Security Week 41: patch week, 12-year-old vulnerability in sshd returns, StrongPity APT
 Last week, the 26th VB conference was held in Denver, organized by the most authoritative long-lived portal Virus Bulletin. The conference on the subject is similar to BlackHat , but there is much less show and more technical details. Laboratories experts spoke at the conference with two presentations. With one, about the false evidence of the identity of malicious code and targeted attacks, I suggest to familiarize yourself, and I will tell you about the other in more detail.
Last week, the 26th VB conference was held in Denver, organized by the most authoritative long-lived portal Virus Bulletin. The conference on the subject is similar to BlackHat , but there is much less show and more technical details. Laboratories experts spoke at the conference with two presentations. With one, about the false evidence of the identity of malicious code and targeted attacks, I suggest to familiarize yourself, and I will tell you about the other in more detail.The StrongPity attack ( news , research ) is interesting not so much by its capabilities for data theft (it's hard to surprise here at all) as by targeting the victims. The attack organizers created several web pages that mimic the official websites of popular software, specifically WinRAR and TrueCrypt. Links to these websites were also able to be dragged onto a pair of software aggregators.
On the fake sites distributed prepared distributions of the above software were distributed: they worked, but had additional functionality aimed at collecting and stealing data. In addition, the malicious components made it possible to profile victims in more detail. There was a search for specialized admin software, software for encryption or for remote access: putty, winscp, a pair of Remote Desktop clients, and so on. Treat this behavior can be different. First, obviously, there were targeted attempts to attack the system administrators, a priori, having expanded rights in the victim's network. Secondly, targeting victims who use software to encrypt data suggests a targeted search for those who have something to hide.
Network devices are susceptible to SSHD 12 years old
News Akamai research .
')
A powerful DDoS attack on the site of security expert Brian Krebs in September ( news ) attracted increased attention to offline network devices, which can also be attributed to the “Internet of things”. Thanks to the source code of the software uploaded to the network for automated and hacking of vulnerable devices, it was finally confirmed that the attack was used, though not for the first time, but with the maximum scale, IoT botnet. The problem was tracked ( news ) to a specific OEM manufacturer of devices - digital video recorders, video surveillance systems and IP cameras. Alas, there is no need to talk about “hacking” of the devices of this vendor: the wired password of the superuser can rather be interpreted as a complete lack of protection for devices permanently connected to the network.
But there are slightly less trivial options. Researchers at Akamai this week published a paper that analyzed the vulnerability of a network video recorder. The study began with a customer complaint of malicious activity associated with such a device. The security analysis of the recorder showed the following: the recorder's web interface is locked with a default password (admin: admin). The web interface, however, is not necessarily available when connecting from outside the local network, but it is possible to connect via ssh. Logging in with the default password for ssh, however, also fails - this option is blocked in the settings.
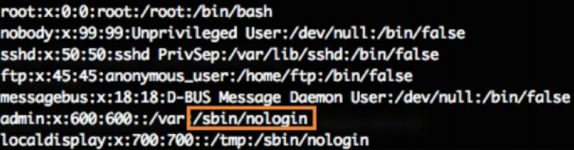
Unfortunately, the default is to connect over ssh in proxy mode (AllowTcpForwarding option is enabled), which allows you to bypass the restriction. As a result, a recorder (it is possible that other devices too) can at least be used for handling malicious traffic. As a maximum - use the device to hack the local network in which it is installed. It is noteworthy that this vulnerability (rather the wrong configuration) was described ( CVE-2004-1653 ) 12 years ago in relation to OpenSSH, but it still occurs.
It seems it is time to declare a month of struggle with default passwords.
Week of patches: Microsoft, Adobe, Cisco, Chrome
This week was also marked by a large number of patches for popular or strategically important software. Microsoft ( news ) closed 10 vulnerabilities, five of which were classified as zero-day - there were already recorded cases of attacks with their use at the time of the release of the patch. Vulnerabilities that could lead to remote code execution are closed in Microsoft Edge, MS Office (RTF document processing) and the Microsoft Internet Messaging API component (can be exploited via MS Outlook).

Adobe quarterly patch has closed more than 80 holes in its products ( news ), most in Acrobat and Reader, plus some vulnerabilities in Adobe Flash. Cisco, which recently had to quickly patch the vulnerabilities revealed in the ShadowBrokers leak, closed several other critical holes in the NX-OS used in Nexus routers. Finally, Google has closed 21 vulnerabilities in the Chrome browser, discovered as part of working with independent researchers on the Bug Bounty program. Among them - two serious vulnerabilities in the embedded PDF viewer.
What else happened
This week, Reuters quoted IAEA Director General Yukiya Amano, who publicly confirmed the successful cyber attack on the nuclear power plant. No details, we only know that the attack caused a "malfunction." Presumably the attack occurred 2 or 3 years ago.
Interesting research about a keylogger who steals credit card data on the web server side. Obviously an increase in the "effectiveness" of the attack in this scenario.

Antiquities
Family “Little”
Non-resident very dangerous viruses. The length is only 45 or 46 bytes. Extremely primitive. Write themselves to the beginning of all .COM files in the current directory without saving the old contents of these files. The affected files, of course, are not restored.
Quote from the book "Computer viruses in MS-DOS" Eugene Kaspersky. 1992 Page 37.
Disclaimer: This column reflects only the personal opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. Then how lucky.
Source: https://habr.com/ru/post/312700/
All Articles