Cybersecurity games in Rio: how it was
The Olympic Games in Brazil ended a little more than a month ago, at which Cisco has traditionally been responsible for network and server infrastructure, including their security. And today we can already share our experience in providing network security for the Rio Summer Olympics, especially since we can already compare what is happening with the games in London in 2012, where Cisco also provided network security for all sports facilities and events.

For the first time, the serious informatization of the Olympic Games was talked about before the Winter Games in the Canadian Vancouver in 2010. Yes, oddly enough, but up to this point the world's largest sporting events could not boast of a serious IT infrastructure, although various stadiums and smaller events rather actively introduced modern information technologies into their operations. Cybersecurity was seriously dealt with only during the preparation for the London games in 2012. According to published statistics, 166 million cybersecurity events were recorded in London (in Beijing, about 12 million events were recorded daily), of which 783 required a detailed investigation. Serious attacks were 6 and one could even disrupt the opening ceremony - while hackers tried to attack the power supply system of the Olympic Stadium. In Rio, experts expected a fourfold increase in the number of cyber attacks; in reality, there were about 510 million, or about 400 attacks per second. During the Paralympic Games in Rio, hacker activity dropped to 120 attacks per second, which is understandable - interest in them is much lower than in the main games.
Obviously, the Olympic two weeks is a paradise for fraudsters and criminals of all stripes, especially in Brazil, which has never been on the list of countries that are prosperous in terms of crime. From the point of view of cybercrime, Brazil is considered one of the most dysfunctional - the growth of serious cyber attacks in it grew from 2010 to 2015 by 400%, with a noticeable 200% surge in 2014, when the country hosted the World Cup. And although according to Jane Weinwright, who headed the security of the organizing committee of the Olympic Games in London, there were no specific attacks on the Olympic infrastructure, this does not mean that there was nothing to fight with. It is enough to remember how many people attend sporting events in person and online in order to understand that the scale of the problem is serious enough.
')
In London, the five key threats to information security were considered:
In Rio, the situation was not very different; the problems were exactly the same - spam advertising fake ticketing sites, reports of allegedly won free tickets to sports events or other near-sports events, mailings with malicious attachments hiding under calendars and maps of Olympic events, phishing sites with Olympic news ( we have recorded and blocked several hundred such malicious domains), etc.
The task we faced was rather difficult - to provide in a short time a secure connection to the network and server infrastructure:
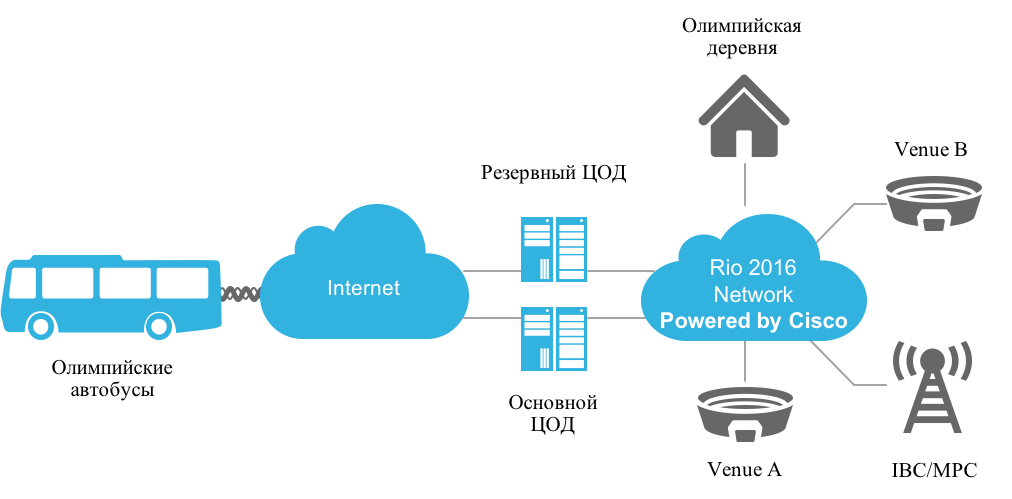
In ensuring the security of 113472 LAN ports and 5159 Wi-Fi wireless access points, the following principles were laid down:
In fact, they differed little from the similar infrastructure in London, where we also provided network security:
Considering the traditional nature of threats and defensive technologies, we used traditional ones. Of the 60 tons and 8115 units of equipment supplied for network security were responsible:
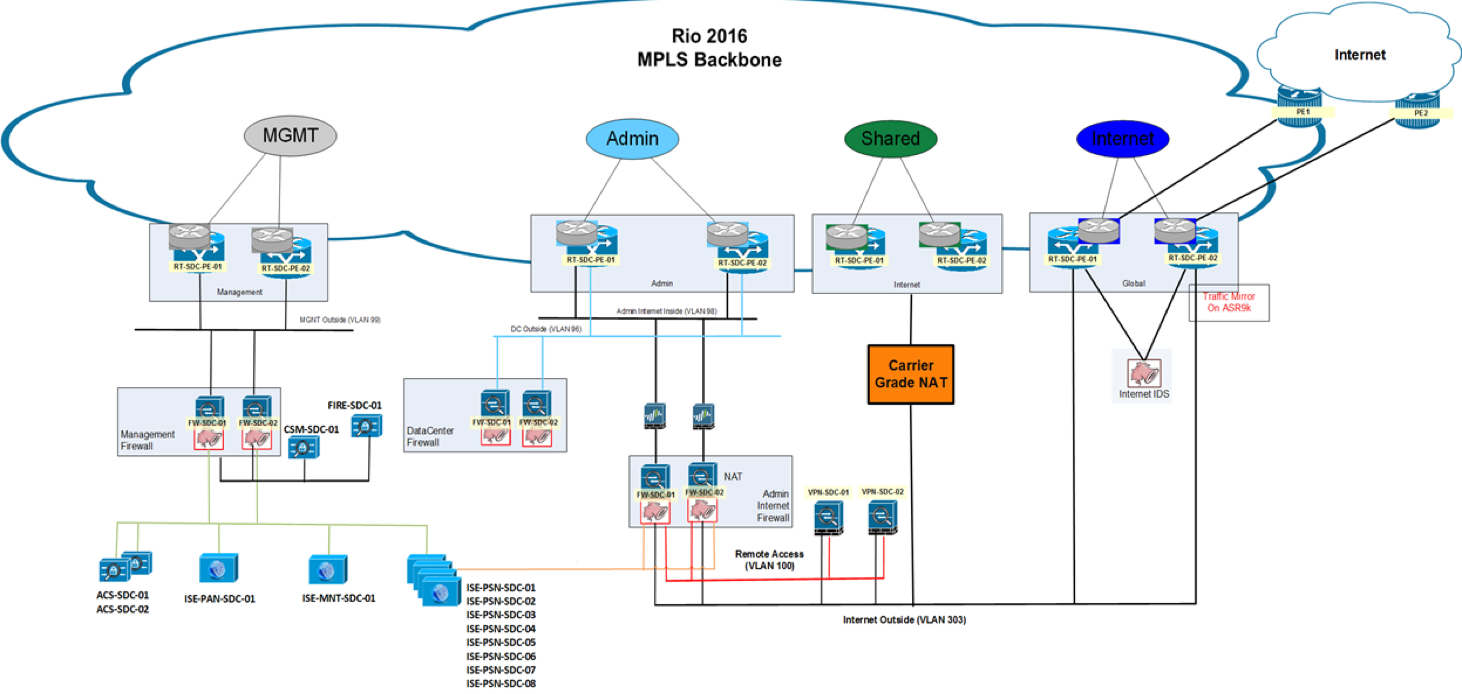
The main tool for the segmentation of steel firewalls Cisco ASA 5585-X and ASA 5515-X, which provide the separation of traffic between different zones of the Olympic infrastructure. Cisco ASR9000 and Cisco ASR1000 routers helped them with this. At the level of virtualization, the Nexus 7000, Nexus 2000, MDS 9000 switches, as well as the UCS 5000 and Fabric Interconnect 6000 computing systems were responsible for the segmentation.
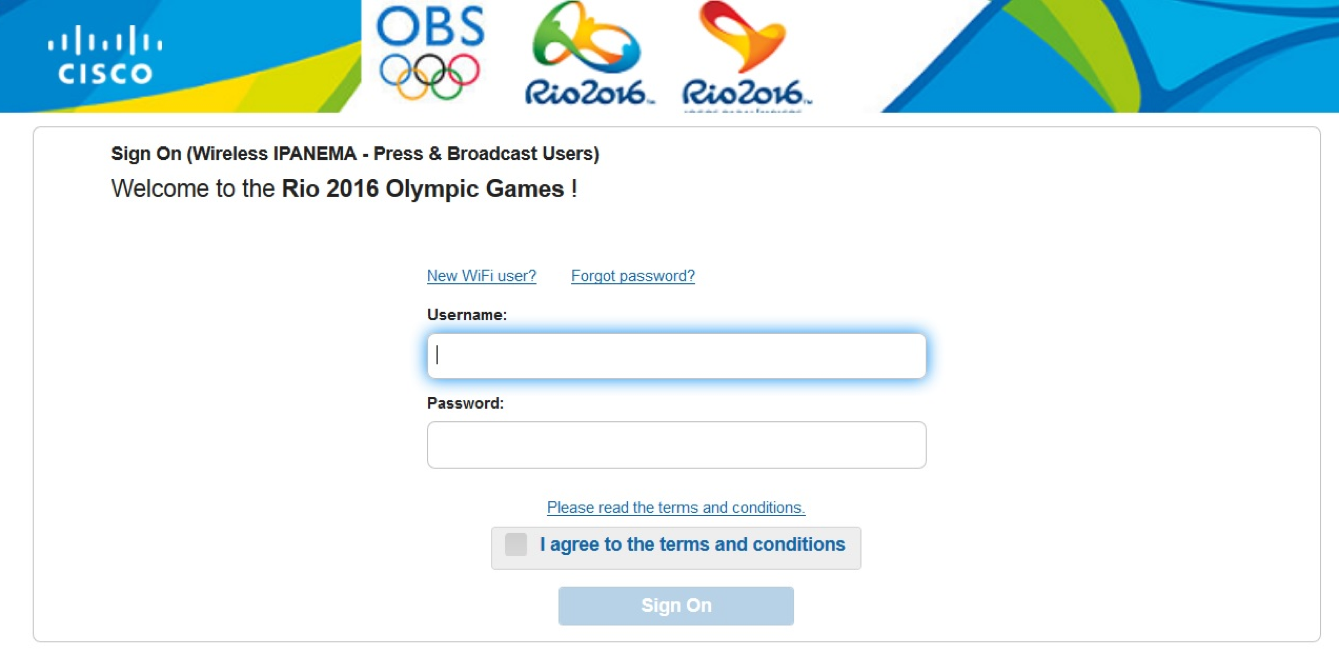
Since the Olympic Games are many different users with different tasks and access rights, we used a cluster of Cisco ISE devices that authenticated and authorized wired and wireless users to control and delimit them. So, for example, the portal of access for journalists of the press center looked like:
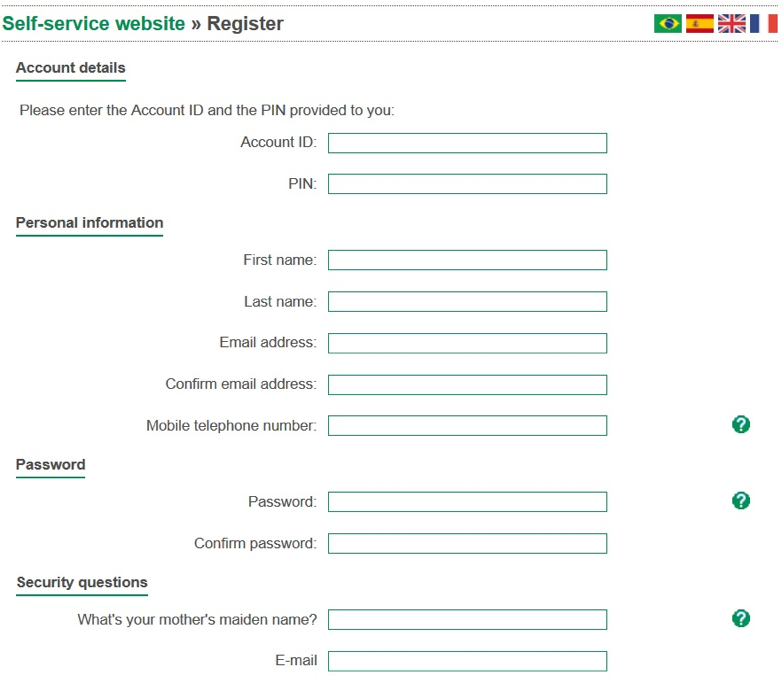
Considering the number of people who needed access to various services and services provided by the Olympic Organizing Committee, a self-service portal was raised on the Cisco ISE, which reduced the workload of the IT specialists of the Games. This self-service related to the registration of accounts:
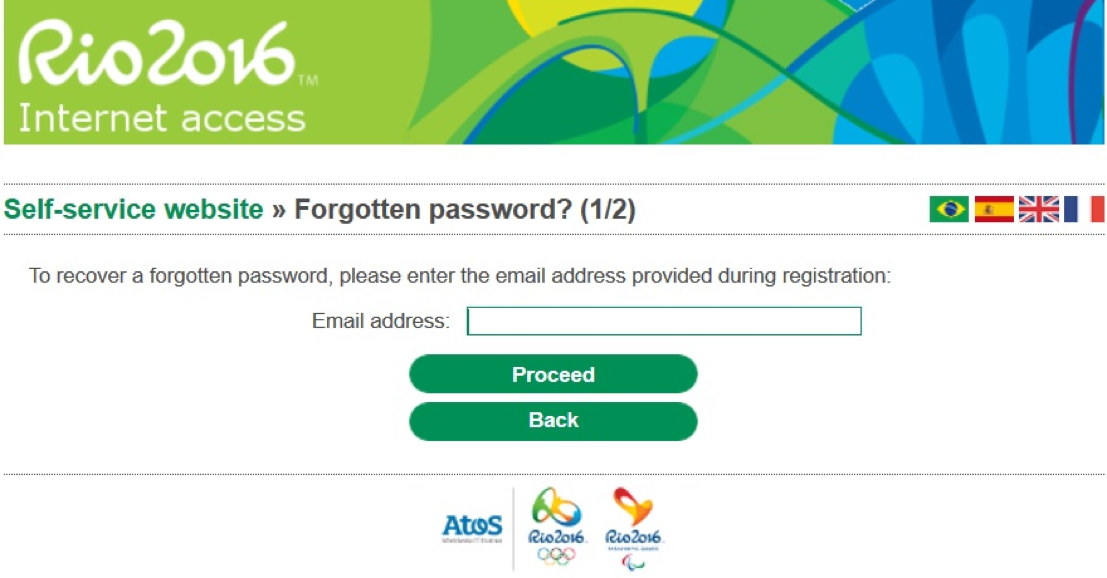
registering mobile devices and recovering forgotten passwords:
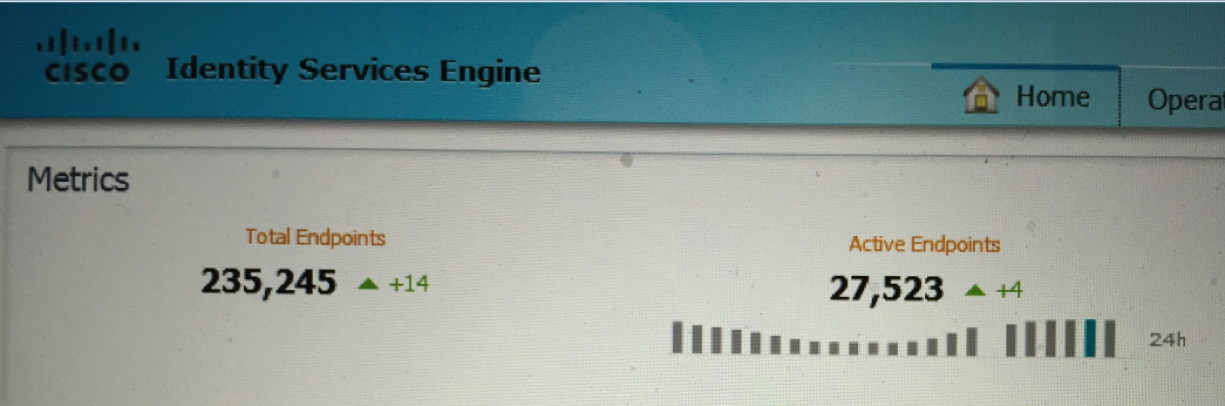
With the help of Cisco ISE, journalists, athletes, volunteers, sponsors, and others could access all necessary services during the entire Olympic and Paralympic Games, as well as in the process of preparing for them. At the same time, access was not limited to any network segments (unless it was required by security policies) or device types — Cisco ISE allowed you to receive secure wireless access when sportsmen were brought from the Olympic Village to sports events (Wi-Fi was deployed on buses) while journalists are working at the press center and at sports events themselves from their personal devices. The total number of unique devices (without visitors) connected to the infrastructure of the Olympic Games and managed using Cisco ISE exceeded 235 thousand by the end of the games (27 thousand devices were connected to the infrastructure at its peak during the closing ceremony of the Olympic Games in Rio):
For detection of attacks on the perimeter and inside the network, the Cisco Firepower NGIPS intrusion prevention system, the Cisco OpenDNS DNS threat monitoring system, and the Netflow-based anomaly neutralization system - Cisco Stealthwatch were responsible. At the same time, the last of the mentioned solutions monitored the virtual infrastructure in the primary and backup data centers of the Olympic infrastructure. Each of the mentioned solutions used network traffic as a source of data, but from different points of view, which made it possible to ensure the principle of echeloned defense and to prevent the penetration of attacks inside the Olympic network infrastructure.
An interesting experience was gained when using Cisco OpenDNS Umbrella, the task of which was to monitor DNS requests from the Olympic infrastructure and cut off everything that was associated with malicious activity:
We managed to implement Cisco OpenDNS Umbrella throughout the infrastructure in just 2 (!) Hours 2 days before the opening ceremony of the Games and already during its operation this service passed 22 million DNS requests through itself daily and 23 thousand of them blocked due to harmfulness.
Of the other interesting numbers that we could share, I would call the following:
These were for us the Olympic Games in Brazil in 2016. We have strengthened our competence in the field of mass sports protection and are planning to re-apply our experience at the games in Japan in 2020. It is already known that Japan plans to spend more than $ 190 million on this area, considering it as one of its priorities. Well, Cisco is ready to help this International Olympic Committee and Atos, the official provider of IT services for the Olympic Games.

For the first time, the serious informatization of the Olympic Games was talked about before the Winter Games in the Canadian Vancouver in 2010. Yes, oddly enough, but up to this point the world's largest sporting events could not boast of a serious IT infrastructure, although various stadiums and smaller events rather actively introduced modern information technologies into their operations. Cybersecurity was seriously dealt with only during the preparation for the London games in 2012. According to published statistics, 166 million cybersecurity events were recorded in London (in Beijing, about 12 million events were recorded daily), of which 783 required a detailed investigation. Serious attacks were 6 and one could even disrupt the opening ceremony - while hackers tried to attack the power supply system of the Olympic Stadium. In Rio, experts expected a fourfold increase in the number of cyber attacks; in reality, there were about 510 million, or about 400 attacks per second. During the Paralympic Games in Rio, hacker activity dropped to 120 attacks per second, which is understandable - interest in them is much lower than in the main games.
Obviously, the Olympic two weeks is a paradise for fraudsters and criminals of all stripes, especially in Brazil, which has never been on the list of countries that are prosperous in terms of crime. From the point of view of cybercrime, Brazil is considered one of the most dysfunctional - the growth of serious cyber attacks in it grew from 2010 to 2015 by 400%, with a noticeable 200% surge in 2014, when the country hosted the World Cup. And although according to Jane Weinwright, who headed the security of the organizing committee of the Olympic Games in London, there were no specific attacks on the Olympic infrastructure, this does not mean that there was nothing to fight with. It is enough to remember how many people attend sporting events in person and online in order to understand that the scale of the problem is serious enough.
')
In London, the five key threats to information security were considered:
- Mobile devices and blocking the sending of data on the results of the competition on smartphones in real time
- “Drive-by” downloads (downloads without an understanding of the consequences on the part of the user - applets, Active-X components, executable files, etc.).
- Phishing
- Substitution and falsification of search results
- Fraudulent ticketing sites.
In Rio, the situation was not very different; the problems were exactly the same - spam advertising fake ticketing sites, reports of allegedly won free tickets to sports events or other near-sports events, mailings with malicious attachments hiding under calendars and maps of Olympic events, phishing sites with Olympic news ( we have recorded and blocked several hundred such malicious domains), etc.
The task we faced was rather difficult - to provide in a short time a secure connection to the network and server infrastructure:
- 10,900 Olympic and 4,300 Paralympic athletes
- 5400 technicians serving the Games infrastructure
- 70,000 volunteers
- 25100 accredited media
- 37 sites, including sports facilities, the Olympic Village, the press center, etc.
- 9 million visitors.

In ensuring the security of 113472 LAN ports and 5159 Wi-Fi wireless access points, the following principles were laid down:
- security is a property of the network infrastructure, not an option
- traffic segmentation and separation
- network as an attack detection system sensor
- identity management
- secure real-time delivery of event results
- the ability to work with personal mobile devices.
In fact, they differed little from the similar infrastructure in London, where we also provided network security:
Considering the traditional nature of threats and defensive technologies, we used traditional ones. Of the 60 tons and 8115 units of equipment supplied for network security were responsible:
- Cisco ASA 5585-X Firewalls
- Cisco ASA 5515-X Next Generation Firewalls with FirePower Services
- Cisco Firepower Intrusion Prevention Systems
- Cisco ASA 5585-X Remote VPN Access Tools
- network access control, including guest access, using Cisco ISE and ACS
- Network Anomaly Monitoring and Neutralization with Cisco Stealthwatch
- monitoring and blocking DNS threats using Cisco OpenDNS Umbrella
- highly scalable NAT using CGN / VSM modules on ASR9000 routers
- DHCP and DNS cache with Cisco Prime Network Registrar
- Manage and monitor information security using Cisco Security Manager and Firesight Management Center.
The main tool for the segmentation of steel firewalls Cisco ASA 5585-X and ASA 5515-X, which provide the separation of traffic between different zones of the Olympic infrastructure. Cisco ASR9000 and Cisco ASR1000 routers helped them with this. At the level of virtualization, the Nexus 7000, Nexus 2000, MDS 9000 switches, as well as the UCS 5000 and Fabric Interconnect 6000 computing systems were responsible for the segmentation.

Since the Olympic Games are many different users with different tasks and access rights, we used a cluster of Cisco ISE devices that authenticated and authorized wired and wireless users to control and delimit them. So, for example, the portal of access for journalists of the press center looked like:

Considering the number of people who needed access to various services and services provided by the Olympic Organizing Committee, a self-service portal was raised on the Cisco ISE, which reduced the workload of the IT specialists of the Games. This self-service related to the registration of accounts:

registering mobile devices and recovering forgotten passwords:

With the help of Cisco ISE, journalists, athletes, volunteers, sponsors, and others could access all necessary services during the entire Olympic and Paralympic Games, as well as in the process of preparing for them. At the same time, access was not limited to any network segments (unless it was required by security policies) or device types — Cisco ISE allowed you to receive secure wireless access when sportsmen were brought from the Olympic Village to sports events (Wi-Fi was deployed on buses) while journalists are working at the press center and at sports events themselves from their personal devices. The total number of unique devices (without visitors) connected to the infrastructure of the Olympic Games and managed using Cisco ISE exceeded 235 thousand by the end of the games (27 thousand devices were connected to the infrastructure at its peak during the closing ceremony of the Olympic Games in Rio):

For detection of attacks on the perimeter and inside the network, the Cisco Firepower NGIPS intrusion prevention system, the Cisco OpenDNS DNS threat monitoring system, and the Netflow-based anomaly neutralization system - Cisco Stealthwatch were responsible. At the same time, the last of the mentioned solutions monitored the virtual infrastructure in the primary and backup data centers of the Olympic infrastructure. Each of the mentioned solutions used network traffic as a source of data, but from different points of view, which made it possible to ensure the principle of echeloned defense and to prevent the penetration of attacks inside the Olympic network infrastructure.
An interesting experience was gained when using Cisco OpenDNS Umbrella, the task of which was to monitor DNS requests from the Olympic infrastructure and cut off everything that was associated with malicious activity:
- malicious code trying to get inside the infrastructure
- botnets and phishing attacks that lead to data leaks
- new, fake and fraudulent sites
We managed to implement Cisco OpenDNS Umbrella throughout the infrastructure in just 2 (!) Hours 2 days before the opening ceremony of the Games and already during its operation this service passed 22 million DNS requests through itself daily and 23 thousand of them blocked due to harmfulness.
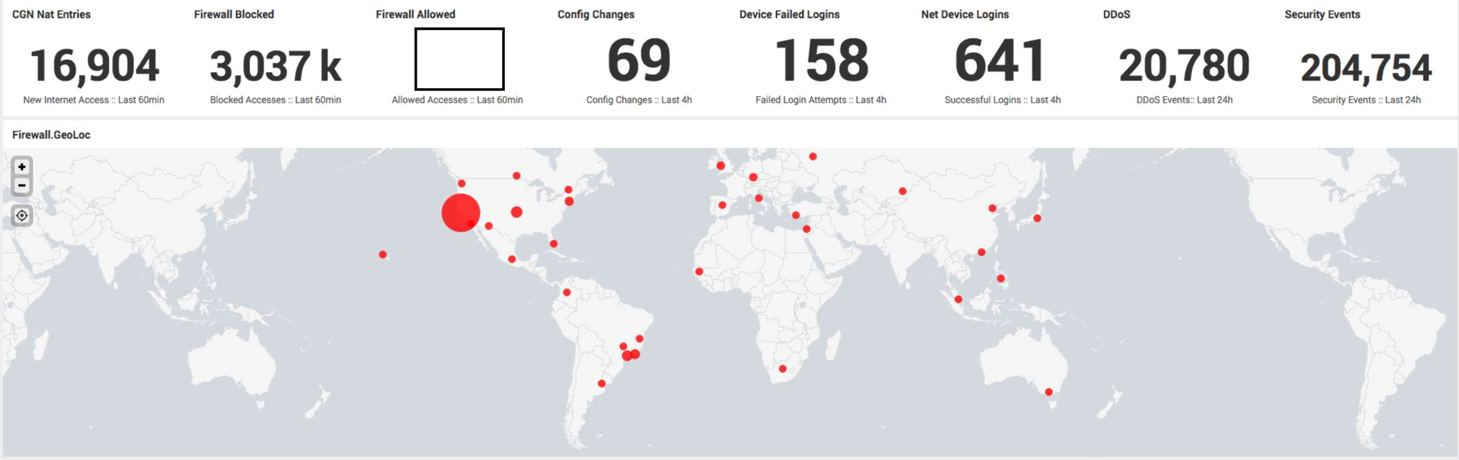
Of the other interesting numbers that we could share, I would call the following:
- In total, over 1 billion 300 million ITU events have been recorded. Cisco ASA
- 15 million TACACS + events
- IDS / IPS recorded over 7 million security events, of which more than a third of all attempts were related to Trojans, and 23% to DoS, of which 99% were related to the DNS protocol
- ISE conducted 13.5 million successful authentications and rejected 1.7 million failed

These were for us the Olympic Games in Brazil in 2016. We have strengthened our competence in the field of mass sports protection and are planning to re-apply our experience at the games in Japan in 2020. It is already known that Japan plans to spend more than $ 190 million on this area, considering it as one of its priorities. Well, Cisco is ready to help this International Olympic Committee and Atos, the official provider of IT services for the Olympic Games.
Source: https://habr.com/ru/post/312140/
All Articles