Google again revealed unpatched vulnerability in Windows

Win32k.sys driver again has a problem
At first glance, it would seem that Google acted irresponsibly and violated IT etiquette, without giving Microsoft time to fix the bug. Experts Google Threat Analysis Group published the fact that there is a dangerous vulnerability in Windows just 10 days after it was reported to Microsoft. The Redmond company just physically did not have time to check the bug, test it on all configurations, prepare the patch, test it on all configurations - and roll out the update in Windows Update. Vulnerability is still not closed.
But there is one nuance. As in many other cases, the detected vulnerability has already been actively exploited by hackers. In fact, most of the closed vulnerabilities are exploited by hackers before patches are released. So the actions of Google are quite appropriate, given the high danger of the bug found. These actions will only force Microsoft to move and release the patch faster than they could have done it without a public scandal.
According to the Google Threat Analysis Group regulations , the period for publishing information about actively exploited vulnerabilities is 7 days. We can say that in this case, Microsoft gave a concession.
')
Information on previously unknown 0-day vulnerabilities in Microsoft and Adobe products were sent to these companies on October 21, 2016. Adobe updated Flash on October 26, 2016 (patch for CVE-2016-7855). This update is available through Adobe's automatic update and Chrome auto-update. Microsoft has not closed the hole so far.
Google reports some details. This is a vulnerability with elevated privileges in the Windows kernel driver, which allows you to exit the sandbox. It is triggered by the specially-formed NtSetWindowLongPtr () system call from the win32k.sys driver, which sets the GWLP_ID index to WS_CHILD for the window with the GWL_STYLE handle.
To prevent exploitation of this vulnerability prior to the release of the patch, the Chrome sandbox now blocks the win32k.sys system calls using the win32k.sys lokoduna procedure under Windows 10. Thus, the output from the sandbox is impossible.
Google urges users to check the normal operation of automatic update systems and make sure that Flash is updated to the latest version - manually or automatically. And immediately install a fresh patch for Windows as soon as it becomes available.
Apparently, this vulnerability is relevant only for the kernel driver in Windows 10. At the same time, Adobe Flash Player was vulnerable under all versions of Windows (7, 8 and 10), as well as under Linux. Vulnerability CVE-2016-7855 is also present in the Adobe Flash Player Desktop Runtime 23.0.0.185 and earlier versions for Windows and Macintosh. For operation in Windows 10, a non-patched Flash Player is required.
Adobe worked very quickly, because the vulnerability was already actively used in working malware.
Google is not the first time revealing information about open vulnerabilities in Windows. She did the same thing last year, for which she was criticized by colleagues from Microsoft . Allegedly, such actions endanger millions of Windows users. At that time, the situation was even more interesting, because Microsoft specifically asked Google to wait a few more days with disclosure - give them time to release a patch for Windows 8.1, but Google did not back down on the principles.
It seems that the two companies are just different views on the problem. Google believes that informing users about the danger only increases overall security and will force a patch to be released earlier. Microsoft believes that there is no need to bring dirty laundry to the public. Now Microsoft has commented in the same style: “We consider the right coordination of actions when disclosing information, and today's act of Google could put users at potential risk.”
Over the past few months, this is the third vulnerability with privilege escalation in win32k.sys : previous patches were released in June and August .
Compared to Microsoft, Google seems to have stricter security requirements. It is clear that in all browsers about the same number of vulnerabilities. But there is a difference in how the company-developer relates to such issues. Google policy is based on the initial installation of vulnerabilities. On this basis, the task is set to make their operation more difficult.
For example, statistics for 2015-2016 shows the minimum number of vulnerabilities in Edge and Safari: 134 and 191, respectively. At the same time, IE and Chrome are found at 346. But assess the severity of these vulnerabilities. Edge has code execution vulnerabilities of 74 (55.22% of the total), IE has 239 (69.08%), and Safari has 132 (69.11%). While Chrome - only ten pieces in two years, eight of them in 2015 and two in 2016 (2.89% of the total).
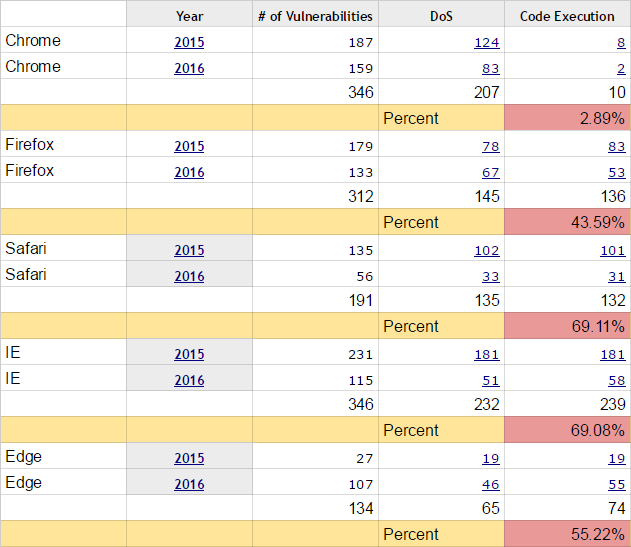
Full version of the table . Note: the table takes into account the found vulnerabilities in all versions of browsers
The patch for the latest vulnerability in Windows should be out soon.
Source: https://habr.com/ru/post/314142/
All Articles