Aidra boosted botnet infected 3,500 devices in less than a week

Data about the new attack appeared from the user's blog with the nickname Unixfreakjp. His publication deals with a new, more powerful, than Mirai, botnet of the Internet of things. He managed to infect about 3,500 devices in a period of five days. Today, this attack has become the most "successful" of the likes of late. Due to the high attack speed, the number of affected bot clients has reached this level since the boot file was detected. After the attack on Dyn, this incident is likely to be only the beginning of the upcoming more unpleasant events for the entire Internet.
In this article we reveal the details of how the worm works and tell who is suspected of organizing the attack.
What a beast
Malicious software is called Linux / IRCTelnet. The program is literally stitched from pieces of code from several known and up to the last attack, malicious applications that attack devices connected to the Internet around the world.
')
Linux / IRCTelnet can be considered a new version of the source code of the Aidra botnet. Telnet's pest wrecking logic for Linux / IRCTelnet was borrowed from the Bashlight botnet. As a result, Linux / IRCTelnet contains a list of some 60 widely used login and password combinations used in Mirai. And everything continues by adding code to the sites under attack. These web platforms typically work with the new generation IPv6 Internet protocol.
Like many botnets, Linux / IRCTelnet does not have what malware experts call “persistence”, not in the traditional sense of the word. Simply put, in order to decontaminate devices that have been attacked, you must restart them and return to the factory settings. This temporary measure will help for a short time only if these devices are not additionally protected by changing account data or breaking the connection with Telnet.
When a device is infected, its ip address is entered into the database and the botnet operator will be able to re-infect it again and again, until it loses connection with the monitoring and control channel.
Parent code
Aidra was first talked about in a very bold and ethically controversial study conducted by Guerilla. Its original purpose was to measure the security level of the entire Internet. In the process, more than 420,000 Linix machines connected to the worldwide network were infected. This is how Guerilla created a truly epic botnet with the ability to scan billions of ip addresses. From an anonymous source, it is known that Aidra captured infected devices to carry out a variety of DDoS attacks. However, it worked on a limited number of gadgets (approximately 30,000 devices).
Details
On the “Malware must die!” Blog, Unixfreakjp made a very interesting and detailed analysis. Below are some excerpts from it.
It is established that the attacks occurred via the Telnet protocol from the ip addresses from the list below.
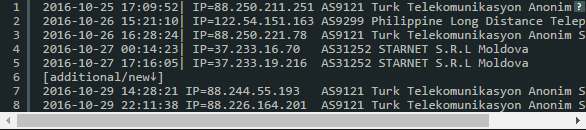
They began as a rough attempt to log in to the system and, if it worked, then the system commands were called
shell , sh , free . They were sent with the following one-line command to download and install the pest program.And after that, the botnet attack operator executed the
/etc/firewall_stop command to close the session. According to a recorded attempt to attack, all this happened in less than one second. This refers only to sending the bootloader via the Telnet protocol. The duration of the boot process is not taken into account.Below is a malware installer script.
A binary analysis of Linux / IRCTelnet showed that ELF (a Trojan script for DDoS attacks for Linux devices) is based on C ++. Mostly compiled with uClibc , except for the binary ARM, followed by the GCC compilation. In general, this is not a large-scale project. Another interesting note - ELF hardcode contains messages in Italian.
It can be assumed that the comments from the screenshot above should mean something to others. But this is not the case - messages are needed for the malicious activity of a botnet. The author of the analysis suggests that the attack could be an Italian hacker, which can be found at d3m0n3 or eVil (d4rk3v1l) from IRCNet channel # hack.it
Linux / IRCTelnet has no permanent autostart or rootkit, or anything else that could damage your gadget connected to the internet. It is common for an ELF script to place an out-of-the-box pest scheme in order to infect anew: reboot the bot, even update old versions and remove competing botnets. To achieve this goal, the Telnet protocol is great, which as an intermediary infects the selected network of devices with the loader code, and the network starts and performs its pest function. Remember that as soon as the botnet is infected, the CNC server console receives a list of recently infected nodes, so that the person controlling the attack can send a re-infection command as quickly as he realizes that one or more specific bot clients have been removed, deleted or inactive.
That is, the point here is that after an infection occurs on an Internet of Things device, the management server console is updated with a new victim. An attacker can send a command to re-infection, if he realizes that the bot client is deleted or inactive.
What's next
The silence of Brian Krebs only confirms the level of existing problems in the modern network. The fact is that this simplicity, with which new waves of DDoS attacks fall on the network, leads us to the idea that it was very easy for anyone to crack the attack two years ago for a subsequent successful attack on reputable Internet platforms. To summarize, Linux / IRCTelnet is the first messenger of the era of the new generation of malware, which readily confirms its considerable ability to harm. How quickly the number of smart devices connected to the Internet increases confirms that problems are not far off. A lot of coordinated harm can be caused to the open global Telnet service.
Previously, no one really knew about the Internet of things. Everybody was just proud of the fact that they got the network connection feature promoted by marketers. As said, it is so convenient that all information is transmitted to the network. What is convenient? Come on, why everywhere have access to your weight chart? Well, really, why on the kettle to listen to the radio or to find out the weather? True, this is extra “frills”. Constant access to the network is in fact urgently needed in any projects with distributed parts that are closed from publicity. In such places, safety is taken seriously. It turns out that what was created for profit brings an unexpected loss of global proportions.
So, if you don’t really need another one-device-connected-in-my-home-to-internet connection, disconnect it from the network, enough electrical.
Source: https://habr.com/ru/post/314324/
All Articles