Mirai botnet was used for powerful DDoS attacks on Dyn
Last Friday, a substantial part of the global Internet worked intermittently or was completely unavailable for several hours. Users experienced problems with access to services such as Twitter, Amazon, Tumblr, Reddit, Spotify, and Netflix. The question arises as to who implemented such a large-scale DDoS attack, on whom and who stood behind it. One of the first information about the incident was published by well-known security journalist Brian Krebs, pointing out that the reason for such a large-scale failure was the organized DDoS attack on the well-known US company Dyn, which provides network infrastructure and DNS services for key American organizations.

Somewhat later, Flashpoint specialists found out that the DDoS attack was organized using IoT devices that were compromised by intruders. In addition, they were included in the Mirai botnet, the source code of which was recently leaked to the network.
The Mirai botnet was previously used to implement a powerful cyber attack on the Brian Krebs website, which reached an intensity of 620 Gb / s and was implemented from IoT devices.
The main method of compromising devices by malware is to select passwords among the standard list. Thus, if access to the router or digital camera is allowed via SSH and a standard password is set, for example, admin: admin, the device is infected with malware and becomes part of the Mirai botnet.
')
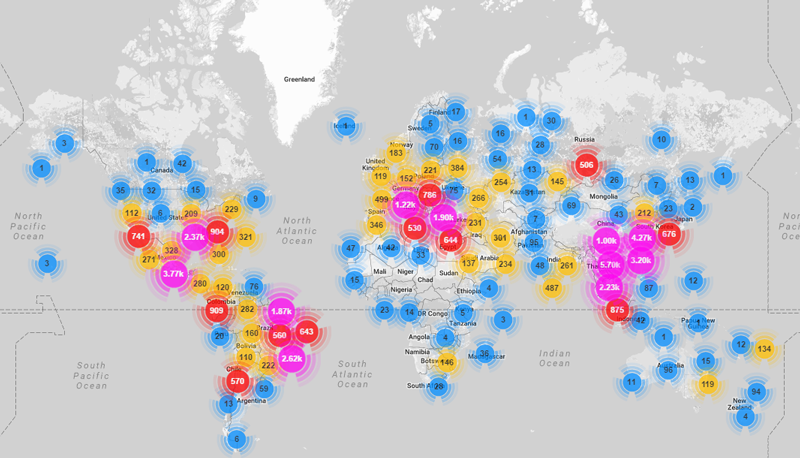
Fig. Map of the location of compromised devices that participated in the DDoS attack ( Incapsula data).

Later, the Chinese manufacturer of IP cameras and DVR XiongMai Technologies confirmed that its devices could have participated in the cyber attack, as they are vulnerable to the methods used by Mirai, i.e., they come with weak passwords. The following weak passwords are included in the Mirai list.
A botnet can organize DDoS based on an HTTP flood, using the following User Agent lines.
Mirai is able to organize DDoS at the network IP protocol level as well as TCP and UDP.
Dyn Statement on 10/21/2016 DDoS Attack
Dyn experts note that tens of millions of different IP addresses were used for cyber attacks on the company's servers.

Somewhat later, Flashpoint specialists found out that the DDoS attack was organized using IoT devices that were compromised by intruders. In addition, they were included in the Mirai botnet, the source code of which was recently leaked to the network.
Flashpoint has been confirmed as malware for the distributed DNS (DDoS) attacks against DNS. Mirai botnets were previously used in the DDoS attacks against security team and were provided by OVH. Mirai malware targets, digital video recordings (DVRs), digital video recordings (DVRs), webcams / security cameras, digital video recordings (HDD)
The Mirai botnet was previously used to implement a powerful cyber attack on the Brian Krebs website, which reached an intensity of 620 Gb / s and was implemented from IoT devices.
The main method of compromising devices by malware is to select passwords among the standard list. Thus, if access to the router or digital camera is allowed via SSH and a standard password is set, for example, admin: admin, the device is infected with malware and becomes part of the Mirai botnet.
')

Fig. Map of the location of compromised devices that participated in the DDoS attack ( Incapsula data).

Later, the Chinese manufacturer of IP cameras and DVR XiongMai Technologies confirmed that its devices could have participated in the cyber attack, as they are vulnerable to the methods used by Mirai, i.e., they come with weak passwords. The following weak passwords are included in the Mirai list.
root xc3511
root vizxv
root admin
admin admin
root 888888
root xmhdipc
root default
root juantech
root 123456
A botnet can organize DDoS based on an HTTP flood, using the following User Agent lines.
Mozilla / 5.0 (Windows NT 10.0; WOW64) AppleWebKit / 537.36 (KHTML, like Gecko) Chrome / 51.0.2704.103 Safari / 537.36
Mozilla / 5.0 (Windows NT 10.0; WOW64) AppleWebKit / 537.36 (KHTML, like Gecko) Chrome / 52.0.2743.116 Safari / 537.36
Mozilla / 5.0 (Windows NT 6.1; WOW64) AppleWebKit / 537.36 (KHTML, like Gecko) Chrome / 51.0.2704.103 Safari / 537.36
Mirai is able to organize DDoS at the network IP protocol level as well as TCP and UDP.
This is a highly distributed attack of millions of IP addresses . We are carrying out a thorough fashion. It was a sophisticated attack across multiple attack vectors and internet locations. Were confirmed by the Mirai botnet . We've seen 10s of millions of discrete IP addresses associated with the Mirai botnet.
Dyn Statement on 10/21/2016 DDoS Attack
Dyn experts note that tens of millions of different IP addresses were used for cyber attacks on the company's servers.
Source: https://habr.com/ru/post/313444/
All Articles