Mass customer robbery Fix-Price
Most people think that it is very difficult to rob them, but when the shop itself helps the robbers, everything becomes much simpler. I will tell how a crowd of schoolchildren managed to enclose the store customers for huge sums and how the store employees contributed to this.
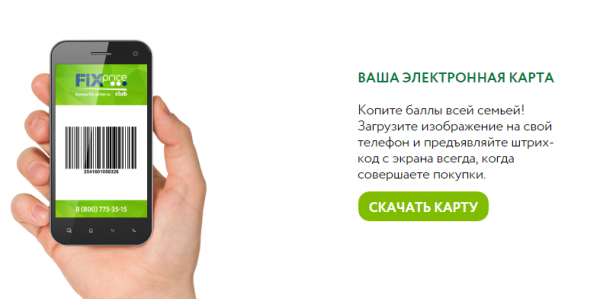
Somewhere in the beginning of summer all bonuses in the amount of ~ 800r were withdrawn from my friend's bonus card, for a student it was a lot of money that he saved for a whole year, and I wondered how the attackers managed to do it. When I entered my personal account, I was offered to download the electronic version of the card as a picture on the phone. And here I realized the full scale of the tragedy! Let's start the investigation from the very beginning:
The first factor: Weak passwords.
')
The vulnerability that cannot be closed is the man himself. I contacted the seller of the hacked accounts and he sent me the passwords for which the accounts most often came across:
Passwords are sorted by popularity. Having visited the site, it was possible to find out personal data, such as: mail, phone number, date of birth, name and address.
The second factor: Checking the number through the site
Where can I get the base number for the brut? Here the store greatly facilitated the work of intruders. During authorization, only 1 POST request was sent to the following URL:
JSON :
« », :
, , — . , , .
:
IP. . , .
, :

. , : 30 000. 30 3 !
, , .
! 50 . , ( ).
:
? :
! ? !
:
:
, .
5-
— , . , « » .
, , , .
, IDE , 10-15% . . :

:

, , , , ! , ! , , , — .

Somewhere in the beginning of summer all bonuses in the amount of ~ 800r were withdrawn from my friend's bonus card, for a student it was a lot of money that he saved for a whole year, and I wondered how the attackers managed to do it. When I entered my personal account, I was offered to download the electronic version of the card as a picture on the phone. And here I realized the full scale of the tragedy! Let's start the investigation from the very beginning:
The first factor: Weak passwords.
')
The vulnerability that cannot be closed is the man himself. I contacted the seller of the hacked accounts and he sent me the passwords for which the accounts most often came across:
1) Phone number without the eight / seven
2) Phone number with 8, 7, +7
3) 123456
4) 123456789
5) 1234567890
6) qwerty
7) fixprice
8) 111111
9) 222222
10) 12345678
11) 1234567
12) 666666
13) 123123
Passwords are sorted by popularity. Having visited the site, it was possible to find out personal data, such as: mail, phone number, date of birth, name and address.
The second factor: Checking the number through the site
Where can I get the base number for the brut? Here the store greatly facilitated the work of intruders. During authorization, only 1 POST request was sent to the following URL:
bonus.fix-price/loginJSON :
1)
2)
3)
4)
« », :
konkurs.fix-price/profile/checkmail?email=&phone=, , — . , , .
:
IP. . , .
, :

. , : 30 000. 30 3 !
, , .
! 50 . , ( ).
:
? :
hash:=sha256(2041 + )
GET bonus.fix-price/assets/fixprice/images/barcode/%hash%.png! ? !
:
:


, .
5-
— , . , « » .
, , , .
, IDE , 10-15% . . :

:

, , , , ! , ! , , , — .
Source: https://habr.com/ru/post/313926/
All Articles