Google and Samsung fixed Dirty COW vulnerability in Android firmware
 Google has released an update for Android Android Security Bulletin — November 2016 , closing multiple vulnerabilities in this mobile OS. As with previous updates, this update was released in three stages. Its peculiarity is that within its framework a large number of critical vulnerabilities were closed, more than twenty. One of these vulnerabilities such as RCE + LPE with identifier CVE-2016-6725 is present in the Qualcomm cryptographic driver that is used on Google Nexus 5X, Nexus 6, Nexus 6P, Android One, Pixel, Pixel XL devices. The vulnerability allows you to remotely execute code on the device owner with the privileges of the Android kernel.
Google has released an update for Android Android Security Bulletin — November 2016 , closing multiple vulnerabilities in this mobile OS. As with previous updates, this update was released in three stages. Its peculiarity is that within its framework a large number of critical vulnerabilities were closed, more than twenty. One of these vulnerabilities such as RCE + LPE with identifier CVE-2016-6725 is present in the Qualcomm cryptographic driver that is used on Google Nexus 5X, Nexus 6, Nexus 6P, Android One, Pixel, Pixel XL devices. The vulnerability allows you to remotely execute code on the device owner with the privileges of the Android kernel.Samsung has also closed vulnerabilities in the Android firmware of its devices by updating SMR-NOV-2016 . The company repaired the Linux kernel Dirty-Cow LPE vulnerability with the identifier SVE-2016-7504 (CVE-2016-5195), which we wrote about earlier. Dirty COW vulnerability has also been closed and Google.
Unlike Google, Samsung does not indicate the models of its devices for which the firmware update will be available. Instead, they indicate that the "flagship device models" will receive the update.
')
Security Management Release (SMR) process. This SMR package includes patches from Google and Samsung.
Samsung fixed a number of vulnerabilities that are present only in its devices. For example, the SVE-2016-6736 LPE vulnerability is present in the / dev / fimg2d driver (Samsung Graphics 2D driver) on devices of the company with the Exynos 5433 / 54xx / 7420 chipset. Samsung also fixed the Dirty COW vulnerability in the Linux kernel, which could be used by attackers to enhance their privileges in the system.
SVE-2016-7504 : Linux kernel race condition on CopyOnWrite (DirtyCOW)
Severity : Critical
Affected versions : All devices
Reported on : October 20, 2016
Disclosure status : Privately disclosed.
If you are going to be able to make it, it will happen that you can use it.
It introduces a new “state” for copy-on-write pages.
For its Nexus devices, Google has fixed a large number of Critical LPE vulnerabilities in various drivers and kernels that can be used to enhance its privileges in the system, as well as local rootkit of devices. For example, several vulnerabilities with identifiers CVE-2015-8961, CVE-2016-7911, CVE-2016-7910 in the kernel file subsystem can be used by attackers to gain root rights in the system, which may entail reflashing the device to remove the consequences such an exploit. Actual for Google Nexus 5X, Nexus 6, Nexus 6P, Nexus 9, Android One, Pixel C, Nexus Player, Pixel, Pixel XL.
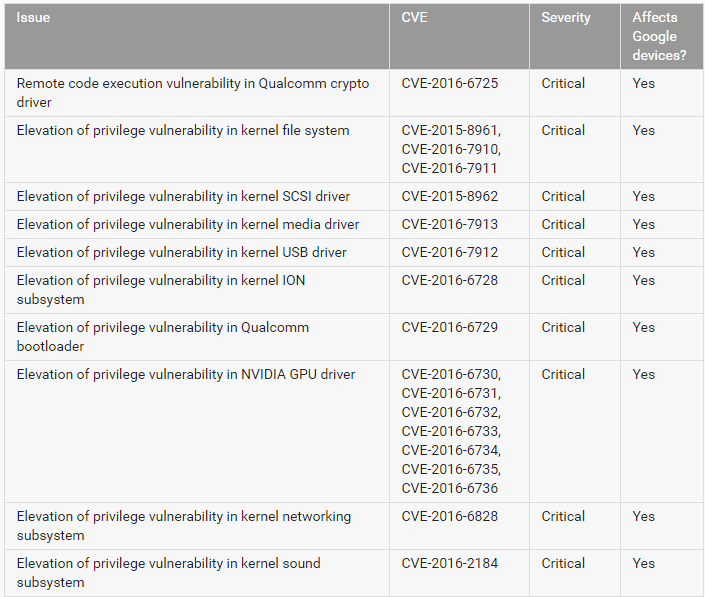
The following drivers and Android kernel subsystems have been updated.
- Qualcomm cryptographic driver.
- Kernel file subsystem.
- SCSI, Media drivers, as well as ION, network, sound kernel subsystems.
- NVIDIA GPU driver.
- The Qualcomm camera driver as well as the Qualcomm bus driver.
- Synaptics touchscreen driver.
Dirty COW vulnerability (CVE-2016-5195) has been fixed by the last part of the 2016-11-06 security patch level update.

We encourage users to update their devices.

be secure.
Source: https://habr.com/ru/post/314722/
All Articles