Network security technologies at OSI level 2. Part 1
It would seem that by gaining access to the internal network, an attacker can relatively easily investigate neighboring nodes, collect the transmitted information and in general everything is already lost.
Nevertheless, with the correct approach to controlling the level of access, the procedures mentioned above can be significantly complicated. At the same time, a competently prepared network infrastructure, having noticed a malicious anomaly, will promptly inform about this, which will help to reduce damage.
Under the cat a list of mechanisms that will help to perform this function.
I would like to give a general squeeze without extra wiki justifications, but with a description of configuration variations, I nonetheless sometimes retreat to the educational program, so that the article would seem more friendly to the outsider.
')
The article was voluminous, and, in my opinion, too large articles are not readable, but fold into a closet with the thought of “somehow mastering”. Therefore, the material had to be divided, and with due success I would make the second part with less common (at least with us) technologies.
Content:
The technologies are described on the basis of a Cisco switch, specifically my test model and version are as follows:

I suppose that this vendor is the most common, and even the most informationally rich, and causes a lot of interest among beginners to study such topics.
Nevertheless, I am sure that after mastering each specific technology on a tsiska, it will not be difficult to correctly configure another vendor if you have 30 minutes. and the usual user guide.
I believe that the information does not duplicate the already existing one in Habré, although something similar can be found here and here .
The technology is designed to control devices connected to the switch and prevent anomalies or attacks aimed at overflowing the MAC address table (CAM table overflow).
With the help of Port Security, the maximum number of MAC addresses is set to a specific switchport (a network port operating on the 2nd OSI level) or VLAN, and access to specified MAC addresses is controlled.
Port-Security can only be activated if the switchport type is explicitly set (ie, either Access or Trunk). If the port is dynamic (which is already wrong), Port-Security cannot be enabled on it.
The technology is defined using the switchport port-security ... command in the specific interface configuration mode, the available options are:
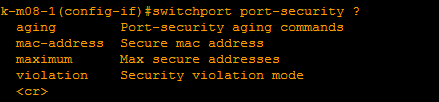
Install what you need, what you do not need to skip.
As a result, it looks like this:
The same, only you can specify the behavior is not relative to the physical interface, and a specific VLAN'a. For this, vlan is added to each of the previous commands at the end.
Without resorting to show run, information regarding Port-Security can be found:
The technology prevents the use of an unauthorized DHCP server on the network, which allows for example to make a man-in-the-middle attack (man-in-the-middle, MITM). It also protects the network from DHCP depletion attacks (DHCP starvation / exauction), which is not very relevant.
The technology monitors DHCP communication on the network, which (mainly) consists of four packets:
Before activating DHCP snooping, you must specify the "trusted" port (s) that the DHCP server is behind. Only trusted ports will transmit DHCP Offer and DHCP ACK (packets from the server). In this connection, no device behind other interfaces of this switch can perform the work of a DHCP server, offering its own network configuration options.
It is very important that after activating DHCP snooping, the switch begins to monitor DHCP communication on the network and identify the issued IP addresses with the MAC addresses of the requesting devices, storing this information in the DHCP snooping binding table.
Under the trusted interface, the

To prevent DHCP starvation under untrusted interfaces, specify the frequency of received client requests using

It is important not to underestimate this characteristic so as not to cut the valid traffic. Tsisk advises to use the number "10".
After that, we specify a specific VLAN for DHCP snooping to work and directly enable the technology itself with a command without options:
The technology is designed to prevent ARP spoofing / poisoning attacks, which is the basic way of organizing traffic interception (again, man-in-the-middle / MITM attack) while in the same broadcast domain with the victim.
In order to effectively prevent ARP spoofing, the switch must have the MAC address / IP address bundle information. As mentioned above, this information is stored in the DHCP snooping table. Therefore, the correct configuration of these two technologies almost always uses together.
When used together with DHCP snooping, the technology is activated in global configuration mode with the command:
After that, only devices that appear in the DHCP snooping table will be allowed in this VLAN.
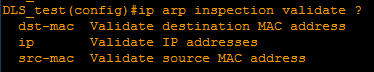
In case the devices do NOT use DHCP, additional measures should be taken. ARP inspection allows the use of static records. For this, ARP access lists are created, which is created from the global configuration mode with the command:
The syntax of a single entry is below:
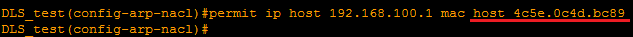
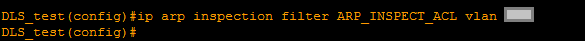
Under this arp access-list, all the necessary static entries are listed. Further, the technology is activated not as before, but with the filter option:
Separate interface (s) can be marked as trusted. There will be no ARP inspection on these interfaces:

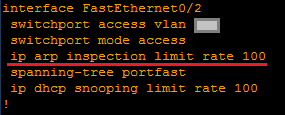
Trunk ports are installed almost always trusted (the most important thing is not to forget about this before activating the whole mechanism). But in this case it is important to raise the default limit of ARP messages - it is equal to 15, and may be too narrow, especially for a trunk. I advise you to put 100-ku:
Optionally, you can add additional checks for compliance with MAC addresses in the ARP and Ethernet headers. This is done with the
The functionality for each option can be read separately here .
Check the status of the technology, whether it is enabled, whether it uses the access list, the status of checking additional options, etc. information:
Useful options for the previous command (add at the end of the line) are statistics (shows drop counters, etc.) and interfaces (trusted interfaces, ARP message limits).
If there is no need to check the entire subnet by ARP inspection, but I would like to protect a couple of nodes from such threats, you can use Source Guard. In practice, their functionality duplicates each other, although there are nuances.
The technology binds the specified IP-MAC to a specific physical interface. As a result, ARP also prevents spoofing, and one network node will not be able to send traffic on behalf of another, replacing the source's IP and MAC addresses (in the case of ARP inspection, this is possible, although it is not critical).
Source Guard also uses a DHCP snooping table. It contains not only the IP-MAC bundle, but also another interface, behind which there is a specific node.
If the nodes again do not use DHCP, a manual entry is created in the global configuration mode:
Source Guard is activated directly on the interface:
Verification of records that technology uses is performed by the command:
show ip source binding
What is useful, the command displays both manual records and those taken from the DHCP snooping table.
The list of interfaces on which Source Guard is activated is displayed by the command:
show ip verify source
Next time I will show you what other access lists are on switches and why they are needed; how to control communication within the same subnet; I will try to highlight the intricacies of the interface transition to the errdisable status and it may be possible to understand whether MACsec is needed at all.

Nevertheless, with the correct approach to controlling the level of access, the procedures mentioned above can be significantly complicated. At the same time, a competently prepared network infrastructure, having noticed a malicious anomaly, will promptly inform about this, which will help to reduce damage.
Under the cat a list of mechanisms that will help to perform this function.
I would like to give a general squeeze without extra wiki justifications, but with a description of configuration variations, I nonetheless sometimes retreat to the educational program, so that the article would seem more friendly to the outsider.
')
The article was voluminous, and, in my opinion, too large articles are not readable, but fold into a closet with the thought of “somehow mastering”. Therefore, the material had to be divided, and with due success I would make the second part with less common (at least with us) technologies.
Content:
The technologies are described on the basis of a Cisco switch, specifically my test model and version are as follows:

I suppose that this vendor is the most common, and even the most informationally rich, and causes a lot of interest among beginners to study such topics.
Nevertheless, I am sure that after mastering each specific technology on a tsiska, it will not be difficult to correctly configure another vendor if you have 30 minutes. and the usual user guide.
I believe that the information does not duplicate the already existing one in Habré, although something similar can be found here and here .
Port security
Description
The technology is designed to control devices connected to the switch and prevent anomalies or attacks aimed at overflowing the MAC address table (CAM table overflow).
With the help of Port Security, the maximum number of MAC addresses is set to a specific switchport (a network port operating on the 2nd OSI level) or VLAN, and access to specified MAC addresses is controlled.
Ways to work with MAC-addresses:
- Dynamic - passes and remembers (for a specified period of time) any MAC addresses until it reaches the allowed maximum;
- Static - allows only the MAC address previously entered by hands (can be used together with the Dynamic type);
- Sticky - learns new MAC addresses by writing them to the configuration;
Actions in case of exceeding the authority:
- Potect - in the case of unnecessary or not specified MAC addresses, it does not allow new ones, does not generate a syslog or SNMP trap, does not drop the interface;
- Restrict is the same as Protect, but plus a log and / or SNMP trap. It also reports to the counter under
show port-security interface <name>: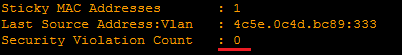
- Shutdown (selected by default) - the previous action, but plus the interface goes into the status of errdisable and stops transmitting traffic;
- Shutdown VLAN - like the previous one, only all interfaces in this VLAN are transferred to errdisable;
Configuration
Port-Security can only be activated if the switchport type is explicitly set (ie, either Access or Trunk). If the port is dynamic (which is already wrong), Port-Security cannot be enabled on it.
Access ports
The technology is defined using the switchport port-security ... command in the specific interface configuration mode, the available options are:

- aging - sets the time interval after which the dynamic MAC address can be rewritten;
- mac-address - gives access to the following branch:
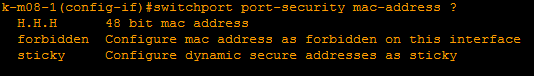
those. we set the allowed / forbidden addresses or tell the hardware to teach them; - maximum - we specify the limit of allowed addresses.
- violation - set the action listed above.
Install what you need, what you do not need to skip.
switchport port-security activate the technology with the command switchport port-security with no options.As a result, it looks like this:
- If we want to allow unknown which poppies, limiting their number to the 5th, set a maximum of 5 and do not set anything statically. Optionally specify the time of life.
- If it is known that the device is at the second end of the wire and nothing else will be there and should not be - maximum = 1, we prescribe the address statically.
- If we are waiting for a new employee with a new PC or too lazy to find out the MAC address, we put Sticky, after connecting, we recheck.
Trunk ports
The same, only you can specify the behavior is not relative to the physical interface, and a specific VLAN'a. For this, vlan is added to each of the previous commands at the end.
Check
Without resorting to show run, information regarding Port-Security can be found:
show port-security- displays a summary of information about interfaces, their status, the number of addresses;show interface <name> switchport- more detailed information (counters, individual options);show mac address-table ..plus option, the list below: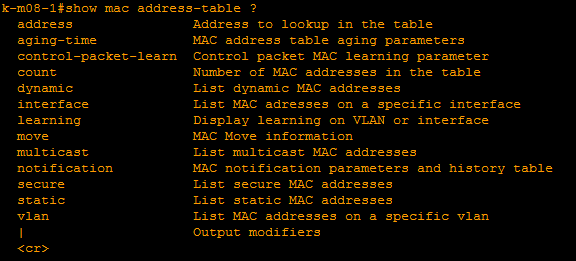
The command checks the current information on the MAC address table. For example, the current number of records in a table for a specific VLAN and the volume of available records is checked usingshow mac address-table count vlan <id>: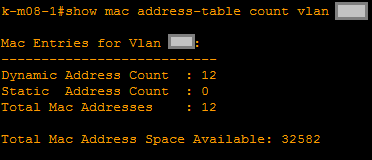
DHCP snooping
Description
The technology prevents the use of an unauthorized DHCP server on the network, which allows for example to make a man-in-the-middle attack (man-in-the-middle, MITM). It also protects the network from DHCP depletion attacks (DHCP starvation / exauction), which is not very relevant.
The technology monitors DHCP communication on the network, which (mainly) consists of four packets:
- DHCP Discover — only the client sends a request for receiving IP via DHCP;
- DHCP Offer - sends only server, configuration offer from DHCP server;
- DHCP Request - sends only the client, the choice of a specific configuration and server;
- DHCP ACK - sends only the server, the final confirmation;
Before activating DHCP snooping, you must specify the "trusted" port (s) that the DHCP server is behind. Only trusted ports will transmit DHCP Offer and DHCP ACK (packets from the server). In this connection, no device behind other interfaces of this switch can perform the work of a DHCP server, offering its own network configuration options.
It is very important that after activating DHCP snooping, the switch begins to monitor DHCP communication on the network and identify the issued IP addresses with the MAC addresses of the requesting devices, storing this information in the DHCP snooping binding table.
Configuration
Under the trusted interface, the
ip dhcp snooping trust command is entered:
To prevent DHCP starvation under untrusted interfaces, specify the frequency of received client requests using
ip dhcp snooping limit rate <nr> :
It is important not to underestimate this characteristic so as not to cut the valid traffic. Tsisk advises to use the number "10".
After that, we specify a specific VLAN for DHCP snooping to work and directly enable the technology itself with a command without options:
(config)# ip dhcp snooping vlan <id> (config)# ip dhcp snooping Check
- show ip dhcp snooping — displays trusted ports and VLANs on which DHCP snooping is enabled;
- show ip dhcp snooping binding - shows the same table, where the IP-MAC binding within VLANs with DHCP snooping enabled is featured:
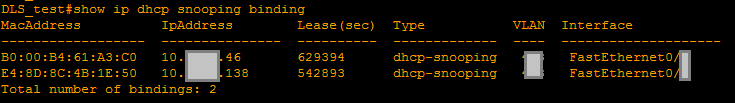
Dynamic ARP inspection
Description
The technology is designed to prevent ARP spoofing / poisoning attacks, which is the basic way of organizing traffic interception (again, man-in-the-middle / MITM attack) while in the same broadcast domain with the victim.
Configuration
In order to effectively prevent ARP spoofing, the switch must have the MAC address / IP address bundle information. As mentioned above, this information is stored in the DHCP snooping table. Therefore, the correct configuration of these two technologies almost always uses together.
When used together with DHCP snooping, the technology is activated in global configuration mode with the command:
(config)# ip arp inspection vlan <id> After that, only devices that appear in the DHCP snooping table will be allowed in this VLAN.
In case the devices do NOT use DHCP, additional measures should be taken. ARP inspection allows the use of static records. For this, ARP access lists are created, which is created from the global configuration mode with the command:
(config)# arp access-list <name> The syntax of a single entry is below:

And also ..
In addition to specifying a single MAC address, you can specify a range in the arp access-list. And this is done by ! reverse ARP ! masks:

In my opinion, this is a terrible crutch and the world has gone mad, but if there is no other way ..

In my opinion, this is a terrible crutch and the world has gone mad, but if there is no other way ..
Under this arp access-list, all the necessary static entries are listed. Further, the technology is activated not as before, but with the filter option:

Separate interface (s) can be marked as trusted. There will be no ARP inspection on these interfaces:

Trunk ports are installed almost always trusted (the most important thing is not to forget about this before activating the whole mechanism). But in this case it is important to raise the default limit of ARP messages - it is equal to 15, and may be too narrow, especially for a trunk. I advise you to put 100-ku:

Optionally, you can add additional checks for compliance with MAC addresses in the ARP and Ethernet headers. This is done with the
ip arp inspection validate <option> command:
The functionality for each option can be read separately here .
Check
Check the status of the technology, whether it is enabled, whether it uses the access list, the status of checking additional options, etc. information:
show ip arp inspection vlan <id> Useful options for the previous command (add at the end of the line) are statistics (shows drop counters, etc.) and interfaces (trusted interfaces, ARP message limits).
Source guard
Description
If there is no need to check the entire subnet by ARP inspection, but I would like to protect a couple of nodes from such threats, you can use Source Guard. In practice, their functionality duplicates each other, although there are nuances.
The technology binds the specified IP-MAC to a specific physical interface. As a result, ARP also prevents spoofing, and one network node will not be able to send traffic on behalf of another, replacing the source's IP and MAC addresses (in the case of ARP inspection, this is possible, although it is not critical).
Configuration
Source Guard also uses a DHCP snooping table. It contains not only the IP-MAC bundle, but also another interface, behind which there is a specific node.
If the nodes again do not use DHCP, a manual entry is created in the global configuration mode:
(config)# ip source binding <mac.add.ress> vlan <id> <IP.add.re.ss> interface <name> Source Guard is activated directly on the interface:
(config-if)# ip verify source port-security Check
Verification of records that technology uses is performed by the command:
show ip source binding
What is useful, the command displays both manual records and those taken from the DHCP snooping table.
The list of interfaces on which Source Guard is activated is displayed by the command:
show ip verify source
I think that's enough for now
Next time I will show you what other access lists are on switches and why they are needed; how to control communication within the same subnet; I will try to highlight the intricacies of the interface transition to the errdisable status and it may be possible to understand whether MACsec is needed at all.
Source: https://habr.com/ru/post/313782/
All Articles