |
| Allow multiplayer gaming | Allows play in multiplayer mode. |
| Allow adding Game Center friends | Allows users to add Game Center friends. |
| Show Control Center in lock screen | Allows users to connect to the Control Center (Control Center) when the device is locked. |
| Show Notification Center in lock screen | Shows the Notifications Center when the device is locked. |
| Show Today view in lock screen | Shows the Today view widget from the Notification Center when the device is locked. |
| Allow documents from managed apps in unmanaged apps | Allows users to share (and use them) data from a corporate application to a personal application that was not provided by the company. |
| Allow documents from unmanaged apps in managed apps | Allows users to share (and use them) data from a personal application to a corporate application that was provided by the company. |
| Access to applications | |
| Allow use of iTunes Store | Allows users to use iTunes Store |
| Allow use of Safari | Allows users to use Safari |
| Enable Safari autofill | Includes auto-complete option. |
| Force Safari fraud warning | If this option is enabled, Safari warns users about visiting fraudulent or dangerous websites. |
| Enable Safari javascript | Allows Javascript |
| Block safari popups | Includes popups |
| ICloud services | |
| Allow iCloud backup | Includes data backup |
| Allow iCloud document sync | Allows document synchronization |
| Allow iCloud Keychain sync | Allows automatic synchronization with iCloud of logins, passwords, bank card numbers, etc. |
| Allow photo stream | Includes photo streams |
| Allow shared stream | Enables stream sharing |
| Security and Privacy | |
| Allow diagnostic data to be sent to Apple | Enables the option to send diagnostic data to Apple |
| Allow user to accept untrusted TLS certificates | Permits the use of untrusted TLS certificates |
| Force encrypted backup | Encrypts backup data |
| Allow automatic updates to certify trust settings (iOS 7) | Allows automatic renewal of trust certificates. |
| Force limited ad tracking (iOS 7) | Allows users to limit ad tracking on the device. |
| Allow fingerprint for unlock (iOS 7) | Allows users to unlock their devices with their fingerprints |
| Content Ratings | |
| Allow explicit music and podcasts | Allows obscene (explicit) music and podcasts |
| Rating Apps | Allows or blocks applications according to the selected rating. |
| Rating Movies | Allows or blocks movies according to the selected rating. |
| Rating TV Shows | Allows or blocks TV shows according to the selected rating. |
| Restrictions on iOS devices controlled via Apple Configurator | |
| Show iMessage | Allows users to use iMessage |
| Allow app removal | Allows Uninstall Applications |
| Allow game center | Allows you to use Game Center |
| Allow bookstore | Allows you to use iBooks |
| Allow Bookstore erotica | Allows users to download media marked as erotic |
| Allow UI configuration profile installation | Allows installation of an interface configuration profile |
| Allow modifying account settings (iOS 7) | Allows users to change their account settings: add or delete email accounts, change settings for iCloud, iMessage, etc. |
| Allow AirDrop (iOS 7) | Allows users to share documents using AirDrop |
| Allow changes to cellular usage usage for apps (iOS 7) | Allows users to disable cellular data for specific applications. |
| Allow user-generated content in Siri | Allows Siri to request content from the Internet (Wikipedia, Bing and Twitter) |
| Allow modifying Find My Friends settings | Allows users to change the "Find my Friends" settings |
| Allow host pairing | Allows devices to connect to other devices. If this option is disabled, the device can only be connected to the host using Apple Configurator. |
VPN
| Field | Description |
|---|---|
| Connection name | VPN Connection Name |
| Connection type | VPN type (L2TP, PPTP, IPSec) |
| Server | IP address of the VPN server |
| Shared secret | The key is shared between the server and the client. |
| User Authentication | Authorization method: password or public / private key |
| Account | User account for connection authentication |
| Proxy type | Proxy to be used with VPN connection |
WiFi
| Field | Description |
|---|---|
| SSID | Sets the Service Set IDentifier |
| Security | Wi-Fi Security Type |
| Password | Wi-Fi password |
| Proxy type | Proxy to be used with Wi-Fi connection |
Creating MDM Policies
To create an MDM policy, you must perform the following steps:
• when creating policies at the account level, select the Account in the main menu, then the Policies tab, and click the New account policy button
• when creating a policy at the level of the required site (project): within the specific site, click New site policy on the Policies tab

Then specify the name of the policy and its type. Since the MDM policy is added, then the type of policy must be Mobile Device Management
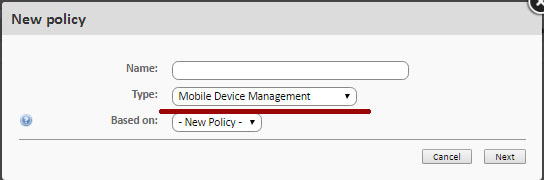
Now it is necessary to determine whether this policy is mandatory for users or not. To do this, you must select the value of the option Remove policy to remove this policy if the policy is optional, or Require password to remove this policy to make this policy mandatory for users (at least for those who do not know the password, which you can immediately configure).
After that, you will need to add policy settings by clicking the Add a setting button.
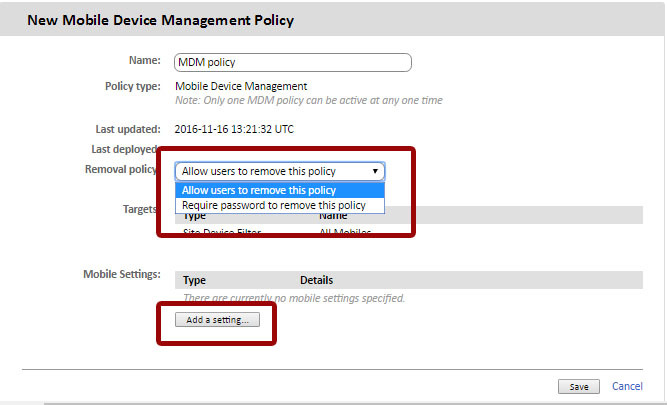
When adding policy settings, you must select the type of MDM policy and configure the corresponding options.
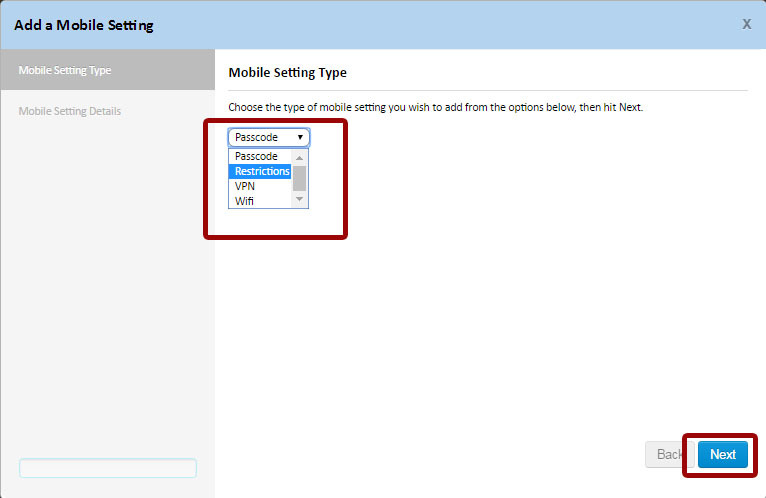
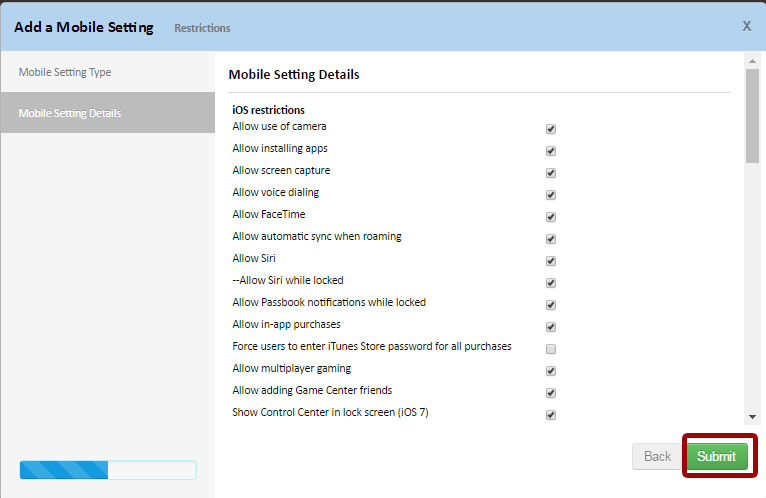
After that, you need to save the MDM policy. To start applying it, you need to activate and apply it by clicking on the Push changes button ...
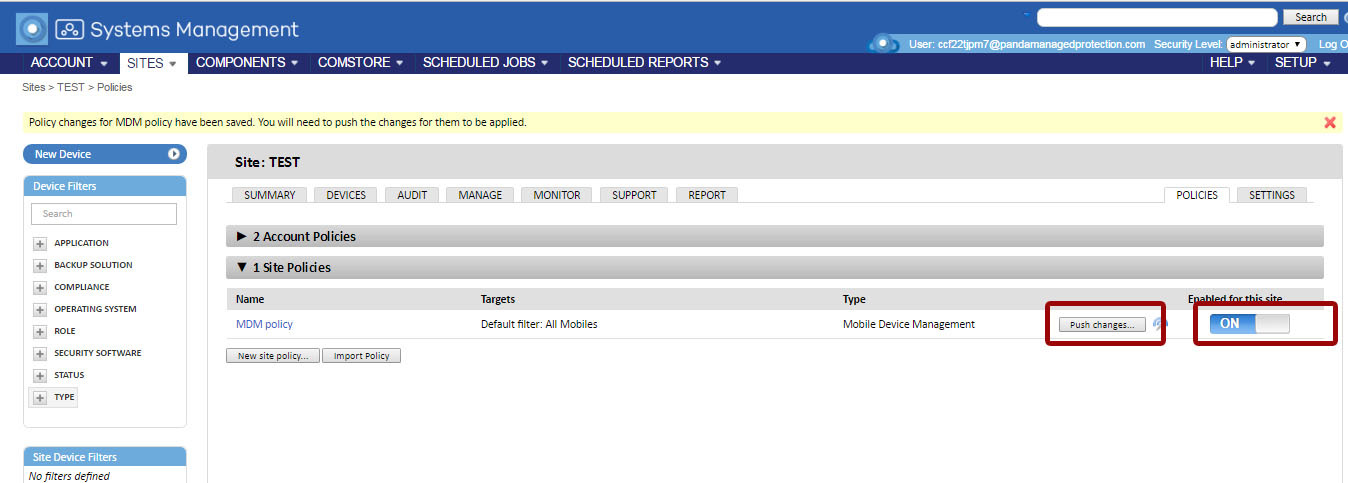
Tools for remote mobile device management
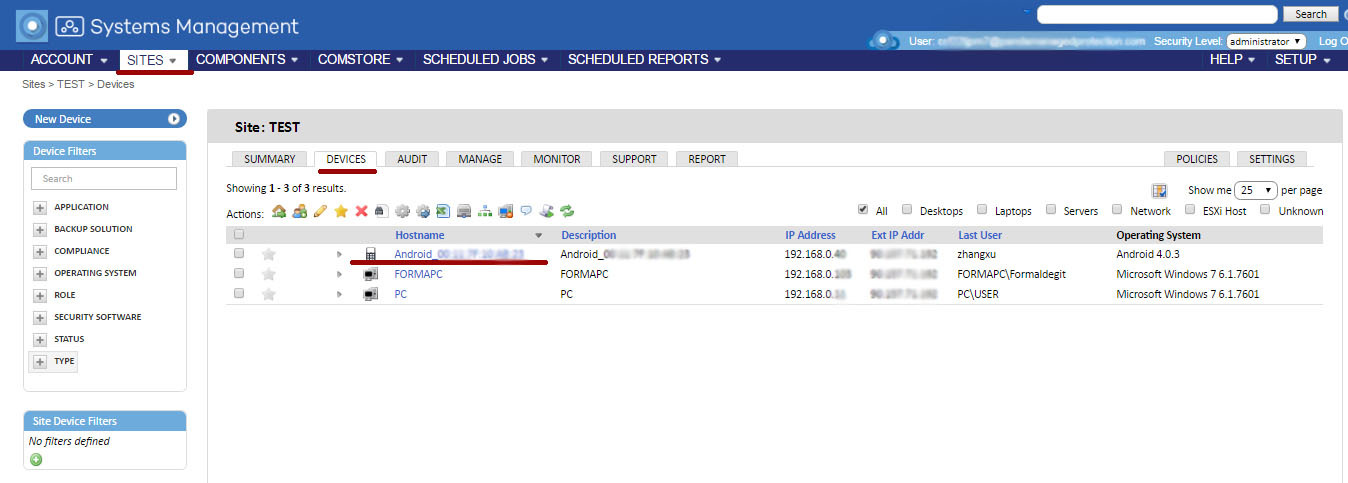
The mobile device management functions in the Panda Systems Management management console are available only at the device level, i.e. for the selected device. To do this, in the Sites section, open the required site, and then go to the Devices tab.

In the device list, select the desired mobile device, after which the list of bookmarks and the set of icons in the Actions toolbar will automatically change, offering various actions that can be applied to the selected device.
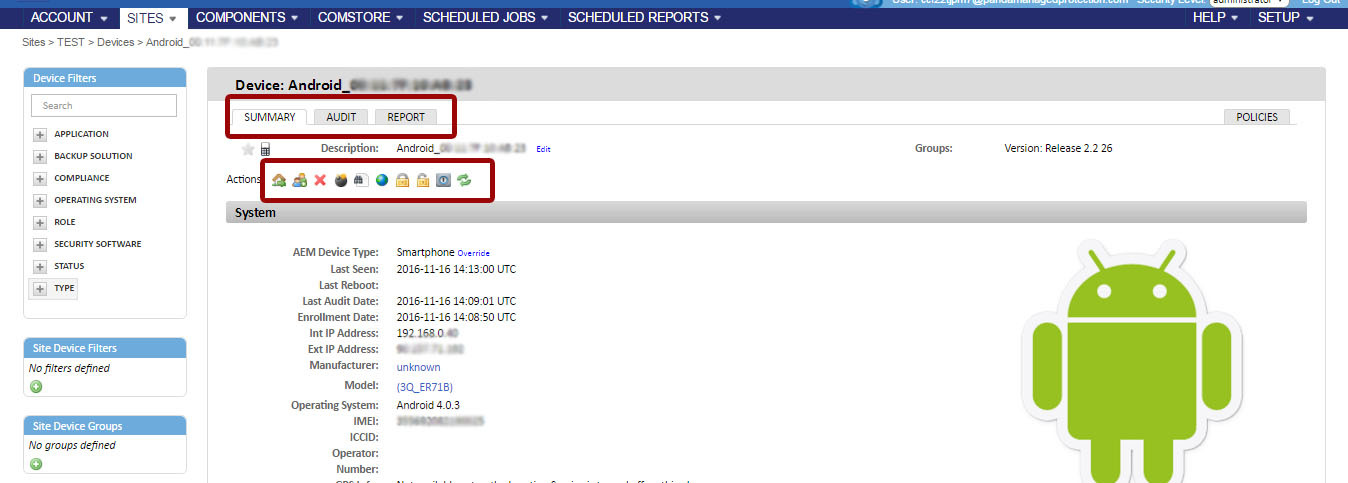
The following specific management tools are available for mobile devices in the Actions toolbar:
Device Wipe
This function performs a remote reset of device parameters to factory settings, preventing data theft in case of loss or theft of the device, as well as its malfunction. But note that in this case all user data (programs, defined configurations, modifications) stored on this device will be deleted on the device. Thus, the device will return to the state in which it came from the manufacturer’s factory.
Geolocation (Location)
This function shows the geographical location of the device on the map. The coordinates of the device are collected in various ways depending on the resources available on the device. The accuracy of determining the coordinates strongly depends on the system. Below are the technologies used to obtain coordinates (in descending order of accuracy):
• GPS (Global Positioning System)
• WPS (Wi-Fi Positioning System)
• GeoIP
By the way, GeoIP can report the location of the device, which will be completely different from the real location of the device.
Device Lock (Device Lock)
This feature locks the device and turns off its screen until the correct PIN code is entered (if configured). This feature is very useful if the device is lost or stolen.
Device Unlock (Unlock Device)
This feature unlocks a locked device (it resets the security PIN if the user forgot it).
Password Policy
This function works in conjunction with the device lock function of the Device Lock, since forces the device owner to set a password (PIN). If this option is enabled, the administrator will be able to block the device if it is stolen, asking the thief for a PIN code if the device is turned on.
This function sends the user a remote request for the installation of a PIN code, but it does not allow the administrator to install this code in the Panda Systems Management management console itself.
Audit
This feature works in the same way as, for example, for devices with Windows, and it is fully integrated into the management console.
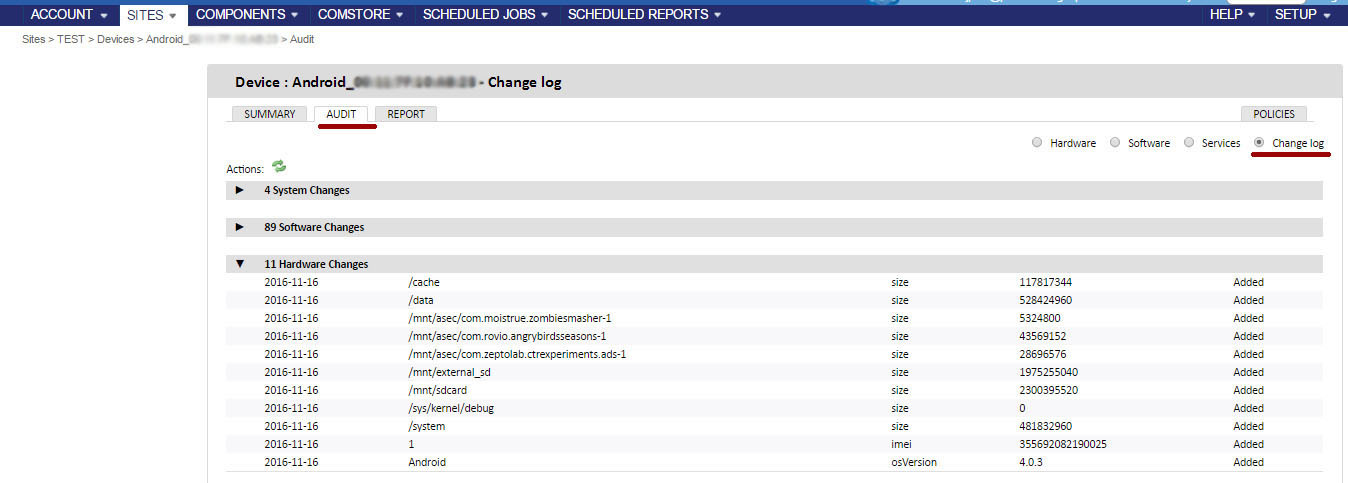
The agent collects from the device on which it is installed all the information about the hardware and software, and also reports any changes to the server, which is displayed on the Audit tab.
The Hardware section shows the following information about mobile devices:
• Operating system and version
• Device Model
• ICCID (a unique number that identifies the SIM card)
• SIM card operator
• Phone number of the SIM card
• Memory size for data storage (internal memory and SD card)
• Network adapters installed on the device (usually Wi-Fi)
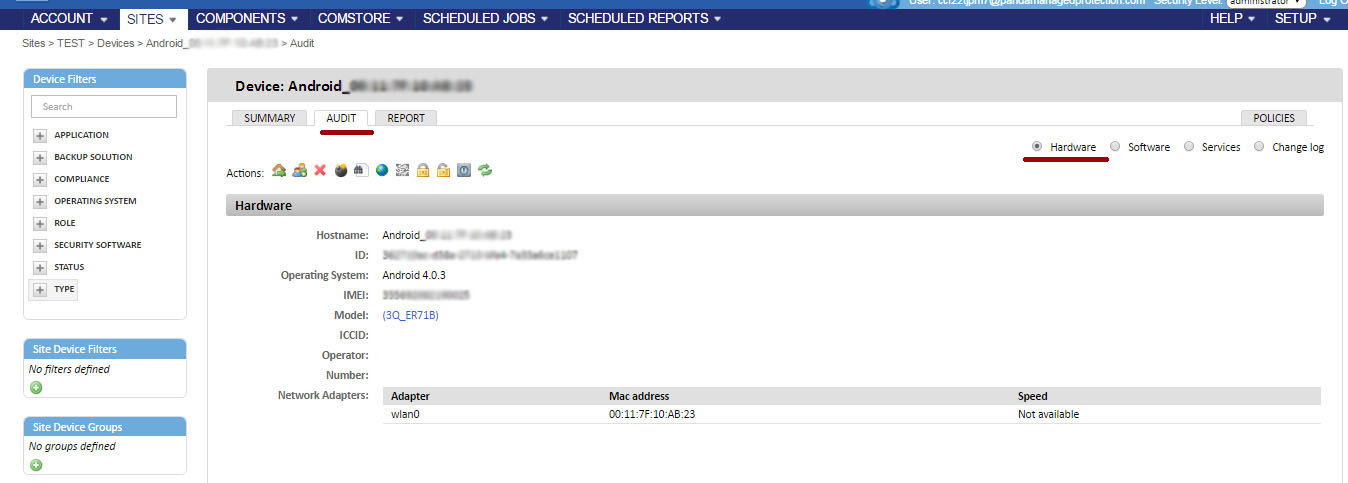
The Software section shows all the packages installed on the device.
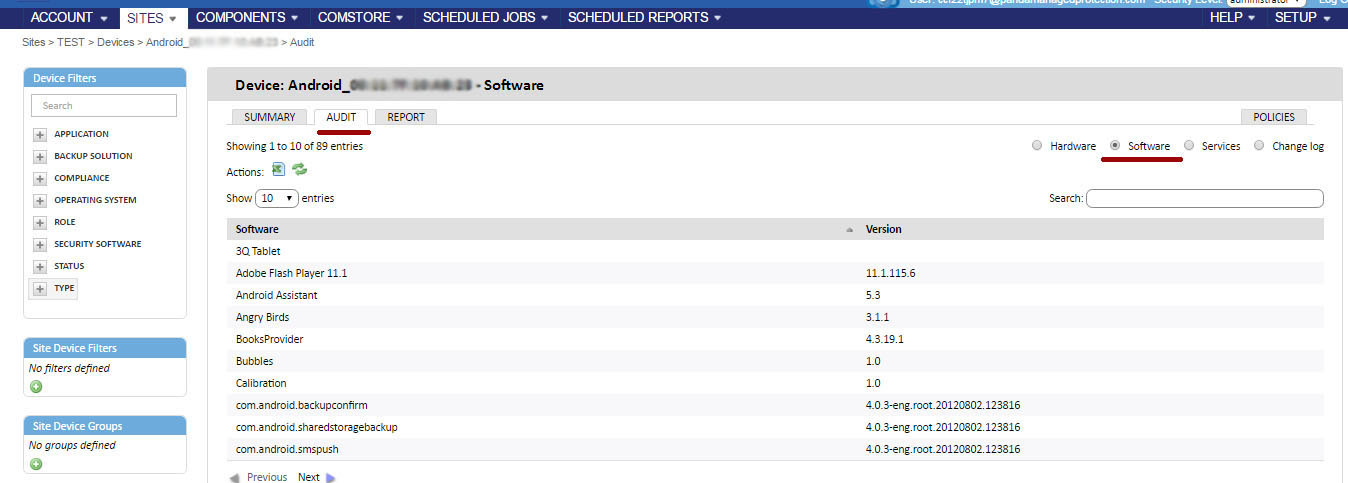
The Changelog section shows all changes in hardware and software that have occurred on the device.
Report
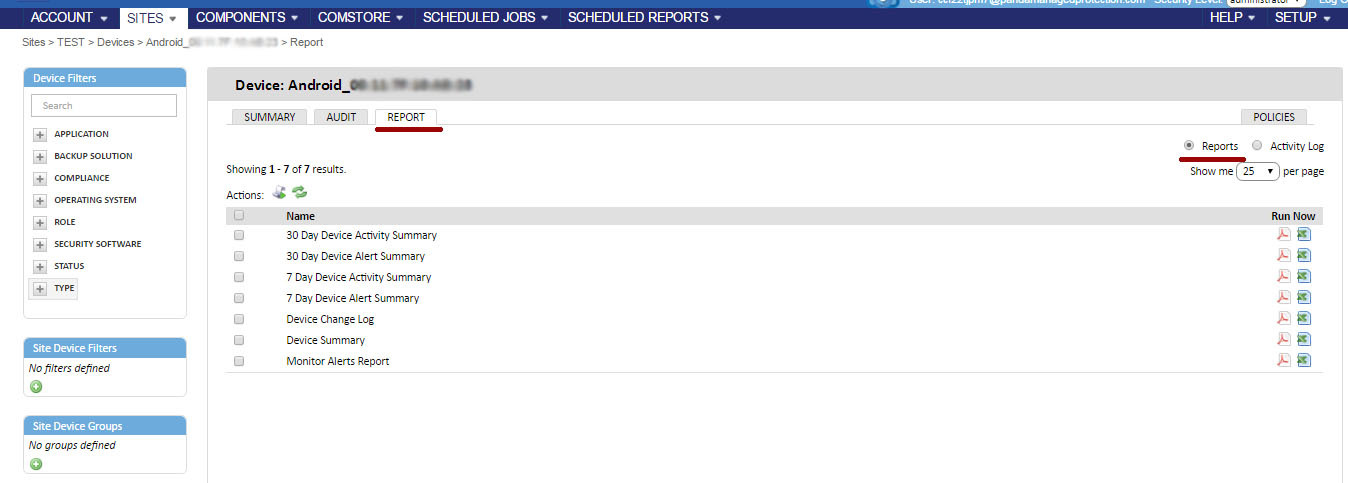
Reports are displayed on the Report tab and their composition depends on the type of device. For example, you can get a report on the activity of the device for the last 7 or 30 days, the history of the monitoring system on this device, changes on the device, general information on the device, etc.
Reports are available in PDF and XLS.
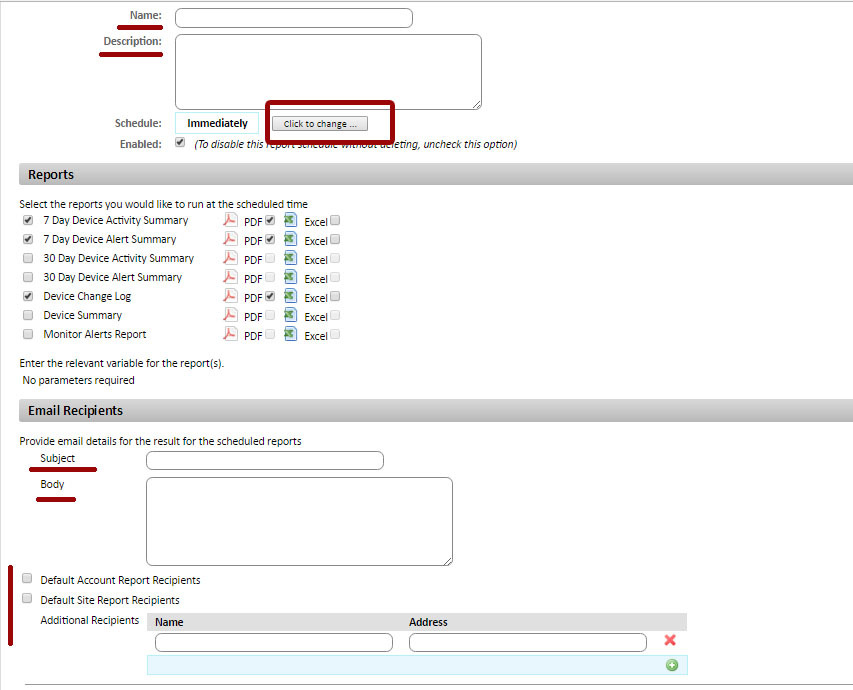
In addition, you can schedule the execution of the required reports for this device. To do this, select the required reports with a checkmark and click on the appropriate icon in the Actions toolbar.

As a result, a window will open with setting up a task for automatic sending of reports. In this window you can configure the following parameters:
• Task name and description
• Schedule for sending reports (right now or on a specific day / time, daily, monthly, on certain months and on certain days of the month, annually)
• List of sent reports and their format
• The subject and content of the letter in which these reports will be sent
• Recipients of this email with reports (you can select standard recipients of reports on an account and / or this site, as well as add other recipients with one click)
Remote software installation on iOS devices
Another useful thing that can be done using the Panda Systems Management RMM service on mobile devices is the centralized remote installation of the required software on smartphones and tablets with iOS, which is downloaded from the Apple Store. There are some peculiarities here, so we will tell you how to do this in a separate article.
Remote software installation on Android devices is not yet supported.
That's all. In this article, we showed the main functions of an RMM mobile device management solution using the example of Panda Systems Management. Some useful things remained outside the scope of this article for the sole reason that the possibilities of RMM in terms of MDM are quite wide, and therefore it is difficult to tell everything in one article. So questions not considered today will be left for our next articles.
Conclusion
Mobile devices have a lot of advantages, which are primarily associated with their mobility. It is a sin not to use such opportunities for solving official tasks. But even greater sin is unsafe and without proper control. And if practically everything is clear with the management and security of traditional workstations and laptops, many aspects of the centralized management and control of smartphones and tablets running Android and iOS are still beyond complete understanding without relevant accumulated experience.
Often, experience shows that in many enterprises it is officially forbidden to use such devices only because there is no clear policy and, most importantly, appropriate tools for centralized control and monitoring of mobile devices. And in vain.
Modern RMM solutions with MDM functions are just such tools. But to figure out how to use them ... is not difficult.
PS We will continue to publish practical articles on the topic "How to do ...". Please indicate in the short survey which topics you would be interested in. We would appreciate your answers.
')
Source: https://habr.com/ru/post/315574/
All Articles
