How to find subdomains in minutes?
The search for subdomains is an integral part of preparation for hacking, and thanks to some tools, opposition to these actions has become much easier.
Unprotected subdomains put your activities at serious risk, and recently there have been a number of incidents in which hackers used subdomains to bypass protection.
In the case of the last in a series of incidents, the entire Vine site code could be downloaded from an unprotected subdomain.
')
If you are a site owner or are studying information security issues, you can use the following tools to find subdomains of any domain.

From the translator:
I hope that these tools will help you to save information on your virtual and dedicated servers.
List of tools:
1. Censys
First of all, to search for subdomains, as a rule, they resort to Censys . In addition to the subdomain, you can find many more interesting things, namely:

You will get a good overview of domain information.
2. Pentest-Tools
Using Pentest-Tools , you can use several methods when searching for a subdomain, for example: transferring a DNS zone, iterating over a DNS based on a word list or using a search engine.
Search results can be saved in PDF format.
3. DNS Dumpster
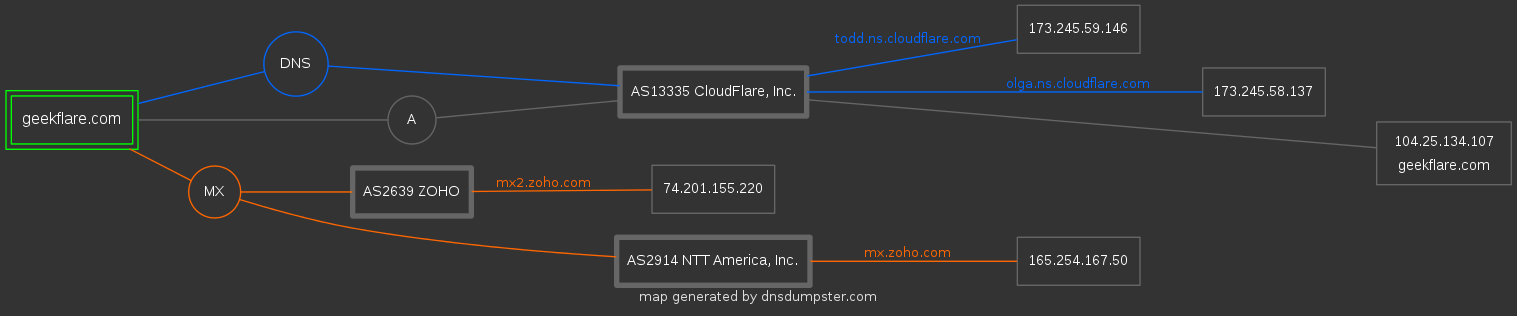
DNS Dumpster is a tool for finding domain and host information. Authors of the project - HackerTarget.com.
You can find information not only about the subdomain, but also about the DNS server, MX and TXT records, as well as get a graphical representation of information about your domain.
4. Sublist3r
Sublist3r is a Python language tool for detecting subdomains using search engines. Sublist3r currently supports Google, Yahoo, Bing, Baidu, Ask, Netcraft, Virustotal, ThreatCrowd, DNSdumpster and PassiveDNS.
Sublist3r only supports Python version 2.7 and is dependent on several libraries.
You can use this tool on Windows, CentOS, RedHat, Ubuntu, Debian, and any other UNIX-based OS. Below is an example for CentOS.
Unzip the downloaded file:
As I mentioned earlier, there are the following dependencies, which can be installed using the yum command:
Now everything is ready to detect subdomains with the following command:
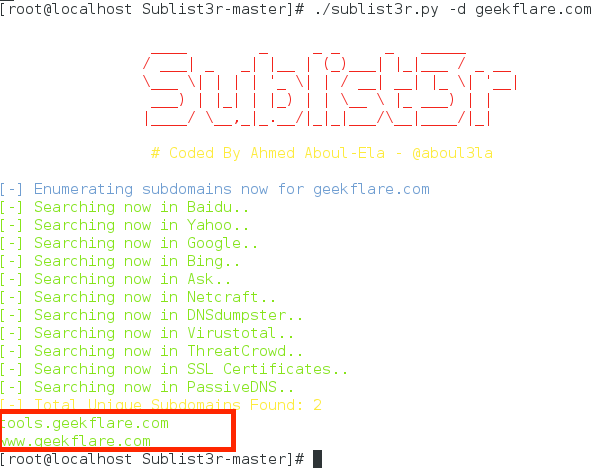
As you can see, the tool found my subdomains.
5. Netcraft
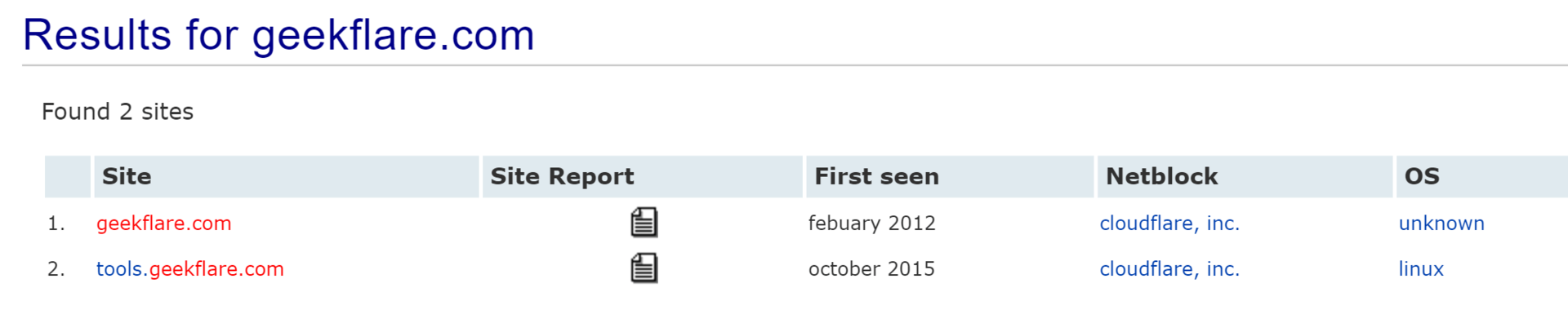
Netcraft has an extensive database of domains and should not be avoided when searching for public information about subdomains.
The search result will contain all information about the domain and subdomains, including the date of the first viewing, the range of addresses and information about the operating system. If you need to get more information about the site, just open the site report and you will be provided with a lot of information about technology, ranking, etc.
6. CloudPiercer
CloudPiercer can sometimes be useful when searching for information about whether a subdomain of your domain exists. By the way, CloudPiercer is a terrific and easy way to find out if the actual IP address of your site is protected. Open IP address information makes your site vulnerable to DDoS attacks.
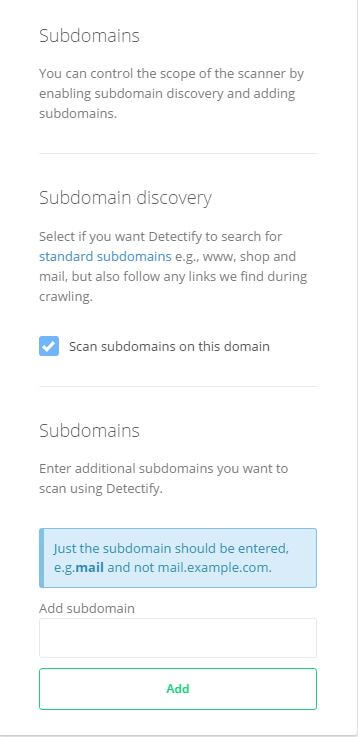
7. Detectify
Detectify searches for subdomains by a predefined list of several hundred words, but only if you are the owner of the domain. However, if you are a registered Detectify user, you can enable the detection of subdomains in the overview section in the settings.
8. SubBrute
SubBrute is one of the most popular and accurate subdomain listing tools. The project was developed by the community and uses an open name resolver as a proxy, so SubBrute does not send traffic to the target DNS server.
This is not an online tool, so you have to install it on your computer. SubBrute can be used on Windows or UNIX systems. The program is very easy to install. Below is an example for CentOS / Linux.
A new subbrute-master folder will be created. Go to the folder and run subbrute.py with the required domain.
The operation will take several seconds and the found subdomains will be displayed.
9. Knock
Knock is another Python tool for detecting subdomains. It is tested for Python 2.7.6. Knock finds the subdomains of the target domain by the word list.
After installation, you can search for subdomains as follows:
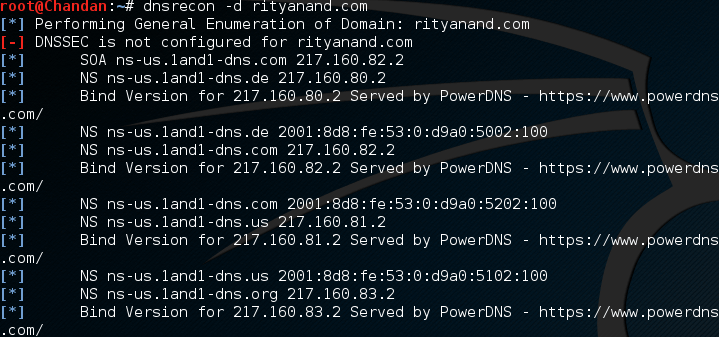
10. DNSRecon for Kali Linux
Kali Linux is a great platform for assessing information security and you can use DNSRecon on it without installing any additional tools.
DNSRecon checks all NS records for zone changes, common DNS records, pattern processing, PTR records, etc.
To use DNSRecon, simply run the following command.
I hope that using the above tools, you will be able to detect the subdomains of the target domain as part of your information security assessment work. Let me know which one you like the most.
I want to remind that recently I earned a project for which we collected more than 8.5 thousand reviews from various forums about 344 hosts - Poisk.Hosting . Virtual servers can still be found on the VDS.menu website, and virtual hosting on SHARED.menu .
Unprotected subdomains put your activities at serious risk, and recently there have been a number of incidents in which hackers used subdomains to bypass protection.
In the case of the last in a series of incidents, the entire Vine site code could be downloaded from an unprotected subdomain.
')
If you are a site owner or are studying information security issues, you can use the following tools to find subdomains of any domain.

From the translator:
I hope that these tools will help you to save information on your virtual and dedicated servers.
List of tools:
- Censys
- Pentest-Tools
- DNS Dumpster
- Sublist3r
- Netcraft
- CloudPiercer
- Detectify
- Subbrute
- Knock
- DNSRecon on Kali Linux
1. Censys
First of all, to search for subdomains, as a rule, they resort to Censys . In addition to the subdomain, you can find many more interesting things, namely:
- IP data (may be useful for finding a real IP address );
- certificate information;
- open ports;
- SSL / TLS handshake protocol and encryption algorithms (useful when searching for weak ciphers / protocols).

You will get a good overview of domain information.
2. Pentest-Tools
Using Pentest-Tools , you can use several methods when searching for a subdomain, for example: transferring a DNS zone, iterating over a DNS based on a word list or using a search engine.

Search results can be saved in PDF format.
3. DNS Dumpster
DNS Dumpster is a tool for finding domain and host information. Authors of the project - HackerTarget.com.
You can find information not only about the subdomain, but also about the DNS server, MX and TXT records, as well as get a graphical representation of information about your domain.

4. Sublist3r
Sublist3r is a Python language tool for detecting subdomains using search engines. Sublist3r currently supports Google, Yahoo, Bing, Baidu, Ask, Netcraft, Virustotal, ThreatCrowd, DNSdumpster and PassiveDNS.
Sublist3r only supports Python version 2.7 and is dependent on several libraries.
You can use this tool on Windows, CentOS, RedHat, Ubuntu, Debian, and any other UNIX-based OS. Below is an example for CentOS.
- Log into your Linux server;
- Download the latest version of Sublist3r
wget https://github.com/aboul3la/Sublist3r/archive/master.zip Unzip the downloaded file:
unzip master.zip - A new folder “Sublist3r-master” will be created.
As I mentioned earlier, there are the following dependencies, which can be installed using the yum command:
yum install python-requests python-argparse Now everything is ready to detect subdomains with the following command:
./sublist3r.py -d yourdomain.com 
As you can see, the tool found my subdomains.
5. Netcraft
Netcraft has an extensive database of domains and should not be avoided when searching for public information about subdomains.

The search result will contain all information about the domain and subdomains, including the date of the first viewing, the range of addresses and information about the operating system. If you need to get more information about the site, just open the site report and you will be provided with a lot of information about technology, ranking, etc.

6. CloudPiercer
CloudPiercer can sometimes be useful when searching for information about whether a subdomain of your domain exists. By the way, CloudPiercer is a terrific and easy way to find out if the actual IP address of your site is protected. Open IP address information makes your site vulnerable to DDoS attacks.
7. Detectify
Detectify searches for subdomains by a predefined list of several hundred words, but only if you are the owner of the domain. However, if you are a registered Detectify user, you can enable the detection of subdomains in the overview section in the settings.

8. SubBrute
SubBrute is one of the most popular and accurate subdomain listing tools. The project was developed by the community and uses an open name resolver as a proxy, so SubBrute does not send traffic to the target DNS server.
This is not an online tool, so you have to install it on your computer. SubBrute can be used on Windows or UNIX systems. The program is very easy to install. Below is an example for CentOS / Linux.
- Log into your Linux server
- Download the latest SubBrute
wget https://github.com/TheRook/subbrute/archive/master.zip - Unzip the downloaded zip file
unzip master.zip A new subbrute-master folder will be created. Go to the folder and run subbrute.py with the required domain.
./subbrute.py yourdomain.com The operation will take several seconds and the found subdomains will be displayed.
9. Knock
Knock is another Python tool for detecting subdomains. It is tested for Python 2.7.6. Knock finds the subdomains of the target domain by the word list.
- Knock can be installed on a Linux based OS.
wget https://github.com/guelfoweb/knock/archive/knock3.zip - Unzip the downloaded zip file with the unzip command
unzip knock3.zip - As a result, a new folder “knock-knock3” will be created.
- Go to the folder and install using the following command
python setup.py install After installation, you can search for subdomains as follows:
./knockpy.py yourdomain.com 10. DNSRecon for Kali Linux
Kali Linux is a great platform for assessing information security and you can use DNSRecon on it without installing any additional tools.
DNSRecon checks all NS records for zone changes, common DNS records, pattern processing, PTR records, etc.
To use DNSRecon, simply run the following command.
dnsrecon –d yourdomain.com 
I hope that using the above tools, you will be able to detect the subdomains of the target domain as part of your information security assessment work. Let me know which one you like the most.
I want to remind that recently I earned a project for which we collected more than 8.5 thousand reviews from various forums about 344 hosts - Poisk.Hosting . Virtual servers can still be found on the VDS.menu website, and virtual hosting on SHARED.menu .
Source: https://habr.com/ru/post/312954/
All Articles