Google telephone interview experience demonstrating the failure of the hiring process
"The diagnosis is not the end, but the beginning of the case."
Martin H. Fisher.
Recently, I had a phone interview with a human resource manager from Google. Since I met the criteria for such (voluntary) interview, but could not take the test, this post lists the questions and the supposed answers to them . This post may be useful to those who one day will call from Google.
For clarity: I started programming 37 years ago (I was then 11 years old) and I’ve been doing it all the time. In addition, 24 years ago (I was 24) I was appointed director of research and development ; Since then, among many other works, I have carried out R & D on the most crucial parts of TWD projects - all of them are supplied as commercial products:
')
A Google representative stressed that both management experience and modern programming is required (a rare combination). But having more than 20 years of experience in the first and almost 40 years in the second turned out to be insufficient - I could not give the “right answers” . Does this mean that Google is raising the bar too high, or that its personnel officers themselves lack the knowledge they are supposed to evaluate?
Let's get a look!
Here are the questions that require "high technical qualification", and my answers to them - until the test was interrupted, since it became obvious that I was not up to the task:
On the other hand, I scored four points out of ten, which is even higher than my best Google rank web page for today!
(*) Both Google and TWD were founded in 1998.
(**) Google-rank web page: a top-secret mathematical formula showing that the rank of sponsored search results is higher than what it actually is.
Advice: hiring people who know what you do not know helps more than hiring people who simply know what everyone knows .
Update: on October 13, 2016 at night (almost 7 months after the publication of this post) we received messages that the server providing the website gwan.ch worked for several hours and had received several emails related to the discussion on the website Hacker News “ In which people who claimed to work at Google denied that the above questions were actually used by recruiting specialists at Google, while others claimed that they had the same interview with exactly the same questions.
I did not have time to read the entire discussion, but some letters were clearly not published, which helped others to advance. First of all, I would like to say that my criterion of relevance in the discussion is goodwill. I want to congratulate those who succeeded in this, acting in difficult conditions.
I didn’t get Google to do this interview. However, after the episode with Hacker News, I received very interesting job offers, as well as resumes from specialists who want to work with us in the TWD project, which shows understanding (if not the majority) of the world in which we actually live. Many thanks to all for the comments, for the kind support, allowing me to hope for the next generation of engineers.
I really would like to have the opportunity to train (and recruit) everyone who wants to learn. If I do not find anything better, then somehow I will write a book to help others do good better than I did - and I promise to publish completely new information (open source, Academia materials, etc.).
All the best ( including Google).
Update: Business Insider magazine published this story (25,000 reads to date).
Update: LinkedIn rationalized this story (published by three different people), and all the supporting comments were written by technical experts (I don’t know most of them).
Update: A Google employee blog post , successfully posted on LinkedIn and using disjointed garbage lexicon (obviously aimed at associating abusive words with my name on search engines), was written by someone who looks like a front person (orange underlines the text , working on Google, red - incoherent angry expressions):
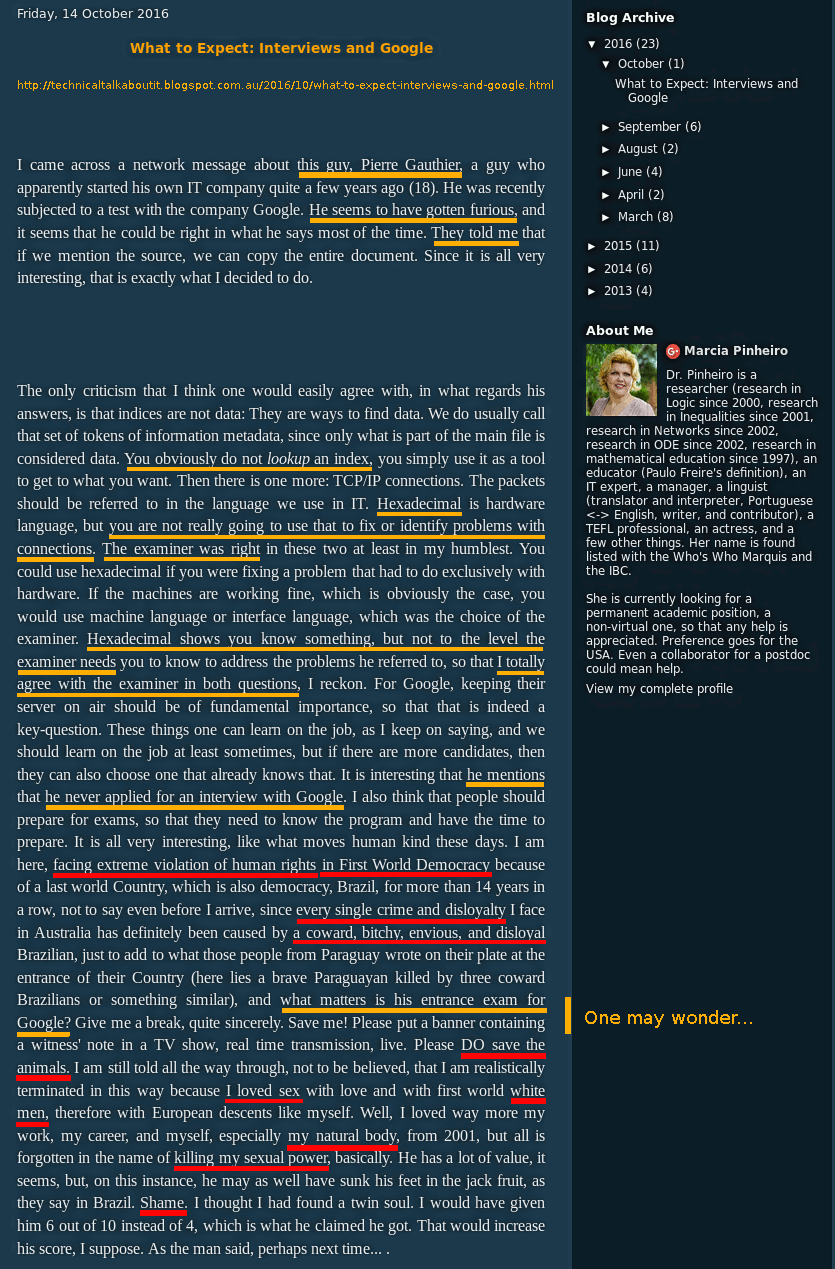
LinkedIn's profile for Marcia Pineiro shows that she works in ... Google. If this is a real person (she also has 3 accounts [ 1 ] [ 2 ] [ 3 ]), then I am sad for her - she has to throw mud at people in order to earn a living. If Google really hired her (or “him”, hidden behind a fake person), then this is a great way to keep the last word. Google adheres to the principle of "Do not do evil" ?
Update: LinkedIn finally posted my post, albeit without reader comments and with a delay of 12 hours. Three other posts written by technical experts who sent me a confirmation of viewing, were not so lucky.
Update: Business Insider magazine has published a (very good) article reviewing Google’s impressive recruitment failures and containing an interesting insight into the problems of experienced technical experts. I highly recommend reading (even to Google employees).
Martin H. Fisher.
Recently, I had a phone interview with a human resource manager from Google. Since I met the criteria for such (voluntary) interview, but could not take the test, this post lists the questions and the supposed answers to them . This post may be useful to those who one day will call from Google.
For clarity: I started programming 37 years ago (I was then 11 years old) and I’ve been doing it all the time. In addition, 24 years ago (I was 24) I was appointed director of research and development ; Since then, among many other works, I have carried out R & D on the most crucial parts of TWD projects - all of them are supplied as commercial products:
')
- Global WAN ( distributed C / VHDL L2 VPN based on a custom kernel-bypass IP stack and our own post-quantum encryption method)
- G-WAN (200-kilobyte application server with 17 embedded programming languages C / C ++, C #, Objective-C, Java, Go, PHP, etc.)
- Remote Anything (patented enterprise network management solution, 280 million licenses used in 138 countries )
A Google representative stressed that both management experience and modern programming is required (a rare combination). But having more than 20 years of experience in the first and almost 40 years in the second turned out to be insufficient - I could not give the “right answers” . Does this mean that Google is raising the bar too high, or that its personnel officers themselves lack the knowledge they are supposed to evaluate?
Let's get a look!
Questions and answers on Google test for the position of "Technical Director"
Here are the questions that require "high technical qualification", and my answers to them - until the test was interrupted, since it became obvious that I was not up to the task:
1. What is the opposite function for malloc () in C?Note: I imagine that in these rare moments you can be assumed to feel pride in your 35 years of programming in C, which is more than 40 years old.
I: free ().
Personnel: correct.
2. What Unix function allows a socket to get connections?Note: does it really qualify me as a network specialist?
I: listen ().
Personnel: correct.
3. How many bytes are required to store the MAC address?Note: I guess I just got a badge [Ethernet] ...
I: six.
Personnel: correct.
4. Allocate time-consuming: reading the CPU register, searching the disk, switching the context, reading the system memory.Note: The usual lectures on computer engineering in the first year of university.
Me: reading the register of the CPU, reading the system memory, switching the context, searching the disk.
Personnel: correct.
5. What is a Linux inode?Note: “metadata” is a more informative term than “file attributes”?
I: a unique file identifier for any given file system.
Personnel: wrong, this is file metadata.
I: the inode is an index that uniquely identifies a file in a given file system, and you can view this index to extract file attributes, such as size, time, owner, and permissions; You can even add your own attributes to such file systems.
Personnel: wrong, not “attributes”, this is “metadata”.
6. What Linux function takes a path and returns an inode?Note: Could it be that Google secretly got a license for the notorious chat bot Tay AI from Microsoft?
Me: I wrote a custom LIBC for G-WAN, our application server, but I don’t remember any syscall returning the inode.
Personnel: stat ().
I: stat (), fstat (), lstat () and fstatat () - they all return an error code, not an inode; they fill in the stat structure containing the file attributes named above, and not just the file inode.
Personnel: The answer is not correct: the inode contains all the metadata.
7. What is the name of the KILL signal?Note: I assume the observable is what happens when chat bots discover the existence of soft drugs.
Me: SIGKILL, with #define set to 9.
Personnel: No, this is “TERMINATE”.
Me: SIGTERM (15) is different from the KILL (9) signal.
Personnel: your answer does not match what is in my document.
8. Why is Quicksort the best sorting method?Note: For the Linux kernel (which Google relies on), Heapsort was chosen, not Quicksort ... for less memory usage and more predictable execution time.
I: this is not always the case, it does not even always fit.
Personnel: Quicksort has the best big-O rating.
Me: “big-O” ignores data storage delays, topology, size, available memory, and even the computational complexity of each CPU command involved in this procedure — instead, it simply counts the number of algorithmic operations! A “big-O” score may be a useful indicator in the design of algorithms, but the best solution for implementation and scaling depends on the specific constraints of each particular problem and environment.
Kadrovik: wrong, you should have given me the reason for the high mark of “big-O” from Quicksort.
9. There is an array of 10,000 16-bit values; How most effectively to count bits?Note: how much can this madness last? The 8-bit transcoding table can process the bytes sequentially one after the other, while the method based on a 64-bit mask processes 8-byte words simultaneously (moreover, modern CPU commands allow working even with 128-bit words, receiving a 10-fold gain in speeds, if not considered portability). Since the 64-bit conversion table is not available to modern computers, there is no doubt that it works faster.
I: it is necessary to shift the bits right on all 64-bit words using the Kernighan method.
Personnel: no.
Me: there are faster ways to process 64-bit words with masks, but I can't explain it by phone - you need to write code.
Personnel: The correct answer is to use the conversion table and then sum the results.
I: what type of CPU? Why not let me compare the results of my program and yours?
Personnel: it is not included in the task of this test.
I: what is the task of this test?
Kadrovik: I need to find out if you know the right answers.
10. What is the type of packets that are exchanged to establish a TCP connection?Note: if you have to read hex dumps of packages to find the cause of the failure, then 3-letter mnemonic codes will not help you find it in the dead network service. Perhaps Google should have stated that practical knowledge is not required for this work.
I: in hexadecimal: 0x02, 0x12, 0x10 - literally “synchronize” and “confirm”.
Shot: wrong, this is a SYN, SYN-ACK and ACK; if there’s a problem with Google, you need to know it in order to diagnose it. We stop testing because it is obvious that you do not have the required knowledge to write or analyze network applications. You need to examine the Linux function calls, how the TCP / IP stack works, and what “big-O” is, to possibly meet our requirements if you will have such an interview later. Good luck, goodbye!
On the other hand, I scored four points out of ten, which is even higher than my best Google rank web page for today!
(*) Both Google and TWD were founded in 1998.
(**) Google-rank web page: a top-secret mathematical formula showing that the rank of sponsored search results is higher than what it actually is.
Advice: hiring people who know what you do not know helps more than hiring people who simply know what everyone knows .
Update: on October 13, 2016 at night (almost 7 months after the publication of this post) we received messages that the server providing the website gwan.ch worked for several hours and had received several emails related to the discussion on the website Hacker News “ In which people who claimed to work at Google denied that the above questions were actually used by recruiting specialists at Google, while others claimed that they had the same interview with exactly the same questions.
I did not have time to read the entire discussion, but some letters were clearly not published, which helped others to advance. First of all, I would like to say that my criterion of relevance in the discussion is goodwill. I want to congratulate those who succeeded in this, acting in difficult conditions.
I didn’t get Google to do this interview. However, after the episode with Hacker News, I received very interesting job offers, as well as resumes from specialists who want to work with us in the TWD project, which shows understanding (if not the majority) of the world in which we actually live. Many thanks to all for the comments, for the kind support, allowing me to hope for the next generation of engineers.
I really would like to have the opportunity to train (and recruit) everyone who wants to learn. If I do not find anything better, then somehow I will write a book to help others do good better than I did - and I promise to publish completely new information (open source, Academia materials, etc.).
All the best ( including Google).
Update: Business Insider magazine published this story (25,000 reads to date).
Update: LinkedIn rationalized this story (published by three different people), and all the supporting comments were written by technical experts (I don’t know most of them).
Update: A Google employee blog post , successfully posted on LinkedIn and using disjointed garbage lexicon (obviously aimed at associating abusive words with my name on search engines), was written by someone who looks like a front person (orange underlines the text , working on Google, red - incoherent angry expressions):

LinkedIn's profile for Marcia Pineiro shows that she works in ... Google. If this is a real person (she also has 3 accounts [ 1 ] [ 2 ] [ 3 ]), then I am sad for her - she has to throw mud at people in order to earn a living. If Google really hired her (or “him”, hidden behind a fake person), then this is a great way to keep the last word. Google adheres to the principle of "Do not do evil" ?
Update: LinkedIn finally posted my post, albeit without reader comments and with a delay of 12 hours. Three other posts written by technical experts who sent me a confirmation of viewing, were not so lucky.
Update: Business Insider magazine has published a (very good) article reviewing Google’s impressive recruitment failures and containing an interesting insight into the problems of experienced technical experts. I highly recommend reading (even to Google employees).
Source: https://habr.com/ru/post/313028/
All Articles