What's New in vSphere 6.5: Security
vSphere 6.5 is a turning point in VMware security infrastructure. What was considered secondary to many
VM encryption
Encrypting virtual machines is something that has been in development for many years. However, this decision has not received proper development, because each decision has negative operational impacts. With vSphere 6.5, this issue is resolved.
Encryption will be performed at the hypervisor level, “under” the virtual machine. Since the virtual disk controller in the VM is acting as I / O, encryption occurs instantaneously using the module in the kernel before it is sent to the kernel storage layer. VM files (vmx file, snapshot
The benefits are many.

')
- Since encryption occurs at the hypervisor level, not at the VM, the type of the guest OS and the type of data storage are not important. Virtual machine encryption - agnostic.
- Encryption is done through policies. Policies can be applied to many VMs, regardless of their guest OS.
- Encryption is not managed "inside" the virtual machine. This is a key differentiation factor in relation to any other solution on the market! You do not have to control the encryption performed in the virtual machine, and the keys are not stored in its memory.
- Key management is based on industry standard, KMIP with 1.1. In vSphere, vcenter is a KMIP client, it works with a large number of KMIP 1.1 key managers. This gives the opportunity to choose and sufficient flexibility for customers. VM keys are not stored in vCenter.
- Encryption of a virtual machine makes it possible to use the latest technical features inherent in today's processors. For encryption, the
AES-Ni algorithm isused . - Encryption vMotion. This question was already long ago, and with version 6.5 it was finally answered. The uniqueness of encryption technology vMotion is that the network is not encrypted. There are no certificates to manage, and there are no network settings to be made.
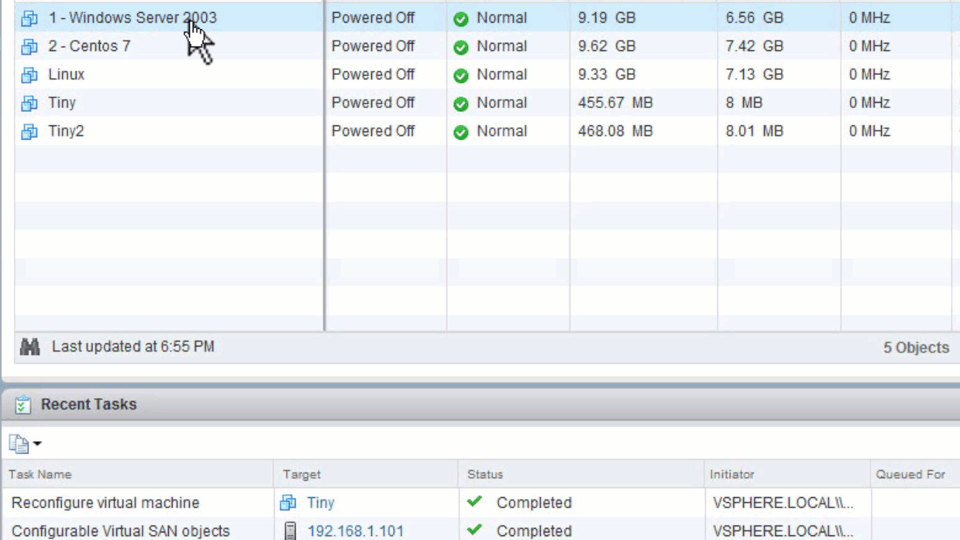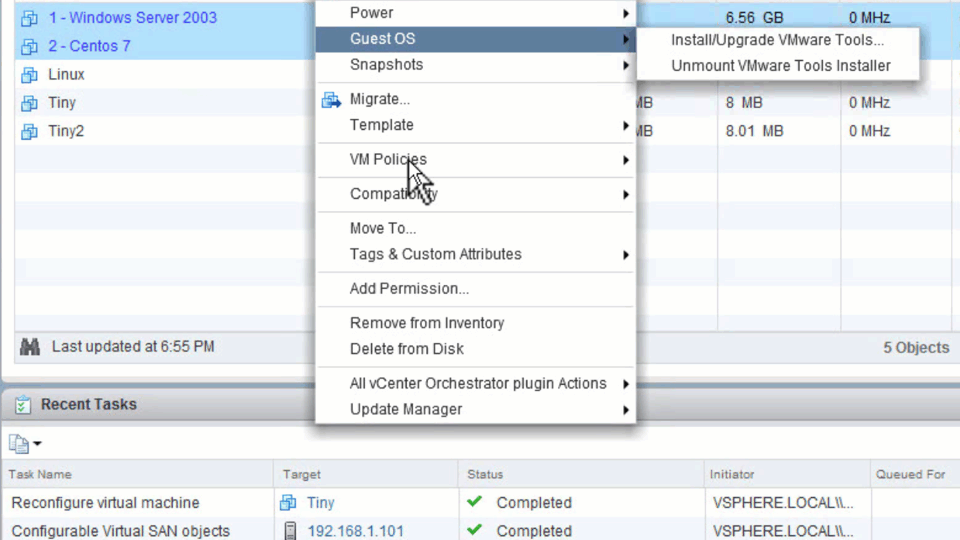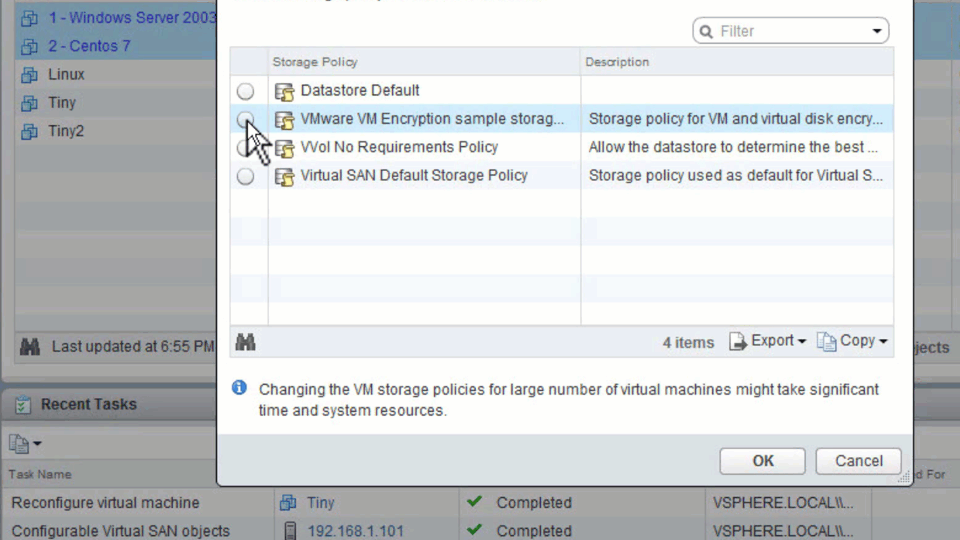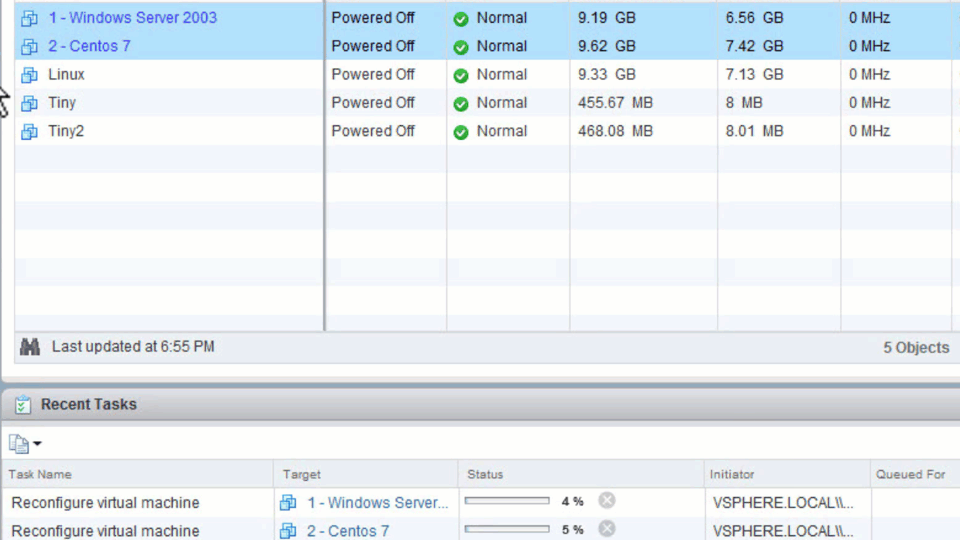
Encryption occurs at the level of each individual virtual machine. VMotion encryption technology gives impetus to everything else. During migration, the VM uses the one-time and randomly generated
In addition, a
Encryption vmotion can be used for unencrypted VMs, and on encrypted VMs it is always used.

Secure Boot support
The vSphere 6.5 release introduces support for Secure Boot for virtual machines and for the ESXi hypervisor.
ESXi Secure Boot
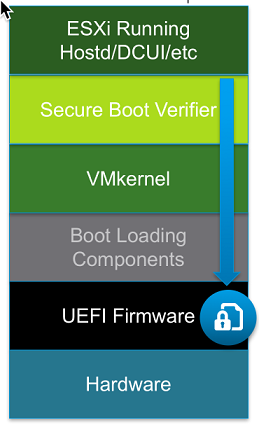 With Secure Boot enabled, the integrated UEFI verifies the ESXi kernel digital signature using a digital certificate in the UEFI firmware. This ensures that only the “correct” kernel will be loaded. For ESXi, Secure Boot goes even further, adding cryptographic support for all ESXi components.
With Secure Boot enabled, the integrated UEFI verifies the ESXi kernel digital signature using a digital certificate in the UEFI firmware. This ensures that only the “correct” kernel will be loaded. For ESXi, Secure Boot goes even further, adding cryptographic support for all ESXi components.Today, ESXi already has a digital signature package - VIB (vSphere Installation Bundle). The ESXi file system refers to the contents of these packages (it is impossible to crack packages). Due to the use of digital certificates in the embedded UEFI, at boot time, the already proven ESXi Kernel will, in turn, check every VIB for an embedded certificate. This provides a cryptographically clean load.
Note: if Secure Boot is enabled, then you will not be able to force unsigned code to install on ESXi. This ensures that, with Secure Boot enabled, ESXi will only work with VMware signed digital code.
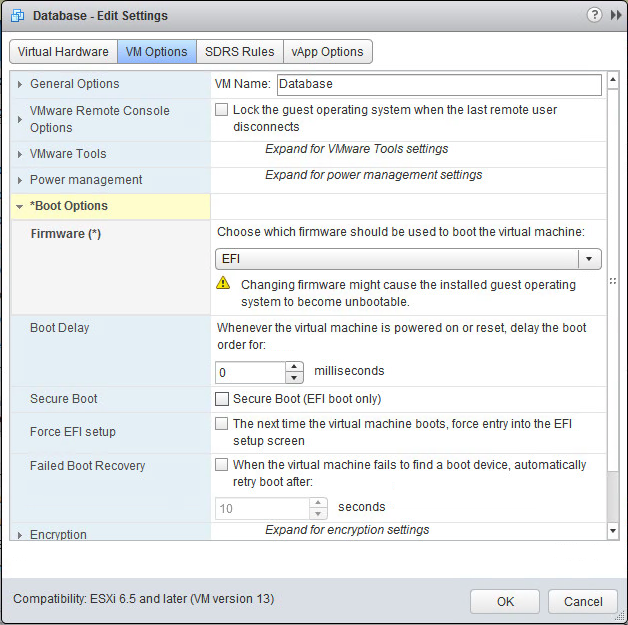
Secure Boot Virtual Machine
With respect to VM, the organization of SecureBoot is very simple. The virtual machine must be configured to use the built-in EFI, and then Secure Boot is enabled by ticking the checkbox. Please note that if secure boot is enabled, you can download only certified drivers to the virtual machine.
Secure Boot for virtual machines works with Windows and Linux.
Extended logs
VSphere logs have traditionally been focused on troubleshooting, not security. The situation changes in vSphere 6.5 with the introduction of extended logs. Gone are the days when you made significant changes to the virtual machine, and in the log you only received a record that the VM was changed.
In the new release, logies are enhanced and made more efficient by sending event data, such as “VM has been migrated”, via the syslog data stream. Events now contain what is actually called data. Instead of notifying that
In 6.5 you get a descriptive report about the action. For example, if 4 GB of memory is added for a virtual machine that currently has 6 GB, the log will tell you how it looked before and how it looks now. In the security context, when you move a virtual machine from vSwitch labeled “PCI” to vSwitch labeled
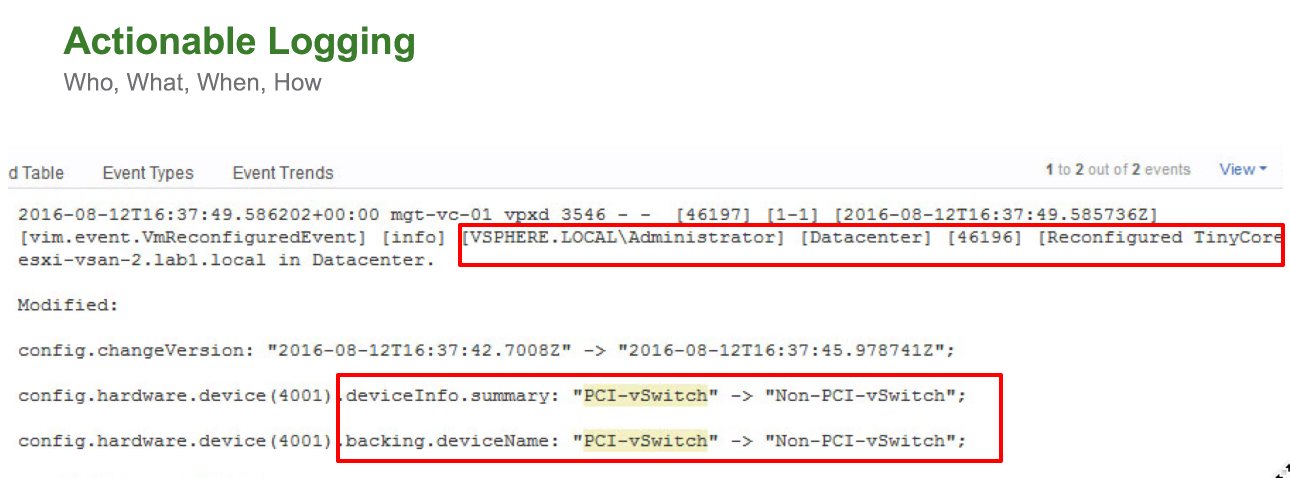
Solutions like VMware Log Insight will now give much more information, but more importantly, a more detailed report means that you can create more prescriptive warnings and corrections. More detailed information helps you make smarter, critical data center decisions.
Automation
All of these features have a certain level of automation, for example, vMotion policy encryption. This is all that we wanted to talk about security in vSphere 6.5. The vSphere Security Guide will be released within a quarter of the release of version 6.5.
Source: https://habr.com/ru/post/313652/
All Articles