Attackers continue to use Linux / Moose malware to compromise devices
Last year, our specialists published a detailed analysis of the Linux / Moose malware, as well as the activities of intruders who used it to compromise embedded devices. Moose was used to compromise network routers, the vast majority of which are running Linux.

The compromised devices were used by operators to steal unencrypted network traffic, as well as provide proxy services to other attackers. In practice, the operators used traffic interception to steal HTTP cookies from popular network services, which were then used to perform illegitimate actions on these services, including such as cheating the number of views of the publication, setting marks like and adding new followers of accounts.
Last year, experts from ESET and security firm GoSecure have joined forces to further research this malware. GoSecure has been investigating the social fraud aspect of intruders, as well as investigating the criminal cyber services market of the botnet called “The Ego Market”. This market was disclosed in a published GoSecure study. Our post is devoted to the analysis of new features Linux / Moose, which appeared after the publication of our previous study.
')
The first change that was noticed in the new samples of Moose was that inside the executable file itself there was no IP address of the manager of the C & C server. It seems that the authors carefully read our previous study of the malware and decided to make its analysis more difficult. In the new version, the authors set the IP address of the C & C server manager as an encrypted command line argument. Below is an example of such a method.

This new feature implies that we can no longer simply launch a malicious file for execution to investigate its functions. Instead, our test devices should have been infected by another device already compromised by the attackers. You can see that the IP address is specified in a 32-bit integer form.
Authors use IP address encryption to make it impossible to detect the address of a C & C server without knowing the argument passed, even if researchers have a sample of the executable file at their disposal. In addition, the knowledge of this value itself is useless without an executable file that contains the key to decrypt the argument. The argument is decrypted by an XOR operation with the key specified inside the file.

As far as we know, this hard-wired value has remained unchanged over the past few months. The following Python code snippet is designed to decrypt the 32-bit integer value of an IP address.

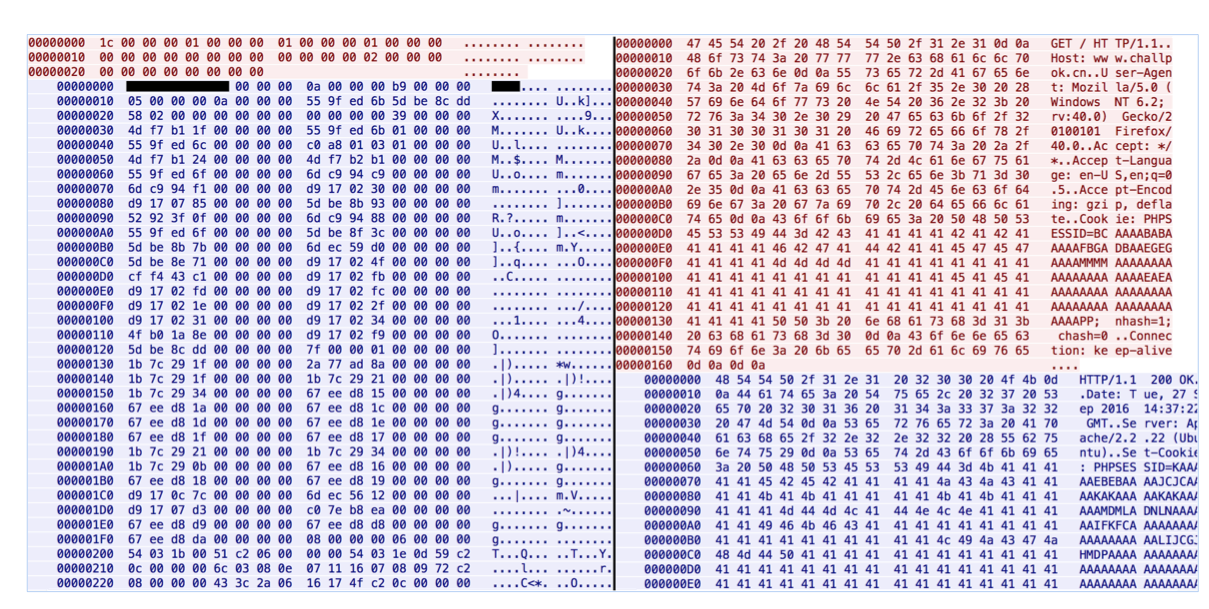
The network protocol was also changed, but its foundation was retained and new features were added. Below is an example of comparing network packets of two different Moose samples. It can be seen that the format of the protocol, which has turned from binary to ASCII, has undergone major changes. The figure below shows the old network protocol (left) and the new (right).
In the last Moose modification, configuration information was sent to the bot by the C & C server manager and contained various fields, including bit fields to determine which bot function should be enabled. For this, configuration fields such as the IP address field, the white list of addresses, and the list of passwords were used. These fields are still present in the new version of the malware, but now they are divided into three different keys (see the table below). To send this configuration data, the operator uses the cookie: and set-cookie: parameters of the HTTP protocol. This information is encrypted in a loop with a simple XOR algorithm, which was also used in the first version. However, the information is also encoded in a readable ASCII view in the HTTP header.

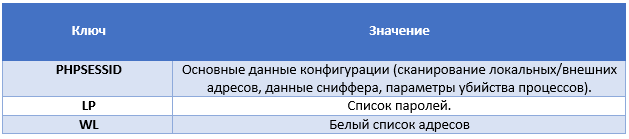
The PHPSESSID configuration key captures the encrypted contents of the bit field, which allows you to enable or disable various Moose functions. The LP parameter records the list of passwords that the malicious program will use in attempting to infect other devices when accessing them via telnet. The authors significantly reduced this list, if in 2015 there were about 300 logins and passwords, now (2016) there are about 10 of them left.

The WL key indicates a white list of IP addresses of devices that should not be infected. In the new version, the list is reduced from 50 addresses to 10. The list of these IP addresses is listed below. Linux / Moose still has the ability to provide attackers with proxy services, while incoming connections are listening on TCP port 20012. Previous modifications used port 10073 for these purposes. The proxy function allows whitelisting IP addresses to interact with the malware.
The Linux / Moose authors did a great job of modifying the malware, adding to it the function of hiding the location of the control C & C servers, as well as changing the network protocol. These new features allow malware authors to make useless indicators of compromising the activity of previous versions of Moose in the case of new versions. Reducing the size of the white list of addresses, as well as passwords, shows their more delicate approach to the use of the bot. We found in the Moose files special fake indicators for misleading researchers, for example, the domain www.challpok.cn , which was found in clear text in the list of strings. In addition, lines were discovered in the same place that attempt to mask Moose as a miner for bitcoins or a DDoS bot. The bot does not use any means to ensure its survival in the system, so a simple reboot of the device will complete its malicious activity.
A list of compromise indicators is also available on our repository .

The compromised devices were used by operators to steal unencrypted network traffic, as well as provide proxy services to other attackers. In practice, the operators used traffic interception to steal HTTP cookies from popular network services, which were then used to perform illegitimate actions on these services, including such as cheating the number of views of the publication, setting marks like and adding new followers of accounts.
Last year, experts from ESET and security firm GoSecure have joined forces to further research this malware. GoSecure has been investigating the social fraud aspect of intruders, as well as investigating the criminal cyber services market of the botnet called “The Ego Market”. This market was disclosed in a published GoSecure study. Our post is devoted to the analysis of new features Linux / Moose, which appeared after the publication of our previous study.
')
The first change that was noticed in the new samples of Moose was that inside the executable file itself there was no IP address of the manager of the C & C server. It seems that the authors carefully read our previous study of the malware and decided to make its analysis more difficult. In the new version, the authors set the IP address of the C & C server manager as an encrypted command line argument. Below is an example of such a method.

This new feature implies that we can no longer simply launch a malicious file for execution to investigate its functions. Instead, our test devices should have been infected by another device already compromised by the attackers. You can see that the IP address is specified in a 32-bit integer form.
Authors use IP address encryption to make it impossible to detect the address of a C & C server without knowing the argument passed, even if researchers have a sample of the executable file at their disposal. In addition, the knowledge of this value itself is useless without an executable file that contains the key to decrypt the argument. The argument is decrypted by an XOR operation with the key specified inside the file.

As far as we know, this hard-wired value has remained unchanged over the past few months. The following Python code snippet is designed to decrypt the 32-bit integer value of an IP address.

The network protocol was also changed, but its foundation was retained and new features were added. Below is an example of comparing network packets of two different Moose samples. It can be seen that the format of the protocol, which has turned from binary to ASCII, has undergone major changes. The figure below shows the old network protocol (left) and the new (right).

In the last Moose modification, configuration information was sent to the bot by the C & C server manager and contained various fields, including bit fields to determine which bot function should be enabled. For this, configuration fields such as the IP address field, the white list of addresses, and the list of passwords were used. These fields are still present in the new version of the malware, but now they are divided into three different keys (see the table below). To send this configuration data, the operator uses the cookie: and set-cookie: parameters of the HTTP protocol. This information is encrypted in a loop with a simple XOR algorithm, which was also used in the first version. However, the information is also encoded in a readable ASCII view in the HTTP header.


The PHPSESSID configuration key captures the encrypted contents of the bit field, which allows you to enable or disable various Moose functions. The LP parameter records the list of passwords that the malicious program will use in attempting to infect other devices when accessing them via telnet. The authors significantly reduced this list, if in 2015 there were about 300 logins and passwords, now (2016) there are about 10 of them left.

The WL key indicates a white list of IP addresses of devices that should not be infected. In the new version, the list is reduced from 50 addresses to 10. The list of these IP addresses is listed below. Linux / Moose still has the ability to provide attackers with proxy services, while incoming connections are listening on TCP port 20012. Previous modifications used port 10073 for these purposes. The proxy function allows whitelisting IP addresses to interact with the malware.
Conclusion
The Linux / Moose authors did a great job of modifying the malware, adding to it the function of hiding the location of the control C & C servers, as well as changing the network protocol. These new features allow malware authors to make useless indicators of compromising the activity of previous versions of Moose in the case of new versions. Reducing the size of the white list of addresses, as well as passwords, shows their more delicate approach to the use of the bot. We found in the Moose files special fake indicators for misleading researchers, for example, the domain www.challpok.cn , which was found in clear text in the list of strings. In addition, lines were discovered in the same place that attempt to mask Moose as a miner for bitcoins or a DDoS bot. The bot does not use any means to ensure its survival in the system, so a simple reboot of the device will complete its malicious activity.
Compromise Indicators (IoC)
0x1F (31) c6edfa2bf916d374e60f1b5444be6dbbee099692 c9ca4820bb7be18f36b7bad8e3044b2d768a5db8 5b444f1ac312b4c24b6bde304f00a5772a6a19a4 f7574b3eb708bd018932511a8a3600d26f5e3be9 0x20 (32) 34802456d10efdf211a7d486f7108319e052cd17 0685cb1d72107de63fa1da52930322df04a72dbc 2876cad26d6dabdc0a9679bb8575f88d40ebd960 f94b6cc5aea170cee55a238eaa9339279fba962f 274ef5884cb256fd4edd7000392b0e326ddd2398 c3f0044ffa9d0bc950e9fd0f442c955b71a706b6 f3daea1d06b1313ec061d93c9af12d0fe746839a 0x21 (33) 7767c8317fb0bbf91924bddffe6a5e45069b0182 1caac933ae6ca326372f7e5dd9fff82652e22e34 5dea6c0c4300e432896038661db2f046c523ce35 e8dc272954d5889044e92793f0f637fe4d53bb91 0843239b3d0f62ae6c5784ba4589ef85329350fa 1d1d46c312045e17f8f4386adc740c1e7423a24a d8b45a1114c5e0dbfa13be176723b2288ab12907 0x22 (34) c35d6812913ef31c20404d9bbe96db813a764886 IP- C&C- 192.3.8.218 192.3.8.219 155.133.18.64 178.19.111.181 151.80.8.2 151.80.8.19 151.80.8.30 62.210.6.34 A list of compromise indicators is also available on our repository .
Source: https://habr.com/ru/post/314458/
All Articles