Intel Software Guard Extensions, a series of educational materials. Part 1, Intel SGX Basics
The first part of the Intel Software Guard Extensions (Intel SGX) study series is a brief description of this technology. For more information, see the documentation included with the Intel Software Guard Extensions SDK . For a list of all training materials in this series, see the article Introducing the Intel Software Guard Extensions series of training materials .

Software applications often have to work with confidential information, such as passwords, account numbers, financial data, encryption keys, medical data. Access to this data should only be available to authorized recipients. In Intel SGX terminology, such confidential information is called an “application secret.”
The task of the operating system is to apply the security policy in the computer so that these secrets are not inadvertently disclosed to other users or applications. The operating system will not allow the user to access another user's files (without explicit permission granted); will not allow one application to access the memory of another application; It will not allow the user to gain access to OS resources without the necessary rights, excluding strictly controlled resources. Applications often use additional security measures, such as data encryption, to prevent third parties from accessing data sent to the repository or via a network connection, even if attackers managed to gain access to the OS and equipment.
')
Despite all these protective measures, vulnerabilities still remain in most computer systems. A variety of mechanisms protect one application from another and protect the OS from a user who does not have permissions, but applications usually have little or no protection from processes running with a higher level of rights, including the OS itself. Malicious programs with administrative rights have unlimited access to all system resources and to all applications running on the system. Advanced malware can attack the security mechanisms of an application to extract encryption keys and even secret data directly from memory.
Intel has developed Intel SGX extensions for high-level secrecy protection and protection against such software attacks. Intel SGX is a set of CPU instructions that allow applications to create enclaves: protected areas in the application's address space, ensuring confidentiality and integrity even with the presence of elevated malware. The enclave code is supported by special instructions, it is compiled and loaded as a Windows * dynamic-link library (DLL) file.
Intel SGX Extensions reduce application vulnerability. In fig. Figure 1 shows the significant difference between potential attack areas with and without Intel SGX enclaves.
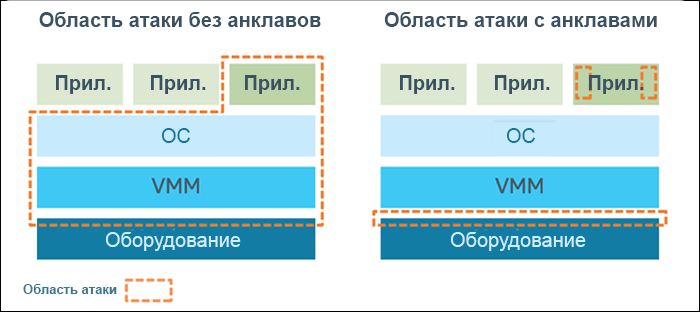
Figure 1. Attack areas with and without enclosures of Intel Software Guard Extensions
Intel SGX provides the following protection against attacks targeting hardware and software.
The size of the protected memory area is strictly limited and is set by the system BIOS. This is usually 64 MB or 128 MB. Some system manufacturers provide the ability to customize this value in the BIOS. Depending on the size of each enclave, from 5 to 20 enclaves can be simultaneously created in memory.

Figure 2. Data protection in Intel Software Guard Extensions enclaves in protected applications
To use the Intel SGX, the application must be divided into two components (see Figure 3).
The trusted component should be as small as possible, it should contain only those data that need the most reliable protection, and operations that work directly with this data. A large enclave with complex interfaces not only consumes more secure memory, but also increases vulnerability.
In enclaves, the interaction between trusted and untrusted components should also be minimized. Enclaves can go beyond the protected memory area and call functions in an untrusted component (using special instructions), but it is recommended to limit such dependencies in order to provide more reliable protection of the enclave against attacks.
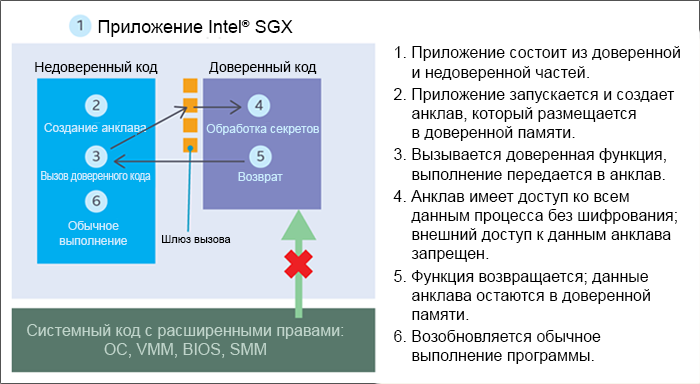
Figure 3. Running the Intel Software Guard Extensions application
In the SGX architecture, certification is a confirmation of the creation of a specific enclave on the platform. There are two certification mechanisms.
Local attestation is useful when applications have multiple enclaves that must work together to perform a task, or when two separate applications must exchange data between enclaves. Each enclave must check the other enclave to ensure its reliability. The enclaves then establish a secure session and use the ECDH key exchange to share the session key. This session key can be used to encrypt data that should be shared between both enclaves.
One enclave cannot access the protected memory space of another enclave, even if both enclaves are created by the same application, therefore it is necessary to remove references to their values from all pointers and copy them; the complete data set must be transferred from one enclave to another.
With remote attestation, the Intel SGX software extensions and platform hardware form a proposal that is transmitted to a third-party server to establish trust. The software includes an enclave of applications, as well as the Quoting Enclave (QE) and Provisioning Enclave (PvE) components provided by Intel. Certification hardware - CPU supporting Intel SGX. A summary of program information in conjunction with a unique asymmetric hardware key for the platform is used to form an offer that is transmitted to a remote server via a verified channel. If the remote server determines that the instance of the enclave was created correctly and started on a processor that supports Intel SGX, then the server establishes a trust relationship and transmits the secrets on the verified channel.
Data sealing is data encryption so that you can write them to untrusted memory or storage without disclosing the contents. This data can be later read by the enclave and printed out (decrypted). Encryption keys are created internally on demand and are not disclosed to the enclave.
There are two ways to seal the data.
When sealed with the identity of the enclave, the key is unique to the particular enclave that sealed the data. Any changes to the enclave that affect its signature will create a new key. When using this method, data sealed with one version of the enclave will not be available for another version of the same enclave. A side effect of this method is that the sealed data cannot be transferred to new versions of the application and its enclave. This approach is intended for sentences in which old sealed data should not be used by new versions of the application.
When sealing with a sealing certificate, several enclaves from the same center can seal and print each other's data. This allows you to transfer data from one version of the enclave to another, or to share data from several applications of the same provider.
If you want to deny access to old versions of software and the enclave to data sealed in new versions of the application, you can use the software version number when signing the enclave. Versions of the enclave that are older than the specified version number of the software will not be able to form a key, so they will not be able to print the data.
We looked at the three most important components of Intel SGX: enclaves, certification, and sealing. In this tutorial, we will focus on the implementation of the enclaves, as this is the basis of the Intel SGX. It is not possible to certify or seal without creating an enclave. In addition, it will limit the size of the training manual.
In the second part of a series of tutorials, Intel Software Guard Extensions Extensions: Part 2, building applications, we will look at Password Manager, which will be created with Intel SGX support. We describe the requirements for creating this application, the limitations and the user interface. Follow the news.
For a list of all training materials in this series, see the article Introducing the Intel Software Guard Extensions series of training materials .

Intel Software Guard Technology Extensions
Software applications often have to work with confidential information, such as passwords, account numbers, financial data, encryption keys, medical data. Access to this data should only be available to authorized recipients. In Intel SGX terminology, such confidential information is called an “application secret.”
The task of the operating system is to apply the security policy in the computer so that these secrets are not inadvertently disclosed to other users or applications. The operating system will not allow the user to access another user's files (without explicit permission granted); will not allow one application to access the memory of another application; It will not allow the user to gain access to OS resources without the necessary rights, excluding strictly controlled resources. Applications often use additional security measures, such as data encryption, to prevent third parties from accessing data sent to the repository or via a network connection, even if attackers managed to gain access to the OS and equipment.
')
Despite all these protective measures, vulnerabilities still remain in most computer systems. A variety of mechanisms protect one application from another and protect the OS from a user who does not have permissions, but applications usually have little or no protection from processes running with a higher level of rights, including the OS itself. Malicious programs with administrative rights have unlimited access to all system resources and to all applications running on the system. Advanced malware can attack the security mechanisms of an application to extract encryption keys and even secret data directly from memory.
Intel has developed Intel SGX extensions for high-level secrecy protection and protection against such software attacks. Intel SGX is a set of CPU instructions that allow applications to create enclaves: protected areas in the application's address space, ensuring confidentiality and integrity even with the presence of elevated malware. The enclave code is supported by special instructions, it is compiled and loaded as a Windows * dynamic-link library (DLL) file.
Intel SGX Extensions reduce application vulnerability. In fig. Figure 1 shows the significant difference between potential attack areas with and without Intel SGX enclaves.

Figure 1. Attack areas with and without enclosures of Intel Software Guard Extensions
How Intel Software Guard Extensions technology helps protect data
Intel SGX provides the following protection against attacks targeting hardware and software.
- Access to the memory of the enclave for reading and writing from outside the enclave is absent regardless of the current level of rights and the operating mode of the CPU.
- The working level enclaves are not available for debugging by both software and hardware debuggers. (You can create an enclave with a debug attribute, in which the Intel SGX debugger can view the contents of the enclave, just like a standard debugger. This is done to improve the convenience of the software development process.)
- It is impossible to enter the environment of the enclave using classical function calls, transitions, manipulations with registers or with a stack. The only way to invoke an enclave function is with a new instruction that performs several defensive checks.
- The enclave memory is protected using standard encryption algorithms with protection against reproduction. If you read the memory or connect the memory modules to another system, only encrypted data can be obtained (see Fig. 2).
- The memory encryption key changes randomly with each change of the power cycle (for example, when loading, when resuming work after sleep and hibernation). The key is stored inside the CPU and unavailable from the outside.
- The data is isolated in enclaves and is available only for the code of this enclave.
The size of the protected memory area is strictly limited and is set by the system BIOS. This is usually 64 MB or 128 MB. Some system manufacturers provide the ability to customize this value in the BIOS. Depending on the size of each enclave, from 5 to 20 enclaves can be simultaneously created in memory.

Figure 2. Data protection in Intel Software Guard Extensions enclaves in protected applications
How does it work
To use the Intel SGX, the application must be divided into two components (see Figure 3).
- Trusted component . This is an enclave. The code in the trusted component accesses the secrets of the application. A single application can have several trusted components / enclaves.
- Untrusted component . This is the rest of the application, any of its modules. It should be noted that in terms of the enclave, both the OS and the VMM are considered untrusted components.
The trusted component should be as small as possible, it should contain only those data that need the most reliable protection, and operations that work directly with this data. A large enclave with complex interfaces not only consumes more secure memory, but also increases vulnerability.
In enclaves, the interaction between trusted and untrusted components should also be minimized. Enclaves can go beyond the protected memory area and call functions in an untrusted component (using special instructions), but it is recommended to limit such dependencies in order to provide more reliable protection of the enclave against attacks.

Figure 3. Running the Intel Software Guard Extensions application
Certification
In the SGX architecture, certification is a confirmation of the creation of a specific enclave on the platform. There are two certification mechanisms.
- Local attestation occurs when two enclaves located on the same platform perform mutual authentication.
- Remote qualification occurs when the power of attorney of the enclave is verified by a remote provider.
Local certification
Local attestation is useful when applications have multiple enclaves that must work together to perform a task, or when two separate applications must exchange data between enclaves. Each enclave must check the other enclave to ensure its reliability. The enclaves then establish a secure session and use the ECDH key exchange to share the session key. This session key can be used to encrypt data that should be shared between both enclaves.
One enclave cannot access the protected memory space of another enclave, even if both enclaves are created by the same application, therefore it is necessary to remove references to their values from all pointers and copy them; the complete data set must be transferred from one enclave to another.
Remote Attestation
With remote attestation, the Intel SGX software extensions and platform hardware form a proposal that is transmitted to a third-party server to establish trust. The software includes an enclave of applications, as well as the Quoting Enclave (QE) and Provisioning Enclave (PvE) components provided by Intel. Certification hardware - CPU supporting Intel SGX. A summary of program information in conjunction with a unique asymmetric hardware key for the platform is used to form an offer that is transmitted to a remote server via a verified channel. If the remote server determines that the instance of the enclave was created correctly and started on a processor that supports Intel SGX, then the server establishes a trust relationship and transmits the secrets on the verified channel.
Data sealing
Data sealing is data encryption so that you can write them to untrusted memory or storage without disclosing the contents. This data can be later read by the enclave and printed out (decrypted). Encryption keys are created internally on demand and are not disclosed to the enclave.
There are two ways to seal the data.
- The certificate of the enclave . This method creates a key that is unique to this particular enclave.
- Sealing certificate . This method creates a key based on the enclave's sealing center identity. Multiple enclaves of the same signer witness may form the same key.
Sealing with ID of the enclave
When sealed with the identity of the enclave, the key is unique to the particular enclave that sealed the data. Any changes to the enclave that affect its signature will create a new key. When using this method, data sealed with one version of the enclave will not be available for another version of the same enclave. A side effect of this method is that the sealed data cannot be transferred to new versions of the application and its enclave. This approach is intended for sentences in which old sealed data should not be used by new versions of the application.
Sealing with sealing certificate
When sealing with a sealing certificate, several enclaves from the same center can seal and print each other's data. This allows you to transfer data from one version of the enclave to another, or to share data from several applications of the same provider.
If you want to deny access to old versions of software and the enclave to data sealed in new versions of the application, you can use the software version number when signing the enclave. Versions of the enclave that are older than the specified version number of the software will not be able to form a key, so they will not be able to print the data.
How we will use Intel Software Guard Extensions technology in the tutorial
We looked at the three most important components of Intel SGX: enclaves, certification, and sealing. In this tutorial, we will focus on the implementation of the enclaves, as this is the basis of the Intel SGX. It is not possible to certify or seal without creating an enclave. In addition, it will limit the size of the training manual.
In further releases
In the second part of a series of tutorials, Intel Software Guard Extensions Extensions: Part 2, building applications, we will look at Password Manager, which will be created with Intel SGX support. We describe the requirements for creating this application, the limitations and the user interface. Follow the news.
For a list of all training materials in this series, see the article Introducing the Intel Software Guard Extensions series of training materials .
Source: https://habr.com/ru/post/312002/
All Articles