Information security: five ways to protect against cyber attacks
Until the new millennium, the most frequent threats in the field of information technology were viruses, simple malicious codes. For the necessary protection against standard cyber attacks, it was enough to install an antivirus program based on the signature detection method. Today's attacks on company information systems are much more complex and require special layers of protection, in particular for key infrastructures. Our security expert Anya Dörner prepared an overview of five ways to protect against cyber attacks.
The current version of Symantec’s Internet security threat report demonstrates that crackers carefully select their victims. In particular, large and medium-sized enterprises are hit. The security industry speaks of targeted persistent threats to Advanced Persistent Threat (APT). The report of the company Symantec states that before the attack, the attackers collect detailed information about the company. Their goal is to obtain information about the structure of the company, about which employees have the most extensive access to the systems, which sites employees use daily to obtain information, etc.
Just look at the example of the Dragonfly community attack in order to understand what a targeted cyber attack might look like:

Dragonfly attack as an example of ART
')
From the diagram you can see how the whole Dragonfly attack campaign unfolded. Since 2013, energy companies have been attacked in the following countries:
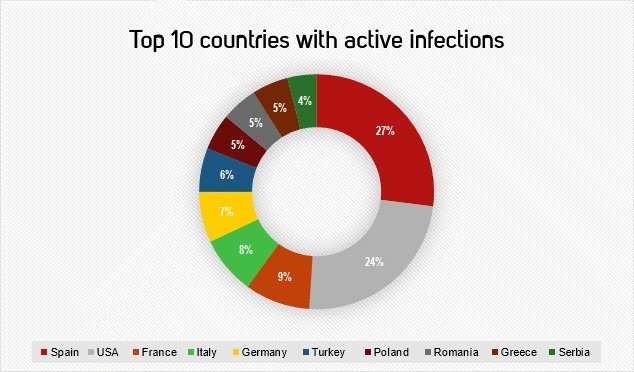
Dragonfly: Western energy companies are under threat of sabotage
Dragonfly is a hacker community that is predominantly located in Eastern Europe. Initially, this community focused its attention on airlines and military-industrial companies, then from 2013 they switched to industrial enterprises in the field of energy. For example, the Dragonfly community acted fairly professionally, hitting the software used in industrial control systems with a Trojan program. The information environment of energy companies was astonished when software was updated (shown in green in the diagram), which gave hackers unhindered access to networks. This hacker group also committed other cyber attacks. First, they chose certain company employees as their goal, sending phishing emails to them (shown in blue in the diagram), and at the same time infecting frequently visited sites (shown in red in the diagram) using malicious code. The Dragonfly community successfully uses malicious codes to export system information, copy documents, view addresses in Outlook, or VPN connection configuration data. A Symantec security report says that such data is then encrypted and sent to the command server hackers.
Undoubtedly, hackers managed not only to get all the information, they were also able to implement their program code in the management system software, thereby controlling technical systems. The worst scenario would be a significant disruption of the country's energy supply.
From the above example, it is clearly seen that a targeted cyber attack can last for several months, and sometimes even years, and it can include a wide range of different attack channels. Will companies today be able to detect threats of this kind and assess the risk for their activities only on the basis of conventional security software ?
Relying on our experience, we can say that the answer to this question is no.
A study conducted by the Information Systems Audit and Control Association (ISACA) shows that 33% of companies are not sure that they are properly protected from cyber attacks or are able to adequately respond to them. Protection against these diverse threats requires a multi-level solution and an intelligent security system.

Five ways to protect against cyber attacks
Step 1: Prevention
Companies must remove their blinders and prepare for a real emergency: prepare emergency strategies and action plans, as well as recognize their vulnerabilities.
Step 2: Introduce Protective Measures
A well-protected workplace is the best way to protect against cyber attacks. So, many different defense mechanisms must ensure that threats cannot even penetrate the information network. With an increase in the frequency of attacks, this concept is complemented by a coordinated security setting in which multiple solutions are combined and share contextual information. This can speed detection and automate response.
Step 3: Detection
Today, there are already a large number of different methods of identifying malware. It is necessary to use modern knowledge to create an informed decision on which strategy will be best suited for deployment.
Step 4: Response
If the network is damaged, malicious programs must be removed completely without any residual marks. In this case, you need to guarantee the safety of the workplace. To prevent such incidents in the future, it is extremely important to determine when and how the malicious code was able to access the network.
Step 5: Recovery
After cleaning the system, use the appropriate backup software for data recovery.
Many companies face the same problems that are shown in the diagram:
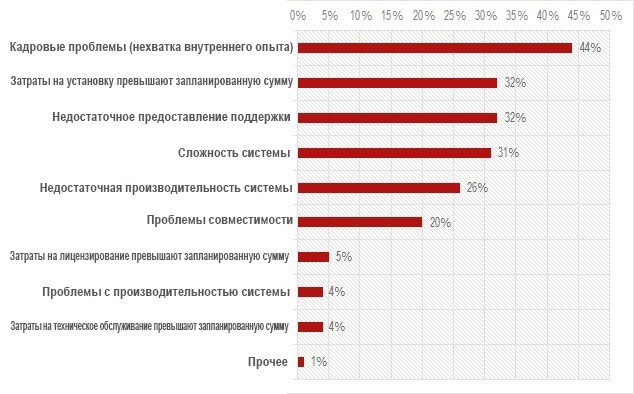
According to the Ponemon Institute: A global study of the costs and investments in information security in 2015.
Today there are many opportunities to ensure sufficient information security of the IT environment. To do this, companies need only to find suitable experts in the field of information security and take advantage of solutions that are appropriate for this company.
The current version of Symantec’s Internet security threat report demonstrates that crackers carefully select their victims. In particular, large and medium-sized enterprises are hit. The security industry speaks of targeted persistent threats to Advanced Persistent Threat (APT). The report of the company Symantec states that before the attack, the attackers collect detailed information about the company. Their goal is to obtain information about the structure of the company, about which employees have the most extensive access to the systems, which sites employees use daily to obtain information, etc.
Just look at the example of the Dragonfly community attack in order to understand what a targeted cyber attack might look like:

Dragonfly attack as an example of ART
')
From the diagram you can see how the whole Dragonfly attack campaign unfolded. Since 2013, energy companies have been attacked in the following countries:

Dragonfly: Western energy companies are under threat of sabotage
Dragonfly is a hacker community that is predominantly located in Eastern Europe. Initially, this community focused its attention on airlines and military-industrial companies, then from 2013 they switched to industrial enterprises in the field of energy. For example, the Dragonfly community acted fairly professionally, hitting the software used in industrial control systems with a Trojan program. The information environment of energy companies was astonished when software was updated (shown in green in the diagram), which gave hackers unhindered access to networks. This hacker group also committed other cyber attacks. First, they chose certain company employees as their goal, sending phishing emails to them (shown in blue in the diagram), and at the same time infecting frequently visited sites (shown in red in the diagram) using malicious code. The Dragonfly community successfully uses malicious codes to export system information, copy documents, view addresses in Outlook, or VPN connection configuration data. A Symantec security report says that such data is then encrypted and sent to the command server hackers.
Undoubtedly, hackers managed not only to get all the information, they were also able to implement their program code in the management system software, thereby controlling technical systems. The worst scenario would be a significant disruption of the country's energy supply.
From the above example, it is clearly seen that a targeted cyber attack can last for several months, and sometimes even years, and it can include a wide range of different attack channels. Will companies today be able to detect threats of this kind and assess the risk for their activities only on the basis of conventional security software ?
Relying on our experience, we can say that the answer to this question is no.
A study conducted by the Information Systems Audit and Control Association (ISACA) shows that 33% of companies are not sure that they are properly protected from cyber attacks or are able to adequately respond to them. Protection against these diverse threats requires a multi-level solution and an intelligent security system.
What measures should be taken to ensure adequate protection?

Five ways to protect against cyber attacks
Step 1: Prevention
Companies must remove their blinders and prepare for a real emergency: prepare emergency strategies and action plans, as well as recognize their vulnerabilities.
Step 2: Introduce Protective Measures
A well-protected workplace is the best way to protect against cyber attacks. So, many different defense mechanisms must ensure that threats cannot even penetrate the information network. With an increase in the frequency of attacks, this concept is complemented by a coordinated security setting in which multiple solutions are combined and share contextual information. This can speed detection and automate response.
Step 3: Detection
Today, there are already a large number of different methods of identifying malware. It is necessary to use modern knowledge to create an informed decision on which strategy will be best suited for deployment.
Step 4: Response
If the network is damaged, malicious programs must be removed completely without any residual marks. In this case, you need to guarantee the safety of the workplace. To prevent such incidents in the future, it is extremely important to determine when and how the malicious code was able to access the network.
Step 5: Recovery
After cleaning the system, use the appropriate backup software for data recovery.
The most common problems faced by companies in the field of information security
Many companies face the same problems that are shown in the diagram:

According to the Ponemon Institute: A global study of the costs and investments in information security in 2015.
Today there are many opportunities to ensure sufficient information security of the IT environment. To do this, companies need only to find suitable experts in the field of information security and take advantage of solutions that are appropriate for this company.
Source: https://habr.com/ru/post/314450/
All Articles