How I tried to enable http2 in my project with nginx
In general, as I have already read here in the comments: “whole articles write on how to add 5 characters and a space in the config”. All is good, if not google chrome. They decided to stop supporting SPDY and NPN (who cares, here is a comment from chromium about this).
For example, take debian 8 on google cloud engine, set up nginx, with the help of letsencrypt we make certificates.
As a result, we get this:
that is, all your keys will lie here /etc/letsencrypt/live/domain.tld/
Add all this beauty to the nginx config:
')
In the end, you should have something like this:
VBart :
You can still look at the file
Perhaps there is already configured a configured DNS server. Check how it works can be as follows:
VBart :
To make DHE:
It seems that everything can be done and service nginx reload but FIG us :) You will receive in response this: Job for nginx.service failed. See 'systemctl status nginx.service' and 'journalctl -xn' for details. , and in details:
In general, nginx did not understand at all what we wanted and wanted from him. We look at the version and it turns out nginx version: nginx / 1.6.2 , okay, we will install the latest version.
Go to the browser, check:

We see the HTTP / 2.0 200 Status , we are happy, we check in chrome:
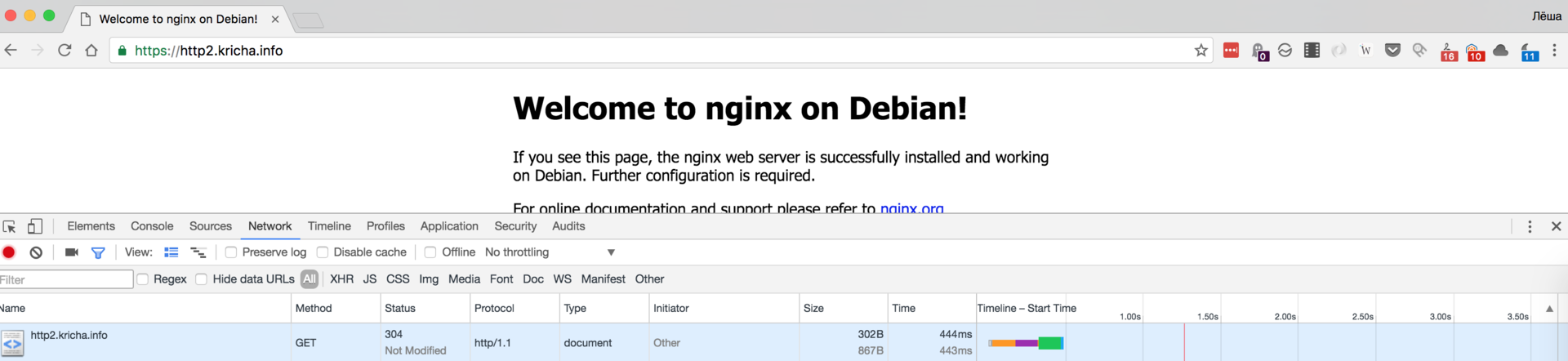
We see Protocol http / 1.1 , sad andleave to cry . No, of course, do not give up, pour rum in a glass and continue.
Instead of make install, you can build the package:
Check in chrome:

In safari:
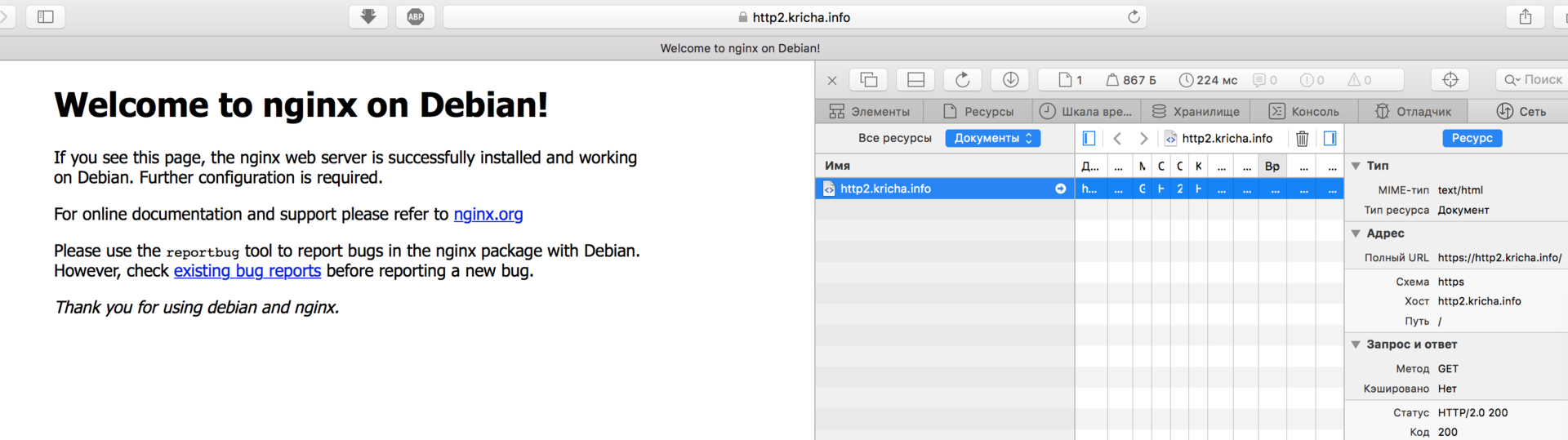
Everywhere we see that the http2 protocol is used, we also check on www.ssllabs.com , we get:
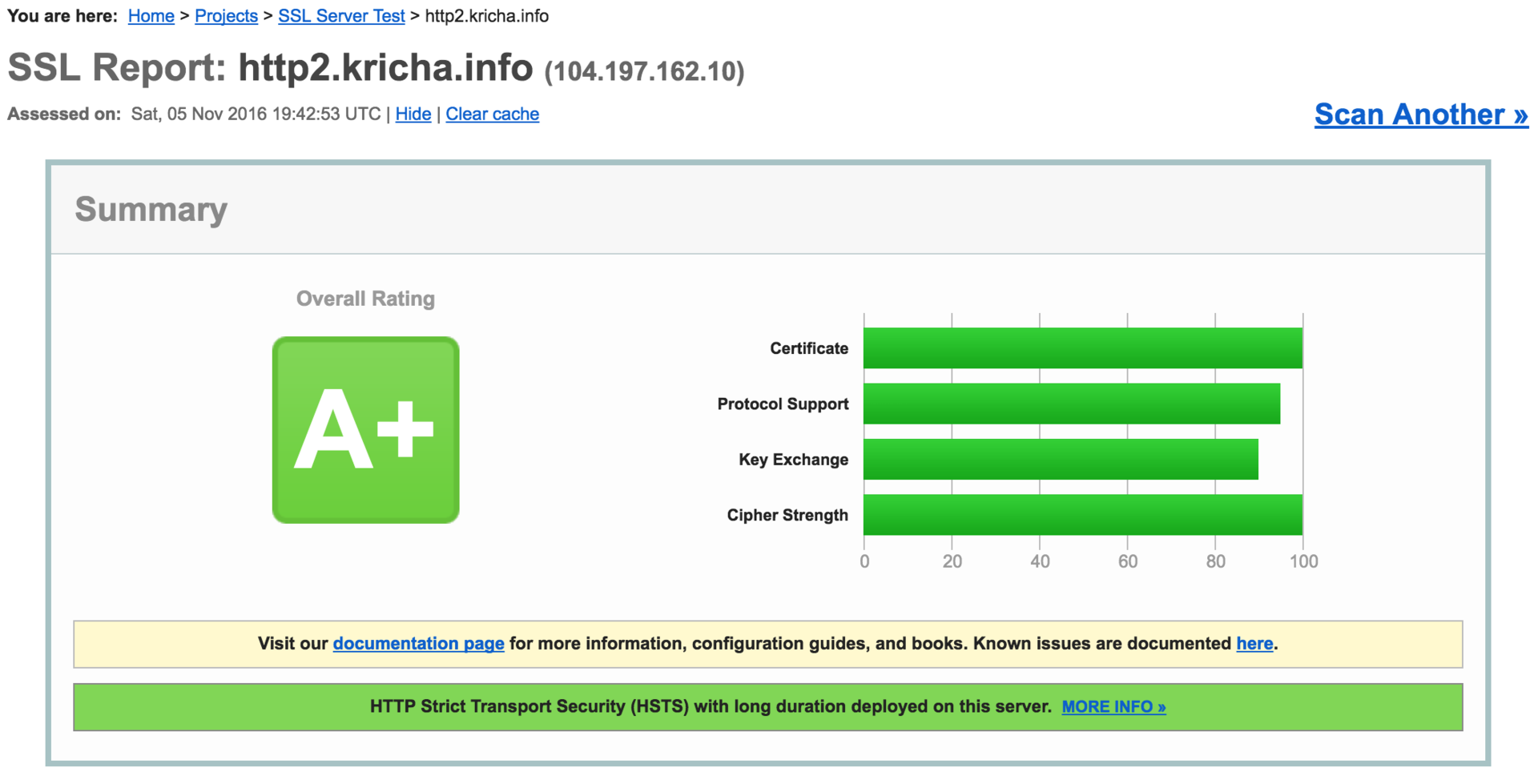
Profit! Fill up with rum and go to sleep! Thank you all for your attention, I hope someone helped.
For example, take debian 8 on google cloud engine, set up nginx, with the help of letsencrypt we make certificates.
For those who can not:
echo "deb http://ftp.debian.org/debian jessie-backports main" >> /etc/apt/sources.list apt-get update apt-get install certbot -t jessie-backports -y certbot certonly --webroot -w /var/www/html -d domain.tld --email=your@email.tld --agree-tos # /var/www/html - , As a result, we get this:
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at
/etc/letsencrypt/live/http2.kricha.info/fullchain.pem. Your cert
will expire on 2017-02-03. To obtain a new or tweaked version of
this certificate in the future, simply run certbot again. To
non-interactively renew * all * of your certificates, run "certbot
renew
that is, all your keys will lie here /etc/letsencrypt/live/domain.tld/
# ls -la /etc/letsencrypt/live/http2.kricha.info/ total 8 drwxr-xr-x 2 root root 4096 Nov 5 17:53 . drwx------ 3 root root 4096 Nov 5 17:53 .. lrwxrwxrwx 1 root root 41 Nov 5 17:53 cert.pem -> ../../archive/http2.kricha.info/cert1.pem lrwxrwxrwx 1 root root 42 Nov 5 17:53 chain.pem -> ../../archive/http2.kricha.info/chain1.pem lrwxrwxrwx 1 root root 46 Nov 5 17:53 fullchain.pem -> ../../archive/http2.kricha.info/fullchain1.pem lrwxrwxrwx 1 root root 44 Nov 5 17:53 privkey.pem -> ../../archive/http2.kricha.info/privkey1.pem Add all this beauty to the nginx config:
')
#let's encrypt certificates ssl_certificate /etc/letsencrypt/live/domain.tld/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/domain.tld/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/domain.tld/chain.pem; In the end, you should have something like this:
server { server_name domain.tld; listen 443 ssl http2; server_tokens off; keepalive_timeout 70; ssl_stapling on; ssl_stapling_verify on; resolver 127.0.0.1; resolver_timeout 10s; ssl on; #let's encrypt certificates ssl_certificate /etc/letsencrypt/live/domain.tld/fullchain.pem; ssl_certificate_key /etc/letsencrypt/live/domain.tld/privkey.pem; ssl_trusted_certificate /etc/letsencrypt/live/domain.tld/chain.pem; ssl_dhparam /etc/nginx/ssl/dhparam.pem; ssl_session_timeout 1h; ssl_session_cache shared:SSL:10m; ssl_protocols TLSv1 TLSv1.1 TLSv1.2; ssl_prefer_server_ciphers on; ssl_ciphers AES256+EECDH:AES256+EDH:!aNULL; add_header Strict-Transport-Security "max-age=63072000; includeSubDomains; preload" always; add_header X-Frame-Options DENY; add_header X-Content-Type-Options nosniff; root /var/www/html; index index.nginx-debian.html; location / { try_files $uri $uri/ =404; } error_log /var/log/nginx/domain.tld.error.log; access_log /var/log/nginx/domain.tld.access.log; } server { listen 80; listen [::]:80; server_name domain.tld; return 301 https://$host$request_uri; } VBart :
The documentation states: nginx.org/ru/docs/http/ngx_http_core_module.html#resolver
To prevent DNS spoofing, it is recommended to use DNS servers in a secure trusted local network.
The built-in resolver is sharpened for performance, with safety sacrificed.
You can still look at the file
cat /etc/resolv.conf nameserver 127.0.0.1 Perhaps there is already configured a configured DNS server. Check how it works can be as follows:
nslookup example.org 127.0.0.1 or dig example.org @127.0.0.1 VBart :
Usually not installed. Instead of a full DNS server, you can use a DNS forwarder such as dnsmasq .
To make DHE:
cd /etc/nginx mkdir ssl openssl dhparam -out ssl/dhparam.pem 2048 It seems that everything can be done and service nginx reload but FIG us :) You will receive in response this: Job for nginx.service failed. See 'systemctl status nginx.service' and 'journalctl -xn' for details. , and in details:
ov 05 18:01:15 http2 systemd[1]: Failed to read PID from file /run/nginx.pid: Invalid argument Nov 05 18:01:15 http2 systemd[1]: Started A high performance web server and a reverse proxy server. Nov 05 18:14:27 http2 systemd[1]: Reloading A high performance web server and a reverse proxy server. Nov 05 18:14:27 http2 nginx[24507]: nginx: [emerg] invalid parameter "http2" in /etc/nginx/sites-enabled/default:4 Nov 05 18:14:27 http2 systemd[1]: nginx.service: control process exited, code=exited status=1 Nov 05 18:14:27 http2 systemd[1]: Reload failed for A high performance web server and a reverse proxy server. In general, nginx did not understand at all what we wanted and wanted from him. We look at the version and it turns out nginx version: nginx / 1.6.2 , okay, we will install the latest version.
Install the latest version of nginx
echo -e "deb http://nginx.org/packages/mainline/debian/ jessie nginx\ndeb-src http://nginx.org/packages/mainline/debian/ jessie nginx" >>/etc/apt/sources.list rm -rf /var/lib/dpkg/info/nginx* apt-get update apt-get upgrade --force-yes -y service nginx restart Go to the browser, check:

We see the HTTP / 2.0 200 Status , we are happy, we check in chrome:

We see Protocol http / 1.1 , sad and
We collect the correct nginx
apt-get install libpcre3 libpcre3-dev libpcrecpp0 libssl-dev zlib1g-dev cd /opt wget http://nginx.org/download/nginx-1.11.5.tar.gz wget https://www.openssl.org/source/openssl-1.0.2j.tar.gz tar xf nginx-1.11.5.tar.gz tar xf openssl-1.0.2j.tar.gz cd nginx-1.11.5 ./configure --prefix=/etc/nginx --sbin-path=/usr/sbin/nginx --modules-path=/usr/lib/nginx/modules --conf-path=/etc/nginx/nginx.conf --error-log-path=/var/log/nginx/error.log --http-log-path=/var/log/nginx/access.log --pid-path=/var/run/nginx.pid --lock-path=/var/run/nginx.lock --http-client-body-temp-path=/var/cache/nginx/client_temp --http-proxy-temp-path=/var/cache/nginx/proxy_temp --http-fastcgi-temp-path=/var/cache/nginx/fastcgi_temp --http-uwsgi-temp-path=/var/cache/nginx/uwsgi_temp --http-scgi-temp-path=/var/cache/nginx/scgi_temp --user=nginx --group=nginx --with-compat --with-file-aio --with-threads --with-http_addition_module --with-http_auth_request_module --with-http_dav_module --with-http_flv_module --with-http_gunzip_module --with-http_gzip_static_module --with-http_mp4_module --with-http_random_index_module --with-http_realip_module --with-http_secure_link_module --with-http_slice_module --with-http_ssl_module --with-http_stub_status_module --with-http_sub_module --with-http_v2_module --with-mail --with-mail_ssl_module --with-stream --with-stream_realip_module --with-stream_ssl_module --with-stream_ssl_preread_module --with-openssl=/opt/openssl-1.0.2j make make install service nginx restart Instead of make install, you can build the package:
apt-get install checkinstall -y dpkg -i nginx_1.11.5-1_amd64.deb Check in chrome:

In safari:

Everywhere we see that the http2 protocol is used, we also check on www.ssllabs.com , we get:

Profit! Fill up with rum and go to sleep! Thank you all for your attention, I hope someone helped.
Source: https://habr.com/ru/post/314474/
All Articles