The vulnerability of Cryptsetup initialization scripts in Debian: just enough to hold Enter
There is a huge flaw in the security of Debian and several other Linux distributions that has gone unnoticed since version 2.6. All online publications refer to a report by Hector Marco and Ismail Ripoll from the Cybersecurity Group.
The vulnerability is found in scripts that give access to partitioning the system, provided that the procedure is protected using Linux Unified Key Setup (LUKS). Information about the "weak spot" was made public on November 11 during the Security Conference DeepSec 2016 in Vienna. The title of the report sounded from the stage is “Abuse of LUKS for hacking the system”.
Sleep with the door open
A vulnerability in the system gives access to the shell of the root initramfs files. The problem is stable and does not depend on the features of the system or configuration. Burglars can copy, modify or destroy the hard disk and still configure the network for unauthorized data transfer.
')
To activate the vulnerability, you need to boot the system, press "Enter", hold and wait about one and a half minutes. After that, the system will take you to the root shell of BusyBox. First of all, this problem should be solved in library systems, ATMs, airports - wherever the entire boot process is protected with just a password in the BIOS, and from input devices there is a mouse, a keyboard. Cloud environments can also be vulnerable without physical access.
What systems are vulnerable
Debian and Ubuntu with encrypted system partitions — most likely all distributions, but the report’s authors did not check this. Also, all systems with Dracut instead of initramfs are Fedora, Red Hat Enterpise Linux, and SUSE Linux Enterprise Server.
Disk Sharing Protection
Occurs during the installation of the system, when it is proposed to divide the disk, if necessary, and format its parts. After that, the user can select the encryption option for security reasons.
Example
Below is shown what the classic structure of a vulnerable system, protected by just one password, looks like.

It can be seen that
/dev/sda5 encrypted and used as a physical disk in the lubuntu-vg group, which consists of two lubuntu--vg-root logical disks lubuntu--vg-root and lubuntu--vg-swap_1 .What is fraught with
With access to the console and the system reboot option, the hacker is able to launch a shell without root permissions in the initrd environment. Password unlocks the system partition. If one section is password protected, this does not mean that the others are also protected. An attacker can do a lot: from extending the rights of a local user to completely removing all information on the disk.
As it happened
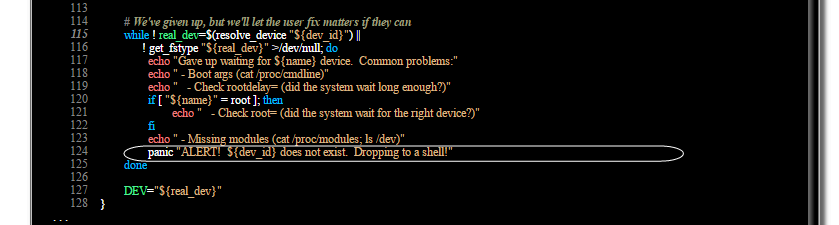
The gap was formed in an incorrect procedure for processing a password check. After three unsuccessful attempts, the system allows you to try again and again.
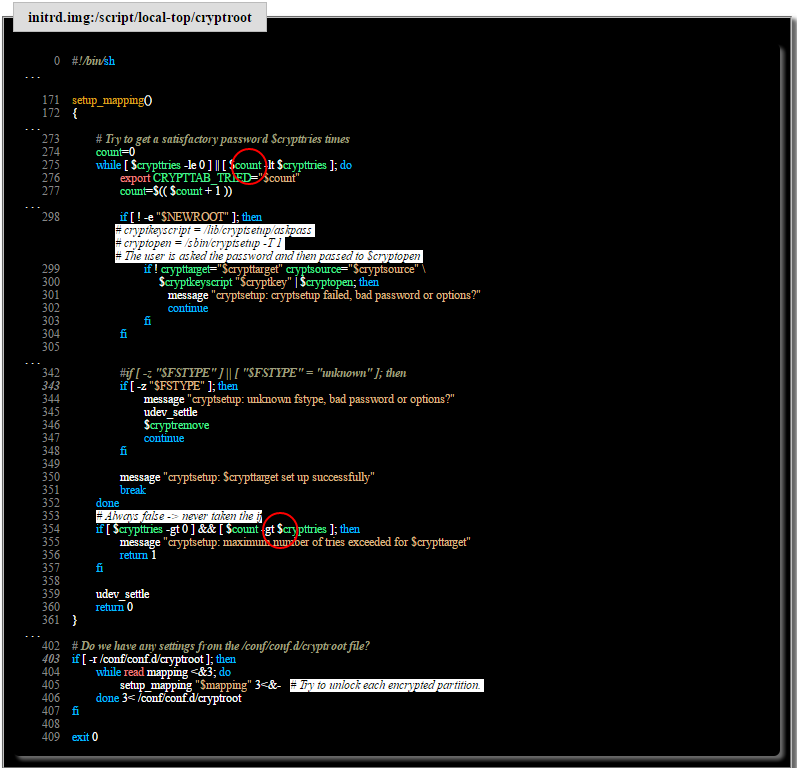
The root of the error is hidden in the file
/scripts/local-top/cryptroot . Once you have exceeded the maximum number of attempts to crash the transitional hardware, you will have access rights to the root level.Inattention Pill
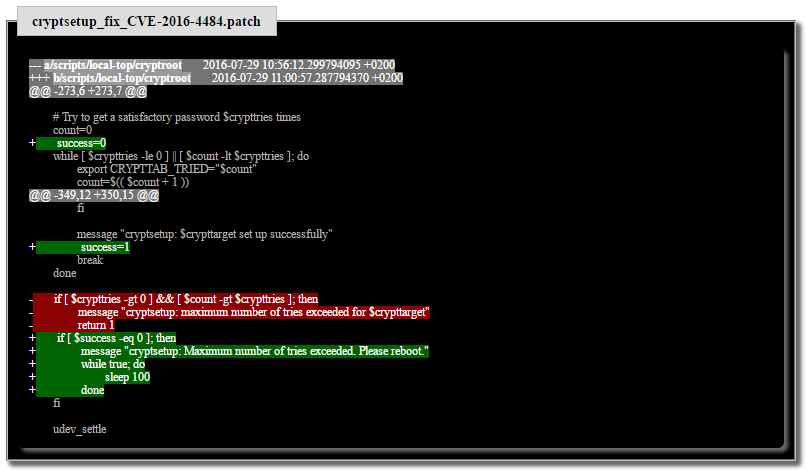
Stop the boot sequence when the number of password entry attempts ends. This patch postpones execution forever. To exit - restart your computer.
What to do
Distribution developers will release fix problems, but you should not wait for caring administrators - patch the system yourself.
In the comments to the post, the demfloro user indicated a possible workaround before the fix: you need to add the
panic parameter to the boot line. More details can be found at the report authors in the “Workaround” section.Source: https://habr.com/ru/post/315376/
All Articles