“Admin: password” problem: standard passwords helped create a botnet from almost 400,000 IoT devices
At the beginning of October, the code for the components of the large IoT-botnet Mirai was published online. It was reported that the botnet mainly includes IoT devices, including video cameras and DVRs, and its total size at the peak reached almost 400,000 devices, with the help of which attackers can carry out extremely powerful DDoS attacks.

Screenshot of the Hackforums forum where the post was posted with links to the botnet source code
')
There are at least two major attacks using Mirai - first, the victim of the attackers was journalist Brian Krebs, whose site underwent DDoS with a capacity of about 620 Gbit / s, and then French hosting provider OVH experienced an even more powerful DDoS with a capacity of 1 TB / s.
At the same time, the logic of botnet propagation and device infection, analyzed by Positive Technologies experts, suggests that its creators were not digital cameras or IoT. Instead, they focused on searching for devices connected to the Internet with standard passwords set - as a result, ordinary home computers, servers and routers could easily get into the botnet.
This fact is confirmed by the presence of 61 standard passwords in the botnet code, with the help of which the creators managed to collect such an impressive network of infected devices. The logic of Mirai is simple - the system scans devices available on the Internet via telnet, and then uses the passwords from the list to access the device using brute force.
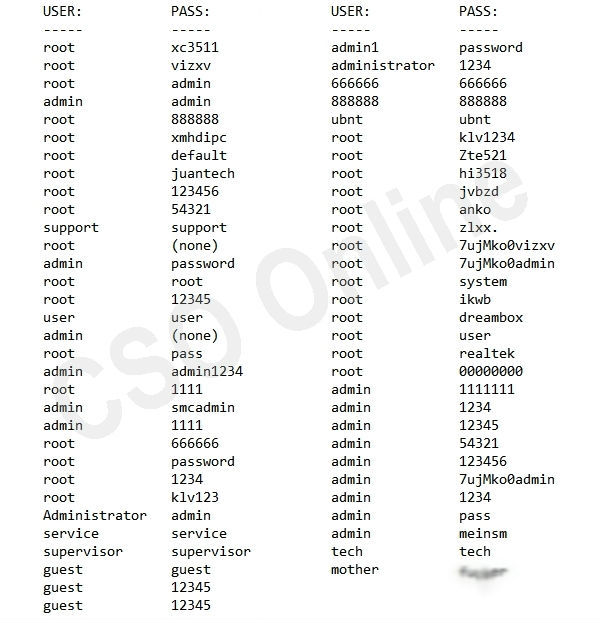
In the list of standard passwords used by Mirai there were many popular combinations like “admin: admin” or “admin: password”. As a rule, such passwords are used in devices and they are supposed to be changed by the user, but very often people forget or are too lazy to do so.
In addition, in some cases, devices are delivered with service accounts “wired” in the code, to which users do not have access and are not documented anywhere. Quite often, such cases are encountered with releases of products from large vendors - by mistake, company specialists may forget to remove from the released version of software the embedded accounts that were used for laying or development needs. An example of such an error is the vulnerability of the NX-OS operating system used in the Cisco Nexus 3000 Series and 3500 Platform switches. The researchers found in it a wired password for Telnet access with root user rights, which cannot be disabled.
At the same time, the sphere of the Internet of Things (IoT) is currently actively developing, and not all companies involved in the creation of such products have implemented approaches to development safety (SSDLC), as did, for example, telecommunications equipment vendors.
Thus, the specificity of the Mirai botnet is only that its creators were able to create malicious software for various architectures.
In our blog, we have already considered the problem of using insufficiently strong or standard passwords and published tips on protecting accounts from IT professionals and security experts. Below are recommendations on the organization of work with passwords from the senior analyst of Positive Technologies Dmitry Sklyarov.
 Dmitry Sklyarov, Senior Analyst, Positive Technologies
Dmitry Sklyarov, Senior Analyst, Positive Technologies
In order for a password to remain only your secret, it is usually enough to follow three simple rules:
In order not to memorize many long complex passwords, you can use any decent Password Keeper. It can also generate random passwords of a given strength.
To protect the database with passwords, you will have to remember one strong password. As an option - use a passphrase with a length of 20-30 characters.
If Password Keeper supports two-factor authentication with a smart card or USB Security Token, this increases the level of security and reduces the “window of opportunity” for the attacker.
Of course, the use of Password Keeper-programs can lead to the loss of secrecy of all stored passwords in case of compromise of the master password. This risk must be taken into account.
Now many programs for storing passwords have versions for mobile operating systems and offer synchronization through the cloud. This is certainly convenient, but convenience is almost against security ...
My choice is KeePass on trusted computers, the base is protected by a long passphrase. And no password stores in the clouds or on mobile devices.

Screenshot of the Hackforums forum where the post was posted with links to the botnet source code
')
There are at least two major attacks using Mirai - first, the victim of the attackers was journalist Brian Krebs, whose site underwent DDoS with a capacity of about 620 Gbit / s, and then French hosting provider OVH experienced an even more powerful DDoS with a capacity of 1 TB / s.
At the same time, the logic of botnet propagation and device infection, analyzed by Positive Technologies experts, suggests that its creators were not digital cameras or IoT. Instead, they focused on searching for devices connected to the Internet with standard passwords set - as a result, ordinary home computers, servers and routers could easily get into the botnet.
This fact is confirmed by the presence of 61 standard passwords in the botnet code, with the help of which the creators managed to collect such an impressive network of infected devices. The logic of Mirai is simple - the system scans devices available on the Internet via telnet, and then uses the passwords from the list to access the device using brute force.

In the list of standard passwords used by Mirai there were many popular combinations like “admin: admin” or “admin: password”. As a rule, such passwords are used in devices and they are supposed to be changed by the user, but very often people forget or are too lazy to do so.
In addition, in some cases, devices are delivered with service accounts “wired” in the code, to which users do not have access and are not documented anywhere. Quite often, such cases are encountered with releases of products from large vendors - by mistake, company specialists may forget to remove from the released version of software the embedded accounts that were used for laying or development needs. An example of such an error is the vulnerability of the NX-OS operating system used in the Cisco Nexus 3000 Series and 3500 Platform switches. The researchers found in it a wired password for Telnet access with root user rights, which cannot be disabled.
At the same time, the sphere of the Internet of Things (IoT) is currently actively developing, and not all companies involved in the creation of such products have implemented approaches to development safety (SSDLC), as did, for example, telecommunications equipment vendors.
Thus, the specificity of the Mirai botnet is only that its creators were able to create malicious software for various architectures.
In our blog, we have already considered the problem of using insufficiently strong or standard passwords and published tips on protecting accounts from IT professionals and security experts. Below are recommendations on the organization of work with passwords from the senior analyst of Positive Technologies Dmitry Sklyarov.
 Dmitry Sklyarov, Senior Analyst, Positive Technologies
Dmitry Sklyarov, Senior Analyst, Positive TechnologiesIn order for a password to remain only your secret, it is usually enough to follow three simple rules:
- Do not try to think of short, easy-to-remember passwords;
- do not use the same passwords on different resources;
- Do not enter passwords on computers that cannot be trusted.
In order not to memorize many long complex passwords, you can use any decent Password Keeper. It can also generate random passwords of a given strength.
To protect the database with passwords, you will have to remember one strong password. As an option - use a passphrase with a length of 20-30 characters.
If Password Keeper supports two-factor authentication with a smart card or USB Security Token, this increases the level of security and reduces the “window of opportunity” for the attacker.
Of course, the use of Password Keeper-programs can lead to the loss of secrecy of all stored passwords in case of compromise of the master password. This risk must be taken into account.
Now many programs for storing passwords have versions for mobile operating systems and offer synchronization through the cloud. This is certainly convenient, but convenience is almost against security ...
My choice is KeePass on trusted computers, the base is protected by a long passphrase. And no password stores in the clouds or on mobile devices.
Source: https://habr.com/ru/post/311754/
All Articles