Telnet and botnet
The recent largest DDoS attack on the DNS servers of the Dyn company on Habré did not go unnoticed . A feature of this blackout is the widespread use of http requests from IoT devices and the open 23rd tcp port used by the telnet service.

It turns out that telnet is alive and well settled on embedded systems and lures. By wicked intent or human thoughtlessness What is this, stupidity or treason? The telnet port was open and completely shattered a huge number of IoT devices, several months before the blackout, but did not take a counter-measure until the thunder struck.
Theoretical minimum
The telnet appeared in the late 1960s , and the first standard with tcp/ip and a virtual terminal dates back to 1983. Naturally, at the time of creation, no one cared about the fact that the data was transmitted in a simple text format. The tcp/ip network protocol was still matured in ARPANET at that time.
Telnet was designed to work between any host (ie, any operating system) and any terminal. Its specification in RFC 854 [Postel and Reynolds 1983a] defines the lowest common denominator terminal, called the network virtual terminal (NVT). It’s not a problem. The user is on the NVT. The server must then map the NVT into whatever terminal type the server supports.
Like many popular Internet protocols, it is also simple to archaic and unsinkable due to its simplicity. And just as often used for other purposes.
(5:574)$ grep -w ^telnet /etc/services telnet 23/tcp # Telnet telnet 23/udp A curious fact, it turns out there is such a thing as telnets , but what is this miracle, I can not say. Even search engines were surprised.
(5:575)$ grep -w ^telnets /etc/services telnets 992/tcp # telnet protocol over TLS/SSL telnets 992/udp Here is the whole simple list of commands:
EOF 236 end-of-file SUSP 237 suspend current process (job control) ABORT 238 abort process EOR 239 end of record SE 240 suboption end NOP 241 no operation DM 242 data mark BRK 243 break IP 244 interrupt process AO 245 abort output AYT 246 are you there? EC 247 escape character EL 248 erase line GA 249 go ahead SB 250 suboption begin WILL 251 option negotiation WONT 252 option negotiation IX) 253 option negotiation DONT 254 option negotiation IAC 255 data byte 255 The telnet supports half-duplex, character-based and in-line input modes, by default the program uses the latter. From man page.
Once the connection has been opened, the TELNET LINEMODE option. If you fail, telnet will support you.
In-band signaling is used - commands and data are transmitted in one stream.
Telnet honeypot
Last year, specialists from a large Czech DNS provider, NIC.CZ, rolled out the honeypot bait and began to monitor traffic.
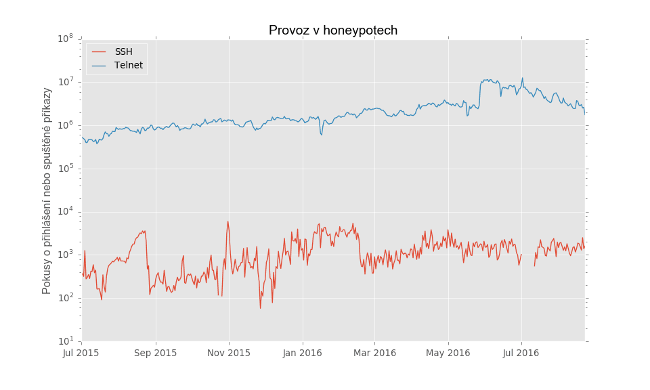
It turned out that telnet traffic is three orders of magnitude greater than ssh traffic. On the vertical scale of the graph, the number of login attempts for telnet and commands ssh for ssh . The logarithmic scale. Clickable
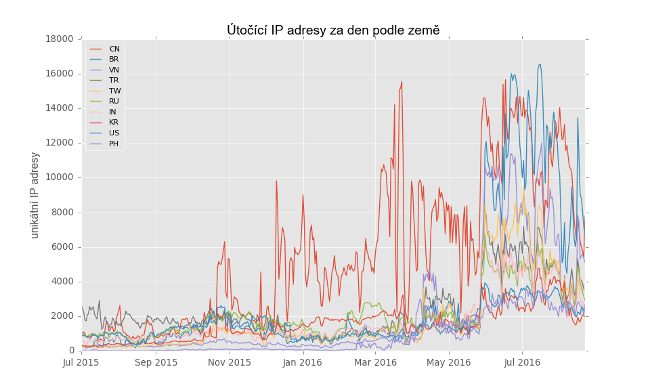
The number of unique IP .

The geography of countries, clickable . Note the coincidence with the result Shodan , below.
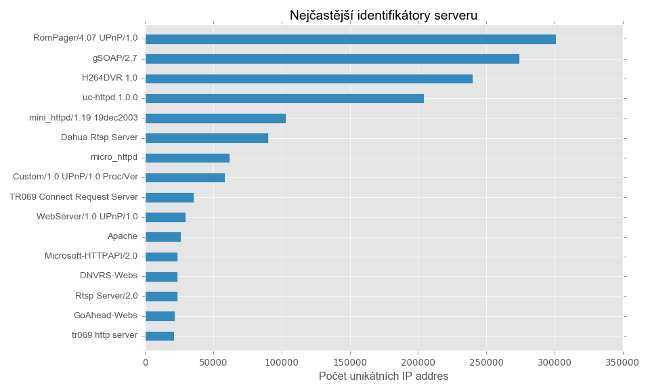
Platform of main devices, clickable .
In the first place, the RomPager / 4.07 HTTP server is a leaky embedded web server , often used in home routers. According to analysts from Allegro Software Development, there may be 75 million . In second place is the popular gSOAP / 2.7 toolkit , and the bronze medal went to H264DVR 1.0 - RTSP (Real Time Streaming Protocol) to the DVR server.
Actually, CCTV cameras are designated by the incoherent Dahua Rtsp Server and also have security problems . Since May 2016, these devices have dramatically increased their activity, at times, 8 thousand unique IP addresses were registered per day.
Despite the local nature of the experiment, the conclusions about the impending large-scale IoT threats seemed to suggest themselves. Having processed data from more than 6 million unique IP addresses , Czech analysts have clearly identified a trend: embedded systems are most vulnerable, especially CCTV video cameras, which often degenerate into a monoculture with the same equipment, stuffing, list of vulnerabilities. The first bell rang quietly and was not heard.
Announce the entire list
Experts from Rapid7, using the infrastructure of their Project Sonar, conducted a global scan of ports around the world , checking the main tcp ports of the IPv4 range. The study turned out to be quite detailed and interesting.
- 15 million hosts with an open telnet port. (Charles!)
- 11 million RDBMS open access hosts
- 4.5 million hosts with open access to print services.
This is how the first ten tcp/ip protocols were distributed, by value.
Port Protocol Number Percent 80 HTTP 76,266,507 19.89% 443 HTTPS 50,507,072 13.17% 22 SSH 21,692,582 5.66% 21 FTP 20,375,533 5.31% 25 SMTP 19,888,484 5.19% 8080 http-alt0 17,477,357 4.56% 23 telnet 14,871,682 3.88% 53 DNS 12,602,272 3.29% 143 IMAP 11,467,158 2.99% 110 POP3 11,073,439 2.89% All thirty protocols in the table ..
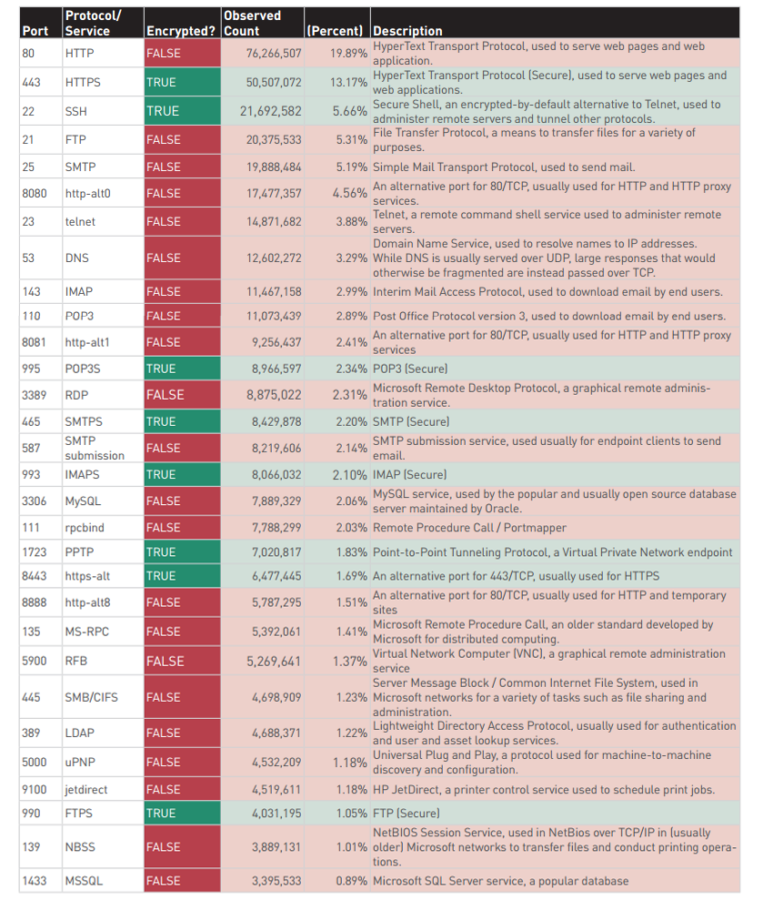
Seventh overall, who would have expected? And if you combine all http* into one category, then telnet will be in fifth place at all! As you can see, the gap with ssh quite small. It was the second bell , but nobody heard it.
That said, we can’t be frustrating and worrying. According to our scans, there are over 14 million devices that are on the internet today.
100,500 vulnerable CCTV camcorders
Experts from Flashpoint followed the trail of the Mirai botnet through the Internet to detect the interesting properties of CCTV cameras XiongMai Technologies and Dahua . As Mikhail Zadornov likes to say “hold onto a chair, otherwise you will fall”.
As of October 6, 2016, more than 515 thousand devices with a web server uc-httpd 1.0.0.0 are simultaneously subject to CVE-2016-1000245 and CVE-2016-1000246 .
Vulnerability CVE-2016-1000245 - it's just a guard. All devices have the same root password xc3511, which cannot be changed as there is no passwd command on the system. The telnet service is enabled and cannot be disabled from the settings, except to delete the init script from /etc/init.d/rcS .
/etc $ cat passwd root:absxcfbgXtb3o:0:0:root:/:/bin/sh /etc $ cat passwd- root:ab8nBoH3mb8.g:0:0::/root:/bin/sh All internet-capable XiongMai Technology boards running the DVR / NVR CMS (Also known as
NetSurveillance) enable the telnet service to run on the primary ethernet interface. This service
is run via / etc / rcS and cannot be disabled. The user "root" has a hardcoded and immutable
password of xc3511. Do not have the "passwd" tool installed and the root
password cannot be changed from command line nor from the web interface.
Vulnerability CVE-2016-1000246 is not inferior to the first. You can bypass the entry of the account and password, if you go through http://<IP>/DVR.htm .
Many known XiongMai DVRs, NVRs and IP Cameras run "CMS" (also called NetSurveillance) built by XM Technologies. XiongMai Technologies. Bypassed by simply changing the way from http: //_IP_/Login.htm to http: //_IP_/DVR.htm . This allows you to access all camera systems without authentication. Furthermore, there is no logging on the system so user management is not possible. The web-server version on all affected products is the same; “Uc-httpd”. All products currently affected by CVE-2016-1000245 are also vulnerable to the authentication bypass.
I hope that these same XiongMai and Dahua are not installed in our airports.
Results
The telnet turned out to be very tenacious and even decades later after the appearance of ssh no hurry to leave the scene. It is quite suitable, even useful if used for its intended purpose - within the direct line of sight between the client and the server. The fact is, however, that telnet broke free from the server room like a gin from a bottle and has already begun to play pranks. Whose fault did it happen?
From my fence I see it. First , the main fault on the mountain-producers of leaky IoT devices and embedded systems. All these XiongMai and Dahua . Belatedly, but the manufacturer recalls from the sale of IP-cameras . However, a cursory review of the news shows that the PR departments of Chinese companies and employees of the Ministry of Commerce do not eat their bread for nothing.
I know this department! They give passports to anyone! [one]
Secondly , of course, the regulatory bodies are guilty - those who certify them and give a positive conclusion. From the Rapid7 report.
Global energy engineering. It is not a default, but it doesn’t need to be a standard Internet protocol board. Cleartext protocols are “doggedly secondary”. [2]
Thirdly , contractors and integrators who planted the whole world with these CCTV cameras.
If you do not take legislative measures regulating the IT security of Internet irons and video cameras, then the blackouts will become more and more cool, like a kaiju.

PS While typing the text, there was a strong desire to check the home router nmap-ohm and other tools. Checked and calmed down, but apparently not for long.
Used materials
- W. Richard Stevens TCP / IP Illustrated, Volume 1, The Protocols, 1994.
- TCP / IP close-up
- Telnet stále žije - alespoň na „chytrých“ zařízeních
- ↑ From M. Bulgakov's novel The Master and Margarita.
- ↑ Results speak for themselves. Despite all the appeals of the IAB, the IETF and virtually all security experts, mandatory encryption has not yet become the norm when developing Internet standards. Plain text, “just works,” and because of this, security requirements are ignored.
')
Source: https://habr.com/ru/post/315266/
All Articles