A little bit about quantum cryptography
Quantum computers and related technologies have recently become increasingly relevant. Research in this area has not ceased for decades, and a number of revolutionary achievements are evident. Quantum cryptography is one of them.
Vladimir Krasavin "Quantum Cryptography"
This article is a prologue to a series of articles and translations on the subject of quantum cryptography.
Indeed, more and more recently we have heard such concepts as “Quantum Computer”, “Quantum Computing” and of course “Quantum Cryptography”.
And if everything is clear in principle with the first two concepts, then “Quantum cryptography” - a concept that, although it has an exact formulation, still remains dark and not quite clear to such people a sort of Hedgehog in the fog.
But before we proceed directly to the analysis of this topic, we introduce the basic concepts:
Cryptography is the science of methods of ensuring confidentiality (the inability to read information by an outsider), data integrity (the impossibility of imperceptibly changing information), authentication (authentication of authorship or other properties of an object), and the impossibility of giving up authorship.
')
Quantum physics is a section of theoretical physics in which quantum-mechanical and quantum-field systems and the laws of their motion are studied. The basic laws of quantum physics are studied in the framework of quantum mechanics and quantum field theory and are applied in other branches of physics.
Quantum cryptography is a communications protection method based on the principles of quantum physics. Unlike traditional cryptography, which uses mathematical methods to ensure the secrecy of information, quantum cryptography focuses on physics, considering the cases when information is transferred using objects of quantum mechanics.
Orthogonality is a concept that is a generalization of perpendicularity for linear spaces with scalar product introduced.
Quantum Bit Error Rate (QBER) - the level of quantum errors.
')
Quantum physics is a section of theoretical physics in which quantum-mechanical and quantum-field systems and the laws of their motion are studied. The basic laws of quantum physics are studied in the framework of quantum mechanics and quantum field theory and are applied in other branches of physics.
Quantum cryptography is a communications protection method based on the principles of quantum physics. Unlike traditional cryptography, which uses mathematical methods to ensure the secrecy of information, quantum cryptography focuses on physics, considering the cases when information is transferred using objects of quantum mechanics.
Orthogonality is a concept that is a generalization of perpendicularity for linear spaces with scalar product introduced.
Quantum Bit Error Rate (QBER) - the level of quantum errors.
Quantum cryptography is a young direction, but slowly developing due to its unusual nature and complexity. From a formal point of view, this is not cryptography in the full sense of the word, since it is based not so much on mathematical models, as on the physics of quantum particles.
Its main feature, and at the same time, a feature of any quantum system is the impossibility of opening the state of the system over time, so at the first measurement the system changes its state to one of the possible nonorthogonal values. Among other things, there is the “Theorem on the prohibition of cloning” formulated in 1982 by Wutters, Zurek and Diex, which says that it is impossible to create a perfect copy of an arbitrary unknown quantum state, although there is a loophole, namely the creation of an inaccurate copy. To do this, you need to bring the original system into interaction with a larger auxiliary system and carry out a unitary transformation of the overall system, as a result of which several components of the larger system will become approximate copies of the original one.
Basics of data transfer
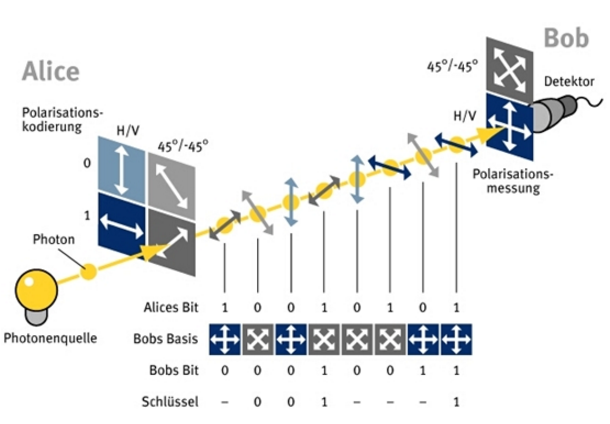
In order not to bring complicated and not all clear schemes, I will resort to a mixture of physics and geometry.
In most cases, single or paired coupled photons are used as information carriers. The values of 0/1 are encoded by different directions of polarization of photons. When transferring, randomly selected 1 of two or three non-orthogonal bases are used. Accordingly, it is possible to correctly process the input signal only if the recipient was able to choose the correct basis, otherwise the outcome of the measurement is considered uncertain.
If the hacker tries to gain access to the quantum channel through which the transfer takes place, then he, like the recipient, will make a wrong choice of basis. That will lead to the distortion of data, which will be detected by the exchange parties during the verification, according to some elaborated text, which they agreed in advance, for example, during a personal meeting or encrypted, using classical cryptography methods, channel.
Waiting and Reality
When using an ideal system, data interception is impossible, as it is instantly detected by the participants in the exchange. However, when accessing real systems, everything becomes much more prosaic.
Two features appear:
- There is the possibility of incorrectly transmitted bits, due to the fact that the process is probabilistic in nature.
- Since the main feature of the system is the use of low-energy pulses, this greatly reduces the data transfer rate.
Now a little more detail about these features.
Wrong, or more precisely distorted bits can occur for two main reasons. The first reason
The decision of the first cause is obvious Quantum Bit Error Rate.
Quantum Bit Error Rate is a level of quantum errors, which is calculated by a rather convoluted formula:
QBER = "p_f + (p_d * n * q * ∑ (f_r * t_l) / 2) * μ"
Where:
p_f: probability of wrong “click” (1-2%)
p_d: probability of an incorrect photon signal:
n: number of detections
q: phase = 1/2; polarization = 1
Σ: detector efficiency
f_r: repetition rate
p_l: data transfer rate (the greater the distance, the smaller)
µ: attenuation for light pulses.
p_d: probability of an incorrect photon signal:
n: number of detections
q: phase = 1/2; polarization = 1
Σ: detector efficiency
f_r: repetition rate
p_l: data transfer rate (the greater the distance, the smaller)
µ: attenuation for light pulses.
Speaking about the second feature it is worth mentioning that in all systems there is attenuation of the signal. And, if in the currently used methods of data transmission, this problem is solved by various methods of amplification. So in the case of a quantum channel, the current speed reached is 75 kbit / s, but the level of lost photons almost reached 50%. Although for the sake of fairness, I will say that according to known data, the minimum transmission loss is 0.5% at a speed of only 5 kbit / s.
Thus, we can draw the following conclusions:
- Although ideally the channel protected by Quantum cryptography is almost impossible to crack, at least at the moment known methods, in practice, following the rule that the stability of a system is determined by the strength of its weakest link, we are convinced of the opposite;
- Quantum cryptography is developing, and quite quickly, but unfortunately the practice does not always keep up with the theory. And as a consequence, the third conclusion follows;
- The systems created at the moment using such protocols as BB84, B92 are subject to attacks, and inherently do not provide sufficient resistance.
Of course you will say:
“But how is it because the E91 and Lo05 protocols.” And it is fundamentally different from BB84, B92.
- Yes, and yet there is one, BUT ...
But more about that in the next article.
Source: https://habr.com/ru/post/315032/
All Articles