7 server security measures

Last time, we talked about how to choose servers and how to install them in the office with your own hands .
Now it's time to take care of the next step - to set up an IT infrastructure to work with applications, web services and databases. This is not an easy task, but without proper protection, the entire infrastructure will be at risk.
This time we will talk about the basic protection measures that should be taken before you start using your servers.
Ssh keys
The technology is based on a pair of cryptographic keys that are used for authentication as an alternative to password authentication. The login system uses private and public keys that are created prior to authentication. The private key is kept secret by a trusted user, while the public key can be distributed from any SHH server to which you want to connect.
')
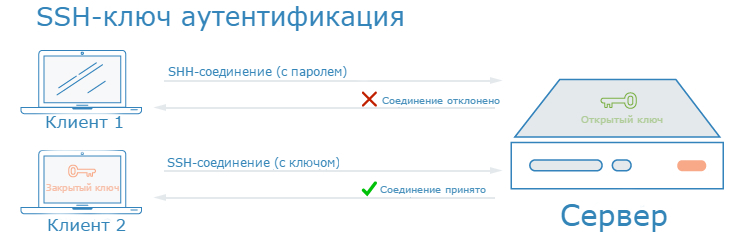
To configure authentication via SSH keys, you must place the user's public key in a special directory on the server. When a user connects to the server, SSH will see the connection request. He then uses the public key to create and send a call. A call is an encrypted message that needs an appropriate response in order to gain access to the server. Only the holder of the private key can correctly reply to the message. That is, only he can take the call and create the appropriate response. The public key is used to encrypt the message, but it cannot decrypt the same message.
The call and answer pass unnoticed by the user. As long as you have a private key, which is usually stored in encrypted form in ~ / .ssh /, your SSH client will be able to send the correct answer to the server.
How does an SSH key increase security?
With SSH, any type of authentication is fully encrypted. However, if password-based authentication is enabled, attackers can get to the server data. With the help of modern computing power, you can access the server by automating hacking attempts by entering combination after combination, until you find the correct password.
Having established authentication using SSH keys, you will be able to forget about passwords. Keys have much more data bits than passwords, which means a significantly larger number of combinations that hackers should pick up. Many SSH key algorithms are considered to be unbreakable by modern computing technology simply because they take too long to match.
How hard is it to implement SSH?
SSH keys are pretty easy to set up. Often they are used as a way to remotely access Linux and Unix server environments. A pair of keys is generated on your computer, then you can transfer the public key to the servers within a few minutes.
Here are the basic steps for setting keys:
1. To generate a key pair on your computer, enter the following command:
ssh-keygen -t rsa 2. Once you have entered the key generation command, you have to answer a couple of questions, for example, where to save the file and which key phrase to choose. In general, the result will look like this:
ssh-keygen -t rsa Generating public/private rsa key pair. Enter file in which to save the key (/home/demo/.ssh/id_rsa): Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in /home/demo/.ssh/id_rsa. Your public key has been saved in /home/demo/.ssh/id_rsa.pub. The key fingerprint is: 4a:dd:0a:c6:35:4e:3f:ed:27:38:8c:74:44:4d:93:67 demo@a The key's randomart image is: +--[ RSA 2048]----+ | .oo. | | . oE | | + . o | | . = = . | | = S = . | | o + = + | | . o + o . | | . o | | | +----------------------------+ 3. Once you have the keys, place the public key on the virtual server you are going to use. It will turn out something like this:
The authenticity of host '12.34.56.78 (12.34.56.78)' can't be established. RSA key fingerprint is b1:2d:33:67:ce:35:4d:5f:f3:a8:cd:c0:c4:48:86:12. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '12.34.56.78' (RSA) to the list of known hosts. user@12.34.56.78's password: Now try logging into the machine, with "ssh 'user@12.34.56.78'", and check in: ~/.ssh/authorized_keys If you feel that you still need an authentication password on your servers, look at solutions like Fail2ban, which limit the number of attempts to enter a password.
Firewalls
A firewall is a piece of software or firmware that filters network traffic and controls network access. This means blocking or restricting access to each open port, except for exceptions.
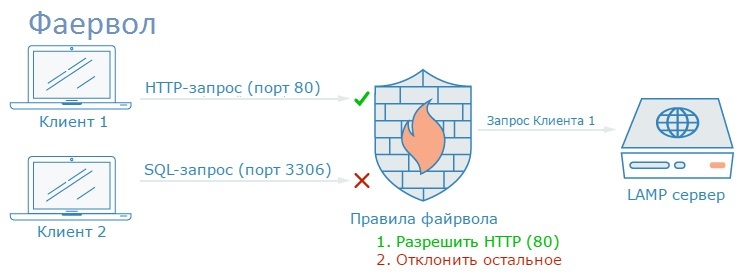
On a typical server, a number of firewall components are running by default. They can be divided into groups:
- Open services, to which everyone can connect to the Internet, often anonymously. A good example is a web server that allows access to your site.
- Private services that are available only from certain places or authorized users. An example is a site or database control panel.
- Internal services available within the server itself, without access to external sources. For example, a database that accepts only local connections.
The use of a firewall ensures that access to software and data will be restricted in accordance with the above categories. Private services can be configured for a variety of parameters, which gives the flexibility to build protection. For unused ports, you can configure blocking in most configurations.
How does a firewall increase security?
Firewalls are an integral part of any server configuration. Even if your software has internal security functionality, the firewall will provide an extra level of protection.
A carefully configured firewall will block access to everything for which you yourself will not assign an exception. Components vulnerable to attack, covered with a firewall, will reduce the attack surface of the server.
How hard is it to implement a firewall?
There are many firewalls available on LAMP servers. In general, the installation of a firewall will take only a few minutes and is needed in two cases: during the initial setup of the server and when changing specific services of an already running server.
In this article we will not recommend specific firewalls, this is a topic for another conversation.
VPN and Private networking
VPN (Virtual Private Network) is a way to create a secure connection between remote computers and the current connection. It allows you to customize your work with the server as if you are using a secure local area network.

How does VPN increase security?
If you choose between a private and public network, the first option is always preferable. It should be remembered that users of the data center are connected by a single network, you should save yourself from the risks as much as possible by taking additional measures for secure communication between servers.
Using VPN is, in essence, a way to create a private network that only your servers can see. Communication will be completely private and secure. In addition, VPN can be configured for individual applications and services so that their traffic passes through a virtual interface. Thus, it is possible to secure processes within the company by opening public access only for the client side, and hide the VPN inside the server.
How hard is it to implement a VPN?
Private data center networks as a service are easy. The complexity is limited only by the parameters of your server, its interface, firewall and applications with which you work. Keep in mind that data centers use large private networks that connect multiple servers, not just yours.
As for VPN, the initial installation is a bit more complicated, but the increased security is worth the money spent in most cases. Each VPN server must be installed and configured using common data and security configurations required for a secure connection. After you start the VPN, you need to configure the software to use the VPN tunnel.
PKI and SSL / TLS encryption
Public Key Infrastructure (PKI) is a set of systems that are designed to create, manage, and verify certificates for identifying individuals and encrypting transmitted data. After authentication, they can also be used for encrypted communication.

How does SSL increase security?
Creating a certificate authority and certificate management for servers allows everyone within the server infrastructure to encrypt their traffic and use other users' identity checks. PKI can help prevent man-in-the-middle attacks when an attacker imitates the server's behavior in your infrastructure in order to intercept traffic or spoof a message.
Each server can be configured so that all participants are authenticated through a certificate authority that creates a pair of keys: public and private. CA can distribute public keys to all participants who have a low level of trust in each other, but high in the CA. Only the latter can confirm the ownership of the public key to its owner.
If you use applications and protocols that support TLS / SSL encryption, then this is a way to reduce VPN costs (which often use SSL).
How hard is it to implement SSL?
Setting up the certificate authority and the rest of the infrastructure may require a lot of initial effort from you. In addition, certificate management is an additional administrative burden: new certificates must be created, signed and revoked if necessary.
For many users, introducing a fully-fledged public-key infrastructure makes more sense only with significant infrastructure growth. Communicating via VPN can be a good measure to protect servers until a company reaches a point where PKI and additional investments in administration are not enough.
Audit services
So far we have talked about technologies that increase the protection of servers. However, much of the security lies with the analysis of your system. Understanding the available attack surfaces and which system components to block will give you the best defense result.
Auditing is a process that shows which services are running in your server infrastructure. Often, the default operating system is configured to load and launch certain components at power up.
An audit will help you analyze which ports the system uses, which protocols are accepted. This information may help configure your firewall.
How does an audit increase security?
Servers run many processes for internal purposes and for processing external data. Each process is a potential threat to attack the server.
After you get an idea of how your infrastructure works, proceed with the analysis. For each process there are several test questions:
- Should the service be launched without permission?
- Has the service been launched in an interface that is not necessary? Should it be bound to the same IP?
- Is the work of the firewall structured correctly, if it misses the traffic of this process?
- Does your firewall allow unwanted traffic from a specific process?
- Do you have a way to receive security notifications in case of vulnerabilities for each of the services?
This type of audit is a mandatory practice of setting up any new server.
How difficult is it to implement an audit?
Basic auditing is very simple. You can find out which service is listening on each interface using the netstat command. A simple example that shows the program name, process identifier (PID), addresses to listen for TCP and UDP traffic:
sudo netstat -plunt You will see about the following result:
Active Internet connections (only servers) Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN 887/sshd tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN 919/nginx tcp6 0 0 :::22 :::* LISTEN 887/sshd tcp6 0 0 :::80 :::* LISTEN 919/nginx Notice the Proto, Local Address, and PID / Program name columns. If it says 0.0.0.0, then the service accepts connections on all interfaces.
File Auditing and Intrusion Detection System
File auditing is the process of comparing the state of the current system with the file records and characteristics of your system when it is in good condition. The method is used to detect changes that require authorization.

Intrusion Detection System (IDS) is a piece of software that monitors a system or network for unauthorized actions. Many hosting IDS use file auditing as a method of checking for changes in the system.
How does file auditing improve security?
Like the server maintenance audit from the example above, this is a very useful method for increasing security. The network administrator can periodically audit the files or this can be done automatically with the help of IDS.
File auditing is one of the few ways to make sure that your file system is not modified by any user or process. For many reasons, hackers often want to go unnoticed in order to use the server for a long time. They can replace files in the hacked version. File auditing will tell you what files have been changed, it will be confident in the integrity of your server environment.
How difficult is it to implement file auditing?
Implementing IDS or checking files can be a difficult process. The initial setup includes a description of all non-standard changes that you made on the server and all paths that need to be excluded.
Auditing makes day-to-day server management more time consuming. This complicates the upgrade procedure, as you will need to re-check the system before running the updates and after installing them to catch the changes in the software version. In addition, you will have to upload reports to a well-protected place so that the audit documents cannot be changed by the attacker.
On the one hand, audit is a burden on administration, on the other hand, it is a reliable way to protect your data from changes.
Isolated Runtime
A way to launch system components in their own allocated space.
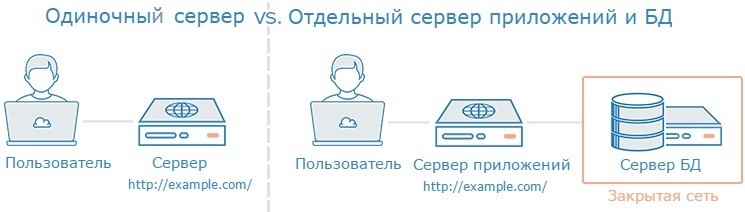
Using the sandbox, you can separate your discrete application components on separate servers. The isolation level largely depends on the system requirements of the applications and their place in your infrastructure.
How does isolated runtime improve security?
By separating your processes into separate runtimes, you increase the ability to quickly isolate any possible threats. Like compartments in ships that hold gaps in the hull and prevent the ship from sinking, the separated components of the server infrastructure will help cut off the hacker's access to other parts of the system.
How difficult is it to implement an isolated environment?
Depending on the type of shell you choose, isolation may be a simple procedure. By packaging your components in containers, you can quickly achieve good insulation performance.
Setting up the chroot environment for each part gives a certain level of isolation, but not complete. The best option is to move components to dedicated machines; this is much simpler, but more expensive.
In custody
The technologies and measures described above are just some of the enhancements you can make to secure your servers. It is important to note that the introduction of such methods of protection is very important and the sooner the better, because the longer you wait, the less effective the means of security.
In this article we consider the issue of server protection from a theoretical point of view. We will be glad to additions from practitioners. Let's put together a useful manual together!
Tell us what protection measures do you use in your practice and why do you consider them effective?
Source: https://habr.com/ru/post/314344/
All Articles