The media learned about the new way to intercept passwords and PIN-code from mobile phones
 Most users believe that the PIN-code reliably protects smartphones from unauthorized access. However, the latest developments of enthusiasts and intruders may cast doubt on this fact. Hacking technologies are developing almost faster than security methods.
Most users believe that the PIN-code reliably protects smartphones from unauthorized access. However, the latest developments of enthusiasts and intruders may cast doubt on this fact. Hacking technologies are developing almost faster than security methods.Recently, the media learned about the emergence of new technology hacking personal data of users through a mobile phone connected to a Wi-Fi network.
In the popular blog of SpringSource's former technical director (creator of Spring's Java framework) Adrian Colyer, The Morning Paper has a description of this technology. It works when you enter the PIN code by contact.
To track down the PIN code set, attackers analyze the WiFi signal. In order for a device to be hacked, a hacker must create a remote wireless access point, choosing as his victim, for example, a cafe visitor sitting at a table with a smartphone in his hands.
')
It turned out that the movement of the user's fingers while dialing a PIN code affects the WiFi signal of the device.
Therefore, by changing the signal, an attacker can trace how the numbers change. The position of the user's fingers on the gadget when entering the password creates vibrations of the wireless signal - micro-interference. Specially created algorithms analyze information and select several PIN-code options. During testing of this method, the system offered three possible password options, one of which turned out to be correct. As a result, it was possible to make a purchase using the Alipay payment system.
Thus, almost any smartphone owner who is not afraid to connect to open and free wireless networks can become a victim of hackers. Such an access point, organized by the attacker, can become a “free cheese mousetrap”. Using this technique, you can take possession of passwords from social networks and payment services.
Analysis of changes in the WiFi signal to identify the entered PIN-code is carried out using special software.
The attack was called WindTalker ("Speaker with the wind") - by analogy with the Navajo crypto-Indians.
Unlike other methods of hacking devices, for example, determining passwords by the sound of keystrokes or tracking a user's movement (or computer mouse), this method does not require direct access to the gadget and connection to it via the existing Wi-Fi channels in this zone. Moreover, it turns out that the technology also works for HTTPS connections, or, more correctly, to bypass them.
How it works
In addition to finger movements, the technology takes into account another parameter - how the user holds the smartphone. In aggregate, on the basis of these two parameters, a unique Channel State Information (CSI) pattern is formed in the time series. Only then can the analysis algorithms be applied.
CSI is part of the Wi-Fi protocol and provides basic information about the state of a Wi-Fi signal.
Previously, CSI was used to recognize larger movements and made it possible to determine the presence of a person in a room and capture gestures. Based on this technology, the WiHear system was developed that can recognize mouth movements, that is, read lips. WiKey brought WiHear to a completely different level - now with its help you can not only read lips, but also determine the movements of fingers, hands and keys.The attacker collects the values of the CSI signal Wi-Fi using a malicious access point. To do this, send the corresponding request via the ICMP protocol and receive a set of packets in response. For analysis, it is necessary to ensure a transfer rate of at least 800 packets per second.
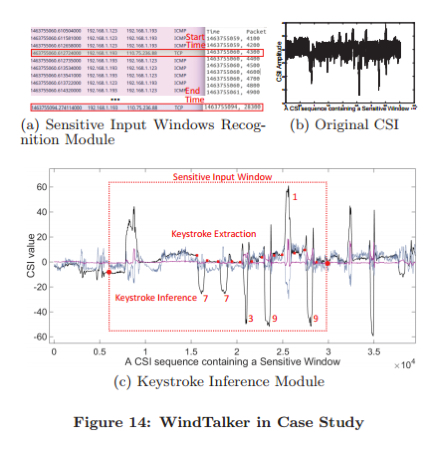
After analyzing the received signal, an attacker can identify the characters typed by the user with an accuracy of up to 68.3%. Accuracy varies by smartphone model, but it can be improved by training the algorithm and obtaining more data.
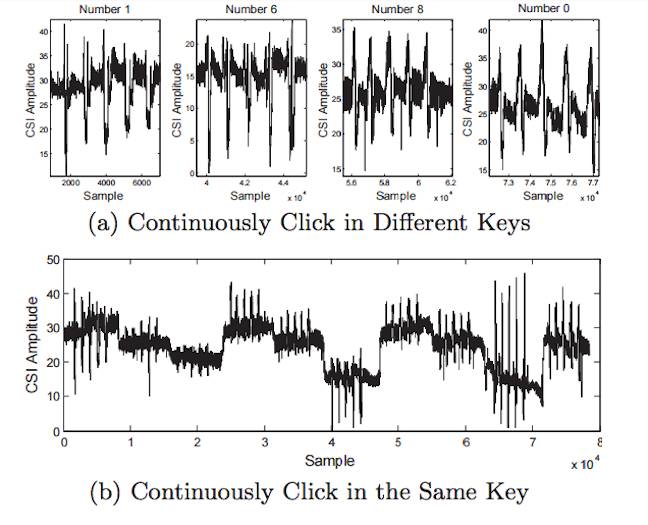
The more attempts the PIN user makes, the higher the recognition accuracy will be, as the array of CSI values in this case grows.
"Thus, the most vulnerable are applications that allow users to try to enter a password multiple times," sums up Adrian Collier.
Predecessors
The calculation of personal data from signals was repeatedly used by various intruders in the creation or development of existing technologies. For example, a smart watch recognized the password with an accuracy of 65%, tracking the movement of the user's hand over the keyboard. With an accuracy of 94%, the microphone of the smartphone, by the sound, determined the sequence of keystrokes on the gadget and so on.
As for the Wi-Fi technology, it was previously considered for use in order to spy on people. One of the developments suggested using Wi-Fi to find people in neighboring rooms, tracking both actions and movements, up to obtaining an image comparable to the video of the cameras.
Previously, the WiKey attack was introduced, allowing CSI to intercept keystrokes on a physical keyboard.
According to the researchers, WiHear is not only provides a vast field of attack, but also provides great opportunities for human-computer interaction.
Source: https://habr.com/ru/post/315242/
All Articles