IT bulldogs under the carpet
And we will talk today about the complex relationships between American IT vendors and special services: about the global IT backstage, the Yahoo scandal, the secret of the backdoor at Juniper, the history of Apple vs the FBI. We will also discuss why the NSA paid RSA $ 10 million for a crypto-backdoor. Let's try to draw a few strokes of the modern IT world as it is, and without too much fuss and paranoid conclusions, and without blind adoration in "pink hues." What happened - look under the cut.
The latest scandals revealed that in the “post-Snow” era in the United States, a legal way of influencing any IT vendor in US jurisdiction, the so-called secret order, allows to build a backdoor (in terms of the NSA - “implant”).
Before we talk about the relationship between American IT vendors and special services, it is necessary to delve into history a bit to understand the root causes. Someone will be surprised, but in the United States until 1942 ... there was no single secret service in the usual sense. Before the creation of the Office of Strategic Services, the OSS, (the Central Intelligence Agency, the CIA then became the successor to the CIA), no one in the United States was engaged in strategic intelligence, and certain private matters were under the jurisdiction of special departments in the State Department, the army and the navy. And only in 1942, William Donovan created and headed a single intelligence agency for the collection and analysis of strategic information.

Figure 1 - General William Donovan (1883–1959)
')
The principles on which US intelligence was created are interesting. Donovan was a multi-millionaire from Wall Street, and at the head of key OSS divisions — the largest US financial-industrial groups, FIGs (finance, weapons, steel, oil, communications) —the people who received the maximum authority from Donovan with minimal restrictions. One of the main strategic goals, besides the direct victory in the war with Japan and Germany, was to ensure the global expansion of the United States and big business to Europe, Asia and Latin America after it ended. Fundamentally, over these 70 years, nothing has changed, and the US intelligence services are also closely intertwined with the FIG and military-industrial complex enterprises, the military industrial complex, serving their business interests. And all these structures have tremendous support in the White House, on Capitol Hill, at the Pentagon and, very likely, in Langley and Maryland (CIA and the National Security Agency, the NSA, respectively).
And everything in this scheme was familiar and calm, until in the early 90s IT vendors promptly entered the world of financial-industrial groups and MIC enterprises: Microsoft, IBM, Intel, Cisco, and then Apple, Google, Facebook. By 2016, in terms of capitalization, the top five American companies today include Apple (1st place), Google (2nd place), Microsoft (3rd place) and Facebook (5th place).
The world's largest oil company ExxonMobil (oil is the main political factor of the modern world) takes only 4th place with a double margin (!) From Apple. The rest of the US IT giants - Cisco, Oracle, IBM, Intel - are not so seriously lagging behind.
It turns out that on the one hand, these IT neophytes were quickly pressed by the leading “traditional” global industrial companies and military-industrial complex enterprises that determine US policy for the last century, and on the other, they clearly didn’t have to “get out of the snag” ( C), having received political influence and cover in Washington corresponding to their financial strength. The traditional military industrial complex obviously does not take IT vendors seriously, considering them to be nothing more than an intermediary serving their interests, without which it cannot be dispensed with. And the largest IT manufacturers rightly believe that today their financial strength allows them to conduct their policies. There is a likely political and economic conflict between IT neophytes and the traditional military-industrial complex. Or is everything much simpler, and they have long been part of a large common game? About this below.
And now let's look at stories with NSA “implants”, secret orders, courts, etc. in terms of IT vendors. Let us try to reflect on why they are helping the NSA or the CIA, who frankly use them to conduct their big geopolitical game in the interests of FIGs and the MIC enterprises. There are two possible scenarios.
In the first, most likely, they are already part of the financial-industrial groups and simply pretend to publicly portray their disagreement. A number of factors favor this scenario. In particular, Apple, Microsoft, Oracle and others are the two largest investment companies in the world, Vanguard and BlackRock, with total assets of about $ 8 trillion (which is close to the total assets of all other global investment funds). These two companies are also the main shareholders of many leading companies in the US military-industrial complex, in particular, Lockheed Martin. This fact does not directly indicate direct control, but speaks volumes. There are also a lot of less significant facts, in particular, for example, the identity of Google Shareholder Eric Schmidt. He recently left his post, returning to work at the US Department of Defense, although this can be regarded as a likely indicator of the beginning of the struggle of top IT neophytes with special services.
The second scenario is a conflict over the redistribution of spheres of influence with FIGs or the struggle of different FIGs that include different IT vendors. In his favor, and testify to the history of Yahoo and Juniper (which is lower). All this is more like a “back cover” with the expression of its disagreement with the state policy in the person of its special services.
So, suppose that vendors are not included in these financial-industrial groups (or the financial clan to which the vendor belongs, in certain cases are not interested in executing this secret order, which is imposed by another financial-industrial group), which means that vendors do not unite the common interests in participation in interstate intelligence activities. IT vendors themselves, as opposed to classic FIGs, do not need to “pry, eavesdrop”. It makes no sense. They are absolute leaders. This whole story of "implants" and global surveillance seriously spoils the business of IT vendors, thereby only enhancing their possible existing conflict with FIGs and the special services defending their interests.
Such “behind-the-scenes fuss” always took place in American big politics, but now, looking at the whole situation with bookmarks from a new angle, we can see confirmation of the conflict in the form of surges: various public statements in the press from Apple, Microsoft, Google, Cisco.
Of course, it would be naive to believe that vendors uphold the interests of a democratic society. They are, in fact, concerned about only one thing - the annual growth of the capitalization of companies and the increase in profits. And they are not interested in the problems of FIGs, special services and the state, if they were not linked in the first scenario. Therefore, in the case of the second scenario, it is obvious that the shareholders and the management of the vendors will by all means fight the practice of secret prescriptions, which we probably see now in the example of recent scandals in the press. Or, everything is worse, and we just observe the echoes of the struggle of various FIGs.
An excellent demonstration of outright cynicism, hidden games and attempts to portray a good face in a bad game in modern IT business is the story of Apple revealed the other day. In December 2015, their vice-president wrote a private, sloppy letter to the chief of the election campaign Clinton, assuring in full company loyalty and satisfying "thousands of requests per month" for disclosing information to the American special services.
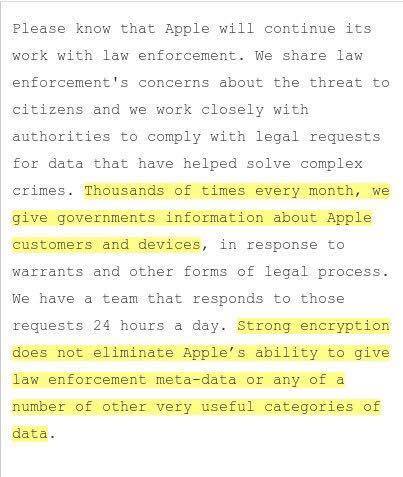
Figure 2 - Fragment of a Letter from Apple's Vice President
And just two months later, Apple is arranging in the press a simulated open scandal under the auspices: “We don’t give anything to the FBI: democracy is in danger!” The question arises if they do this with the industry’s whale like Apple, what about smaller fish.
America is a colossal country with great traditions. Do not underestimate the principles of freedom and democracy that guide many Americans. On the people who sincerely believe in all this, keeps the US IT industry. Let us recall the famous video with the sincere enthusiastic shouts of Steve Ballmer at the annual meeting of Microsoft with its employees: "Developers, developers, developers !!!" And they have their own principles. Most of them sincerely believe in freedom and democracy, and it is not interesting for them to deliberately embed backdoors into their products, even after receiving a secret order, the disclosure of which is equal to the disclosure of state secrets with all the ensuing consequences. And even if the shareholders and bosses of the IT giants have long been "linked" with FIGs and special services, this does not mean that the developers will support them. At a minimum, until Russia and China, by means of many years of propaganda, once again make the "Evil Empire" frighten. Therefore, the developers - the second and perhaps today the main level of resistance. No wonder the RSA received a premium of $ 10 million from the NSA, but more on that below.
Last time, the world is extremes. It is clear that there is no uniquely black or 100% white, there is a mass of shades and semitones. This also applies to the relationship between IT vendors and the state. Today it is a big business, and it has its own laws. There are plenty of legal opportunities to influence any company and it is obvious that they will use these methods in a market economy.
The specificity of corporate law in the United States is such that to influence it is not necessary to own the entire company, it is enough to control it. Given the 8+ trillion assets for two at Vanguard and Black Rock, multiple cross-ownership, as well as the presence of shares in almost all large corporations whose shares rotate on the stock exchange, it is easy to see that, being the largest shareholders of IT vendors and enterprises of the military-industrial complex, allows them to centrally pursue any policy of their own, correcting it and taking into account the interests of both the FIG and the US as a whole. At the same time, it is obvious that behind such gigantic capital are not IT neophytes, but the same representatives of various global FIGs who 100 years ago defined US policy - their capital over the 100 years has not gone down, but only multiplied and multiplied .
By the way, a couple of years ago in Florence, they conducted an interesting study comparing the list of 1000 richest families in the city 500 years ago and now - the correlation turned out to be close to 100%: the vast majority of families that were rich then are also rich now. Therefore, one should not think that the Rockefeller clan with their billions of the beginning of the 20th century had suddenly disappeared somewhere and now their place has been taken by modern IT neophytes owning "miserable" tens of billions of dollars. The real "puppeteers" who control trillions of dollars and influence world politics, now seem to prefer to stay far behind the scenes, not flickering in Forbes lists.
Understanding this, you can look at many of today's processes in a large IT business with different eyes. There is a big game, the echoes of which we sometimes see in the American press, including a serious struggle between various FIGs, and IT vendors, as public companies, probably have not had the opportunity to play their part on their own for a long time. From the tentacles of control of the control now can not escape.
Moreover, the very idea of the universal sale of the stock exchange itself, previously sold, with capital, and it’s more than enough for the global backstage business, makes it possible to gradually and completely get control of all public companies and technologies of interest without any blood. Understanding this, now it is also possible to look at the process in some cases, with seemingly meaningless absorption by large public companies of small and medium, but non-public ones, with somewhat different eyes. And most importantly, many previously incomprehensible stories are becoming quite commonplace and simple.
For example, the story of RSA, which Snowden talked about when the company specifically built the NSA's cryptobacdor for $ 10 million. Clearly, for RSA, as a company that was then sold for $ 2.1 billion, this is clearly not the same amount which she would risk her reputation. Most likely, it was a bonus to top managers and developers who were able to ensure the implementation of this order. And the company RSA was simply forced to "take the peak" and execute the order.
The unanswered question is how many more such secret orders have been given and will still be received by various US vendors from the US government. Today we see only a very small tip of this giant IT iceberg.
We briefly recall that in October 2016, a huge scandal broke out in the American press due to a leak, which, according to information from competent sources, revealed:
It is interesting to look at the story from Yahoo from a new angle. So, Yahoo management receives a secret order to embed the "implant", which they implement in a narrow group of specialists. However, judging by the available fragmentary information from the press, information about this began to gradually spread inside Yahoo. As a result, CISO left the company, apparently not agreeing to participate in this game and then switching to Facebook. According to informed sources, during the next check, Yahoo’s IB security service discovered an “implant”. After some time there was a leak in the press and a huge scandal broke out.
From experience, it is unlikely that Yahoo's security teams discovered this “implant” without additional hindrances — most likely they were helped by the developers (or top managers, although in this case it is doubtful).
The most mysterious story at the junction of the information security / IT world happened less than a year ago - at the end of December 2015 - with Cisco's main competitor, Juniper. She did not cause much noise. Firstly, the vendor is not so popular, and secondly, it was on Christmas Eve. In fact, it was a mysterious story that was inexplicable at that time, which may have been solved by the recent events from the moment of the publication of the NSA cyber weapon archive to the story of Yahoo.
How was the deal. On December 21, 2015, Juniper announced the discovery of two tabs on its VPN device, which gave the attacker the following great opportunities:
In other words, it was about the complete compromise of the VPN of almost all versions of Juniper devices. At the same time, representatives of the company said ... they do not know where in their code the two bookmarks appeared. The FBI then announced the investigation, but the whole story then very suspiciously quickly stalled in the American press - no one remembers it even now, although in vain.
Then it was impossible to understand, firstly, why the company itself unveiled a scandalous fact, and, secondly, how the experts simultaneously discovered two such completely different bookmarks. Nobody prevented Juniper from quietly releasing a patch, adding them to other vulnerabilities or updates, which would then gradually be distributed to customers. The probability that someone from the researchers would take up the reverse of the patch, finding these tabs, is extremely small, although it should not be ruled out. Juniper also did not interfere with the traditionally name the found bookmarks as vulnerabilities, without attracting attention to them, instead of publicly acknowledging the detection of foreign bookmarks to the code.
The second vulnerability associated with the ability to remotely open VPN sessions turned out to be particularly important. Cryptographers realized only a few months (!) After the disclosure that it was a virtuoso weakening in the implementation of the cryptoalgorithm. Whose handwriting is it? Obviously, special services. Who has the highest level of skill in cryptanalysis: experts from the United States, the Russian Federation, probably China, Great Britain, France, and possibly Israel. The last three can be safely deleted. China and Russia are extremely unlikely: it is difficult to deploy their agents inside Juniper, and they would be much more interesting to hack Cisco. The circle of suspects is narrowed, and the most likely of them are NSA employees . Moreover, they have already done this before for $ 10 million with RSA.
After the discovery of the NSA cyber weapons archive, another fact surfaced that indirectly points to the NSA in this story. As it turned out, for many years the agency had the ability to remotely open VPN sessions through a vulnerability (vulnerability or bookmark?) ... Cisco. To provide decent coverage, they lacked ... the availability of a similar feature in the products of Cisco's main world competitor, Juniper.
Let's remember what the press said about this story by Juniper itself. Allegedly, in the process of auditing and analyzing their security code, they found these vulnerabilities. Remembering the story of Yahoo - a one-on-one legend. It is especially interesting how they so suddenly accidentally discovered such a complex vulnerability in a VPN, and the default password was simply impossible to detect - it was necessary to know exactly what and where to look.
Probably, representatives of Juniper had previously either received a secret order from the NSA to embed these bookmarks into their equipment, or at one time the NSA was able to conduct a successful special operation. Then the developers who knew about this story made a leak inside the company, and the bug in this case was pointedly publicized, which, by the way, suggests that Juniper is probably not incorporated into any of the FIG groups, or this is evidence of the clan struggle. Or is this a very subtle game unavailable?
From open information, it is rather difficult to reliably assess exactly what is happening in the relationship between American IT vendors and special services. It is clear that there is a powerful undercover game, the echoes of which we regularly see in the press. It is also clear that such monsters as Apple, Microsoft and Google, if they are no longer inside traditional FIGs (although judging by the main owners of the first two in the person of Vanguard and BlackRock are very similar to this) have huge financial opportunities to influence the situation and, judging by all are looking for political cover on Capitol Hill to counterbalance the actions of the special services. And even if they do it only to divert their eyes or these are the consequences of the struggle of various financial clans, recent stories have clearly shown that we should not discard American developers - they are fully able to influence this situation without letting the NSA live in peace. So it turns out that the developers today ... the last real bastion of freedom and democracy in the modern IT world.
And the modern corporate IT world has finally turned into a traditional big business with its own harsh laws, and it is not the one we are used to quite recently. The shades of the black-and-gray scale came to the place of the naive pink tones, and today you need to be extremely optimistic color-blind to not see all this. The pieces of the IT puzzle scattered across the table have gradually taken shape today into one big and extremely unattractive picture. To our universal and greatest regret.
The latest scandals revealed that in the “post-Snow” era in the United States, a legal way of influencing any IT vendor in US jurisdiction, the so-called secret order, allows to build a backdoor (in terms of the NSA - “implant”).
Historical roots
Before we talk about the relationship between American IT vendors and special services, it is necessary to delve into history a bit to understand the root causes. Someone will be surprised, but in the United States until 1942 ... there was no single secret service in the usual sense. Before the creation of the Office of Strategic Services, the OSS, (the Central Intelligence Agency, the CIA then became the successor to the CIA), no one in the United States was engaged in strategic intelligence, and certain private matters were under the jurisdiction of special departments in the State Department, the army and the navy. And only in 1942, William Donovan created and headed a single intelligence agency for the collection and analysis of strategic information.

Figure 1 - General William Donovan (1883–1959)
')
The principles on which US intelligence was created are interesting. Donovan was a multi-millionaire from Wall Street, and at the head of key OSS divisions — the largest US financial-industrial groups, FIGs (finance, weapons, steel, oil, communications) —the people who received the maximum authority from Donovan with minimal restrictions. One of the main strategic goals, besides the direct victory in the war with Japan and Germany, was to ensure the global expansion of the United States and big business to Europe, Asia and Latin America after it ended. Fundamentally, over these 70 years, nothing has changed, and the US intelligence services are also closely intertwined with the FIG and military-industrial complex enterprises, the military industrial complex, serving their business interests. And all these structures have tremendous support in the White House, on Capitol Hill, at the Pentagon and, very likely, in Langley and Maryland (CIA and the National Security Agency, the NSA, respectively).
IT neophytes
And everything in this scheme was familiar and calm, until in the early 90s IT vendors promptly entered the world of financial-industrial groups and MIC enterprises: Microsoft, IBM, Intel, Cisco, and then Apple, Google, Facebook. By 2016, in terms of capitalization, the top five American companies today include Apple (1st place), Google (2nd place), Microsoft (3rd place) and Facebook (5th place).
The world's largest oil company ExxonMobil (oil is the main political factor of the modern world) takes only 4th place with a double margin (!) From Apple. The rest of the US IT giants - Cisco, Oracle, IBM, Intel - are not so seriously lagging behind.
It turns out that on the one hand, these IT neophytes were quickly pressed by the leading “traditional” global industrial companies and military-industrial complex enterprises that determine US policy for the last century, and on the other, they clearly didn’t have to “get out of the snag” ( C), having received political influence and cover in Washington corresponding to their financial strength. The traditional military industrial complex obviously does not take IT vendors seriously, considering them to be nothing more than an intermediary serving their interests, without which it cannot be dispensed with. And the largest IT manufacturers rightly believe that today their financial strength allows them to conduct their policies. There is a likely political and economic conflict between IT neophytes and the traditional military-industrial complex. Or is everything much simpler, and they have long been part of a large common game? About this below.
Shareholders - the first level of resistance
And now let's look at stories with NSA “implants”, secret orders, courts, etc. in terms of IT vendors. Let us try to reflect on why they are helping the NSA or the CIA, who frankly use them to conduct their big geopolitical game in the interests of FIGs and the MIC enterprises. There are two possible scenarios.
In the first, most likely, they are already part of the financial-industrial groups and simply pretend to publicly portray their disagreement. A number of factors favor this scenario. In particular, Apple, Microsoft, Oracle and others are the two largest investment companies in the world, Vanguard and BlackRock, with total assets of about $ 8 trillion (which is close to the total assets of all other global investment funds). These two companies are also the main shareholders of many leading companies in the US military-industrial complex, in particular, Lockheed Martin. This fact does not directly indicate direct control, but speaks volumes. There are also a lot of less significant facts, in particular, for example, the identity of Google Shareholder Eric Schmidt. He recently left his post, returning to work at the US Department of Defense, although this can be regarded as a likely indicator of the beginning of the struggle of top IT neophytes with special services.
The second scenario is a conflict over the redistribution of spheres of influence with FIGs or the struggle of different FIGs that include different IT vendors. In his favor, and testify to the history of Yahoo and Juniper (which is lower). All this is more like a “back cover” with the expression of its disagreement with the state policy in the person of its special services.
So, suppose that vendors are not included in these financial-industrial groups (or the financial clan to which the vendor belongs, in certain cases are not interested in executing this secret order, which is imposed by another financial-industrial group), which means that vendors do not unite the common interests in participation in interstate intelligence activities. IT vendors themselves, as opposed to classic FIGs, do not need to “pry, eavesdrop”. It makes no sense. They are absolute leaders. This whole story of "implants" and global surveillance seriously spoils the business of IT vendors, thereby only enhancing their possible existing conflict with FIGs and the special services defending their interests.
Such “behind-the-scenes fuss” always took place in American big politics, but now, looking at the whole situation with bookmarks from a new angle, we can see confirmation of the conflict in the form of surges: various public statements in the press from Apple, Microsoft, Google, Cisco.
Of course, it would be naive to believe that vendors uphold the interests of a democratic society. They are, in fact, concerned about only one thing - the annual growth of the capitalization of companies and the increase in profits. And they are not interested in the problems of FIGs, special services and the state, if they were not linked in the first scenario. Therefore, in the case of the second scenario, it is obvious that the shareholders and the management of the vendors will by all means fight the practice of secret prescriptions, which we probably see now in the example of recent scandals in the press. Or, everything is worse, and we just observe the echoes of the struggle of various FIGs.
An excellent demonstration of outright cynicism, hidden games and attempts to portray a good face in a bad game in modern IT business is the story of Apple revealed the other day. In December 2015, their vice-president wrote a private, sloppy letter to the chief of the election campaign Clinton, assuring in full company loyalty and satisfying "thousands of requests per month" for disclosing information to the American special services.

Figure 2 - Fragment of a Letter from Apple's Vice President
And just two months later, Apple is arranging in the press a simulated open scandal under the auspices: “We don’t give anything to the FBI: democracy is in danger!” The question arises if they do this with the industry’s whale like Apple, what about smaller fish.
Developers - the second level of resistance
America is a colossal country with great traditions. Do not underestimate the principles of freedom and democracy that guide many Americans. On the people who sincerely believe in all this, keeps the US IT industry. Let us recall the famous video with the sincere enthusiastic shouts of Steve Ballmer at the annual meeting of Microsoft with its employees: "Developers, developers, developers !!!" And they have their own principles. Most of them sincerely believe in freedom and democracy, and it is not interesting for them to deliberately embed backdoors into their products, even after receiving a secret order, the disclosure of which is equal to the disclosure of state secrets with all the ensuing consequences. And even if the shareholders and bosses of the IT giants have long been "linked" with FIGs and special services, this does not mean that the developers will support them. At a minimum, until Russia and China, by means of many years of propaganda, once again make the "Evil Empire" frighten. Therefore, the developers - the second and perhaps today the main level of resistance. No wonder the RSA received a premium of $ 10 million from the NSA, but more on that below.
FIG vs vendors, or nothing personal - only business
Last time, the world is extremes. It is clear that there is no uniquely black or 100% white, there is a mass of shades and semitones. This also applies to the relationship between IT vendors and the state. Today it is a big business, and it has its own laws. There are plenty of legal opportunities to influence any company and it is obvious that they will use these methods in a market economy.
The specificity of corporate law in the United States is such that to influence it is not necessary to own the entire company, it is enough to control it. Given the 8+ trillion assets for two at Vanguard and Black Rock, multiple cross-ownership, as well as the presence of shares in almost all large corporations whose shares rotate on the stock exchange, it is easy to see that, being the largest shareholders of IT vendors and enterprises of the military-industrial complex, allows them to centrally pursue any policy of their own, correcting it and taking into account the interests of both the FIG and the US as a whole. At the same time, it is obvious that behind such gigantic capital are not IT neophytes, but the same representatives of various global FIGs who 100 years ago defined US policy - their capital over the 100 years has not gone down, but only multiplied and multiplied .
By the way, a couple of years ago in Florence, they conducted an interesting study comparing the list of 1000 richest families in the city 500 years ago and now - the correlation turned out to be close to 100%: the vast majority of families that were rich then are also rich now. Therefore, one should not think that the Rockefeller clan with their billions of the beginning of the 20th century had suddenly disappeared somewhere and now their place has been taken by modern IT neophytes owning "miserable" tens of billions of dollars. The real "puppeteers" who control trillions of dollars and influence world politics, now seem to prefer to stay far behind the scenes, not flickering in Forbes lists.
Understanding this, you can look at many of today's processes in a large IT business with different eyes. There is a big game, the echoes of which we sometimes see in the American press, including a serious struggle between various FIGs, and IT vendors, as public companies, probably have not had the opportunity to play their part on their own for a long time. From the tentacles of control of the control now can not escape.
Moreover, the very idea of the universal sale of the stock exchange itself, previously sold, with capital, and it’s more than enough for the global backstage business, makes it possible to gradually and completely get control of all public companies and technologies of interest without any blood. Understanding this, now it is also possible to look at the process in some cases, with seemingly meaningless absorption by large public companies of small and medium, but non-public ones, with somewhat different eyes. And most importantly, many previously incomprehensible stories are becoming quite commonplace and simple.
For example, the story of RSA, which Snowden talked about when the company specifically built the NSA's cryptobacdor for $ 10 million. Clearly, for RSA, as a company that was then sold for $ 2.1 billion, this is clearly not the same amount which she would risk her reputation. Most likely, it was a bonus to top managers and developers who were able to ensure the implementation of this order. And the company RSA was simply forced to "take the peak" and execute the order.
The unanswered question is how many more such secret orders have been given and will still be received by various US vendors from the US government. Today we see only a very small tip of this giant IT iceberg.
Data. History 1. Yahoo
We briefly recall that in October 2016, a huge scandal broke out in the American press due to a leak, which, according to information from competent sources, revealed:
- Mass analysis of all 500 million users of the mail service through the installation of the NSA’s “implant” vendor itself for secretly collecting information;
- a system of secret regulations, according to which the state can oblige any vendor to fulfill a secret order for embedding the "implant".
It is interesting to look at the story from Yahoo from a new angle. So, Yahoo management receives a secret order to embed the "implant", which they implement in a narrow group of specialists. However, judging by the available fragmentary information from the press, information about this began to gradually spread inside Yahoo. As a result, CISO left the company, apparently not agreeing to participate in this game and then switching to Facebook. According to informed sources, during the next check, Yahoo’s IB security service discovered an “implant”. After some time there was a leak in the press and a huge scandal broke out.
From experience, it is unlikely that Yahoo's security teams discovered this “implant” without additional hindrances — most likely they were helped by the developers (or top managers, although in this case it is doubtful).
Data. Story 2. Juniper
The most mysterious story at the junction of the information security / IT world happened less than a year ago - at the end of December 2015 - with Cisco's main competitor, Juniper. She did not cause much noise. Firstly, the vendor is not so popular, and secondly, it was on Christmas Eve. In fact, it was a mysterious story that was inexplicable at that time, which may have been solved by the recent events from the moment of the publication of the NSA cyber weapon archive to the story of Yahoo.
How was the deal. On December 21, 2015, Juniper announced the discovery of two tabs on its VPN device, which gave the attacker the following great opportunities:
- remote access to the device through the default password (it was very cleverly camouflaged in the code);
- remote decryption of the VPN connection by weakening the implementation of the cryptoalgorithm.
In other words, it was about the complete compromise of the VPN of almost all versions of Juniper devices. At the same time, representatives of the company said ... they do not know where in their code the two bookmarks appeared. The FBI then announced the investigation, but the whole story then very suspiciously quickly stalled in the American press - no one remembers it even now, although in vain.
Then it was impossible to understand, firstly, why the company itself unveiled a scandalous fact, and, secondly, how the experts simultaneously discovered two such completely different bookmarks. Nobody prevented Juniper from quietly releasing a patch, adding them to other vulnerabilities or updates, which would then gradually be distributed to customers. The probability that someone from the researchers would take up the reverse of the patch, finding these tabs, is extremely small, although it should not be ruled out. Juniper also did not interfere with the traditionally name the found bookmarks as vulnerabilities, without attracting attention to them, instead of publicly acknowledging the detection of foreign bookmarks to the code.
The second vulnerability associated with the ability to remotely open VPN sessions turned out to be particularly important. Cryptographers realized only a few months (!) After the disclosure that it was a virtuoso weakening in the implementation of the cryptoalgorithm. Whose handwriting is it? Obviously, special services. Who has the highest level of skill in cryptanalysis: experts from the United States, the Russian Federation, probably China, Great Britain, France, and possibly Israel. The last three can be safely deleted. China and Russia are extremely unlikely: it is difficult to deploy their agents inside Juniper, and they would be much more interesting to hack Cisco. The circle of suspects is narrowed, and the most likely of them are NSA employees . Moreover, they have already done this before for $ 10 million with RSA.
After the discovery of the NSA cyber weapons archive, another fact surfaced that indirectly points to the NSA in this story. As it turned out, for many years the agency had the ability to remotely open VPN sessions through a vulnerability (vulnerability or bookmark?) ... Cisco. To provide decent coverage, they lacked ... the availability of a similar feature in the products of Cisco's main world competitor, Juniper.
Let's remember what the press said about this story by Juniper itself. Allegedly, in the process of auditing and analyzing their security code, they found these vulnerabilities. Remembering the story of Yahoo - a one-on-one legend. It is especially interesting how they so suddenly accidentally discovered such a complex vulnerability in a VPN, and the default password was simply impossible to detect - it was necessary to know exactly what and where to look.
Probably, representatives of Juniper had previously either received a secret order from the NSA to embed these bookmarks into their equipment, or at one time the NSA was able to conduct a successful special operation. Then the developers who knew about this story made a leak inside the company, and the bug in this case was pointedly publicized, which, by the way, suggests that Juniper is probably not incorporated into any of the FIG groups, or this is evidence of the clan struggle. Or is this a very subtle game unavailable?
Instead of conclusion
From open information, it is rather difficult to reliably assess exactly what is happening in the relationship between American IT vendors and special services. It is clear that there is a powerful undercover game, the echoes of which we regularly see in the press. It is also clear that such monsters as Apple, Microsoft and Google, if they are no longer inside traditional FIGs (although judging by the main owners of the first two in the person of Vanguard and BlackRock are very similar to this) have huge financial opportunities to influence the situation and, judging by all are looking for political cover on Capitol Hill to counterbalance the actions of the special services. And even if they do it only to divert their eyes or these are the consequences of the struggle of various financial clans, recent stories have clearly shown that we should not discard American developers - they are fully able to influence this situation without letting the NSA live in peace. So it turns out that the developers today ... the last real bastion of freedom and democracy in the modern IT world.
And the modern corporate IT world has finally turned into a traditional big business with its own harsh laws, and it is not the one we are used to quite recently. The shades of the black-and-gray scale came to the place of the naive pink tones, and today you need to be extremely optimistic color-blind to not see all this. The pieces of the IT puzzle scattered across the table have gradually taken shape today into one big and extremely unattractive picture. To our universal and greatest regret.
Source: https://habr.com/ru/post/313728/
All Articles