Cyber-grouping Sednit activities under a microscope - Part 2
Our experts have published the second part of a detailed study of the activities and cybercrime malware Sednit. In the previous part, we published information about phishing messages and user compromise mechanisms from this group, and also mentioned the exploits they use. In the new part of our research we will focus on the malware that Sednit uses to compromise users.

The grouping specializes in compromising only those targets that were previously chosen for a cyber attack, i.e. the cyber attack is directional and is carried out after reconnaissance of these targets. The authors' malicious tool (toolkit) consists of three main components: the backdoors SEDRECO, XAGENT and the network agent XTUNNEL.
The attackers use both backdoors to compromise their victims, which allows one of them to remain active even if the other is detected by an antivirus product. Thus, it gives them additional confidence that control over the victim’s system will not be lost.
The SEDRECO backdoor allows Sednit operators to perform various operations on a compromised system, including reading and writing files, tracking keystrokes on the keyboard, searching for files in the system and on network resources. ESET specialists also found that SEDRECO can use special plugins for its own purposes, which are passed to it by the C & C server manager.
')
The SEDRECO backdoor uses the program code that we observed in another Sednit backdoor called XAGENT. XAGENT helps operators extract information of interest from the infected system via HTTP or e-mail. It can also interact with another component called USBSTEALER, which specializes in data theft from isolated air-gapped computers. Our specialists managed to get the source code of the XAGENT component that runs on Linux.
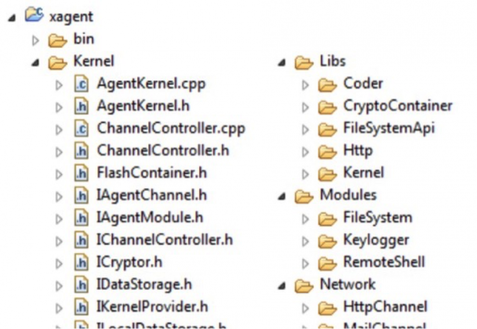
As is known, various modifications of XAGENT are actively used by cyber-grouping from November 2012 to the present. The victims of this backdoor include the computers of the governing body of the US Democratic Party Democratic National Committee (DNC).
Although our specialists have observed the XAGENT version of the backdoor for platforms such as Windows, Linux and iOS, most likely there is a version of this malware for Android.
Well-designed by the authors, the XAGENT malware consists of several modules providing various functionalities. This factor, as well as the properties examined by ESET malware samples, show that the attackers adapted each cyber attack to a specific target. This helps attackers to minimize the risk of exposing all XAGENT code to antivirus analysts.
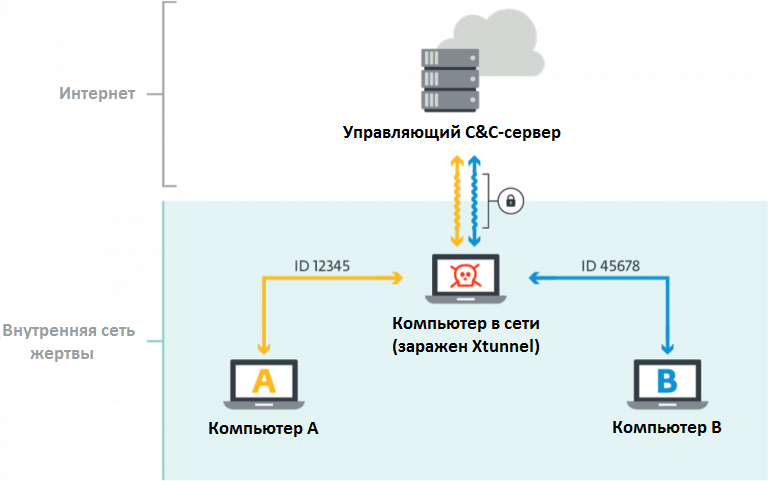
The other component mentioned above, called XTUNNEL, is a network proxy tool that operators use to redirect network traffic from the victim’s network to their servers.
The first known copy of XAGENT dates from May 2013, its later copies were found on the servers of the Democratic Party Committee DNC in May 2016 and the German parliament in June 2015, and the authors continue to develop malicious code. Our experts confirmed that significant resources were invested in the development of XTUNNEL, SEDRECO and XAGENT.
Sednit relies on Xagent and Sedreco for its cyber espionage activities. Both of these malicious programs have been developing intensively over the past years. Similar efforts have been invested in the development of Xtunnel. These three malicious tools are key to understanding Sednit activities.
However, it would not be entirely correct to imagine that the group uses only these tools in its cyber attacks. For example, they can also use password collection tools on compromised computers, some of which are created by the authors for a specific attack. The same goes for tools for capturing desktop screenshots.
The full version of the second part of our research can be read here .

The grouping specializes in compromising only those targets that were previously chosen for a cyber attack, i.e. the cyber attack is directional and is carried out after reconnaissance of these targets. The authors' malicious tool (toolkit) consists of three main components: the backdoors SEDRECO, XAGENT and the network agent XTUNNEL.
The attackers use both backdoors to compromise their victims, which allows one of them to remain active even if the other is detected by an antivirus product. Thus, it gives them additional confidence that control over the victim’s system will not be lost.
The SEDRECO backdoor allows Sednit operators to perform various operations on a compromised system, including reading and writing files, tracking keystrokes on the keyboard, searching for files in the system and on network resources. ESET specialists also found that SEDRECO can use special plugins for its own purposes, which are passed to it by the C & C server manager.
')
The SEDRECO backdoor uses the program code that we observed in another Sednit backdoor called XAGENT. XAGENT helps operators extract information of interest from the infected system via HTTP or e-mail. It can also interact with another component called USBSTEALER, which specializes in data theft from isolated air-gapped computers. Our specialists managed to get the source code of the XAGENT component that runs on Linux.

As is known, various modifications of XAGENT are actively used by cyber-grouping from November 2012 to the present. The victims of this backdoor include the computers of the governing body of the US Democratic Party Democratic National Committee (DNC).
Although our specialists have observed the XAGENT version of the backdoor for platforms such as Windows, Linux and iOS, most likely there is a version of this malware for Android.
Well-designed by the authors, the XAGENT malware consists of several modules providing various functionalities. This factor, as well as the properties examined by ESET malware samples, show that the attackers adapted each cyber attack to a specific target. This helps attackers to minimize the risk of exposing all XAGENT code to antivirus analysts.
The other component mentioned above, called XTUNNEL, is a network proxy tool that operators use to redirect network traffic from the victim’s network to their servers.

The first known copy of XAGENT dates from May 2013, its later copies were found on the servers of the Democratic Party Committee DNC in May 2016 and the German parliament in June 2015, and the authors continue to develop malicious code. Our experts confirmed that significant resources were invested in the development of XTUNNEL, SEDRECO and XAGENT.
Sednit relies on Xagent and Sedreco for its cyber espionage activities. Both of these malicious programs have been developing intensively over the past years. Similar efforts have been invested in the development of Xtunnel. These three malicious tools are key to understanding Sednit activities.
However, it would not be entirely correct to imagine that the group uses only these tools in its cyber attacks. For example, they can also use password collection tools on compromised computers, some of which are created by the authors for a specific attack. The same goes for tools for capturing desktop screenshots.
The full version of the second part of our research can be read here .
Source: https://habr.com/ru/post/313678/
All Articles