Dive into the blockchain technology: EmerCoin secrets
Recently, we talked about the use of blockchain technology in real projects on the example of EmerCoin, one of the first partner providers of the blockchain service in the Azure Marketplace. Continuing the series of articles devoted to this topic, we will understand more deeply the EmerCoin technologies (EMC) and the main differences between the Emer kernel and other cryptocurrencies.
The Emer network, like other peer-to-peer networks, has unlimited scaling, and the more participants there are, the more efficient and stable it is. Therefore, based on it, you can make not only Enterprise solutions, but also solutions of a worldwide scale.

1. A series of materials on Emer technology:
1.1. The secrets of EmerCoin .
1.2. Decentralized uncensored domain name system .
1.3. Worldwide public key infrastructure .
1.4. Decentralized password-free security system .
2. Fast and secure transactions .
3. Ecosystem of digital dentistry .
4. Combating counterfeit goods .
5. Mutual insurance of animals .
6. What is ICO and how to conduct it .
7. Loading ...
')
First distinguish between the concepts:
Emer is a technology, network and infrastructure.
EmerCoin - credit units that circulate within the Emer network.
It is accepted that the word “EmerCoin” refers to both of these concepts, therefore we will also follow the generally accepted semantics, using the word “Emer”, only to emphasize that we are talking about technology, and not the accounting and accounting aspect. By the words "coins", "money" and the like, we will mean non-cash credit units circulating in a distributed network of cryptocurrencies.
Historically, the EmerCoin core was inherited from the Peercoin core, which in turn was inherited from Bitcon. Peercoin has added a key innovation to its project — the Proof-of-Stake mechanism for generating consensus, creating a hybrid consensus mechanism using two basic mechanisms — and Proof-of-work (POW) and Proof-of-Stake (POS). Consider these mechanisms and the consensus itself in more detail.
Consensus is an algorithm for public cryptocurrency, through which ordinary members of the decentralized network vote for the truth of a particular version of the blockchain under construction. Consensus arises as a result of the aggregated efforts of all the miners who, with their own resources, vote for one or another version of the blockchain branch, and for this they receive a miner's reward — freshly printed issue money and / or transactional payments. It can be said that miners sell an impersonal coin-network service to maintain trust in the blockchain (trust), and receive compensation for their services in the form of newly issued coins.
The first obvious idea is wallet. But, an attacker can create millions of wallets and these "dead souls" to vote for the version of the blockchain, which is beneficial to him.
The next idea is the IP address. It also does not work, since any provider can simulate a large network, and again create hordes of "dead souls." Voting requires a limited resource that cannot be replicated and falsified.
Satoshi Nakamoto in the Bitcon system proposed as such a Proof-of-Work - proof through computational power. Indeed, if you have a computer with computing power X, you can virtually divide it into N sub-computers, but their total computing power will remain X. That is, the voice weight of the owner of such a computer will not increase.
Then other concepts of consensus were proposed that were focused not on the use of a processor, but on a different computing resource — for example, the capacity of disk drives, Proof-of-Capacity. Such concepts are based on the limited physical resource - computing power or disk capacity. Naturally, in the process of developing the cryptocurrency ecosystem, this leads to an “arms race” when miners invest in the corresponding mining equipment until a parity is reached on equipment depreciation and mining income. After that, “Mine has become unprofitable crying, crypt - cheating”.
The breakthrough idea of Sunny King, the author of Peersoin, was the concept of Proof-of-Stake, in which coins controlled by the same system acted as a limited voting resource. This made it possible to get out of the trap: the “arms race of material resources”, replacing the material resource (processor, disks) with the intangible one — coins. This, in turn, has stopped the senseless consumption of material resources, irretrievably spent on mining (electricity, equipment).
Each consensus mechanism individually has its drawbacks. For example, the not very popular PoW cryptocurrency can be attacked by temporarily renting out enormous computing power (which was done several times), and POS cryptocurrencies are potentially vulnerable to other types of attacks, for example, attacks from deep. To protect against the latter, additional mechanisms are used, for example, dynamic checkpoints, and in general, the POS mechanism proved to be more stable than POW.
However, Peercoin's hybrid consensus mechanism is considered the safest, and it was used as the basis for its project. For a successful attack on Emer, an attacker must have both 51% of the entire computing power of the network and 51% of the entire money supply. This creates for the attacker two barriers of different nature, which protect the network from being compromised.
The choice was also influenced by the fact that Peercoin is based on the classic and mature Bitcoin code, which is not only deeply analyzed by many security experts, but also against which many unsuccessful crypto-attacks were conducted. Emer was guided by the fact that the Bitcoin code has good support, and it can continue to be used to develop its project.
In addition, Emer profess an industrial approach to their projects, which implies maximum adherence to existing standards and specifications. Since de facto, Bitcoin technologies and APIs are crypto industry standards, the company strives to maintain maximum compatibility with them, and accordingly, use Bitcoin as the core of the core.
In this section, you will learn which cryptocurrency components remained unchanged and which were changed. Differences will be considered with respect to Bitcoin, as the most illuminated project. Below you can see the EmerCoin components plan.
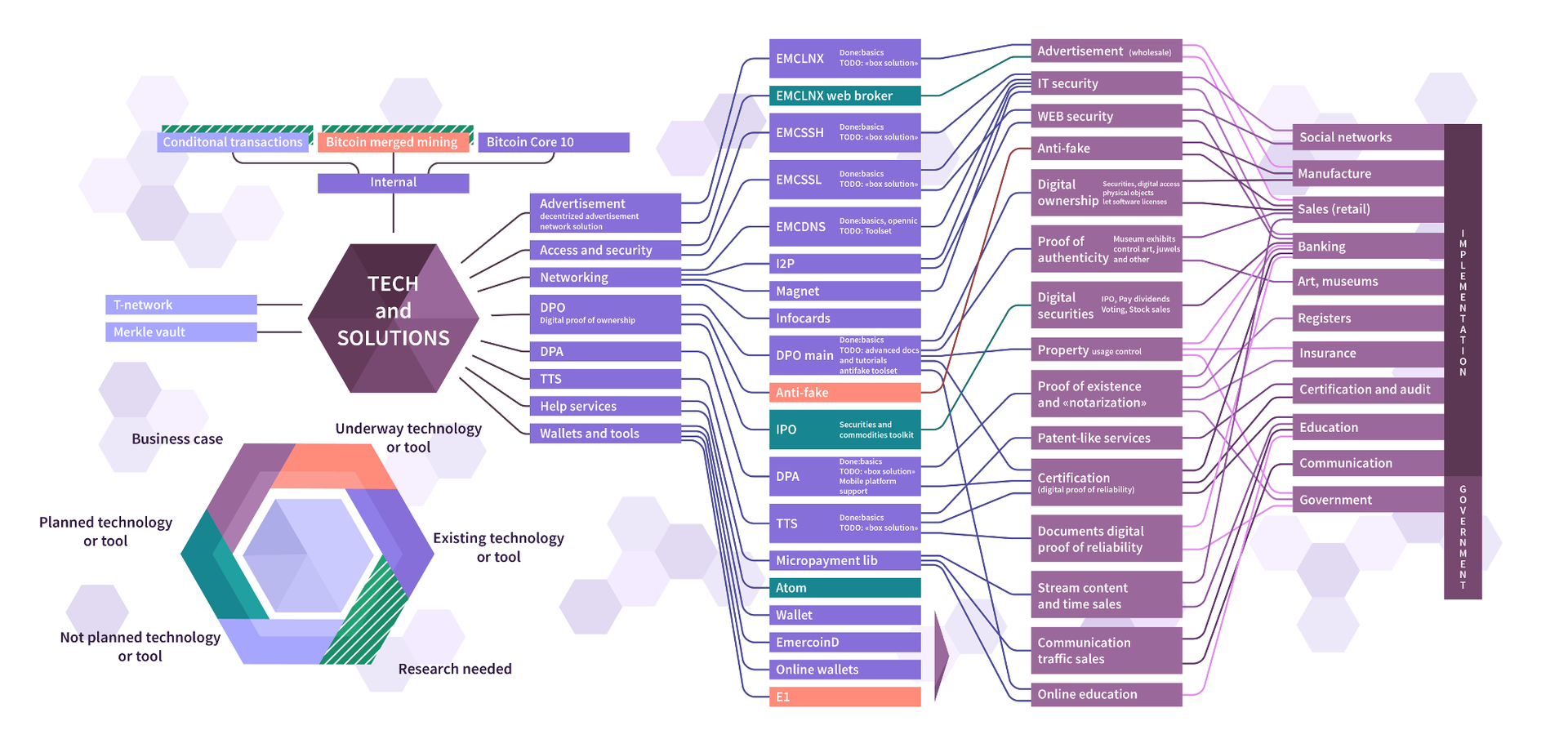
As mentioned above, EmerCoin has a hybrid consensus mechanism, which determined the starting point of the project. This hybrid mechanism was inherited by us from Peercoin with the only change - a big shift towards POS. In fact, Emer is a POS cryptocurrency, in which the POW mechanism is left for security reasons, and plays an important, but supporting role, and about 80% of the blocks are closed by the POS.
The block closing hash function is the same as that used in Bitcoin and Peercoin - sha256. The reason is that sha256 is a standard and continues to provide a sufficient level of security to maintain a stable network.
Also, due to the fact that sha256 mining has long been performed by specialized ASICs processors, you can be sure of two things:
The block closing time remains the same as in Bitcoin and Peercoin - 10 minutes. Satoshi chose a good option, and reducing the block time can lead to a large number of collisions with orphan blocks and loss of network stability. Consider this statement in more detail.
The probability of a collision is the network update time divided by the block closing time. The update time of the network depends on the topology and network load, and for the Bitcoin network it can now reach minutes. Accordingly, other cryptocurrencies (for example, Quark), which have reduced the closure time to sub-minute intervals, risk getting permanent forks as soon as the load on them rises to more or less significant values.
It can be argued that there is an excellent Ghost protocol used in Etherium, and he is not afraid of forks, since orphan blocks (they have them called uncles) do not get into the resulting blockchain, but vote for one version or another of the chain, therefore, there the block time may be around 20 seconds.
In turn, EmerCoin believes that this protocol has a number of vulnerabilities. For example, a network under the Ghost protocol may be subject to a network storm — an effect that occurs on broadcast Ethernet networks when a certain critical load is reached. Simply put, this happens because the network update time is proportional to the network load, that is, the traffic. When a critical load is reached (a large number of transactions per second), the update time will be comparable to the block generation time. At the same time, various miners will independently produce candidate blocks for inclusion in the blockchain. And here is a surprise - these blocks will contain the same transactions. And these big blocks will be sent out over the network again, which will create traffic multiplication, that is, will load the network again, which again will lead to delays to even more uncles. The network's behavior will become similar to the DNS / NTP Amplification attack, only the attacker and the victim are the same network nodes, and the achievement of the critical load, depending on the network topology, becomes the trigger.
And if we also take into account that only one of the candidate blocks will get to the blockchain, and the network was spending not only on the decision of this block, but also on its “brothers” who only voted, but did not enter the blockchain, the dramatic decrease becomes obvious the trust of the adopted blockchain as a result of such a storm, and the possibility of an attack with a power of less than 51%.
Therefore, Satoshi's approach is the most correct at the moment.
Unlike Bitcoin, where mining complexity is recalculated once for every 2016 blocks (about once every two weeks), complexity on the Emer network (like Peercoin) is recalculated after each block. This approach improves the stability of the network. Let's give an example.
For example, after the next recalculation of complexity, half of the miners stopped working in the Bitcon network. By the way, this is far from a hypothetical case - it is enough to pass the relevant laws in time in the states in whose territories there are large mining pools. As a result, the blocks will be closed twice less frequently, that is, once every 20 minutes. Also, transaction confirmation time and block size will double. And given that often now blocks reach their limit of 1 megabyte, there are direct chances that many transactions will simply not fall into the blocks and will be unconfirmed for many days. This will cause a panic, and an even greater number of transactions related to the desire to sell for what it is, which will only aggravate the situation. And the system only after a month will restore performance.
When recalculating the complexity after each block, such a problem cannot arise - the network immediately begins to adapt to the change in the total power of the miners. In addition, since EmerCoin is basically a POS cryptocurrency, in which mining and pools play a secondary role, even a full and one-time stop of all pools will lead to an increase in block time by 20%, which will be adjusted by the adaptation system during the day.
In EmerCoin, there is another mechanism to maintain a more or less stable mining power - this is a loop of negative feedback on the network hashrate (aggregated mining power). The bottom line is that the mine’s reward for a block is not fixed, as in Bitcoin, but inversely proportional to the 4th degree root of the network complexity.
As a result, if we assume that the cost of EmerCoin has increased in fiat terms, then a large number of agents will begin to mine it, which will lead to an increase in complexity and a decrease in the unit reward. As a result, the network is protected from strong inflation in fiat terms. And vice versa - in the case of a strong reduction in network complexity due to the loss of miners of interest in EmerCoin for any reason - the latter is trying to keep the miners, offering a great reward.
Theoretically, the most effective EmerCoin mining strategy is to get together, mine the minimum power and share the maximum income between the participants. But this will not work because of the selfishness of the miners who are in the situation described in the Prisoner's Dilemma .
Since EmerCoin is also a POS cryptocurrency, you can mine it not only with equipment, but with coins in your wallet. A POS-award of 6% per annum was selected in the project. In other words, if in a certain transaction, coins without movement have lain for more than a month, then they have a chance to close the unit, and bring the owner a reward of 6% per annum. If the coins were used elsewhere, then the term of their vylevyvaniya "burns", and begins to accumulate on the new from the new owner. That is, 6% is the upper limit of the POS reward, which is achievable only in the case of fixed money. At the present time, the practical value of money growth due to the POS-award is 4-5% per annum, and as the use of EmerCoin expands, it will decrease, reaching values adopted in stable fiat currencies, but not turning to zero.
In response to the objection: “You have inflation because of these 6%”, we note that EmerCoin demonstrates deflationary, that is, the value of the coin grows, and quite quickly. This is evident in the course of the coin, which has grown roughly fourfold since the beginning of the year. This discrepancy with the naive model is explained by the fact that the value of the coin reflects the value of the corresponding economy, and as the economy grows, the coin grows as well, and the pumping of the money supply due to POS is negligible compared to other factors.
From the above, we can conclude that the money supply EmerCoin will grow indefinitely. And this is in the first approximation true. Indeed, participants maintaining a consensus sell their services to the network, and for this they receive freshly printed coins. However, in the EmerCoin system, there is a mechanism for the destruction of coins, which is the opposite of emission. The destruction of coins occurs when using the blockchain services - sending coins or buying records in NVS. That is, unlike the Bitcoin network, where emissions are limited, but there is no destruction mechanism, there is an unrestricted emission on the EmerCoin network and a process designed to counteract it. Network members receive an award, and services that buy from a network pay for them.
Approximate estimates say that given the known factors, the amount of 1 billion EMC will be reached in about 80 years.
The first unique innovation EmerCoin is using the protocol rfc5389 , STUN to obtain an external IP-address. The wallet program behind NAT needs to know the external IP. Bitcoin has previously received it (and other cryptocurrencies continue to receive) with a request to the centralized server
Another unique innovation, unique to Emer, is the transaction optimizer.
In cryptocurrencies, the blockchain of which contains transactions, when creating a next transaction, it is necessary to select a subset of inputs that this transaction will spend. In Bitcoin and other cryptocurrencies, a stochastic algorithm is used, which makes 1000 random samples and selects a subset with an amount as close as possible to the target. At the same time, even if the wallet contains a subset of transactions that allow you to collect the amount "for calculation", the standard algorithm almost always misses it, and in the new transaction will create an output for payment and delivery to yourself. This leads to the excessive size of the created transaction, and to the appearance of a future transaction, which will spend the change.
In addition, this algorithm creates the problem of “golden sand”, when a lot of transaction-transfers for small sums accumulate in the wallet.
In Emer, a dynamic programming approach was used to select a subset of transactions, and the algorithm is guaranteed to find such a subset to provide an amount without change, if such is possible. As a result, it is estimated that the average transaction size decreased by 5%, which consequently reduced the growth rate of the blockchain size. Details on this - in the article .
Some exotic POS-specific attacks can be applied to POS cryptocurrencies. The main one is the "attack from the depths." Its essence is that if someone gets control over wallets containing already spent coins, he can modelly roll back the time to the moment when these wallets contain coins, and having thus obtained 51% of coins, build an alternative blockchain chain longer than the main , and thus change the contents of the blockchain retroactively.
To prevent this attack, checkpoints are used, deeper than which the system does not revise the blockchain structure. Bitcoin uses only hard checkpoints embedded in the wallet code, which are updated only with the release of a new wallet release. Peercoin and Emer also have dynamic checkpoints when developers send information about control points on the network, which does not require updating the code on the client side and keeps the structure of control points up to date.
In the current Peercoin and the old version of Emer, only one node could send checkpoints. When sending them from several nodes, the probability of a conflict in the network appeared. Accordingly, the failure of this node led to the fact that information about dynamic checkpoints was no longer updated.
Emer, starting with version 0.5.0, contains a mechanism for distributed decentralized checkpoints, in which checkpoints are sent by independent nodes, and there is an algorithm for avoiding "double dispatch". This increases the reliability of the network, as the control points will continue to be updated, even if some nodes fail.
No, and not foreseen. Emer is categorically against this for security reasons and consider unauthorized downloading of Turing-compatible code to the users' computers and its enforcement on an external event as critically dangerous.
Here the most interesting is the microkernel approach, where all the external and non-authorized by developers code is executed outside the Emer kernel.
The main innovation with external utilitarian value is the NVS subsystem - Name-Value Storage. The development of this subsystem was inspired by the Namecoin distributed DNS from cryptocurrency.
And if such a structure Namecoin was strictly focused on distributed DNS, then Emer NVS is a trusted general purpose distributed storage with decentralized management. More information about this subsystem can be found on the website .
In short, the subsystem is a storage of binary data (up to 20kb) of any kind. Data is associated with a search key up to 512 bytes in length. The key is unique within the entire EmerCoin network. That is, it is impossible to create a duplicate of an existing key. The record is associated with a billing address owned by the owner of a certain wallet.
The record can be managed only by the owner of the payment address, and no one else. Management involves the creation of a new record in return for the old one, or the transfer of ownership rights to another billing address. But at the same time the old record does not disappear, and also remains accessible from the blockchain. Thus, the full history of modifications and changes of ownership of a particular record becomes available.
Technically, such an entry in the blockchain represents the exit of a transaction at 0.01EMC to the billing address of the recording host. This output inside the script-contract itself contains the contents of NVS. Only the owner of the record can spend this exit, since only in his wallet there is a corresponding private key for signing the exit. When this output is spent, you can modify the record by replacing value or other items in it, including the billing address. In the latter case, the record will be transferred to the wallet containing the destination address.
You can interact with the NVS subsystem either through the JSON API in a way similar to interacting with a Bitcoin wallet, or through a wallet GUI, in a special tab.
This subsystem became the basis for the creation of Emer services, which will be discussed in the following posts.

Oleg Hovayko is a leading cryptocurrency developer EmerCoin, an expert in the field of cryptography and computer security. Since 1994 he has been working in IT. Currently, he is also the vice-president of the American investment bank, which makes operations with securities - Jefferies & Company. Which is considered one of the largest independent US banks.
The Emer network, like other peer-to-peer networks, has unlimited scaling, and the more participants there are, the more efficient and stable it is. Therefore, based on it, you can make not only Enterprise solutions, but also solutions of a worldwide scale.

The series of articles "Immersion in technology blockchain"
1. A series of materials on Emer technology:
1.1. The secrets of EmerCoin .
1.2. Decentralized uncensored domain name system .
1.3. Worldwide public key infrastructure .
1.4. Decentralized password-free security system .
2. Fast and secure transactions .
3. Ecosystem of digital dentistry .
4. Combating counterfeit goods .
5. Mutual insurance of animals .
6. What is ICO and how to conduct it .
7. Loading ...
')
Introduction
First distinguish between the concepts:
Emer is a technology, network and infrastructure.
EmerCoin - credit units that circulate within the Emer network.
It is accepted that the word “EmerCoin” refers to both of these concepts, therefore we will also follow the generally accepted semantics, using the word “Emer”, only to emphasize that we are talking about technology, and not the accounting and accounting aspect. By the words "coins", "money" and the like, we will mean non-cash credit units circulating in a distributed network of cryptocurrencies.
EmerCoin history
Historically, the EmerCoin core was inherited from the Peercoin core, which in turn was inherited from Bitcon. Peercoin has added a key innovation to its project — the Proof-of-Stake mechanism for generating consensus, creating a hybrid consensus mechanism using two basic mechanisms — and Proof-of-work (POW) and Proof-of-Stake (POS). Consider these mechanisms and the consensus itself in more detail.
Consensus is an algorithm for public cryptocurrency, through which ordinary members of the decentralized network vote for the truth of a particular version of the blockchain under construction. Consensus arises as a result of the aggregated efforts of all the miners who, with their own resources, vote for one or another version of the blockchain branch, and for this they receive a miner's reward — freshly printed issue money and / or transactional payments. It can be said that miners sell an impersonal coin-network service to maintain trust in the blockchain (trust), and receive compensation for their services in the form of newly issued coins.
What is considered a voice on such a distributed network?
The first obvious idea is wallet. But, an attacker can create millions of wallets and these "dead souls" to vote for the version of the blockchain, which is beneficial to him.
The next idea is the IP address. It also does not work, since any provider can simulate a large network, and again create hordes of "dead souls." Voting requires a limited resource that cannot be replicated and falsified.
Satoshi Nakamoto in the Bitcon system proposed as such a Proof-of-Work - proof through computational power. Indeed, if you have a computer with computing power X, you can virtually divide it into N sub-computers, but their total computing power will remain X. That is, the voice weight of the owner of such a computer will not increase.
Then other concepts of consensus were proposed that were focused not on the use of a processor, but on a different computing resource — for example, the capacity of disk drives, Proof-of-Capacity. Such concepts are based on the limited physical resource - computing power or disk capacity. Naturally, in the process of developing the cryptocurrency ecosystem, this leads to an “arms race” when miners invest in the corresponding mining equipment until a parity is reached on equipment depreciation and mining income. After that, “Mine has become unprofitable crying, crypt - cheating”.
The breakthrough idea of Sunny King, the author of Peersoin, was the concept of Proof-of-Stake, in which coins controlled by the same system acted as a limited voting resource. This made it possible to get out of the trap: the “arms race of material resources”, replacing the material resource (processor, disks) with the intangible one — coins. This, in turn, has stopped the senseless consumption of material resources, irretrievably spent on mining (electricity, equipment).
Network security
Each consensus mechanism individually has its drawbacks. For example, the not very popular PoW cryptocurrency can be attacked by temporarily renting out enormous computing power (which was done several times), and POS cryptocurrencies are potentially vulnerable to other types of attacks, for example, attacks from deep. To protect against the latter, additional mechanisms are used, for example, dynamic checkpoints, and in general, the POS mechanism proved to be more stable than POW.
However, Peercoin's hybrid consensus mechanism is considered the safest, and it was used as the basis for its project. For a successful attack on Emer, an attacker must have both 51% of the entire computing power of the network and 51% of the entire money supply. This creates for the attacker two barriers of different nature, which protect the network from being compromised.
The choice was also influenced by the fact that Peercoin is based on the classic and mature Bitcoin code, which is not only deeply analyzed by many security experts, but also against which many unsuccessful crypto-attacks were conducted. Emer was guided by the fact that the Bitcoin code has good support, and it can continue to be used to develop its project.
In addition, Emer profess an industrial approach to their projects, which implies maximum adherence to existing standards and specifications. Since de facto, Bitcoin technologies and APIs are crypto industry standards, the company strives to maintain maximum compatibility with them, and accordingly, use Bitcoin as the core of the core.
EmerCoin: Similarities and Differences
In this section, you will learn which cryptocurrency components remained unchanged and which were changed. Differences will be considered with respect to Bitcoin, as the most illuminated project. Below you can see the EmerCoin components plan.

POW + POS vs POW
As mentioned above, EmerCoin has a hybrid consensus mechanism, which determined the starting point of the project. This hybrid mechanism was inherited by us from Peercoin with the only change - a big shift towards POS. In fact, Emer is a POS cryptocurrency, in which the POW mechanism is left for security reasons, and plays an important, but supporting role, and about 80% of the blocks are closed by the POS.
Sha256
The block closing hash function is the same as that used in Bitcoin and Peercoin - sha256. The reason is that sha256 is a standard and continues to provide a sufficient level of security to maintain a stable network.
Also, due to the fact that sha256 mining has long been performed by specialized ASICs processors, you can be sure of two things:
- There will not be a revolution of complexity caused by the appearance of specialized equipment for another algorithm, which can lead to network shaking and consolidation of mining power in the hands of the owners of new equipment.
- EmerCoin against mining on universal computers, as with this approach the uncomplicated can suffer. As you know, before the appearance of the ASICs, there were a number of viruses that used the computing power of infected computers to mine bitcoins. The emergence of ASICs made such viruses unprofitable. However, the danger persists for other cryptocurrencies that are shared on universal computers.
10 minutes
The block closing time remains the same as in Bitcoin and Peercoin - 10 minutes. Satoshi chose a good option, and reducing the block time can lead to a large number of collisions with orphan blocks and loss of network stability. Consider this statement in more detail.
The probability of a collision is the network update time divided by the block closing time. The update time of the network depends on the topology and network load, and for the Bitcoin network it can now reach minutes. Accordingly, other cryptocurrencies (for example, Quark), which have reduced the closure time to sub-minute intervals, risk getting permanent forks as soon as the load on them rises to more or less significant values.
It can be argued that there is an excellent Ghost protocol used in Etherium, and he is not afraid of forks, since orphan blocks (they have them called uncles) do not get into the resulting blockchain, but vote for one version or another of the chain, therefore, there the block time may be around 20 seconds.
In turn, EmerCoin believes that this protocol has a number of vulnerabilities. For example, a network under the Ghost protocol may be subject to a network storm — an effect that occurs on broadcast Ethernet networks when a certain critical load is reached. Simply put, this happens because the network update time is proportional to the network load, that is, the traffic. When a critical load is reached (a large number of transactions per second), the update time will be comparable to the block generation time. At the same time, various miners will independently produce candidate blocks for inclusion in the blockchain. And here is a surprise - these blocks will contain the same transactions. And these big blocks will be sent out over the network again, which will create traffic multiplication, that is, will load the network again, which again will lead to delays to even more uncles. The network's behavior will become similar to the DNS / NTP Amplification attack, only the attacker and the victim are the same network nodes, and the achievement of the critical load, depending on the network topology, becomes the trigger.
And if we also take into account that only one of the candidate blocks will get to the blockchain, and the network was spending not only on the decision of this block, but also on its “brothers” who only voted, but did not enter the blockchain, the dramatic decrease becomes obvious the trust of the adopted blockchain as a result of such a storm, and the possibility of an attack with a power of less than 51%.
Therefore, Satoshi's approach is the most correct at the moment.
Recalculation of complexity after each block
Unlike Bitcoin, where mining complexity is recalculated once for every 2016 blocks (about once every two weeks), complexity on the Emer network (like Peercoin) is recalculated after each block. This approach improves the stability of the network. Let's give an example.
For example, after the next recalculation of complexity, half of the miners stopped working in the Bitcon network. By the way, this is far from a hypothetical case - it is enough to pass the relevant laws in time in the states in whose territories there are large mining pools. As a result, the blocks will be closed twice less frequently, that is, once every 20 minutes. Also, transaction confirmation time and block size will double. And given that often now blocks reach their limit of 1 megabyte, there are direct chances that many transactions will simply not fall into the blocks and will be unconfirmed for many days. This will cause a panic, and an even greater number of transactions related to the desire to sell for what it is, which will only aggravate the situation. And the system only after a month will restore performance.
When recalculating the complexity after each block, such a problem cannot arise - the network immediately begins to adapt to the change in the total power of the miners. In addition, since EmerCoin is basically a POS cryptocurrency, in which mining and pools play a secondary role, even a full and one-time stop of all pools will lead to an increase in block time by 20%, which will be adjusted by the adaptation system during the day.
Recalculation of awards for POW-block
In EmerCoin, there is another mechanism to maintain a more or less stable mining power - this is a loop of negative feedback on the network hashrate (aggregated mining power). The bottom line is that the mine’s reward for a block is not fixed, as in Bitcoin, but inversely proportional to the 4th degree root of the network complexity.
As a result, if we assume that the cost of EmerCoin has increased in fiat terms, then a large number of agents will begin to mine it, which will lead to an increase in complexity and a decrease in the unit reward. As a result, the network is protected from strong inflation in fiat terms. And vice versa - in the case of a strong reduction in network complexity due to the loss of miners of interest in EmerCoin for any reason - the latter is trying to keep the miners, offering a great reward.
Theoretically, the most effective EmerCoin mining strategy is to get together, mine the minimum power and share the maximum income between the participants. But this will not work because of the selfishness of the miners who are in the situation described in the Prisoner's Dilemma .
POS 6% APY
Since EmerCoin is also a POS cryptocurrency, you can mine it not only with equipment, but with coins in your wallet. A POS-award of 6% per annum was selected in the project. In other words, if in a certain transaction, coins without movement have lain for more than a month, then they have a chance to close the unit, and bring the owner a reward of 6% per annum. If the coins were used elsewhere, then the term of their vylevyvaniya "burns", and begins to accumulate on the new from the new owner. That is, 6% is the upper limit of the POS reward, which is achievable only in the case of fixed money. At the present time, the practical value of money growth due to the POS-award is 4-5% per annum, and as the use of EmerCoin expands, it will decrease, reaching values adopted in stable fiat currencies, but not turning to zero.
In response to the objection: “You have inflation because of these 6%”, we note that EmerCoin demonstrates deflationary, that is, the value of the coin grows, and quite quickly. This is evident in the course of the coin, which has grown roughly fourfold since the beginning of the year. This discrepancy with the naive model is explained by the fact that the value of the coin reflects the value of the corresponding economy, and as the economy grows, the coin grows as well, and the pumping of the money supply due to POS is negligible compared to other factors.
Emission and burning
From the above, we can conclude that the money supply EmerCoin will grow indefinitely. And this is in the first approximation true. Indeed, participants maintaining a consensus sell their services to the network, and for this they receive freshly printed coins. However, in the EmerCoin system, there is a mechanism for the destruction of coins, which is the opposite of emission. The destruction of coins occurs when using the blockchain services - sending coins or buying records in NVS. That is, unlike the Bitcoin network, where emissions are limited, but there is no destruction mechanism, there is an unrestricted emission on the EmerCoin network and a process designed to counteract it. Network members receive an award, and services that buy from a network pay for them.
Approximate estimates say that given the known factors, the amount of 1 billion EMC will be reached in about 80 years.
STUN rfc5389
The first unique innovation EmerCoin is using the protocol rfc5389 , STUN to obtain an external IP-address. The wallet program behind NAT needs to know the external IP. Bitcoin has previously received it (and other cryptocurrencies continue to receive) with a request to the centralized server
http://checkip.dyndns.org , but now the code for this request is removed from Bitcoin, and only UPNP or manual configuration is used. This approach was not suitable for several reasons (for example, UPNP does not work correctly for multi-layer NAT), so we decided to get rid of the dependence on the centralized server and apply STUN, which is used for this purpose in IP-telephony, and is an industry standard . Currently, the Emer group owns the most comprehensive list of public STUN servers on the network, and these servers are used by the STUN subsystem Emer to determine the external IP.Transaction Optimizer
Another unique innovation, unique to Emer, is the transaction optimizer.
In cryptocurrencies, the blockchain of which contains transactions, when creating a next transaction, it is necessary to select a subset of inputs that this transaction will spend. In Bitcoin and other cryptocurrencies, a stochastic algorithm is used, which makes 1000 random samples and selects a subset with an amount as close as possible to the target. At the same time, even if the wallet contains a subset of transactions that allow you to collect the amount "for calculation", the standard algorithm almost always misses it, and in the new transaction will create an output for payment and delivery to yourself. This leads to the excessive size of the created transaction, and to the appearance of a future transaction, which will spend the change.
In addition, this algorithm creates the problem of “golden sand”, when a lot of transaction-transfers for small sums accumulate in the wallet.
In Emer, a dynamic programming approach was used to select a subset of transactions, and the algorithm is guaranteed to find such a subset to provide an amount without change, if such is possible. As a result, it is estimated that the average transaction size decreased by 5%, which consequently reduced the growth rate of the blockchain size. Details on this - in the article .
Distributed dynamic control points
Some exotic POS-specific attacks can be applied to POS cryptocurrencies. The main one is the "attack from the depths." Its essence is that if someone gets control over wallets containing already spent coins, he can modelly roll back the time to the moment when these wallets contain coins, and having thus obtained 51% of coins, build an alternative blockchain chain longer than the main , and thus change the contents of the blockchain retroactively.
To prevent this attack, checkpoints are used, deeper than which the system does not revise the blockchain structure. Bitcoin uses only hard checkpoints embedded in the wallet code, which are updated only with the release of a new wallet release. Peercoin and Emer also have dynamic checkpoints when developers send information about control points on the network, which does not require updating the code on the client side and keeps the structure of control points up to date.
In the current Peercoin and the old version of Emer, only one node could send checkpoints. When sending them from several nodes, the probability of a conflict in the network appeared. Accordingly, the failure of this node led to the fact that information about dynamic checkpoints was no longer updated.
Emer, starting with version 0.5.0, contains a mechanism for distributed decentralized checkpoints, in which checkpoints are sent by independent nodes, and there is an algorithm for avoiding "double dispatch". This increases the reliability of the network, as the control points will continue to be updated, even if some nodes fail.
Ethereum Smart Contracts
No, and not foreseen. Emer is categorically against this for security reasons and consider unauthorized downloading of Turing-compatible code to the users' computers and its enforcement on an external event as critically dangerous.
Here the most interesting is the microkernel approach, where all the external and non-authorized by developers code is executed outside the Emer kernel.
Name-Value Storage (NVS)
The main innovation with external utilitarian value is the NVS subsystem - Name-Value Storage. The development of this subsystem was inspired by the Namecoin distributed DNS from cryptocurrency.
And if such a structure Namecoin was strictly focused on distributed DNS, then Emer NVS is a trusted general purpose distributed storage with decentralized management. More information about this subsystem can be found on the website .
In short, the subsystem is a storage of binary data (up to 20kb) of any kind. Data is associated with a search key up to 512 bytes in length. The key is unique within the entire EmerCoin network. That is, it is impossible to create a duplicate of an existing key. The record is associated with a billing address owned by the owner of a certain wallet.
The record can be managed only by the owner of the payment address, and no one else. Management involves the creation of a new record in return for the old one, or the transfer of ownership rights to another billing address. But at the same time the old record does not disappear, and also remains accessible from the blockchain. Thus, the full history of modifications and changes of ownership of a particular record becomes available.
Technically, such an entry in the blockchain represents the exit of a transaction at 0.01EMC to the billing address of the recording host. This output inside the script-contract itself contains the contents of NVS. Only the owner of the record can spend this exit, since only in his wallet there is a corresponding private key for signing the exit. When this output is spent, you can modify the record by replacing value or other items in it, including the billing address. In the latter case, the record will be transferred to the wallet containing the destination address.
You can interact with the NVS subsystem either through the JSON API in a way similar to interacting with a Bitcoin wallet, or through a wallet GUI, in a special tab.
This subsystem became the basis for the creation of Emer services, which will be discussed in the following posts.
about the author

Oleg Hovayko is a leading cryptocurrency developer EmerCoin, an expert in the field of cryptography and computer security. Since 1994 he has been working in IT. Currently, he is also the vice-president of the American investment bank, which makes operations with securities - Jefferies & Company. Which is considered one of the largest independent US banks.
Source: https://habr.com/ru/post/311690/
All Articles