Manage identity verification with Windows Hello for Business
We are sharing with you an overview of the Windows Hello service, which provides two-factor testing for Windows 10. You will also learn how it will be useful for large companies, why you should choose a PIN code, not a password, and how to set it up.

In Windows 10, Windows Hello for Business replaces passwords with strong two-factor authentication on computers and mobile devices. It is to create a new type of user credentials associated with the device, the use of biometric data or a PIN code.
The first versions of Windows 10 included Microsoft Passport and Windows Hello, which provided multifactor authentication. To simplify deployment and expand support, Microsoft has combined these technologies into a single solution - Windows Hello. If you have already deployed these technologies, you will not notice any changes in the functioning of the services. For those who have yet to evaluate how Windows Hello works, deploying will be much easier thanks to simplified policies, documentation, and semantics.
')
The Hello service is designed to solve common user problems encountered when working with passwords:
Hello allows you to authenticate a Microsoft account, an Active Directory account, a Microsoft Azure Active Directory account (Azure AD), and an identity provider or relying party service that supports Fast ID Online authentication (FIDO) v2.0.
After the initial two-step verification, when registering on your device, the Hello service is configured, and you set up a gesture, which can be either a biometric, such as a fingerprint, or a PIN code. Next, you need to make a gesture to verify your identity. Windows then uses Hello to authenticate and grant them access to protected resources and services.
On behalf of the administrator of a company or general educational organization, you can create Hello management policies for use on Windows 10 devices that connect to your organization.
Windows Hello is designed for convenient and secure user login. This use of Hello provides a separate level of protection, since it is unique to the device on which it is configured, but there is no authentication based on certificates.
Windows Hello for Business, which is configured by Group Policy or MDM Policy, uses key or certificate based authentication.
Currently, Active Directory accounts using Windows Hello do not support key or certificate based authentication. This feature should appear in a future release.
Passwords are shared secrets, they are entered on the device and transmitted over the network to the server. Intercepted account name and password can be used by anyone. For example, credentials may be disclosed when a server is hacked.
In Windows 10, in the process of preparation, the Hello service creates a pair of cryptographic keys associated with a trusted platform module (TPM), if the device is equipped with such a module, or in a software implementation. Access to these keys and obtaining a signature to verify that the user owns the private key is provided only with a PIN or biometric gesture. The two-step verification that occurs when registering with the Hello service forms a trusting relationship between the identity provider and the user when the public part of the public / private key pair is sent to the identity provider and associated with the user account. When a user performs a gesture on a device, the identity provider determines, using a combination of Hello keys and a gesture, that this is a verified identity, and provides an authentication token with which Windows 10 accesses resources and services. In addition, during the registration process, an identity claim is generated for each identity provider in order to cryptographically confirm that Hello keys are bound to the TPM. If the identity claim is not submitted to the identity provider during registration, the identity provider must assume that the Hello key was created programmatically.

Imagine that someone is looking over your shoulder while receiving money from an ATM and sees the PIN you enter. The presence of this PIN-code will not help them to access the account, since they do not have a bank card. Similarly, intercepting a PIN for a device does not allow an attacker to access the account, since the PIN is local to a specific device and does not provide any type of authentication from any other device.
Hello just allows you to protect identities and user credentials. Since no passwords are used, phishing and picking attacks become useless. This technology also helps prevent server hacking, since Hello credentials are an asymmetric key pair, which prevents attacks with duplicate packets, as these keys are protected by trusted platform modules (TPM).
You can also use devices with Windows 10 Mobile as remote credentials when logging in to a PC running Windows 10. During logging in to a PC running Windows 10, it can connect and access Hello on your Windows 10 Mobile device via Bluetooth . Since we always carry the phone with us, Hello makes it much easier to implement two-factor authentication.
The phone login feature is currently only available to individual members of the Technology Acceptance Program (TAP).
The advantages of a PIN code compared to a password are not related to its structure (length and complexity), but to the principle of operation
1. The PIN is tied to the device . An attacker who gains access to a password can log in to an account from any device, but if the PIN code is stolen, it will not be possible to enter the account without access to the corresponding device.
2. The PIN is stored locally on the device . The password is transmitted to the server and can be intercepted during the transfer or stolen from the server. The PIN is set on the device at the local level, is not transmitted and is not stored on the server. When a PIN is created, a trust relationship is established with the identity provider and a pair of asymmetric keys are used for authentication. When you enter the PIN, the authentication key is unlocked and is used to confirm the request sent to the server for authentication.
3. The PIN is supported by the hardware . The Hello PIN is supported by a TPM (Chip TPM) chip, which is a robust cryptographic processor for performing encryption operations. This chip contains several physical protection mechanisms to prevent hacking, and malware cannot bypass the TPM security features. TPM is used in all phones with Windows 10 Mobile and in many modern laptops.
The user key material is created and made available in a trusted platform module (TPM) on the user's device, which protects the material from being intercepted and used by intruders. Since Hello technology involves the use of pairs of asymmetric keys, user credentials will not be stolen in the event of a security breach of the identity provider or websites that the user accesses.
TPM protects against many known and potential attacks, including PIN-code picking attacks. After a certain number of attempts to enter the wrong PIN-code, the device is blocked.
4. PIN can be complicated . The Windows Hello for Business PIN code applies the same set of IT management policies as the password, including complexity, length, expiration date, and change history. Despite the confidence of most users that the PIN is a simple 4-digit code, administrators can set policies for managed devices that imply a PIN-code complexity level comparable to a password. You can make mandatory or prohibit special characters, uppercase and lowercase letters, as well as numbers.
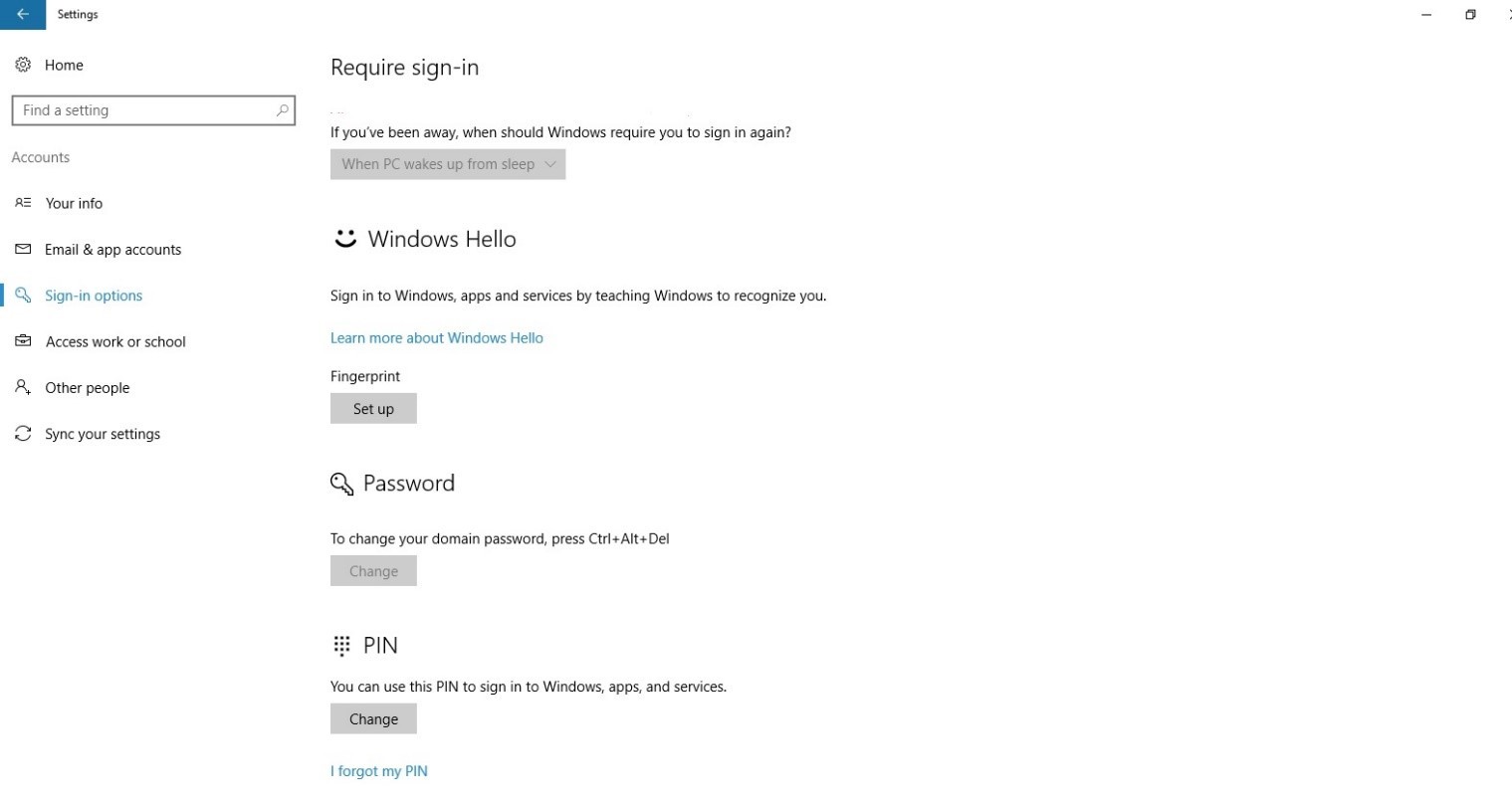
Section of the settings menu in which the PIN code and biometrics parameters are set:
To violate the security of Windows Hello credentials protected by TPM, an attacker needs to access the physical device, find a way to steal user biometric data, or pick up a PIN code. All this needs to be done before the TPM tamper protection functional mechanism blocks the device. For laptops with no TPM, you can configure additional protection by activating BitLocker and limiting the number of failed login attempts.
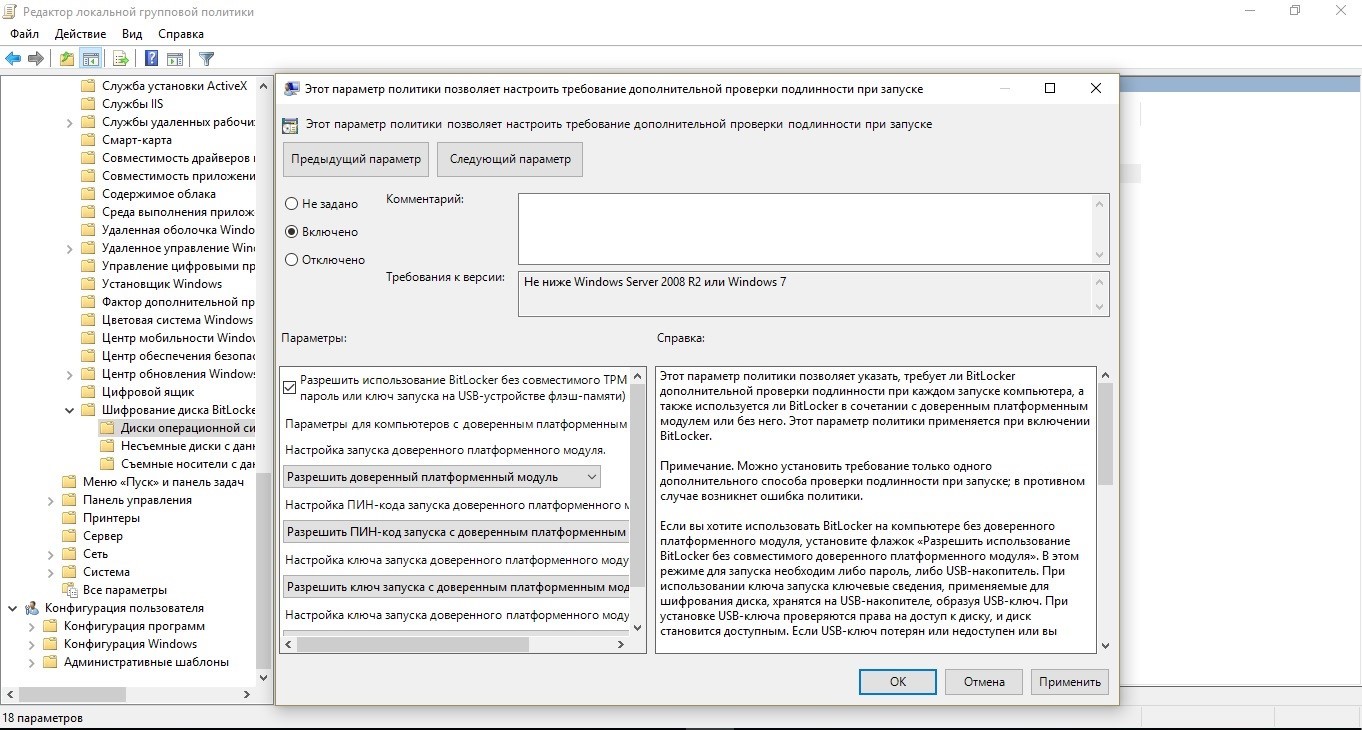
Use the local group policy editor (gpedit.msc) to activate the following policy:
Computer Configuration → Administrative Templates → Windows Components → BitLocker Drive Encryption → Operating System Drives → Require Additional Authentication at Startup
In the policy settings, select Enable BitLocker without a compatible TPM , and then click OK .
Go to Control Panel → System and Security → BitLocker Drive Encryption and select the operating system drive you want to protect.
Using the Local Group Policy Editor (gpedit.msc), activate the following policy: Computer Configuration → Windows Settings → Security Settings → Account Policies → Account Lockout Policy → Block Threshold .
Set the allowed number of failed login attempts and click OK .

1. The credentials of the Hello service are based on a certificate or an asymmetric key pair and are associated with the device, just like a token obtained with the credentials.
2. The identity provider (for example, Active Directory, Azure AD, or Microsoft account) verifies the user's identity and matches the Hello public key with the user account during the registration phase.
3. Keys can be generated in hardware (TPM 1.2 or 2.0 for businesses and TPM 2.0 for consumers) or policy-based software.
4. Authentication is a two-factor authentication using a combination of a key or certificate associated with a device and information known to the user (PIN), or user identification data (Windows Hello). The Hello gesture does not move between devices and is not provided to the server. It is stored locally on the device.
5. The private key never leaves the device. The authenticating server has a public key that was associated with a user account during registration.
6. Entering a PIN and biometric gestures leads to the verification of the user's identity in Windows 10 and authentication using keys or Hello certificates.
7. Personal (Microsoft account) or corporate accounts (Active Directory or Azure AD) use one key container. All keys are divided by identity provider domains to ensure user privacy.
8. Certificate private keys can be protected by a Hello container and a Hello gesture.
Windows Hello for Business can use keys (hardware or software) or certificates with keys in hardware or software to verify identity. Enterprises with a public key infrastructure (PKI) for issuing and managing certificates can continue to use PKI along with the Hello service. Enterprises that do not have a PKI or who want to reduce the amount of work involved in managing certificates can use key-based credentials for the Hello service.
The hardware keys that are generated by the TPM module provide the highest level of warranty. When manufactured, a TPM certificate (EK) is placed in the TPM. This EK certificate creates root trust for all other keys that are generated in this TPM module. EK certification is used to generate an authentication key certificate (AIK) issued by Microsoft Certification Service. You can use this AIK certificate as an identity claim to prove to identity providers that Hello keys were generated by the same TPM. The Microsoft Certificate Authority (CA) generates an AIK certificate for each device, user, and IDP to ensure privacy protection.
If identity providers, such as Active Directory or Azure AD, register the certificate with Hello, Windows 10 will support the same set of scripts as the smart card. If the credential type is a key, only trust and key-based operations will be supported.
We have tried to write for you a detailed and understandable tutorial on working with the Windows Hello service. If you have any questions, ask in the comments.

Windows Hello - what is it and why?
In Windows 10, Windows Hello for Business replaces passwords with strong two-factor authentication on computers and mobile devices. It is to create a new type of user credentials associated with the device, the use of biometric data or a PIN code.
The first versions of Windows 10 included Microsoft Passport and Windows Hello, which provided multifactor authentication. To simplify deployment and expand support, Microsoft has combined these technologies into a single solution - Windows Hello. If you have already deployed these technologies, you will not notice any changes in the functioning of the services. For those who have yet to evaluate how Windows Hello works, deploying will be much easier thanks to simplified policies, documentation, and semantics.
')
The Hello service is designed to solve common user problems encountered when working with passwords:
- Passwords can be difficult to remember, and users often reuse passwords on multiple sites.
- Server hacks can reveal symmetric network credentials.
- Passwords can be subject to packet replay.
- Users may inadvertently provide their password due to phishing.
Hello allows you to authenticate a Microsoft account, an Active Directory account, a Microsoft Azure Active Directory account (Azure AD), and an identity provider or relying party service that supports Fast ID Online authentication (FIDO) v2.0.
After the initial two-step verification, when registering on your device, the Hello service is configured, and you set up a gesture, which can be either a biometric, such as a fingerprint, or a PIN code. Next, you need to make a gesture to verify your identity. Windows then uses Hello to authenticate and grant them access to protected resources and services.
On behalf of the administrator of a company or general educational organization, you can create Hello management policies for use on Windows 10 devices that connect to your organization.
Difference between Windows Hello and Windows Hello for Business
Windows Hello is designed for convenient and secure user login. This use of Hello provides a separate level of protection, since it is unique to the device on which it is configured, but there is no authentication based on certificates.
Windows Hello for Business, which is configured by Group Policy or MDM Policy, uses key or certificate based authentication.
Currently, Active Directory accounts using Windows Hello do not support key or certificate based authentication. This feature should appear in a future release.
Why a PIN, not a password?
Passwords are shared secrets, they are entered on the device and transmitted over the network to the server. Intercepted account name and password can be used by anyone. For example, credentials may be disclosed when a server is hacked.
In Windows 10, in the process of preparation, the Hello service creates a pair of cryptographic keys associated with a trusted platform module (TPM), if the device is equipped with such a module, or in a software implementation. Access to these keys and obtaining a signature to verify that the user owns the private key is provided only with a PIN or biometric gesture. The two-step verification that occurs when registering with the Hello service forms a trusting relationship between the identity provider and the user when the public part of the public / private key pair is sent to the identity provider and associated with the user account. When a user performs a gesture on a device, the identity provider determines, using a combination of Hello keys and a gesture, that this is a verified identity, and provides an authentication token with which Windows 10 accesses resources and services. In addition, during the registration process, an identity claim is generated for each identity provider in order to cryptographically confirm that Hello keys are bound to the TPM. If the identity claim is not submitted to the identity provider during registration, the identity provider must assume that the Hello key was created programmatically.

Imagine that someone is looking over your shoulder while receiving money from an ATM and sees the PIN you enter. The presence of this PIN-code will not help them to access the account, since they do not have a bank card. Similarly, intercepting a PIN for a device does not allow an attacker to access the account, since the PIN is local to a specific device and does not provide any type of authentication from any other device.
Hello just allows you to protect identities and user credentials. Since no passwords are used, phishing and picking attacks become useless. This technology also helps prevent server hacking, since Hello credentials are an asymmetric key pair, which prevents attacks with duplicate packets, as these keys are protected by trusted platform modules (TPM).
You can also use devices with Windows 10 Mobile as remote credentials when logging in to a PC running Windows 10. During logging in to a PC running Windows 10, it can connect and access Hello on your Windows 10 Mobile device via Bluetooth . Since we always carry the phone with us, Hello makes it much easier to implement two-factor authentication.
The phone login feature is currently only available to individual members of the Technology Acceptance Program (TAP).
So how does a PIN help protect a device better than a password?
The advantages of a PIN code compared to a password are not related to its structure (length and complexity), but to the principle of operation
1. The PIN is tied to the device . An attacker who gains access to a password can log in to an account from any device, but if the PIN code is stolen, it will not be possible to enter the account without access to the corresponding device.
2. The PIN is stored locally on the device . The password is transmitted to the server and can be intercepted during the transfer or stolen from the server. The PIN is set on the device at the local level, is not transmitted and is not stored on the server. When a PIN is created, a trust relationship is established with the identity provider and a pair of asymmetric keys are used for authentication. When you enter the PIN, the authentication key is unlocked and is used to confirm the request sent to the server for authentication.
3. The PIN is supported by the hardware . The Hello PIN is supported by a TPM (Chip TPM) chip, which is a robust cryptographic processor for performing encryption operations. This chip contains several physical protection mechanisms to prevent hacking, and malware cannot bypass the TPM security features. TPM is used in all phones with Windows 10 Mobile and in many modern laptops.
The user key material is created and made available in a trusted platform module (TPM) on the user's device, which protects the material from being intercepted and used by intruders. Since Hello technology involves the use of pairs of asymmetric keys, user credentials will not be stolen in the event of a security breach of the identity provider or websites that the user accesses.
TPM protects against many known and potential attacks, including PIN-code picking attacks. After a certain number of attempts to enter the wrong PIN-code, the device is blocked.
4. PIN can be complicated . The Windows Hello for Business PIN code applies the same set of IT management policies as the password, including complexity, length, expiration date, and change history. Despite the confidence of most users that the PIN is a simple 4-digit code, administrators can set policies for managed devices that imply a PIN-code complexity level comparable to a password. You can make mandatory or prohibit special characters, uppercase and lowercase letters, as well as numbers.
Section of the settings menu in which the PIN code and biometrics parameters are set:

What happens if a laptop or phone is stolen?
To violate the security of Windows Hello credentials protected by TPM, an attacker needs to access the physical device, find a way to steal user biometric data, or pick up a PIN code. All this needs to be done before the TPM tamper protection functional mechanism blocks the device. For laptops with no TPM, you can configure additional protection by activating BitLocker and limiting the number of failed login attempts.
Configure BitLocker without TPM
Use the local group policy editor (gpedit.msc) to activate the following policy:
Computer Configuration → Administrative Templates → Windows Components → BitLocker Drive Encryption → Operating System Drives → Require Additional Authentication at Startup
In the policy settings, select Enable BitLocker without a compatible TPM , and then click OK .

Go to Control Panel → System and Security → BitLocker Drive Encryption and select the operating system drive you want to protect.
Using the Local Group Policy Editor (gpedit.msc), activate the following policy: Computer Configuration → Windows Settings → Security Settings → Account Policies → Account Lockout Policy → Block Threshold .
Set the allowed number of failed login attempts and click OK .

How Windows Hello for Business Works: Highlights
1. The credentials of the Hello service are based on a certificate or an asymmetric key pair and are associated with the device, just like a token obtained with the credentials.
2. The identity provider (for example, Active Directory, Azure AD, or Microsoft account) verifies the user's identity and matches the Hello public key with the user account during the registration phase.
3. Keys can be generated in hardware (TPM 1.2 or 2.0 for businesses and TPM 2.0 for consumers) or policy-based software.
4. Authentication is a two-factor authentication using a combination of a key or certificate associated with a device and information known to the user (PIN), or user identification data (Windows Hello). The Hello gesture does not move between devices and is not provided to the server. It is stored locally on the device.
5. The private key never leaves the device. The authenticating server has a public key that was associated with a user account during registration.
6. Entering a PIN and biometric gestures leads to the verification of the user's identity in Windows 10 and authentication using keys or Hello certificates.
7. Personal (Microsoft account) or corporate accounts (Active Directory or Azure AD) use one key container. All keys are divided by identity provider domains to ensure user privacy.
8. Certificate private keys can be protected by a Hello container and a Hello gesture.
Comparison of key and certificate based authentication
Windows Hello for Business can use keys (hardware or software) or certificates with keys in hardware or software to verify identity. Enterprises with a public key infrastructure (PKI) for issuing and managing certificates can continue to use PKI along with the Hello service. Enterprises that do not have a PKI or who want to reduce the amount of work involved in managing certificates can use key-based credentials for the Hello service.
The hardware keys that are generated by the TPM module provide the highest level of warranty. When manufactured, a TPM certificate (EK) is placed in the TPM. This EK certificate creates root trust for all other keys that are generated in this TPM module. EK certification is used to generate an authentication key certificate (AIK) issued by Microsoft Certification Service. You can use this AIK certificate as an identity claim to prove to identity providers that Hello keys were generated by the same TPM. The Microsoft Certificate Authority (CA) generates an AIK certificate for each device, user, and IDP to ensure privacy protection.
If identity providers, such as Active Directory or Azure AD, register the certificate with Hello, Windows 10 will support the same set of scripts as the smart card. If the credential type is a key, only trust and key-based operations will be supported.
We have tried to write for you a detailed and understandable tutorial on working with the Windows Hello service. If you have any questions, ask in the comments.
Source: https://habr.com/ru/post/314822/
All Articles