How MikroTik sees neighbors. Neighbor discovery update in RouterOS 6.38
The service of detecting neighboring routers and compatible equipment has been present in RouterOS for a long time. Unfortunately, comrades admins rarely think about the “Neighbor Discovery” operating scheme. It seems as if everything is simple, but just not as it seems.
The unsuccessful attempts to hide the information about your MikroTik router, while receiving information about the routers of the neighbors within the provider’s broadcast-domain, serve as a graphic illustration. So to speak, to spy on the neighbors on the provider switch. This usually looks like a firewall's ban on sending discovery UDP service announcement 255.255.255.255,5678. Having driven the prohibiting rule into the firewall configuration, some believe that they have completely hidden their router from being visible to their neighbors. But it is not.
Let's see how Neighbor Discovery works in MikroTik.
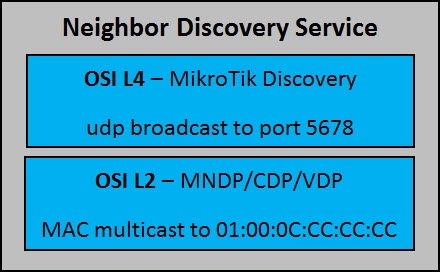
Neighbor Discovery in RouterOS up to 6.38 contains two ways to advertise and retrieve information that work at different levels of the OSI model: the UDP transport operates on the L4 level, and the MNDP / VDP / CDP family of information on the L2 level receives and transmits it. Information obtained from both sources is combined and displayed in the list of detected neighbors “ / ip neighbors ”. This is what Neighbor Discovery looks like in the current release:
')
Thus, by simply prohibiting the sending of UDP packets to port 5678, it is impossible to hide information about the router. You must either completely disable the Neighbors service on the interface with the command / ip neighbor discovery set ether1-gateway discover = no, or filter outgoing L2 traffic for MNDP packets using bridge filters. For example, like this:
Now a new version of RouterOS 6.38 is being prepared for release, and finally something happened in it that theBolsheviks had been talking about for so long the administrators of many countries asked. At 6.38 a good bun is finally added in the form of support for the open protocol LLDP . This further expands the capabilities of the equipment in terms of monitoring the state of the L2 connection. Now you can see any LLDP-compatible equipment in the list of neighbors, provided that it also includes support for LLDP ads. For example, now my test router perfectly “sees” the neighboring switch HP v1905-24
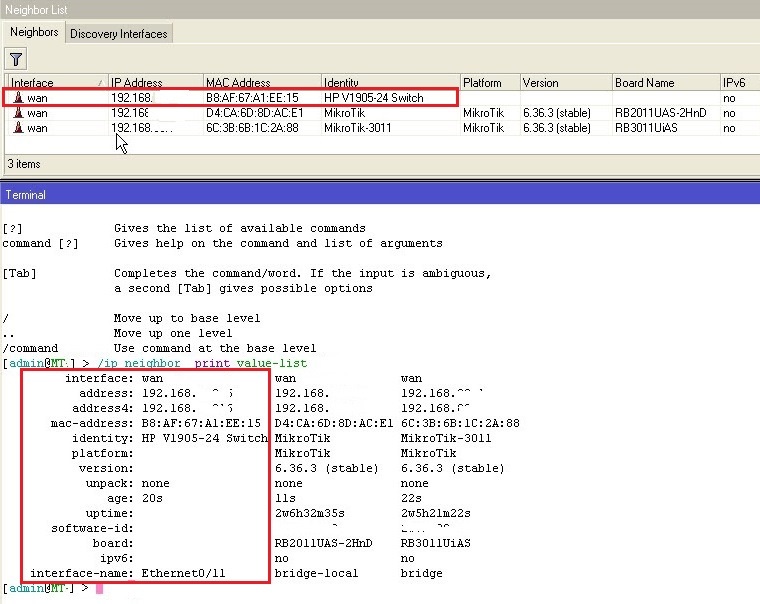
While information is received and transmitted a little, but for monitoring the presence / absence of visibility on L2 is enough. I note that LLDP support did not replace other protocols, but was added to the list of supported in MikroTik Discovery and starting from 6.38 it will look like this:

The official WiKi MikroTik has already added information about the information received and transmitted by RouterOS via LLDP.
RouterOS sends out:
Chassis subtype (MAC)
RouterOS accepts and processes:
Well, well, we are waiting for the official release and carefully monitor the test devices - for that, the status of 6.38 is still “rc”.
The unsuccessful attempts to hide the information about your MikroTik router, while receiving information about the routers of the neighbors within the provider’s broadcast-domain, serve as a graphic illustration. So to speak, to spy on the neighbors on the provider switch. This usually looks like a firewall's ban on sending discovery UDP service announcement 255.255.255.255,5678. Having driven the prohibiting rule into the firewall configuration, some believe that they have completely hidden their router from being visible to their neighbors. But it is not.

Let's see how Neighbor Discovery works in MikroTik.
Neighbor Discovery in RouterOS up to 6.38 contains two ways to advertise and retrieve information that work at different levels of the OSI model: the UDP transport operates on the L4 level, and the MNDP / VDP / CDP family of information on the L2 level receives and transmits it. Information obtained from both sources is combined and displayed in the list of detected neighbors “ / ip neighbors ”. This is what Neighbor Discovery looks like in the current release:
')

Thus, by simply prohibiting the sending of UDP packets to port 5678, it is impossible to hide information about the router. You must either completely disable the Neighbors service on the interface with the command / ip neighbor discovery set ether1-gateway discover = no, or filter outgoing L2 traffic for MNDP packets using bridge filters. For example, like this:
/interface bridge filter add action=drop chain=output disabled=no dst-mac-address=01:00:0C:CC:CC:CC/FF:FF:FF:FF:FF:FF out-interface=ether1-gateway. Now a new version of RouterOS 6.38 is being prepared for release, and finally something happened in it that the

Do not forget to enable LLDP on switch HP v1905-24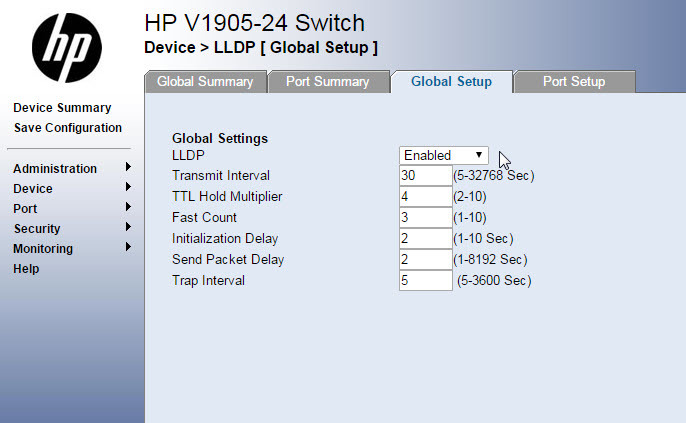

While information is received and transmitted a little, but for monitoring the presence / absence of visibility on L2 is enough. I note that LLDP support did not replace other protocols, but was added to the list of supported in MikroTik Discovery and starting from 6.38 it will look like this:

The official WiKi MikroTik has already added information about the information received and transmitted by RouterOS via LLDP.
RouterOS sends out:
Chassis subtype (MAC)
- Port subtype (interface name)
- TTL
- System name (system identity)
- Sys description ({platform} RouterOS {osvers} {boardName})
- All IP addresses are configured on the port.
RouterOS accepts and processes:
- identity (LLDP_TYPE_SYS_NAME)
- interfaceName (depending on the priority, if one is the empty checks the next: LLDP_TYPE_CHASSIS_ID, LLDP_TYPE_PORT_ID, LLDP_TYPE_PORT_DESC)
- ip4 (first entry of IPv4 LLDP_TYPE_MANAGEMENT_ADDR)
- ip6 (first entry of IPv6 LLDP_TYPE_MANAGEMENT_ADDR)
- TTL (LLDP_TYPE_TTL)
- MAC (Source - 6-11 byte)
Well, well, we are waiting for the official release and carefully monitor the test devices - for that, the status of 6.38 is still “rc”.
Source: https://habr.com/ru/post/312236/
All Articles