Vulnerability of old Ubuntu through an audio file played by 1975 processor emulation
Vulnerability and logical separation error settled in the gstreamer player versions 0.10.x for the Nintendo Entertainment System music files , said Chris Evans on his cybersecurity blog. The vulnerability of the system allows to obtain stable access to the use and circumvention of 64-bit ASLR , DEP, and so on. This was made possible thanks to the support of turing-full scripting music files inside the player. The vulnerability lies in the support of backward compatibility.
The vulnerability is affected by Ubuntu of the old, still supported LTS version 12.04.5. In subsequent versions, new glibc is used, and the exploit in the system no longer works.
What is a
The author of the analysis gives a screenshot of the exploit call.
')
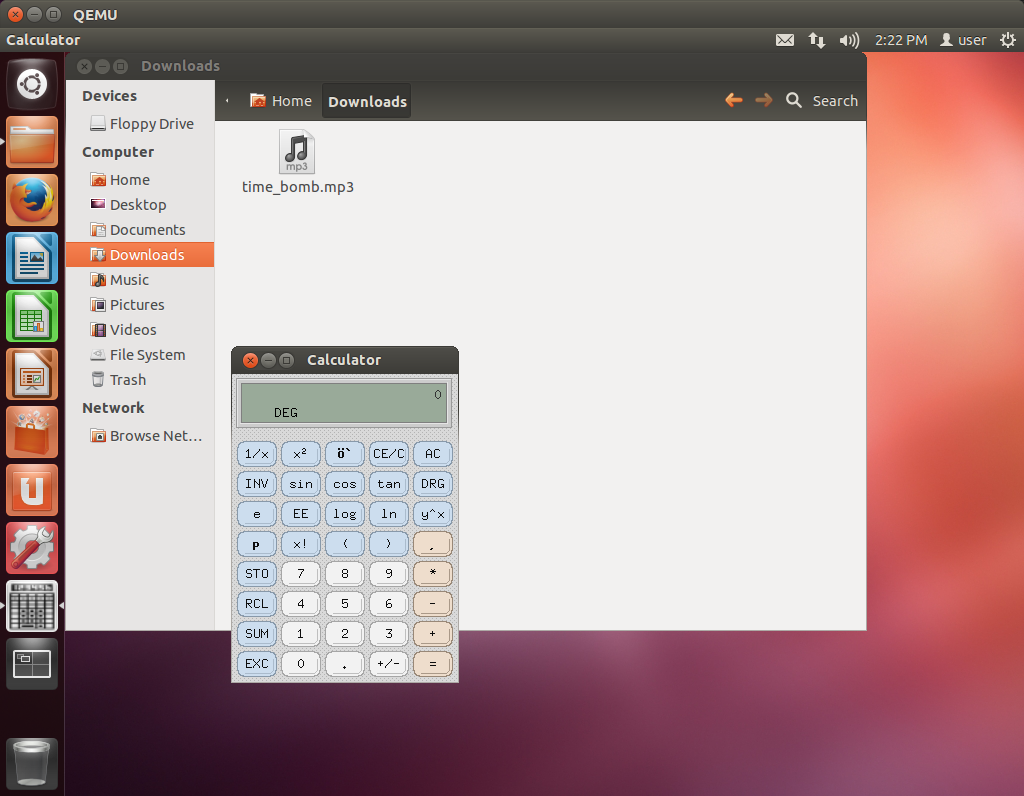
The activation process takes place without initializing the infected file; to do this, just go to the folder with it.
There is a bug in the sound decoder file
libgstnsf.so from the gstreamer-0.10 distribution, which is used in the system by default for all tasks related to sound. Ubuntu 14.04 also has this decoder, but by default in most cases gstreamer-1.0 .During the installation of Ubuntu, the system as if, by the way, asks if the user wants to work with mp3-files. Many additional packages are installed after a positive response, including plugins from the Bad package - those that do not always please with quality: they do not have revisions of the code, maintainer, documentation, and so on.
How does the attack
An exploit abuses the vulnerability of the plugin to play NSF music files. These audio tracks are not like the usual tracks played by a personal computer.
NSF format files are played by the NES console processor emulator and real-time audio hardware. In addition, inside the NSF file there may be a set of instructions. To play it, the vulnerable audio player emulated a forty-year-old processor. There are two players in the vulnerable version of Ubuntu, but there is no error in the second
libgme .The
gstreamer plugin creates a virtual 6502 processor hardware environment and plays music by running some of the code on the emulator. It then reads the resulting values from the virtual audio registers and renders audio samples based on them.The NES sound format is a music file standard that compresses NES game music for playback. It contains the script language that is used to trigger the vulnerability. When you open an NSF file on an infected Ubuntu system, it finds its way to the
libgstnsf.so file through a music player and the gstreamer multimedia framework.Those interested in the example can download the audio file from Castlevania 2 cv2.nsf . If your Linux supports this format, the sound is
totem cv2.nsf by a command like totem cv2.nsf . This tiny file of 17,264 bytes contains a small program - the samples will fit in this way. If the system does not recognize this format, it will offer to download the missing plugin.The plugin works in the process of emulating a real 6502, as in NES for receiving output music and somewhere here there is a vulnerability. So it's not just about multilayer backward compatibility for playing incomprehensible music file formats, but also emulating a program for eight-bit from the 1970s.
What methods can use this vulnerability:
- Forward exploit as an attachment to the letter. If the victim downloads and opens files, his system is at risk. Many Linux configurations do not know how to work with an NSF file - so you can rename it to mp3. Most
gstreamerbased media players will ignore the file extension and apply automatic format detection to load the corresponding decoder to it. - Partial drive-by download . Using, in some sense risky, downloading files through Google Chrome, it is possible to dump files into the downloads folder of the victim’s system when a user visits the “wrong” web pages. When the download directory is later opened by the file manager, the software tries to show icons to files with system-understandable extensions.
- Full drive-by download. With a similar unsafe download through the Google Chrome browser, there is a way for a possible complete download-by-download. Chris promised to tell about it in the next article of his blog.
- Attack based on USB drive. If you open the USB flash drive in the file manager, it will again try to draw the file icons.
Additional explanations
This exploit works equally well when launched in the following programs:
- Totem
- Rhythmbox
- gst-launch-0.10
- Nautilus (can run a subprocess)
Details are described in the relevant sections of Chris's post : an overview of the exploit itself, possible options for vulnerabilities, details of the exploit.
He also writes that the error found is formally related to the 0-day vulnerabilities, but affects only the old Ubuntu 12.04, which was released in April 2012 and is a long-term support-version. It will be supported until April 26, 2017. The problem is rather minor than major. The fact that it came through a 1975 processor remains funny.
PS The vulnerability has already been fixed by members of the Ubuntu team.
Source: https://habr.com/ru/post/315378/
All Articles