Zerodium raises reward for jailbreak for iOS
While Apple was arranging a private event for a narrow circle of security re-writers of its products (recently announced by the bug bounty program), Zerodium announced an increase in the rewards it pays for the discovered vulnerabilities. In particular, the reward for a remote jailbreak device running iOS 10 has grown to $ 1.5M. Recall that iOS 10 on iPhone 7 has already been compromised by a 19-year-old security reader, also invited to an Apple closed event.
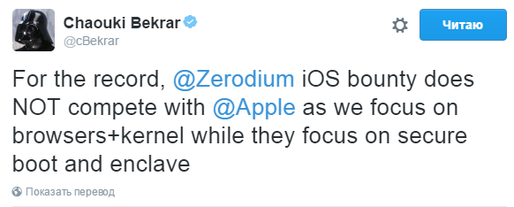
We have repeatedly mentioned in our posts the corporate blog of the founder of the company Zerodium Chaouki Bekrar, who is known for his scandalous statements about Apple and Google in connection with insufficient payments to security researchers. In one of his tweets, Bekrar confirmed that Zerodium was not related to Trident exploits, which we wrote about earlier. A bunch of these exploits allowed for a remote jailbreak of iOS 9 and was estimated by Zerodium at $ 1M.
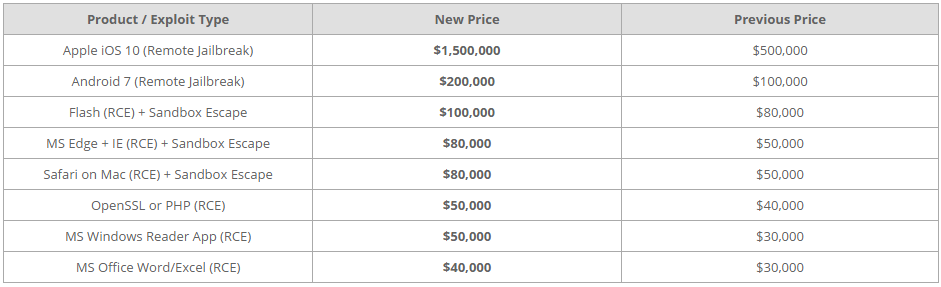
Fig. New pricing Zerodium.
')
The notion of a remote jailbreak iOS, mentioned by Zerodium, is the most technically complex method of compromising this mobile OS. It implies remote execution of code in iOS with maximum root privileges, which, in some cases, can lead to a complete reflashing of the device to return it to its original state. This process should involve several vulnerabilities in various components of iOS: the WebKit web browser engine and the kernel itself. A classic case of a remote jailbreak is the newly discovered Trident exploit bundle. It used three types of vulnerabilities: the RCE vulnerability in the WebKit engine, the SFB vulnerability in the kernel to bypass the KASLR, and the LPE vulnerability in the kernel to raise its rights to root level.
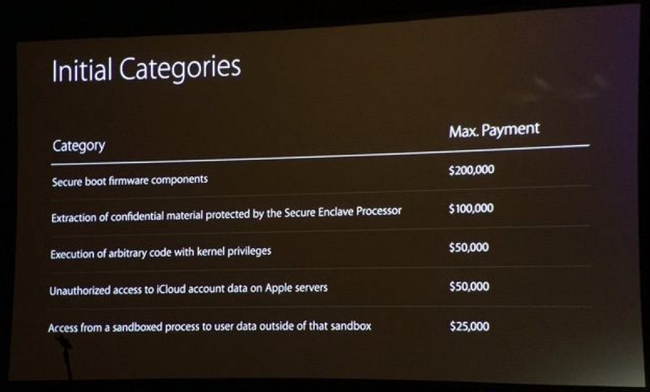
Fig. Apple's bug bounty pricing.
As you can see, the main technical difference between the bug bounty programs of Apple and Zerodium is that the latter is interested in exploits for vulnerabilities, which have a more practical purpose. That is, we are talking about remote code execution, which may be interesting to Zerodium customers with whom it works. You do not need to be a great expert in noticing what is really the case with Zerodium, RCE + LPE exploits (i.e., bypassing the sandbox) are used in cyber attacks, including special services.
Unlike Apple, Google, Microsoft, and other vendors with bug bounty programs, Zerodium does not burden itself with ethical issues. The firm’s clients can also be intelligence services using advanced exploits for cyber attacks in the interests of their state. Such exploits have already been used more than once by such elite state-sponsored groups as the Equation Group (FiveEyes, Tilded Team) and Animal Farm (Snowglobe).
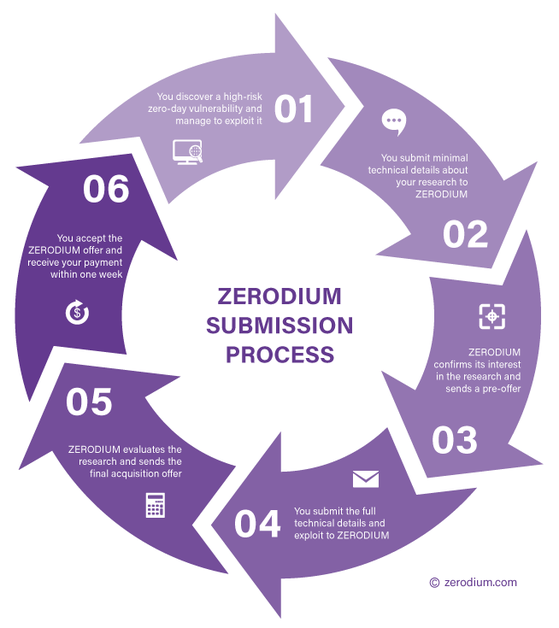
Fig. The stages of the submission of an exploit and the decision on the amount of payment in the case of Zerodium.
Bekrar also pointed out on his twitter that bug vendors are characterized by a “protracted” decision-making process about the posted demonstration of exploitation of a vulnerability. In contrast, Zerodium offers only a seven-day period from the submission of the exploit to the payment of remuneration.
The head of Zerodium itself had previously been involved in the well-known security firm VUPEN, which was developing its own exploits and searching for vulnerabilities to sell this information to its customers. After the adoption of the Wassenaar Agreement and the imposition of restrictions on trade in exploits, as well as “dual-use” technologies to other countries, it was announced that VUPEN would cease operations. After that, Bekrar founded Zerodium (USA), which also recruits security resellers in R & D.
Note that suspicions about the sale of exploits to special services that may be involved in state-sponsored cyber attacks against Zerodium or VUPEN are not fictitious . In particular, among the clients of VUPEN was the NSA (NSA), which is related to the grouping of the Equation Group. VUPEN collaborated with the Hacking Team, a large-scale compromise which occurred last year. Hacking Team worked with the state. agencies and private companies around the world, selling them information about exploits.

We have repeatedly mentioned in our posts the corporate blog of the founder of the company Zerodium Chaouki Bekrar, who is known for his scandalous statements about Apple and Google in connection with insufficient payments to security researchers. In one of his tweets, Bekrar confirmed that Zerodium was not related to Trident exploits, which we wrote about earlier. A bunch of these exploits allowed for a remote jailbreak of iOS 9 and was estimated by Zerodium at $ 1M.

Fig. New pricing Zerodium.
')
The notion of a remote jailbreak iOS, mentioned by Zerodium, is the most technically complex method of compromising this mobile OS. It implies remote execution of code in iOS with maximum root privileges, which, in some cases, can lead to a complete reflashing of the device to return it to its original state. This process should involve several vulnerabilities in various components of iOS: the WebKit web browser engine and the kernel itself. A classic case of a remote jailbreak is the newly discovered Trident exploit bundle. It used three types of vulnerabilities: the RCE vulnerability in the WebKit engine, the SFB vulnerability in the kernel to bypass the KASLR, and the LPE vulnerability in the kernel to raise its rights to root level.

Fig. Apple's bug bounty pricing.
As you can see, the main technical difference between the bug bounty programs of Apple and Zerodium is that the latter is interested in exploits for vulnerabilities, which have a more practical purpose. That is, we are talking about remote code execution, which may be interesting to Zerodium customers with whom it works. You do not need to be a great expert in noticing what is really the case with Zerodium, RCE + LPE exploits (i.e., bypassing the sandbox) are used in cyber attacks, including special services.
Unlike Apple, Google, Microsoft, and other vendors with bug bounty programs, Zerodium does not burden itself with ethical issues. The firm’s clients can also be intelligence services using advanced exploits for cyber attacks in the interests of their state. Such exploits have already been used more than once by such elite state-sponsored groups as the Equation Group (FiveEyes, Tilded Team) and Animal Farm (Snowglobe).

Fig. The stages of the submission of an exploit and the decision on the amount of payment in the case of Zerodium.
Bekrar also pointed out on his twitter that bug vendors are characterized by a “protracted” decision-making process about the posted demonstration of exploitation of a vulnerability. In contrast, Zerodium offers only a seven-day period from the submission of the exploit to the payment of remuneration.
The head of Zerodium itself had previously been involved in the well-known security firm VUPEN, which was developing its own exploits and searching for vulnerabilities to sell this information to its customers. After the adoption of the Wassenaar Agreement and the imposition of restrictions on trade in exploits, as well as “dual-use” technologies to other countries, it was announced that VUPEN would cease operations. After that, Bekrar founded Zerodium (USA), which also recruits security resellers in R & D.
Note that suspicions about the sale of exploits to special services that may be involved in state-sponsored cyber attacks against Zerodium or VUPEN are not fictitious . In particular, among the clients of VUPEN was the NSA (NSA), which is related to the grouping of the Equation Group. VUPEN collaborated with the Hacking Team, a large-scale compromise which occurred last year. Hacking Team worked with the state. agencies and private companies around the world, selling them information about exploits.
Source: https://habr.com/ru/post/311428/
All Articles