Security in IoT: Azure IoT Suite for those who start from scratch
Introducing the translation of a series of articles on security in IoT. The first material is an overview of the capabilities of Microsoft Azure IoT Suite.

1. Azure IoT Suite for those who start from scratch .
2. A comprehensive protection strategy .
3. Security system architecture .
4. Secure the deployment of IoT .
Note: further narration will be conducted on behalf of the author.
')
Azure IoT Suite is a complete solution with integrated security tools that provide protection at all levels. At Microsoft, software security is an integral part of the development process in accordance with the established principles for building reliable and secure software over the decades. This is accomplished using the Secure Application Development Lifecycle (SDL) —a basic software development method combined with the Operational Security Assurance (OSA) suite of services, as well as the Microsoft Digital Crimes Unit, the Microsoft Security Response Center, and the Microsoft Malware Protection Center. programs).
The Azure IoT Suite provides unique features that allow you to easily, visually and, most importantly, securely prepare an IoT device for operation, connect to it, and store the data coming from it. In this article, we look at the security components and deployment strategies of the Azure IoT Suite, which provide robust protection, privacy and compliance.
The Internet of Things (IoT) is a technology that today gives companies a real opportunity to cut costs, increase profits and transform their business. However, many companies are hesitant to move to actively deploying IoT technologies, because they do not feel confident about security, confidentiality and compliance. The most disturbing thing is the unique IoT infrastructure in which the digital world integrates with the physical. At the same time, of course, the risks characteristic of both worlds also increase. The security of the IoT infrastructure depends on the integrity of the code running on the devices. This code is used to verify the authenticity of the device and users, determine the ownership of the device (and the data generated by it), as well as protect it against network and physical attacks of intruders.
Finally, a privacy issue. Companies need transparency in data transfer. They need to understand what kind of data is collected and why, who can view it, who controls access, and so on. No less important are general issues related to the safety of equipment and the safety of operators during operation, as well as problems of compliance with industry standards.
Given the numerous requirements for security, confidentiality, transparency, and compliance, choosing an IoT solution provider becomes a very difficult task. If a single solution combines separate applications and IoT services from different providers, then security, privacy, and compliance vulnerabilities are simply unavoidable. Often they are incredibly difficult to even detect, not to mention the elimination. A reliable IoT software and services provider should have extensive experience in developing such services that cover different levels of infrastructure, take into account geographic location, and also provide tools for safe and transparent horizontal scaling. A great advantage for the selected supplier will also be many years of experience in the development of secure software installed on billions of computers worldwide, as well as the ability to quickly and professionally evaluate and eliminate the threats associated with the implementation of the Internet of Things technology.
Over a billion customers in 127 countries use the Microsoft Cloud infrastructure. Our rich long-term experience in developing corporate software and supporting the largest network services allows us to provide such a level of security, confidentiality, compliance and elimination of risks that most customers could hardly achieve on their own.
The Microsoft Secure Application Development ( SDL ) development life cycle allows you to forcibly include all company levels in the development process, which aims to introduce security components throughout the software life cycle. To ensure that our operations processes comply with all safety requirements, we use strict security policies developed as part of the Operational Security Assurance (OSA) process. We collaborate with third-party audit service providers, engaging them to verify compliance with all requirements and regulations. We also take appropriate security measures when setting up competence centers (the Microsoft Digital Crimes Unit, the Microsoft Security Response Center and the Microsoft Malware Protection Center).
Microsoft Azure is a complete cloud solution that combines an ever-expanding set of integrated cloud services (analytics, machine learning, storage, security, network and web services) with industry leading data protection and privacy technologies. Our hacking strategy is implemented by the “red team” of software security experts. By simulating attacks, they test Azure’s ability to detect emerging threats, as well as provide effective data protection and recovery. Our global incident response specialists work around the clock, seven days a week, to help users deal with the effects of attacks and malicious actions. Our specialists adhere to established procedures for managing incidents, informing users and eliminating the consequences of an attack, interacting through the most transparent and predictable channels with partners both inside and outside the organization.
Our systems continuously detect and prevent intrusions, block attacks on services, regularly perform penetration tests, and make extensive use of analytical tools that help detect and eliminate threats in a timely manner. Multi-factor authentication provides an additional level of security when end users access the network. For application and remote access providers, we offer full access control, vulnerability monitoring and antivirus scanning tools, as well as patches and configuration tools.
The Microsoft Azure IoT Suite contains the built-in security and privacy features of the Azure platform, as well as SDL and OSA processes — all used to securely develop and operate Microsoft software. Using these procedures, infrastructure and network protection are implemented, as well as identification and management functions that are key to ensuring security within any solution.
The Azure IoT Hub component of the IoT Suite is a fully managed service that provides reliable protection for two-way data exchange between IoT devices and Azure services (for example, Azure and Azure Stream Analytics machine learning services) by using individual credentials for each specific device and access control to it.
In order to more fully present the embedded security and privacy components of the Azure IoT Suite, we look at the software package in the context of the three main areas of security:
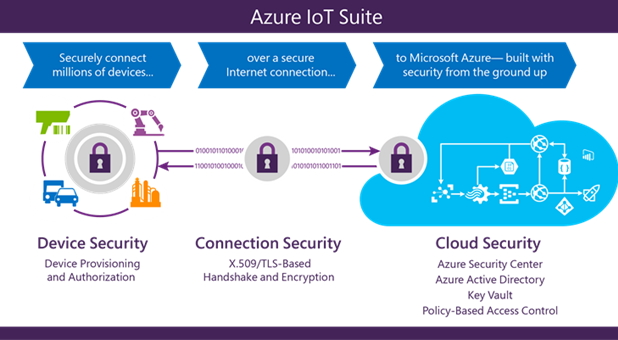
Azure IoT Suite protects devices while they are working in the field. To do this, each device is configured with a unique identity key, which the infrastructure uses to communicate with the working device. Setting up this procedure is not complicated and does not take much time. A token is created based on the key with the device identifier specified by the user, which is subsequently used in all data transfers between the device and the Azure IoT Hub service.
You can associate identifiers with devices at the manufacturing stage (that is, add them to a hardware trusted model) or use existing fixed credentials (for example, the CPU serial number) as a proxy. Changing these device IDs is not easy, but it is also important to use logical identifiers. Thus, even with a change in the basic hardware characteristics of the device, its logical characteristics will remain the same. In some cases, the device identity mapping can be performed at the deployment stage (that is, the technician physically configures the new device directly in the data exchange process with the server part of the IoT solution). The Azure IoT Hub Identity Registry is designed to securely store device identities, as well as solution security keys. By adding white or blacklisted individual device identities or groups of identities, you can fully control access to devices.
Using the access control policies in the cloud environment implemented in the Azure IoT Hub, you can enable or disable any device identity, and also, if necessary, cancel the device mapping with the IoT deployment. Mapping and unmapping device mappings are performed using the credentials of each specific device.
Additionally, you can use the following device security features:
Continuous and stable data exchange is critical to any IoT solution. Especially important is the continuity of the delivery of commands and receiving data from the device, given that IoT devices are connected via the Internet or other similar networks, and such a connection may be unreliable. Using a system to send confirmations for received messages, Azure IoT Hub provides the necessary stability when exchanging data between the cloud and the device. By caching messages in the IoT Hub service, the resiliency of messaging is enhanced. Cached messages are stored for seven (telemetry) or two days (commands).
It is imperative to ensure efficiency in resource conservation and work in an environment with limited resources. HTTPS (HTTP Secure) is an industry standard protected version of the popular HTTP protocol. In Azure IoT Hub, the HTTPS protocol is responsible for the most efficient data exchange. The AMQP and MQTT protocols, which are also supported by Azure IoT Hub, not only provide efficiency in terms of resource consumption, but also ensure reliable message delivery.
Scaling requires secure interaction with a wide variety of devices. Azure IoT Hub provides a secure connection to devices that support and do not support IP. IP-enabled devices can directly connect to the IoT Hub service and exchange data with it over a secure connection. Non-IP-enabled devices use limited resources and can only establish a connection using data exchange protocols with a small range (Z-Wave, ZigBee and Bluetooth).
The field gateway is used to aggregate these devices and broadcast the protocol, which provides secure two-way data exchange with the cloud.
Additionally, you can use the following connection security features:
Azure IoT Hub guarantees comprehensive protection at all levels of data transfer - from encryption to processing in the cloud. The service provides the necessary flexibility and adaptability, allowing the use of additional methods of encrypting security keys and advanced key management functions. Azure Active Directory (AAD) is used to authenticate and authorize users in Azure IoT Hub. Azure IoT Suite implements a policy-based data authorization in the cloud that simplifies access control and provides the ability to validate and audit. It allows you to almost instantly revoke permissions to access data in the cloud and block devices connected to Azure IoT Suite.
Data transferred to the cloud can be processed and stored in any user-defined workflow. Azure Active Directory manages access to different data partitions depending on the storage service being used.
All keys used by the IoT infrastructure are stored in a secure cloud storage. They can be changed in case they need to be re-submitted. The data is stored in a DocumentDB database or in SQL databases , which allows you to determine the required security levels. In addition, Azure has effective tools for monitoring and auditing data access, notifying the user of intrusions or unauthorized access.
The Internet of Things begins with things. From the very things that are most important for modern companies. IoT technology gives companies incredible benefits - reducing costs, increasing profits and transforming business. The success of such a transformation largely depends on the choice of a reliable supplier of software and services IoT. In other words, you need to find a supplier who will not only be able to understand all your needs and help you competently transform your business, but also provide applications and services that guarantee security, privacy protection, transparency and compliance.
Microsoft Azure IoT Suite offers built-in security and secure resource monitoring tools. These tools will improve productivity and operational efficiency, innovate and use advanced data analysis technologies to transform business. The multi-layered security approach, the various security components and the Azure IoT Suite architecture patterns all help you deploy the infrastructure that will become a reliable assistant in transforming your business.
All pre-configured solutions within Azure IoT Suite create the following instances of Azure services:
IoT Suite:
If you see an inaccuracy of the translation, please let us know in your private messages.

Cycle of articles "Security in IoT"
1. Azure IoT Suite for those who start from scratch .
2. A comprehensive protection strategy .
3. Security system architecture .
4. Secure the deployment of IoT .
Note: further narration will be conducted on behalf of the author.
')
Azure IoT Suite is a complete solution with integrated security tools that provide protection at all levels. At Microsoft, software security is an integral part of the development process in accordance with the established principles for building reliable and secure software over the decades. This is accomplished using the Secure Application Development Lifecycle (SDL) —a basic software development method combined with the Operational Security Assurance (OSA) suite of services, as well as the Microsoft Digital Crimes Unit, the Microsoft Security Response Center, and the Microsoft Malware Protection Center. programs).
The Azure IoT Suite provides unique features that allow you to easily, visually and, most importantly, securely prepare an IoT device for operation, connect to it, and store the data coming from it. In this article, we look at the security components and deployment strategies of the Azure IoT Suite, which provide robust protection, privacy and compliance.
Introduction
The Internet of Things (IoT) is a technology that today gives companies a real opportunity to cut costs, increase profits and transform their business. However, many companies are hesitant to move to actively deploying IoT technologies, because they do not feel confident about security, confidentiality and compliance. The most disturbing thing is the unique IoT infrastructure in which the digital world integrates with the physical. At the same time, of course, the risks characteristic of both worlds also increase. The security of the IoT infrastructure depends on the integrity of the code running on the devices. This code is used to verify the authenticity of the device and users, determine the ownership of the device (and the data generated by it), as well as protect it against network and physical attacks of intruders.
Finally, a privacy issue. Companies need transparency in data transfer. They need to understand what kind of data is collected and why, who can view it, who controls access, and so on. No less important are general issues related to the safety of equipment and the safety of operators during operation, as well as problems of compliance with industry standards.
Given the numerous requirements for security, confidentiality, transparency, and compliance, choosing an IoT solution provider becomes a very difficult task. If a single solution combines separate applications and IoT services from different providers, then security, privacy, and compliance vulnerabilities are simply unavoidable. Often they are incredibly difficult to even detect, not to mention the elimination. A reliable IoT software and services provider should have extensive experience in developing such services that cover different levels of infrastructure, take into account geographic location, and also provide tools for safe and transparent horizontal scaling. A great advantage for the selected supplier will also be many years of experience in the development of secure software installed on billions of computers worldwide, as well as the ability to quickly and professionally evaluate and eliminate the threats associated with the implementation of the Internet of Things technology.
Secure infrastructure from scratch
Over a billion customers in 127 countries use the Microsoft Cloud infrastructure. Our rich long-term experience in developing corporate software and supporting the largest network services allows us to provide such a level of security, confidentiality, compliance and elimination of risks that most customers could hardly achieve on their own.
The Microsoft Secure Application Development ( SDL ) development life cycle allows you to forcibly include all company levels in the development process, which aims to introduce security components throughout the software life cycle. To ensure that our operations processes comply with all safety requirements, we use strict security policies developed as part of the Operational Security Assurance (OSA) process. We collaborate with third-party audit service providers, engaging them to verify compliance with all requirements and regulations. We also take appropriate security measures when setting up competence centers (the Microsoft Digital Crimes Unit, the Microsoft Security Response Center and the Microsoft Malware Protection Center).
Microsoft Azure - reliable and secure IoT infrastructure for a company of any profile
Microsoft Azure is a complete cloud solution that combines an ever-expanding set of integrated cloud services (analytics, machine learning, storage, security, network and web services) with industry leading data protection and privacy technologies. Our hacking strategy is implemented by the “red team” of software security experts. By simulating attacks, they test Azure’s ability to detect emerging threats, as well as provide effective data protection and recovery. Our global incident response specialists work around the clock, seven days a week, to help users deal with the effects of attacks and malicious actions. Our specialists adhere to established procedures for managing incidents, informing users and eliminating the consequences of an attack, interacting through the most transparent and predictable channels with partners both inside and outside the organization.
Our systems continuously detect and prevent intrusions, block attacks on services, regularly perform penetration tests, and make extensive use of analytical tools that help detect and eliminate threats in a timely manner. Multi-factor authentication provides an additional level of security when end users access the network. For application and remote access providers, we offer full access control, vulnerability monitoring and antivirus scanning tools, as well as patches and configuration tools.
The Microsoft Azure IoT Suite contains the built-in security and privacy features of the Azure platform, as well as SDL and OSA processes — all used to securely develop and operate Microsoft software. Using these procedures, infrastructure and network protection are implemented, as well as identification and management functions that are key to ensuring security within any solution.
The Azure IoT Hub component of the IoT Suite is a fully managed service that provides reliable protection for two-way data exchange between IoT devices and Azure services (for example, Azure and Azure Stream Analytics machine learning services) by using individual credentials for each specific device and access control to it.
In order to more fully present the embedded security and privacy components of the Azure IoT Suite, we look at the software package in the context of the three main areas of security:

Secure Device Preparation and Authentication
Azure IoT Suite protects devices while they are working in the field. To do this, each device is configured with a unique identity key, which the infrastructure uses to communicate with the working device. Setting up this procedure is not complicated and does not take much time. A token is created based on the key with the device identifier specified by the user, which is subsequently used in all data transfers between the device and the Azure IoT Hub service.
You can associate identifiers with devices at the manufacturing stage (that is, add them to a hardware trusted model) or use existing fixed credentials (for example, the CPU serial number) as a proxy. Changing these device IDs is not easy, but it is also important to use logical identifiers. Thus, even with a change in the basic hardware characteristics of the device, its logical characteristics will remain the same. In some cases, the device identity mapping can be performed at the deployment stage (that is, the technician physically configures the new device directly in the data exchange process with the server part of the IoT solution). The Azure IoT Hub Identity Registry is designed to securely store device identities, as well as solution security keys. By adding white or blacklisted individual device identities or groups of identities, you can fully control access to devices.
Using the access control policies in the cloud environment implemented in the Azure IoT Hub, you can enable or disable any device identity, and also, if necessary, cancel the device mapping with the IoT deployment. Mapping and unmapping device mappings are performed using the credentials of each specific device.
Additionally, you can use the following device security features:
- Devices do not accept unsolicited incoming connections. Supports only outgoing connections and routes. In order to receive commands from the server, the device must independently initiate the connection and check for the presence of commands waiting to be processed. Once a secure connection has been established between the device and the IoT Hub service, encryption is not required for exchanging messages between the cloud environment and the device, as well as between different devices.
- Devices can connect and install routes only to known trusted services that are at the same level as it (for example, Azure IoT Hub).
- For authorization and authentication at the system level, device identities are used, which allows you to almost instantly revoke credentials and access permissions.
Secure connection
Continuous and stable data exchange is critical to any IoT solution. Especially important is the continuity of the delivery of commands and receiving data from the device, given that IoT devices are connected via the Internet or other similar networks, and such a connection may be unreliable. Using a system to send confirmations for received messages, Azure IoT Hub provides the necessary stability when exchanging data between the cloud and the device. By caching messages in the IoT Hub service, the resiliency of messaging is enhanced. Cached messages are stored for seven (telemetry) or two days (commands).
It is imperative to ensure efficiency in resource conservation and work in an environment with limited resources. HTTPS (HTTP Secure) is an industry standard protected version of the popular HTTP protocol. In Azure IoT Hub, the HTTPS protocol is responsible for the most efficient data exchange. The AMQP and MQTT protocols, which are also supported by Azure IoT Hub, not only provide efficiency in terms of resource consumption, but also ensure reliable message delivery.
Scaling requires secure interaction with a wide variety of devices. Azure IoT Hub provides a secure connection to devices that support and do not support IP. IP-enabled devices can directly connect to the IoT Hub service and exchange data with it over a secure connection. Non-IP-enabled devices use limited resources and can only establish a connection using data exchange protocols with a small range (Z-Wave, ZigBee and Bluetooth).
The field gateway is used to aggregate these devices and broadcast the protocol, which provides secure two-way data exchange with the cloud.
Additionally, you can use the following connection security features:
- Data exchange between devices and / or gateways and Azure IoT Hub is secured using industry standard TLS protocol. Azure IoT Hub authentication is performed using the X.509 protocol.
- To protect devices from unsolicited incoming connections, Azure IoT Hub blocks all connection requests to this device. The device always initiates connections on its own.
- Azure IoT Hub stores messages addressed to devices in secure storage and waits until the device initiates a connection on its own. Commands are stored for two days, which allows devices to sporadically establish a connection to receive commands, if this is necessary due to the nature of the power supply or connectivity. Azure IoT Hub also creates a separate queue for each device.
Secure handling and storage in the cloud
Azure IoT Hub guarantees comprehensive protection at all levels of data transfer - from encryption to processing in the cloud. The service provides the necessary flexibility and adaptability, allowing the use of additional methods of encrypting security keys and advanced key management functions. Azure Active Directory (AAD) is used to authenticate and authorize users in Azure IoT Hub. Azure IoT Suite implements a policy-based data authorization in the cloud that simplifies access control and provides the ability to validate and audit. It allows you to almost instantly revoke permissions to access data in the cloud and block devices connected to Azure IoT Suite.
Data transferred to the cloud can be processed and stored in any user-defined workflow. Azure Active Directory manages access to different data partitions depending on the storage service being used.
All keys used by the IoT infrastructure are stored in a secure cloud storage. They can be changed in case they need to be re-submitted. The data is stored in a DocumentDB database or in SQL databases , which allows you to determine the required security levels. In addition, Azure has effective tools for monitoring and auditing data access, notifying the user of intrusions or unauthorized access.
Conclusion
The Internet of Things begins with things. From the very things that are most important for modern companies. IoT technology gives companies incredible benefits - reducing costs, increasing profits and transforming business. The success of such a transformation largely depends on the choice of a reliable supplier of software and services IoT. In other words, you need to find a supplier who will not only be able to understand all your needs and help you competently transform your business, but also provide applications and services that guarantee security, privacy protection, transparency and compliance.
Microsoft Azure IoT Suite offers built-in security and secure resource monitoring tools. These tools will improve productivity and operational efficiency, innovate and use advanced data analysis technologies to transform business. The multi-layered security approach, the various security components and the Azure IoT Suite architecture patterns all help you deploy the infrastructure that will become a reliable assistant in transforming your business.
additional information
All pre-configured solutions within Azure IoT Suite create the following instances of Azure services:
- Azure IoT Hub . The gateway through which the connection is established between the cloud and "things". You can scale your infrastructure by configuring millions of connections to each hub, and process huge amounts of data using all device authentication, which guarantees security and protection for the entire solution.
- Azure DocumentDB . Scalable, fully indexable database service that is used to store semi-structured data. It manages device metadata (attributes, configuration, and security settings) when preparing them for operation. DocumentDB provides high performance and throughput in data processing, as well as indexing without regard to the schema and an improved interface for creating SQL queries.
- Azure Stream Analytics . Thanks to streaming processing in the cloud in real time, you can quickly develop and deploy low-cost analytical solutions to analyze data from devices, sensors, infrastructure elements and applications in real time. Data obtained from this fully managed service can be scaled without restriction, while maintaining high throughput, robustness and low latency.
- Azure App Services . A cloud-based platform for developing powerful web and mobile applications that can connect to data both in the cloud and locally. Development of attractive mobile applications for iOS, Android and Windows platforms. Built-in connectivity to dozens of cloud services and enterprise applications provide the ability to integrate with SaaS applications and enterprise software. With the ability to write code in your preferred language and the IDE interface (.NET, NodeJS, PHP, Python, or Java), you can create web applications and APIs even faster.
- Logic applications . The application logic feature in Azure Application Service allows you to integrate an IoT solution into existing business systems and effectively automate workflows. , — , - . Logic applications also provide built-in connectivity to the SaaS ecosystem, the cloud environment, and local applications.
- Binary storage . , .
Useful materials
IoT Suite:
- .
- IoT Suite: .
If you see an inaccuracy of the translation, please let us know in your private messages.
Source: https://habr.com/ru/post/313762/
All Articles