23 Free Incident Investigation Tools for the Information Security Specialist

Data leaks occur almost every day. According to the data leakage index , since 2013, more than 4,762,376,960 records have been lost or stolen.
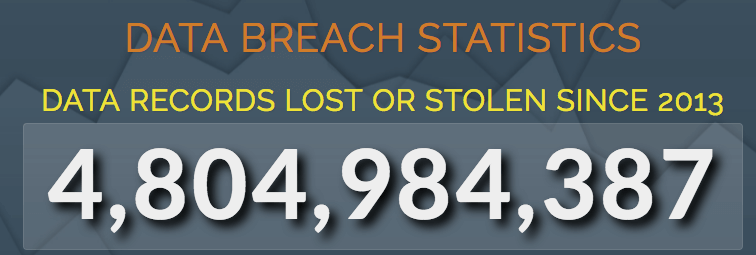
The largest data breaches occurred in:
')
- JP Morgan Chase
- Bank of America
- HSBC
- TD Bank
- Target
- Tumbler
- Home depot
- Myspace
- ebay
- Adobe System Inc
- iMesh
Juniper Research suggests that by 2019 the damage from cybercrime will be more than 2 trillion dollars. Therefore, the demand for forensic analysis will continue to grow.
Software tools are the best friends of the system administrator, and using the right tool will help you work faster and more productively.
Investigation of incidents is not an easy task, because you need to gather as much information as possible in order to secure evidence and develop a mitigation plan. Below, I will describe some useful incident investigation tools. Most of them are free!
List of tools:
- Autopsy
- Encrypted Disk Detector
- Wireshark
- Magnet RAM Capture
- Network miner
- NMAP
- Ram capturer
- Forensic Investigator
- FAW
- Hashmyfiles
- USB Write Blocker
- Crowd Response
- NFI Defraser
- ExifTool
- Toolsley
- SIFT
- Dumpzilla
- Browser History
- ForensicUserInfo
- Back track
- Paladin
- Sleuth kit
- CAINE
1. Autopsy
Autopsy is an open source and GUI-based program for efficient forensic investigation of hard drives and smartphones. Thousands of people use Autopsy to figure out what really happened to the computer.
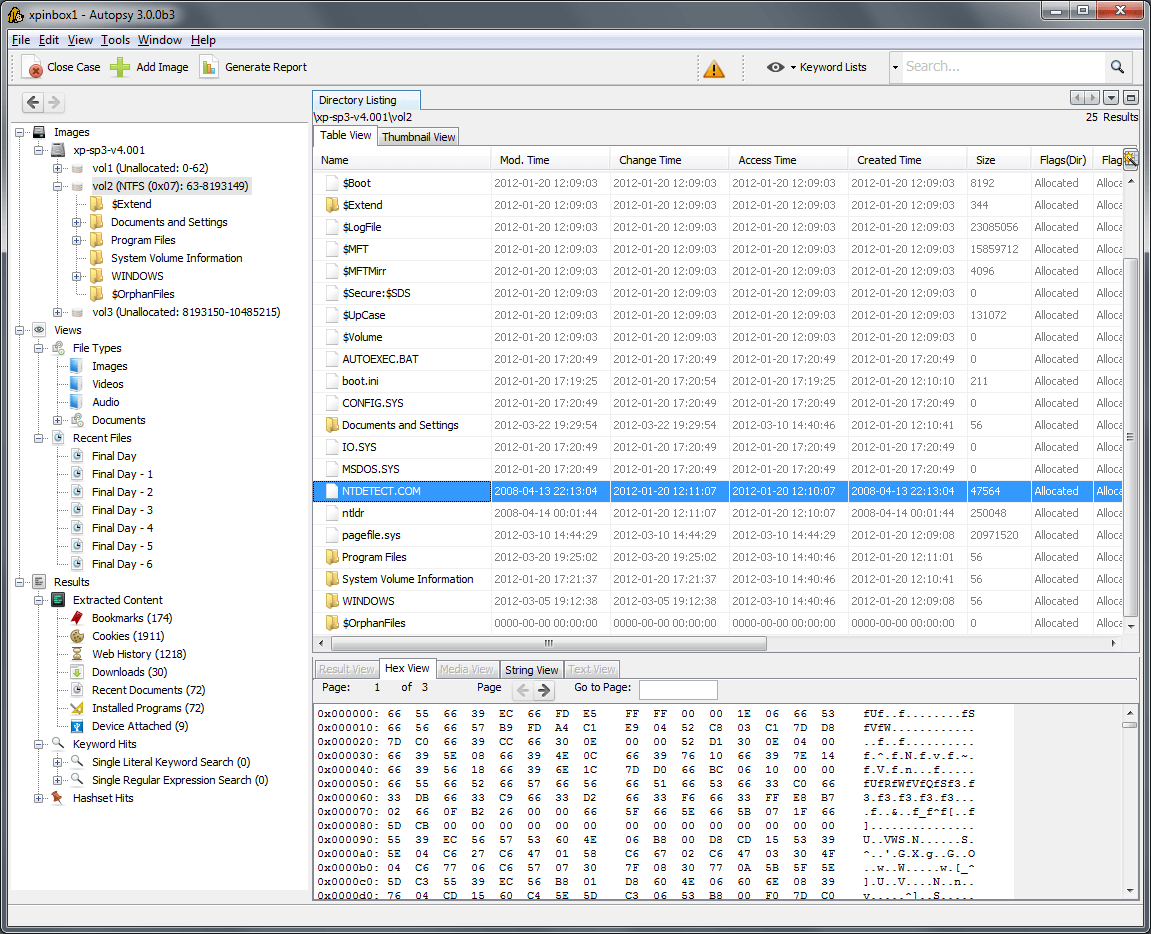
Specialists of large companies and the military widely use Autopsy in their work. Below are some of the features of Autopsy:
- email analysis;
- file type definition;
- multimedia playback;
- registry analysis;
- photo recovery from a memory card;
- extracting geolocation and camera information from JPEG files;
- extract network activity data from the browser;
- display of system events in the graphical interface;
- chronological analysis;
- extract data from Android devices: SMS, call log, contacts, etc.
Using the tool, you can generate reports in HTML and XLS formats.
2. Encrypted Disk Detector
Encrypted Disk Detector can help analyze encrypted hard drives. The program works with partitions encrypted with TrueCrypt, PGP, Bitlocker, Safeboot.
3. Wireshark
Wireshark is a network packet capture and analysis tool that helps you monitor what's happening on your network. Wireshark is useful in investigating a network incident.
4. Magnet RAM Capture
Magnet RAM capture allows you to take a snapshot of RAM and analyze artifacts in memory. The program works with Windows.
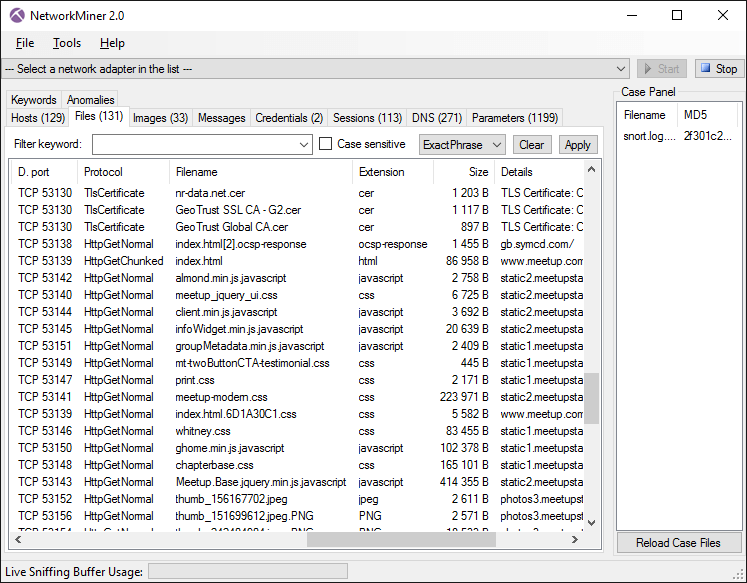
5. Network Miner
This interesting network forensic tool for Windows, Linux and MAC OS X allows you to determine the operating system, host name, detect sessions and open ports using a traffic analyzer or PCAP file. Network Miner displays extracted artifacts in an intuitive interface.
6. NMAP
NMAP (Network Mapper) is one of the most popular tools for auditing network and information security. NMAP is compatible with most operating systems, including Windows, Linux, Solaris, MAC OS, HP-UX, etc. The program is open source, so it is free.
7. RAM Capturer
RAM Capturer by Belkasoft is a free tool for dumping volatile computer memory data. The program is compatible with Windows. A memory dump can contain passwords and data for entering email or social networks located on encrypted volumes.
8. Forensic Investigator
If you use Splunk, then Forensic Investigator will come in handy. This application for Splunk performs many functions.
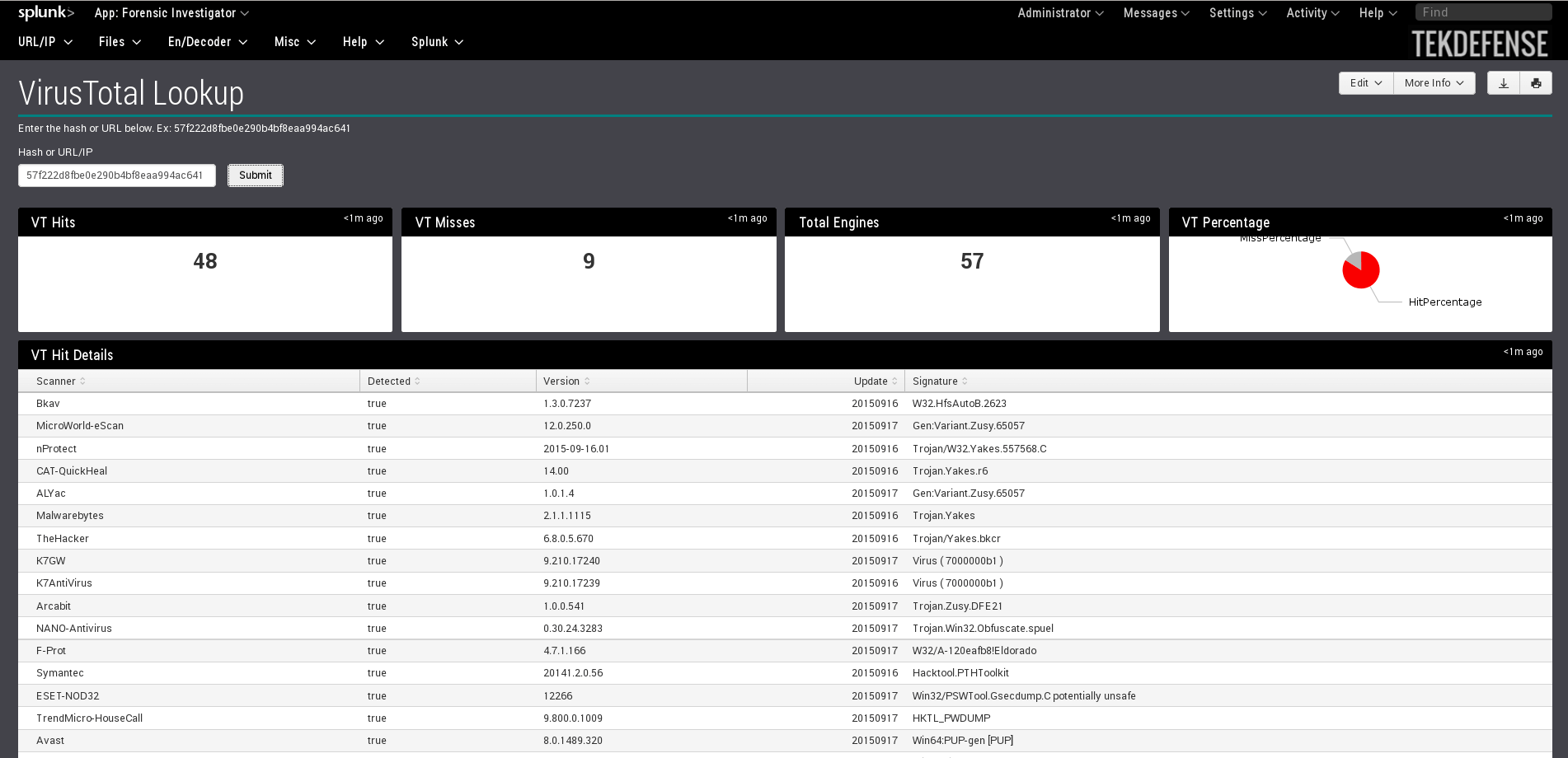
- WHOIS / GeoIP queries;
- Ping;
- port scanner;
- header collector;
- URL analyzer / decoder;
- XOR / HEX / Base64 converter;
- view SMB Share / NetBIOS;
- Virus Total check.
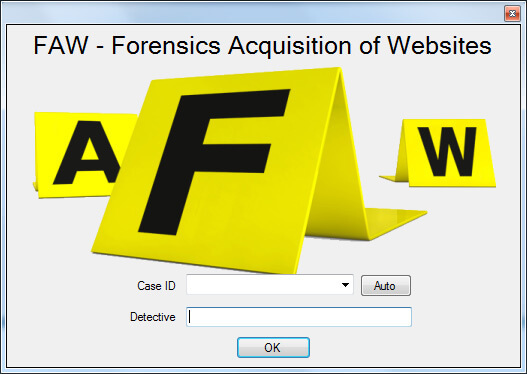
9. FAW
FAW (Forensics Acquisition of Websites) is used to collect data on a web page for further research. The tool implements the following:
- save page partially or completely;
- saving all kinds of images;
- save the source HTML code of the web page;
- Work with Wireshark.
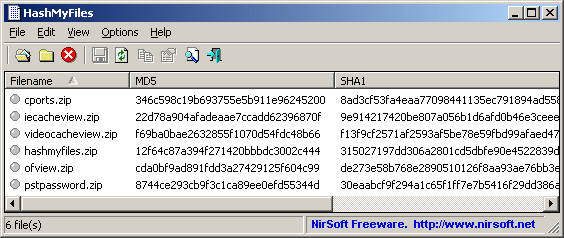
10. HashMyFiles
HashMyFiles helps you calculate MD5 and SHA1 hashes. The tool works on almost all recent versions of Windows.
11. USB Write Blocker
View the contents of the USB drive without leaving fingerprints, metadata, and time stamps. USB Write Blocker uses the Windows registry to protect against writing to USB devices.
12. Crowd Response
Crowd Strike Response is a Windows application designed to gather system information for incident response and increased security. Results can be presented in XML, CSV, TSV or HTML formats using CRConvert. The program works on all 32-bit and 64-bit versions of Windows since XP.
Crowd Strike has other good investigative tools:
- Tortilla allows you to anonymously route TCP / IP and DNS traffic through TOR;
- Shellshock Scanner - check the network for shellshock vulnerabilities;
- Heartbleed scanner - check the network for heartbleed vulnerabilities in OpenSSL.
13. NFI Defraser
Defraser is a research tool that can help you find media files or their fragments in the information stream.
14. ExifTool
Using ExifTool, you can read, write, and edit metadata of various kinds of files, including EXIF, GPS, IPTC, XMP, JFIF, GeoTIFF, Photoshop IRB, FlashPix, etc.
15. Toolsley
Toolsley offers over a dozen useful investigation tools:
- verification of digital signature files;
- file format identification;
- hashing and checking files;
- binary file inspector;
- text encryption;
- data URI generator;
- password generator.
16. SIFT
SIFT (SANS investigative forensic toolkit) is a workstation freely available for Ubuntu 14.04. SIFT is a collection of useful analysis tools and one of the most popular open source incident response platforms.
17. Dumpzilla
Extract all the information you need from the Firefox, Iceweasel and Seamonkey browsers using Dumpzilla .

18. Browser History
Foxton has two interesting tools:
- Saving browser history (Chrome, Firefox, IE and Edge) for Windows;
- View browser history. You can extract and analyze the history of actions in most modern browsers. Results are displayed on an interactive graph, and historical data can be filtered.
19. ForensicUserInfo
Using ForensicUserInfo you can extract the following information:
- RID;
- LM / NT hash;
- change password, account validity period;
- number of logins, dates of unsuccessful attempts;
- groups;
- profile path.
20. Back Track
Backtrack is one of the most popular platforms for vulnerability testing, but it also includes forensic analysis functions.
21. Paladin
PALADIN Forensic Suite is the most popular forensic toolkit for Linux in the world, a modified Linux distribution based on Ubuntu and available in 32- and 64-bit versions.

Paladin includes over 100 tools that are grouped into 29 categories. This is almost all you need to investigate an incident. Autospy is included in the latest version - Paladin 6.
22. Sleuth Kit
The Sleuth Kit is a set of command line tools designed to examine and analyze logical drives and file systems to find data.
23. CAINE
CAINE (Computer Aided Investigate Environment) is a Linux distribution that offers a full-featured expert platform with over 80 tools for analyzing, researching, and reporting actions.

I hope that the above tools will help you cope with the incident and speed up the investigation.
By tradition, I invite everyone interested to take a look at our HOSTING.cafe and choose a virtual server or virtual hosting . Reviews about hosts collected on POISK.hosting .
Source: https://habr.com/ru/post/315278/
All Articles