Basics of computer networks. Subject number 5. The concept of IP addressing, subnet masks and their calculation

I welcome you to the next issue. And today we will talk about what IP-addresses are and how to use them. What is a subnet mask, how it is considered, and why it is needed. How to divide networks into subnets and summarize them. I invite interested persons to read.
Content
1) Basic network terms, OSI network model and TCP / IP protocol stack.
2) Top-level protocols.
3) Protocols of lower levels (transport, network and channel).
4) Network devices and types of cables used.
5) The concept of IP addressing, subnet masks and their calculation.
6) The concept of VLAN, Trunk and VTP and DTP protocols.
7) Spanning Tree Protocol: STP.
8) Channel Aggregation Protocol: Etherchannel.
9) Routing: static and dynamic on the example of RIP, OSPF and EIGRP.
10) Network Address Translation: NAT and PAT.
11) Reservation protocols for the first transition: FHRP.
12) Computer network security and virtual private networks: VPN.
13) Global networks and protocols used: PPP, HDLC, Frame Relay.
14) Introduction to IPv6 configuration and routing.
15) Network management and network monitoring.
PS Perhaps over time, the list will be added.
2) Top-level protocols.
3) Protocols of lower levels (transport, network and channel).
4) Network devices and types of cables used.
5) The concept of IP addressing, subnet masks and their calculation.
6) The concept of VLAN, Trunk and VTP and DTP protocols.
7) Spanning Tree Protocol: STP.
8) Channel Aggregation Protocol: Etherchannel.
9) Routing: static and dynamic on the example of RIP, OSPF and EIGRP.
10) Network Address Translation: NAT and PAT.
11) Reservation protocols for the first transition: FHRP.
12) Computer network security and virtual private networks: VPN.
13) Global networks and protocols used: PPP, HDLC, Frame Relay.
14) Introduction to IPv6 configuration and routing.
15) Network management and network monitoring.
PS Perhaps over time, the list will be added.
Let's start, or will continue, with the most popular, hackneyed and sick. These are IP addresses. Over the course of 4 articles, this concept has been encountered several times, and most likely you have already either understood what they are for, or noggulili and read about them. But I have to tell you this, because without a clear understanding it will be hard to move on.
')
So the IP address is the address that the node uses at the network level. It has a hierarchical structure. What does it mean? This means that each number in its writing has a specific meaning. I will explain with a very good example. An example would be a regular telephone number - +74951234567. The first digit is +7. This suggests that the number belongs to the zone of the Russian Federation. This is followed by 495. This is the code of Moscow. And the last 7 digits I took random. These numbers are assigned to the district area. As you can see here there is a clear hierarchy. That is, by number you can understand which country, zone it belongs to. IP addresses follow a similar strict hierarchy. The organization is controlled by the IANA (Internet Assigned Numbers Authority). If in Russian, then this is the "Administration of the address space of the Internet." Note that the word "Internet" with a capital letter. Few people attach importance to this, so I will explain the difference. In the English literature, the term “internet” is used to describe several networks connected to each other. And the term "Internet" to describe the global network. So take note.
Despite the fact that the topic of the article is more theoretical than practical, I strongly recommend that you take it seriously, because it depends on understanding of further topics, and especially routing. There is no one for whom, I think, it is no secret that we are accustomed to perceive numeric information in decimal format (in numbers from 0-9). However, all modern computers perceive information in binary (0 and 1). It does not matter with the help of current or light information is transmitted. All of it will be perceived by the device as there is a signal (1) or not (0). Only 2 values. Therefore, an algorithm was developed for converting from binary to decimal, and vice versa. I'll start with a simple one and tell you what IP addresses look like in decimal format. This whole article is about IP addresses of version 4. There will be a separate article about version 6. In previous articles, labs, and indeed in life, you saw something like this "193.233.44.12." This is the IP address in decimal. It consists of 4 numbers, called octets and separated by dots. Each such number (octet) can take a value from 0 to 255. That is, one of 256 values. The length of each octet is 8 bits, and the total length of IPv4 = 32 bits. Now an interesting question. How will this address take the computer, and how will it work with it?
You can of course stuff it into a calculator, of which there is bulk on the Internet, and it will convert it into binary format, but I believe that everyone should be able to translate manually. This is especially true of those who are planning to take the exam. You will have nothing on hand except paper and a marker, and you will have to rely only on your skills. Therefore, showing how to do it manually. Build a table.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| x | x | x | x | x | x | x | x |
Instead of “x”, either 1 or 0 is written. The table is divided into 8 columns, each of which carries 1 bit (8 columns = 8 bits = 1 octet). They are arranged in order from left to right. That is, the first (left) bit is the oldest and has the number 128, and the last (right) is the youngest and has the number 1. Now I will explain where these numbers come from. Since the system is binary, and the length of the octet is equal to 8 bits, each number is obtained by raising the number 2 to the power from 0 to 7. And each of the received digits is written into the table from the largest to the smallest. That is, from left to right. From 2 to the 7th degree to 2 to the 0th degree. I will give a table of degrees 2-ki.
I think now it is clear how the table is built. Let's now look at the address "193.233.44.12" and see how it looks in binary format. Let us examine each octet separately. Take the number 193 and see from what table combinations it is obtained. 128 + 64 + 1 = 193.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| one | one | 0 | 0 | 0 | 0 | 0 | one |
Those numbers that participated in the formation of a combination get 1, and all the others get 0.
Take the first octet 233. 128 + 64 + 32 + 8 + 1.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| one | one | one | 0 | one | 0 | 0 | one |
For 44, this is 32 + 8 + 4.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| 0 | 0 | one | 0 | one | one | 0 | 0 |
And finally 12. 8 + 4.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| 0 | 0 | 0 | 0 | one | one | 0 | 0 |
The result is a long bit sequence 11000001.11101001.00101100.00001100. It is with this kind of work network devices. The bit sequence is reversible. You can also insert each octet (8 characters) into the table and get a decimal notation. I will present a completely random sequence and bring it to decimal form. Let it be 11010101.10110100.11000001.00000011. I build the table and put in it the first block.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| one | one | 0 | one | 0 | one | 0 | one |
I get 128 + 64 + 16 + 4 + 1 = 213.
I calculate the second block.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| one | 0 | one | one | 0 | one | 0 | 0 |
I think 128 + 32 + 16 + 4 = 180.
The third block.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| one | one | 0 | 0 | 0 | 0 | 0 | one |
128 + 64 + 1 = 193.
And finally, the fourth.
| 128 | 64 | 32 | sixteen | eight | four | 2 | one |
|---|---|---|---|---|---|---|---|
| 0 | 0 | 0 | 0 | 0 | 0 | one | one |
2 + 1 = 3
We collect the results of calculations and get the address 213.180.193.3. Nothing hard, pure arithmetic. If it is difficult and direct unbearably difficult, then practice. At first, it may seem scary, as many have graduated 10 years ago and have forgotten a lot. But I assure you that as soon as you put your hand, it will be much easier to count. Well, to consolidate, I'll give you a few examples for self-calculation (there will be answers under the spoiler, but only open them when you decide it yourself).
Problem number 1
1) 10.124.56.220
2) 113.72.101.11
3) 173.143.32.194
4) 200.69.139.217
5) 88.212.236.76
6) 01011101.10111011.01001000.00110000
7) 01001000.10100011.00000100.10100001
8) 00001111.11011001.11101000.11110101
9) 01000101.00010100.00111011.01010000
10) 00101011.11110011.10000010.00111101
Answers
1) 00001010.01111100.00111000.11011100
2) 01110001.01001000.01100101.00001011
3) 10101101.10001111.00100000.11000010
4) 11001000.01000101.10001011.11011001
5) 01011000.11010100.11101100.01001100
6) 93.187.72.48
7) 72.163.4.161
8) 15.217.232.245
9) 69.20.59.80
10) 43.243.130.61
2) 01110001.01001000.01100101.00001011
3) 10101101.10001111.00100000.11000010
4) 11001000.01000101.10001011.11011001
5) 01011000.11010100.11101100.01001100
6) 93.187.72.48
7) 72.163.4.161
8) 15.217.232.245
9) 69.20.59.80
10) 43.243.130.61
Now IP-addresses should not be something scary, and you can delve into their study.
Above, we talked about the structure of telephone numbers and their hierarchy. And at the dawn of the birth of the Internet in the view in which we used to see it, a question arose. The question was that the IP addresses need to somehow be grouped and controlled to issue. The solution was to divide the entire space of IP addresses into classes. This decision was called class addressing (from the English. Classful) . It has long been outdated, but in almost every book, entire chapters and sections are devoted to it. Cisco also does not forget about it and in its educational materials tells about it. Therefore, I will go over this topic and show how it shone from 1981 to 1995.
The space was divided into 5 classes. Each class has been assigned a block of addresses.
Let's start with class A. If you look closely at the table, you can see that this block is given the largest block of addresses, and to be exact, half of the entire address space. This class was intended for large networks. The structure of this class is as follows.
What is the essence. The first octet, that is, 8 bits, remains behind the network address, and the last 3 octets (that is, the remaining 24 bits) are assigned to the hosts. Here, in order to show which piece belongs to the network, and which to the hosts, a mask is used. The structure of the record is similar to the record of the IP address. The difference between masks and IP addresses is that 0 and 1 cannot alternate. First there are 1, and then 0. Thus, where there is a unit, then this is a network segment. Below, after analyzing classes, I will show you how to work with it. Now the main thing to know that the mask of class A - 255.0.0.0. In the table some first bit is also mentioned, and for class A it is equal to 0. This bit is just needed in order for the network device to understand which class it belongs to. He also sets the initial and final address range. If in binary form units are recorded on all octets, except the first bit in the first octet (there is always 0), we get 127.255.255.255, which is the class A boundary. For example, take the address 44.58.63.132. We know that in class A, the first octet is given to the network address. That is, "44" is the network address, and "58.63.132" is the host address.
Let's talk about class B
This class has been given a smaller block. And addresses from this block were intended for medium-scale networks. 2 octets are given for the network address, and 2 - for the address of the hosts. The mask for the B class is 255.255.0.0. The first bits are strictly 10. And the rest are changing. Let us turn to the example: 172.16.105.32. The first two octets for the network address are “172.16”. And the 3rd and 4th under the address of the host - "105.32".
Class C
This class was cheated with addresses and gave it the smallest unit. It was intended for small networks. But this class gave as many as 3 octets for the network address and only 1 octet for hosts. His mask is 255.255.255.0. The first bits are 110. For example, it looks like this - 192.168.1.5. The network address is “192.168.1”, and the host address is “5”.
Classes D and E. I am inconsistent in combining them into one. Addresses from these blocks are reserved and cannot be assigned to networks and hosts. Class D is for multicast. An analogy can be made with television. The channel broadcasts a group of persons its broadcast. And those who are connected, can watch TV. That is, only 3 first classes can be available to administrators.
Let me remind you that the first bits of class D are 1110. An example of the address is 224.0.0.5.
And the first bits of class E is 1111. Therefore, if you suddenly see the address of the form 240.0.0.1, feel free to say that this is the address of the E class.
Pro classes have mentioned. Now I will voice the question that I was recently asked. So why then masks? We have so the hosts understand what class they are in. But the point is this. For example, you have a small office, and you need a block of IP addresses. Nobody will give you all the addresses of class C. And they will give only his piece. For example, 192.168.1.0 with a mask of 255.255.255.0. So this mask will determine your border. We have already said that the octet varies in value from 0 to 255. This 4 octet is completely at your disposal. Except for the first address and the last one, that is, 0 and 255 in this case. The first address is the network address (in this case, 192.168.1.0), and the last address is the broadcast address (192.168.1.255). Let me remind you that the broadcast address is used in the case when you need to transmit information to all nodes in the network. Therefore, there is a rule. If you need to know the network number, then all bits related to the host are set to 0, and if broadcast, then all bits are set to 1. Therefore, if 2 addresses are taken from 256 addresses, then 254 addresses are left to be assigned to the hosts (256 - 2) . At interviews and exams often like to ask: "The number of IP addresses on the network?" And "How many IP addresses on the network to assign to the hosts?". Two different questions that can stump. The answer to the first one will be all the addresses, including the network address and the broadcast address, and the second question is all addresses except the network address and the broadcast address.
Now dive into the study of the mask.
I recorded the class C address 192.168.1.1 with the mask 255.255.255.0 in decimal and binary format. Notice how the IP address and the mask look like in binary format. If the IP address 0 and 1 alternate, then the mask first goes 1, and then 0. These bits fix the network address and set the size. In the table above, we can conclude that in binary form the mask is represented by a sequence of 24 units in a row. This suggests that as many as 3 octets are allocated to the network, and 4 octets are free for addressing for the hosts. There is nothing unusual here. This is a standard class C mask.
But here's the catch. For example, you have 100 computers in your office, and you do not plan to expand. Why produce a network of 250+ addresses that you do not need? Subnetting comes to the rescue. This is a very convenient thing. Let me explain the principle using the example of the same class C. However you would like, but you cannot touch 3 octets. They are fixed. But here 4 octet is free for hosts, so you can touch it. Borrowing bits from the host chunk, you split the network into the n-th number of subnets and, accordingly, reduce the number of addresses for the hosts.
Let's try to translate it into reality. Change the mask. I borrow the first bit from the host part (that is, I set the 1st bit of the 4th octet to one). It turns out the following mask.
This mask divides the network into 2 parts. If before the crushing the network had 256 addresses (from 0 to 255), then after crushing each piece will have 128 addresses (from 0 to 127 and from 128 to 255).
Now I will see what will change in general with addresses.
In red, I showed those bits that are fixed and cannot change. That is, the mask sets the boundary for it. Accordingly, bits marked in black are defined to address the hosts. Now I will calculate this boundary. To determine the beginning, all free bits (marked in black) must be turned to zero, and to determine the end to turn into units. I'm starting.
That is, in the fourth octet, all bits except the first one are changed. It is rigidly fixed within this network.
Now we will look at the second half of the network and calculate its addresses. Our division was made by borrowing the first bit in the 4th octet, which means it is a divisor. The first half of the network was obtained when this bit took the value 0, which means the second network is formed when this bit takes the value 1. I turn this bit to 1 and look at the boundaries.
I will give a decimal view.
Accordingly .128 and .255 cannot be assigned to hosts. So in the availability of 128-2 = 126 addresses.
This is how you can use the mask to control the size of the network. Each borrowed bit divides the network into 2 parts. If we bite off 1 bit from the host part, we divide it into 2 parts (128 addresses each), 2 bits = 4 parts (64 addresses each), 3 bits = 8 (32 addresses each), and so on.
If you calculated the number of bits for hosts, then the number of available IP addresses can be calculated by the formula
In the book of W. Odom on the preparation for the CCNA R & S, a good formula is given for calculating the bits sent to the subnet and hosts:
N + S + H = 32 , where N is the number of network bits (class A is 8 bits, B is 16 bits, C is 24 bits), S is the number of borrowed bits per subnet (this is what we did above, when borrowed 1 bit from the host), H - the number of bits allocated to the hosts.
I will clarify and explain how and where to apply these formulas.
Take an example:
We were given a network of 172.16.0.0 and asked to create 120 subnets with 180 hosts and write a mask. Let's get started
As a cheat sheet, and for quick calculation, I have prepared a table of powers of two below.
Moving on. The first major condition, when using class addressing, is that one mask should be used for all subnets. That is, if you have a mask of 255.255.255.0 for one subnet, then for another subnet it cannot be 255.255.255.128.
Now we look at the issued network. By logical reflections, we understand that this is a class B address. And that means its N (number of network bits) = 16. Ok. So the hosts are also allocated 16 bits. We recall the conditions of the problem. Need to create 120 subnets. "Bite off" bits from the network part is prohibited, it means we bite from the host part.
Now you need to take such a number of bits, so that is enough for 120 subnets, but leaves a sufficient number of bits for the host. We look at the table above. If we take 7 bits, we get 128. 128> 120, therefore we fall under the condition. If we take 6 bits, we get 64. 64 <128, so we do not fall under the condition and discard this option.
OK. Found out that S should be allocated at least 7 bits. Now let's see what is left for the hosts.
If N + S + H = 32 => H = 32 - (N + S) => H = 32 - (16 + 7) = 9. Look at the table above (or raise 2 to the 9th power in the mind) and get the number 512. Subtract 2 (the network address and the broadcast address) and get 510 addresses. We need 180, which means we get under the condition with a large margin. In such cases, you are given the right to choose. Make more subnets or hosts per subnet. Explain what it means. We have 9 bits per host. If we take 8 bits, we get the number 256. 256 - 2 = 254 addresses. This option also suits us. Take 7 bits. We get 128. Even without taking away 2 addresses, it becomes clear that this is less than 180 => this option is discarded immediately. In total, we find that the minimum number for a subnet is 7 bits, and for hosts it is 8 bits. Therefore, the free bit can be given either to the subnet or to the hosts. The mask is obtained by adding N and S. In our case, if we give 7 bits for the subnet, we get 23. In decimal form, the mask will look like 255.255.254.0. And if we give 8 bits to the subnet, we get 24 (or in decimal 255.255.255.0). Sometimes it happens that there is only one mask for the task. And, of course, there may be cases when the mask does not fall under any conditions. In these cases, you need to take a network of another class or prove to the customer that this is impossible.
I think now it is clear how class addressing worked, and how it was calculated. Perhaps the first time the head does not digest this, so reread again and more closely. As soon as something starts to clear up, practice on the tasks I’ll leave.
Problem number 2
1) Write a mask for the project: network 172.16.0.0. 250 subnets and 220 hosts.
2) Write a mask for the project: network 10.0.0.0. 2000 subnets and 1500 hosts.
3) Write a mask for the project: network 192.168.0.0. 4 subnets and 60 hosts.
Answers to tasks
1) 24 bits or 255.255.255.0
2) 19 bits (255.255.224.0), 20 bits (255.255.240.0), 21 bits (255.255.248.0)
3) 26 bits or 255.255.255.192
2) 19 bits (255.255.224.0), 20 bits (255.255.240.0), 21 bits (255.255.248.0)
3) 26 bits or 255.255.255.192
On this conversation about class networks I will begin to round out and summarize. Class addressing is the birth of today's Internet, and it all began with it. Therefore, it has a lot of advantages, and thanks to the creators for it. But, as you can see, she had a tight binding to one mask.Due to this, IP addresses were not used economically and wastefully. And in connection with the rapid growth of the Internet addresses was not enough, and urgently needed to make changes.
Understood the leading minds that the use of class networks is not convenient and you need to give them up. This led to the creation of classless addressing and variable length masks, which we will discuss below. But before that, a few words about the types of IP addresses. Despite the fact that the transition from class to classless addressing suggested saving IP addresses, in fact, this problem was still not fully resolved. It all came down to the IPv4 technology itself. I will explain why. Above, I said that the length of the IP address is 32 bits. Each bit can take the value 0 or 1, that is, two values. Accordingly, in order to calculate all the combinations, it is necessary to build 2 to the 32nd degree. We get 4294967296 addresses. If we subtract from here the reserved for special needs and other things, then there will remain approximately 4.2 billion addresses, when about 7.3 billion people live on Earth.Therefore, leading minds quickly cut through this chip and began to look for a solution. They decided to allocate some address space that will be used only within the local network and will not be used on the Internet. It divided the addresses into 2 camps: white or public (eng. Public) and gray or private (eng. Private).
I quote a range of addresses that are allocated for local networks:
1) 10.0.0.0 - 10.255.255.255 with a mask of 255.0.0.0 (or briefly 10/8).
2) 172.16.0.0 - 172.31.255.255 with a mask of 255.240.0.0 (or briefly 172.16 / 12).
3) 192.168.0.0 - 192.168.255.255 (or briefly 192.168 / 16).
To be honest, I have seen the use of addressing 172.16.XX in a few places. Usually 10.XXX is always used in the corporate environment, and 192.168.XX in houses / apartments and small offices.
Now I ask you to pay attention to a very important thing that many confuse. Do not confuse class addressing with a range of private addresses. A lot of people step on this rake and firmly believe that the range of private addresses 10.0.0.0 - 10.255.255.255 is the range of the A class.
Understood what are private addresses or private addresses. But that is not all. There is also a list of reserved addresses that cannot be lit on the Internet. They have written the entire IETF documentation. I give a link where you can read the original. I will briefly describe the common ones.
1) 0.0.0.0/8 - the address range used by hosts for self-identification. This can usually be seen when the host is trying to get an IP address from a DHCP server. Since he initially does not have an IP address, he inserts an address from this range into the source field.
2) 127.0.0.0/8 - loopback or localhost addresses. These are the IP addresses used by the computer to access itself. Very useful for checking TCP / IP performance. The fact is that regardless of the connection to the Internet or local network, addresses from this pool should always be pinged. If this does not happen, then the system is covered or covered with a copper basin.
3) 169.254.0.0/16 - link-local address or local addresses. Automatically used by hosts in the absence of a DHCP server or its inaccessibility. This allows you to quickly organize a local network and check the operation of nodes. However, this address pool is not routed. Consequently, to go online with them will not work.
4) 224.0.0.0/4 - a block of addresses reserved for multicast or multicast. For those who want to learn more about multicast, leave a link .
Classless Addressing (Classless Inter-Domain Routing or CIDR) . It was described in the RFC1519 standard in 1993. She abandoned the class framework and fixed mask. Addresses are divided only into public and reserved, which are written above. If in class addressing the mask is cut to be uniform for all subnets, then in the classless address, each subnet may have its own mask. On theory, everything is good and beautiful, but there is nothing better than practice. Therefore, I turn to it and explain how it can be divided into subnets with different numbers of hosts.
As a cheat sheet give a list of all possible masks.
Imagine the situation.You were given a network of 192.168.1.0/24 and set the following conditions:
1) Subnet on 10 addresses for guests.
2) Subnet at 42 addresses for employees.
3) Subnet for 2 addresses to connect 2 routers.
4) Subnet at 26 addresses for the branch.
OK.This mask indicates that we have 256 addresses at our disposal. By condition, this network must somehow be divided into 4 subnets. Let's try.256 is very well divided by 4, giving 64 in response. So one big block of 256 addresses can be divided into 4 equal blocks of 64 addresses each. And everything would be fine, but it generates a large number of empty addresses. For employees who need 42 addresses, okay, the company may further hire them. But the subnet for routers, which requires only 2 addresses, will leave 60 empty addresses. Yes, you can say that these are private addresses, and who cares about them. Now imagine that these are public addresses that are routed on the Internet. There are so few of them, and here we will still throw them away. This is not the case, especially when we can flexibly manage the address space. Therefore, we return to the example and cut the subnet as we need.
So, which subnets should be sliced to contain all the addresses specified by the condition?
1) For 10 hosts, the smallest subnet will be a block of 16 addresses.
2) For 42 hosts, the smallest subnet is a block of 64 addresses.
3) For 2 hosts, the smallest subnet will be a block of 4 addresses.
4) For 26 hosts, the smallest subnet will be a block of 32 addresses.
I understand that not everyone can grasp this right from the first, and there is nothing to worry about. All people are different and perceive information differently. For completeness, I will show the division in the picture.
Here we have a block consisting of 256 addresses.
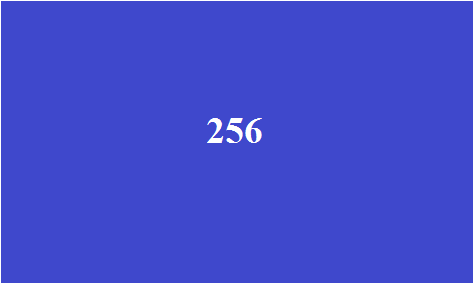
After dividing into 4 parts, the following picture is obtained.
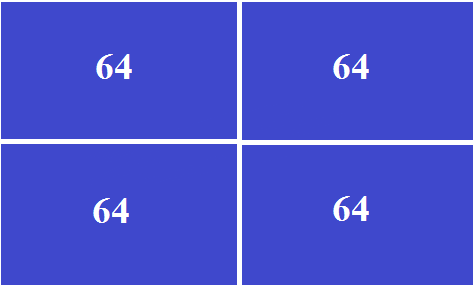
Above, we found that in this situation addresses are not used rationally. Now pay attention to how the address space began to look after cutting subnets of different lengths.
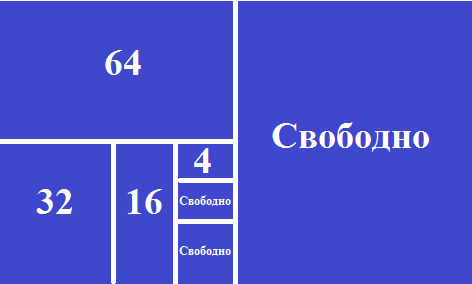
As you can see, there are a lot of addresses in free access, which we will be able to use in the future. You can count the exact figure. 256 - (64 + 32 + 16 + 4) = 140 addresses.
Here are the addresses we saved. Moving on and answering the following questions:
- What will be the network and broadcast addresses?
- What addresses can be assigned to hosts?
- How will I look like a mask?
The mechanism of dividing into subnets with different masks is called VLSM (from the English. Variable Length Subnet Mask) or variable length subnet mask. I give important advice! Start addressing from the largest subnet. Otherwise, you can get to the fact that the address will overlap. Therefore, first plan the network on paper. Draw it, draw it in the form of figures, calculate it manually or on a calculator, and only then proceed to the setting in combat conditions.
So, the largest subnet consists of 64 addresses. Let's start with it. The first address pool will be the following:
The subnet address is 192.168.1.0.
The broadcast address is 192.168.1.63.
A pool of addresses to assign to hosts from 192.168.1.1 to 192.168.1.62.
Now the choice of the mask. It's simple.We take away the necessary piece from the whole network and write the resulting number into the mask octet. That is, 256 - 64 = 192 => mask 255.255.255.192 or / 26.
Next comes the smaller subnet. It consists of 32 addresses. If the first one ended in .63, then this one will start with .64:
The subnet address is 192.168.1.64.
The broadcast address is 192.168.1.95.
The address pool for assignment to hosts will be from 192.168.1.65 to 192.168.1.94.
Mask: 256 - 32 = 224 => 255.255.255.224 or / 27.
The 3rd subnet that is intended for the branch will start from .96:
The subnet address is 192.168.1.96.
The broadcast address is 192.168.1.111.
The address pool for assignment to hosts will be from 192.168.1.97 to 192.168.1.110.
Mask: 256 - 16 = 240 => 255.255.255.240 or / 28.
Well, for the last subnet that goes under the interfaces connecting the routers will start with .112:
The subnet address is 192.168.1.112.
The broadcast address is 192.168.1.115.
The resolved addresses are 192.168.1.113 and 192.168.1.114.
Mask: 256 - 4 = 252 => 255.255.255.252 or / 30.
I note that the address 192.168.1.115 is the last used address. Starting from 192.168.1.116 and up to .255 are free.
In this way, using VLSM or variable-length masks, we have economically created 4 subnets with the required number of addresses in each. I think it is worth fixing a puzzle for an independent decision.
Problem number 3
Split the network 192.168.1.0/24 into 3 different subnets. Find and record in each subnet its address, broadcast address, pool of allowed addresses and mask. I specify the required sizes of subnets:
1) Subnet for 120 addresses.
2) Subnet to 12 addresses.
3) Subnet to 5 addresses.
Answer
1) — 192.168.1.0.
— 192.168.1.127.
192.168.1.1 192.168.1.126.
: 256 — 128 = 128 => 255.255.255.128 /25.
2) — 192.168.1.128.
— 192.168.1.143.
192.168.1.129 192.168.1.142.
: 256 — 16 = 240 => 255.255.255.240 /28.
3) — 192.168.1.144.
— 192.168.1.151.
192.168.1.145 192.168.1.150.
: 256 — 8 = 248 => 255.255.255.248 /29.
— 192.168.1.127.
192.168.1.1 192.168.1.126.
: 256 — 128 = 128 => 255.255.255.128 /25.
2) — 192.168.1.128.
— 192.168.1.143.
192.168.1.129 192.168.1.142.
: 256 — 16 = 240 => 255.255.255.240 /28.
3) — 192.168.1.144.
— 192.168.1.151.
192.168.1.145 192.168.1.150.
: 256 — 8 = 248 => 255.255.255.248 /29.
Now that you know how to divide networks into subnets, it's time to learn how to assemble subnets into one common subnet. Otherwise, it is called summation or summarization . Summation is most often used in routing. When you have several neighboring subnets in the router table that are routed through the same interface or address. Most likely this process is better explained when parsing routing, but given that the topic of routing is already large, I will explain the process of summation in this article. Moreover, the summation is a solid mathematics, and in this article we are doing it. Well, let's get started.
Imagine that I have a company consisting of the main building and buildings. I work in the main building, and in the buildings of a colleague. Although I have the main building, there are only 4 subnets in it:
- 192.168.0.0/24
- 192.168.1.0/24
- 192.168.2.0/24
- 192.168.3.0/24
Then the colleagues from the neighboring building found out and realized flew configuration on the router, and there are no backups. They do not remember by heart which subnets in the main building, but they remember that they are next to each other and ask to send one summarized one. Now I have a problem how to summarize them. To begin, I will translate all subnets in binary form.
Look carefully at the table. As you can see, in 4 subnets, the first 22 bits are the same. Accordingly, if I take 192.168.0.0 with a mask / 22 or 255.255.252.0, then I will cover my 4 subnets. But pay attention to the 5 subnet, which I specifically introduced. This is the subnet 192.168.4.0. Its 22nd bit is different from the previous 4th, which means that the one selected above will not cover this subnet.
OK.Now I will send a summarized subnet to my colleagues, and if they register everything correctly, then routing to my subnets will work without problems.
Take the same example and slightly change the conditions. We were asked to send a summary route for subnets 192.168.0.0 and 192.168.1.0. I will not be lazy and create another table.
Note that the first 2 subnets have the same 22 bits instead of 22 bits. This means that they can be summed up even more compactly. In principle, it will work both ways. But as it was said in one advertisement: “If there is no difference - why pay more?”. Therefore, try to summarize, without affecting the neighboring subnets.
Thus, by converting subnets to binary and finding the same bits, you can sum them up.
In general, summation is useful when you need to combine several subnets located close to each other. This will save router resources. However, this is not always possible. To sum up, for example, the subnet 192.168.1.0 and 192.168.15.0, without capturing the neighboring subnets, is impossible. Therefore, before summing up, it is worth considering its expediency. Therefore, I repeat once again that it is necessary to start any revolution on a piece of paper. Well, to secure the material leave a small task.
Problem number 4
Given 4 subnets:
1) 10.3.128.0
2) 10.3.129.0
3) 10.3.130.0
4) 10.3.131.0 Sum
up the subnets and find a mask that can cover them without affecting the neighboring subnets.
Answer
Based on this, the answer will be 10.3.128.0/22 (255.255.252.0)
Based on this, the answer will be 10.3.128.0/22 (255.255.252.0)
It's time to wrap up. The article was not very long. I would even say the opposite. But everything that Cisco needs to know about IPv4 is covered. It is the most important thing to do. And, of course, it's right to divide the subnets and distribute address space. Thank you for reading. And if you want to have your prices.
Source: https://habr.com/ru/post/314484/
All Articles