Cybergrouping Sednit activities under the microscope
We have already written several times about the Sednit cyber-grouping activities (APT28, Fancy Bear, Pawn Storm, Sofacy) in previous posts on our corporate blog. This group tried to compromise more than 1000 users in various organizations using phishing attacks, as well as zero-day exploits. Attackers are interested in stealing confidential information from computers of compromised users.

Sednit has been carrying out cyber attacks on users since at least 2004, and sophisticated methods have been used to bypass the network security settings. ESET researchers have tracked Sednit’s activities over the past two years. Sednit was convicted of cyber attacks on the Democratic Party Congress Election Committee, the German parliament , the servers of the French TV channel TV5Monde , and the anti-doping agency WADA .
Grouping uses a fairly common method to steal user account credentials. It consists of sending targeted phishing emails with URL links leading to fake account login pages where you need to enter a username and password.

')
Phishing emails use social engineering techniques to trick users. The user is trying to instill that he needs to follow the specified link as soon as possible, while he can forget about the possible consequences of such a step.
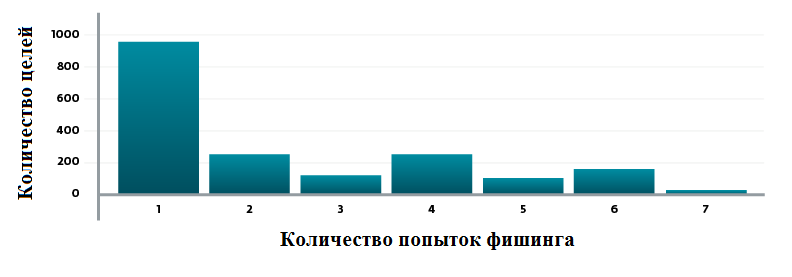
As a result of the analysis, our specialists discovered 1,888 unique e-mail addresses to which phishing messages were sent between March 16 and September 14, 2015. At the same time, it is clear that the greatest number of attacks falls on Monday or Friday.
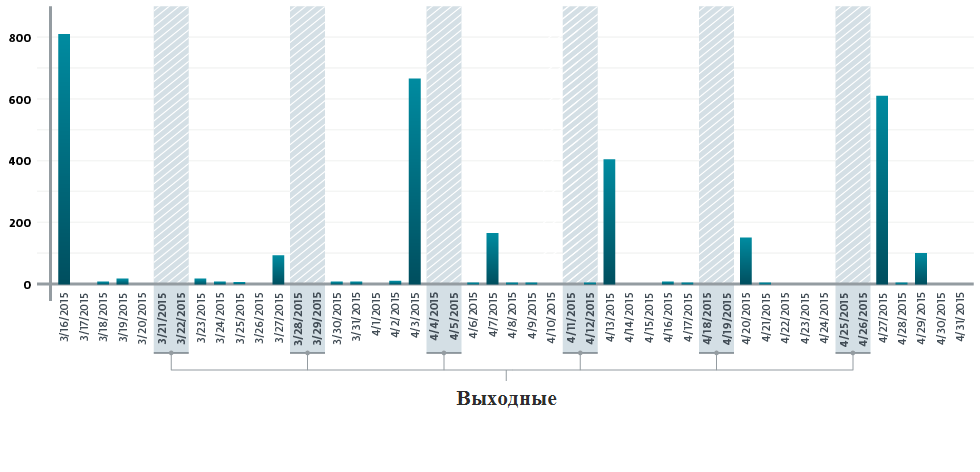
Our experts suggest that regular bursts of activity correspond to the launch time of new phishing campaigns.
Grouping Sednit uses emails to infect users by sending them either a malicious attachment or a malicious link to a set of exploits inside the letter. In the case of attachments, Sednit resorts to exploits for such common products as Microsoft Word, Microsoft Excel, Adobe Flash and Adobe Reader.
In the screenshot below, you can see the phishing message used by the group, allegedly from the All-Ukrainian Economic Union, to which is attached a document with information on the deterioration of relations between Russia and the EU.
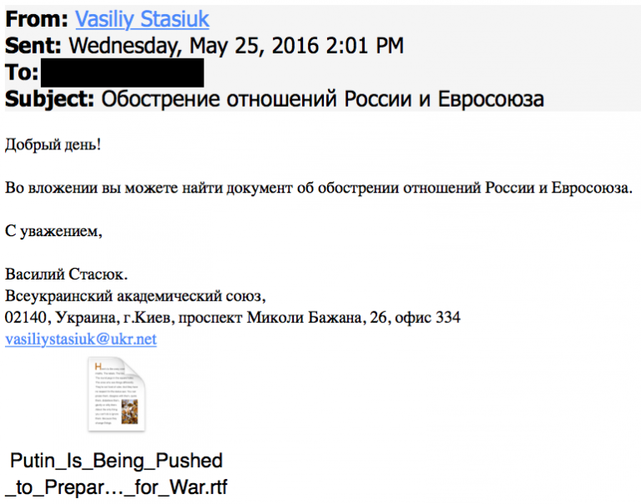
In this particular case, the attached RTF file exploits a vulnerability in Office to drop the victim of another malicious component onto the disk. In the case of other cyber attacks, the group used the themes of current news feeds to lure the user to a malicious resource to download the file. Examples of such news topics are listed below.
Using 0day exploits allows the group to solve two problems, firstly, to increase their chances of successfully compromising the system, and secondly, to install malware in an automatic mode with minimal user intervention.
ESET specialists found that only in 2015 the group used exploited at least six 0day vulnerabilities for Windows, Adobe Flash and Java.

In addition, as will be described in subsequent posts, the group has developed dozens of its malicious programs, including backdoors with various modules, bootkits, and rootkits to successfully complete the tasks.
The full version of the analysis of the activities of the group Sednit can be found at this link .

Sednit has been carrying out cyber attacks on users since at least 2004, and sophisticated methods have been used to bypass the network security settings. ESET researchers have tracked Sednit’s activities over the past two years. Sednit was convicted of cyber attacks on the Democratic Party Congress Election Committee, the German parliament , the servers of the French TV channel TV5Monde , and the anti-doping agency WADA .
Theft of confidential information credentials postal services
Grouping uses a fairly common method to steal user account credentials. It consists of sending targeted phishing emails with URL links leading to fake account login pages where you need to enter a username and password.

')
Phishing emails use social engineering techniques to trick users. The user is trying to instill that he needs to follow the specified link as soon as possible, while he can forget about the possible consequences of such a step.

As a result of the analysis, our specialists discovered 1,888 unique e-mail addresses to which phishing messages were sent between March 16 and September 14, 2015. At the same time, it is clear that the greatest number of attacks falls on Monday or Friday.

Our experts suggest that regular bursts of activity correspond to the launch time of new phishing campaigns.
Malicious Emails
Grouping Sednit uses emails to infect users by sending them either a malicious attachment or a malicious link to a set of exploits inside the letter. In the case of attachments, Sednit resorts to exploits for such common products as Microsoft Word, Microsoft Excel, Adobe Flash and Adobe Reader.
In the screenshot below, you can see the phishing message used by the group, allegedly from the All-Ukrainian Economic Union, to which is attached a document with information on the deterioration of relations between Russia and the EU.

In this particular case, the attached RTF file exploits a vulnerability in Office to drop the victim of another malicious component onto the disk. In the case of other cyber attacks, the group used the themes of current news feeds to lure the user to a malicious resource to download the file. Examples of such news topics are listed below.
- "West's military advantage is being eroded, report warns"
- "Despite ISIS Attacks, North Korea Remains the` Varsity` of Global Threats "
- "Taking War Seriously: a Russia-NATO Showdown Is No Longer Just Fiction"
- "Russia warns Turkey over Aegean warship incident"
- "Iraq warns of attacks before Paris assault"
Using zero day vulnerabilities
Using 0day exploits allows the group to solve two problems, firstly, to increase their chances of successfully compromising the system, and secondly, to install malware in an automatic mode with minimal user intervention.
ESET specialists found that only in 2015 the group used exploited at least six 0day vulnerabilities for Windows, Adobe Flash and Java.

In addition, as will be described in subsequent posts, the group has developed dozens of its malicious programs, including backdoors with various modules, bootkits, and rootkits to successfully complete the tasks.
The full version of the analysis of the activities of the group Sednit can be found at this link .
Source: https://habr.com/ru/post/313188/
All Articles