The results of the summer internship at Digital Security. Department of research

Our company at the end of April of this year announced an open internship in the three most technical departments: research, analysis of security and security of business systems. This experience was new to us, and I want to share it.
The issue of education in the field of information security is, in our opinion, very acute. Therefore, as part of our internship, we wanted not only to teach the children and show them something new and relevant from a technical point of view, but even to instill our technical view on research in the field of information security.
brief information
We are the research department ( Research Center ) of Digital Security. First of all, we deal with reverse engineering tasks, search for vulnerabilities in binary applications and writing exploits. If you like to sit in a disassembler or debugger, if you want to automate various tasks to search for vulnerabilities, if you like writing fuzzers, then you are close to us in spirit.
Introduction
We have received applications for internship from both students and those who are firmly on their feet, but want to “pump” their skills or try their strength in the field of information security. After all, after each noisy “hacking”, our sphere is becoming increasingly popular :)
')
Of course, we provided the opportunity to participate in the process remotely to those who could not visit our office, but those who could come to us personally benefited the most. And these guys have visited us quite often (we hope that this is in no way connected with quite frequent rains in St. Petersburg this summer, which prevented us from visiting beaches and other vacation spots on holidays).
We conducted small interviews with those who chose an internship at our office, and by the results made the final decision. Remote communication took place mainly through e-mail and, frankly, there were softer criteria, because they were evaluated by summaries and several issues related to the planned topics.
On the topics dwell in more detail. Before launching the internship program, we brainstormed within our department and generated topics that meet the following criteria:
- at the end of the internship, the children could publish the results of their research (github, gitlab and other repositories for open source projects) and / or speak to the public at a conference
- related to real-world practical tasks
According to the results of the answers to the questions, we offered the trainee a topic (or several), the most suitable for his skills and interests from the constantly updated list. In case the task was not satisfactory or someone asked to “read the entire list”, we went forward.
To be honest, most trainees expected jobs from us to look for “cool” vulnerabilities like Heartbleed, Ghost, etc. However, in order to find such errors, it is not enough to run any ready-made program, it is also necessary to understand the mechanics of its work. After all, over time, each distinguished researcher has his own set of software, both from ready-made, but “customized” tools for his tasks, and written personally. It is also important to recall that the study could be done immediately publicly (this was already decided by the interns themselves).
Within the framework of the program, several meetings were held. Some of them were based on old speeches, but updated to current realities or supplemented with a demonstration of non-public vulnerabilities;):
- “No Symbols = (” (Dmitry Evdokimov and Georgy Nosenko)
- "Light and Dark side of Code Instrumentation" (Dmitry Evdokimov)
- "Testing CAN network with help of CANToolz" (Alexey Sintsov)
- "The boot process in x86-compatible PC" (Alexander Ermolov)
- Mitapas from colleagues from the audit department
And in the middle of summer, the interns themselves had already conducted a similar mitap for us, presenting their results. At the end of each talk, my colleagues and other interns asked questions, thanks to this, other ways to solve the problem and new topics for future research appeared.
Some of the guys have not fully realized their plans, but this does not mean that they have failed. Just some of the topics were broader, and they wanted to implement additional tasks in them. We are pleased with the results and will work on the quality of the internship process. Some interns were offered to start working at our company now.
Supervised by interns:
- Dmitry Evdokimov d1g1
- Georgy Nosenko
- Yegor Litvinov Xarlan
- Boris Ryutin dukebarman
Questions for a mini-interview
- Why did you decide to train in DSec? What attracted you to the company?
- Did you like the internship? What is especially remembered? How much reality coincided with your expectations?
- Tell us about your task / tasks.
- Did the tasks you worked on during the internship seem interesting? Was there something you wanted to do, but failed?
- Are you ready to return to the company for an internship or a job?
Below are the answers of some interns.
Localhost trainees
Igor Kirillov (4th year student of St. Petersburg Polytechnic University)
Theme: “Explore the possibilities of the hexrays-tools plugin for the IDA Pro disassembler, port it for new versions of IDA Pro. Consider migrating a plugin from C ++ to IDAPython . ”
Interview:
- I like to understand the device of complex systems. And although programming is also interesting, I am more attracted to the internal processes taking place in the OS, the OS device. I think the best place for the development and application of my interests is the DSec research department. In addition, DSec is an international company, and in the field of information security in Russia, this title except Kaspersky Lab can boast.
- Liked. Most of all I remembered the interview. I was preparing to test my knowledge, but I obtained it through self-education, so it was difficult for me to assess the starting requirements. However, after the story about how I bypassed the protection of a toy that encrypts traffic and does not allow to modify the code, we immediately went on to discuss possible topics for internships and what should be studied for further development. It's great that there is an opportunity to show oneself in action, and not in some abstract conditions. He was set up that it would be difficult, and indeed, at first, when he began the task, he “sank” in chains of functions and structures. I looked at the code and tried to understand what it was doing. Climbed into the functions and definitions of the participating structures, understood that they also consist of something. And so on for recursion ...
IDA still has a peculiarity in the form of not-too-high-quality documentation, as well as in structures whose name says little. However, it took several days and all these tinfo_t, vdui_t, cvar.idati, etc. have become my best friends. - It was necessary to port the plugin-winner of the competition, organized by IDA developers. Well, think about transferring it to Python. The plugin was sharpened for version 6.3 (Hex-Rays 1.8) and when trying to compile for 6.6 it produced about 500 errors. Another 50 pieces ran into the transfer from 6.6 to 6.8. In general, it was possible to fix it in 2 weeks, but since the code was practically unreadable (some hardcoded function calls were worth something) and poorly expandable, I took up writing my version in Python, adding a few significant changes. At the moment, the plugin already has the following features:
- Allows interactive reconstruction of structures and classes, and also helps to understand the purpose of the fields.

- Creates a list of classes, allowing you to keep virtual functions in front of you, as well as centrally edit their names and signatures.
- At offsets pointing out of the structure, compiles a list of suitable extended structures and replaces the code with the CONTAINING_RECORD macro (The list can be made using any Type Library).
- Builds a nice graph from interconnected structures and allows you to navigate through it.

- Many other support features.
The plugin itself will be presented at the ZeroNights 2016 conference. - Allows interactive reconstruction of structures and classes, and also helps to understand the purpose of the fields.
- Since IDA is the main program for reverse engineering, and I want to know its capabilities well, I chose the task of fixing a useful C ++ plugin for fresh versions of IDA. And later I transferred it to Python, considerably improving it. The task was very fascinating and I had to restrain myself so as not to do it from morning to evening. I would like to search for vulnerabilities in real programs (especially in drivers and OOP code, where you can thoroughly test my plugin at the same time), but for now you need to "digest" a certain amount of literature and other information.
- Definitely - yes.
Mikhail Kolesov (6th year student at St. Petersburg Electrotechnical University "LETI")
Theme: "Development of a semantic search engine for ROP gadgets based on the Triton Framework."
Interview:
- I read the description of what the research department does. And I realized that it was just what I was interested in.
- Internship very much. Interesting tasks, cordial and responsive staff, a cozy office, new acquaintances, the 27th meeting of Defcon Russia , the cruiser Aurora outside the window. Super!
- As an internship assignment, I was offered a number of topics, of which the development of the engine for the semantic search for ROP gadgets based on the Triton Framework seemed to be the most interesting. In order to better understand the issues related to ROP operation, I began to study theoretical materials and relevant practical tasks. Incredibly useful were the materials that we constantly threw up the company's employees. Next, he began to analyze and study the source codes of programs designed to collect gadgets in executable files. The most interesting of them were ROPGadget and Ropper , implemented in Python. However, due to the fact that they did not provide detailed (necessary for us) information about gadgets, it was decided to write their own utility (GadgetFinder).
To do this, I needed to tighten my knowledge of the formats of executable files, get acquainted with Capstone Framework, think over the format of input / output data and write a few hundred lines of code. At the same time, together with the manager, we studied the materials on the Triton Framework, implemented small scripts in order to become better acquainted with its capabilities.
We also dealt with the use of SMT solvers in the field of information security and thought through the architecture of the future application (RopFinder). Currently, work is underway on RopFinder, namely:- implementation of simple semantic queries
(eax == ebx, [esi] == 0xdeadbeef) - thinking about the technology with which you can combine gadgets into ROP chains, based on the required restrictions.
Working with the Triton Framework via IDA Pro - implementation of simple semantic queries
- The solution of each of the proposed tasks is a tool that will facilitate the life of the researcher and increase productivity. So the tasks are not only interesting, but also relevant. Achieving goals on your own - great, but doubly cool - to carry out a comprehensive, comprehensive study of some voluminous software as part of a team of professionals. Therefore, I would like to participate in a real project, which is engaged in the research department. But, being an intern, this is hardly possible.
- Of course!
Evgeny Rasskazov (4th year student at Saint-Petersburg State University of Economics)

Topic: "Implementing the hardware and software for MITM attacks and fuzzing knx-tp"
Interview:
- I know about the company for a long time, because friends from the university have been training with you, some have remained to work. Positive feedback from friends who have fully justified themselves.
- Internship definitely liked. The interview will be remembered for a long time, on the good side, a very cool, friendly atmosphere. There were no expectations as such, everything went as it was, and I am very pleased with it.
- My internship task was the implementation of software and hardware for conducting MITM attacks and fuzzing KNX-TP. I started doing it by studying KNX. What is it? How does it work? What is the structure of packages running over the network? How can you interact with all this?

KNX-TP transceiver for RaspberryPi
Having studied the work of ETS5, I have assembled a KNX network and set up its work. Armed with an oscilloscope and a logic analyzer, I watched the operation of the KNX-TP network at a lower level. My next goal was to make a PCN project for a KNX transceiver based on the NCN5120 chip for the Raspberry PI. Altium Designer was chosen as CAD. Having dealt with AD and studied the work of the NCN5120, I began to design the board. In the process, there were various difficulties in working with AD, but the board was completed and sent to production. As a result, we received a board with two NCN5120, which allowed us to wedge into the disconnection of the communication line in the KNX-TP. Because of this, the possibility of implementing an MITM attack. The board connects to the Raspberry PI using SPI. In the course of in-depth study of the Raspberry PI, it turned out that the tool does not support SPI operation in the slave mode (probably not even it, but Linux itself does not support the SPI slave, although it can also be noted that the processor on the Raspberry PI can only make a slave on 1 of 2 SPI, which also does not suit us very much), and the NCN5120 only works in master mode. It was decided to write a software implementation of the SPI slave. After trying to work with Python, it was decided to implement everything on clean C. Unfortunately, the supply of components was delayed and the working board was not fully assembled. As a result, testing the operation of the software SPI slave along with the board also failed.
- Yes, the tasks were interesting, periodically changed and corrected. I think you can always find something that I would like to work out more. In my case, it turned out that I was thinking about the reverse of programs, and as a result I studied the manuals for chips and was engaged in the development of a printed circuit board. Although I liked it a lot more.
- As an intern, no more than yes. And as an employee - with pleasure.
Evgeny Minibaev (4th year student at Innopolis University, l4l )

Topic: “ Understand the Joern / Bjoern utilities and compose queries according to their rules for finding vulnerabilities of various types. For a start on the example of those already found earlier. ”
Interview:
- DSec is one of the few companies I know that deals with an area that is interesting to me; in addition, quite often saw high-quality publications from the company on Habrahabr. Partly, the advantage is that the office is located in St. Petersburg, and I am madly in love with this city.
- Yes, I really liked the internship :) Not only did I get a lot of new knowledge (sometimes from completely unexpected areas), but it all took place in a friendly atmosphere. Most of all, the presentations of the interns' successes probably remembered when something that I didn’t even test earned from me. A small recommendation for the future: it is worth combining the presentations of related departments, so that everyone can once again meet and talk.
- As part of the summer internship, I was tasked with exploring the capabilities of joern and bjoern static analyzers to find vulnerabilities in applications. In the process of work I got acquainted with the internal device of these tools, and also in practice I studied the peculiarities of the language of search queries. The existing requests were analyzed and verified to search for vulnerabilities of the following classes: Integer Overflow, Buffer Overflow. In addition, I developed and tested my own queries.

Graph representation of the vulnerable function in Linux 3.1
During the internship process, documentation was created on the installation, configuration and operation of these tools. As a result, an idea was obtained about modern methodologies for finding vulnerabilities in software products, as well as experience in using static analysis tools. In addition, it was possible to master the scientific basis of the listed static analyzers (the basics of the compilers, the intermediate presentation of the source code, graph models, etc.).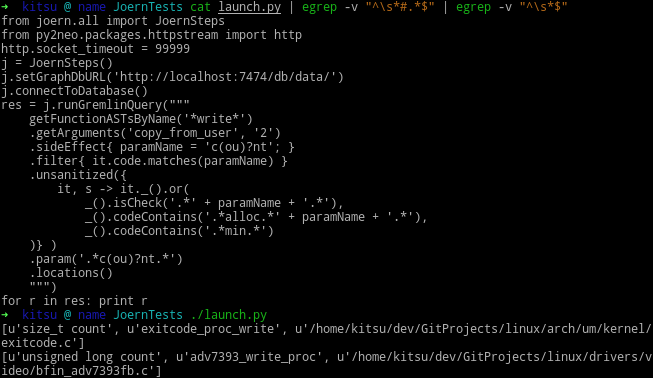
Vulnerability Search CVE-2013-4512
In addition to the main topic of the practice, reports were closely listened directly to the activities of the information security analyst (binary code instrumentation, techniques for efficiently working with executable files without symbolic information, analysis of CAN bus security in cars). - The tasks were cool and unusual, and in a good way. I liked it very much that we [the interns] were not piled up with some kind of monstrous enterprise product of hundreds of megabytes and were not instructed to deal with it, but gave interesting and quite relevant projects from open source, which we would hardly have analyzed without these tasks. On the other hand, I personally lacked more reverse, because I really wanted to dig into some kind of exotic firmware and everything like that.
- Of course, ready to return! I even left a pass: D
Remote trainees
The following guys were engaged, in fact, one topic. They needed to understand the TMS 320LF2407 architecture and implement its support in popular tools for Reverse Engineering. One trainee was focused on the IDA Pro design tool that was mentioned more than once before, and the second one chose the Radare2 open source framework.

Source: www.ti.com/product/TMS320LF2407
Anton Boyarkin
Theme: “Add support for TMS 320LF2407 microcontroller architecture in IDA Pro (Python processor module)”
Interview:
- On the forum reverse4you.org the topic of the internship flashed, I decided to try my hand. The company holds a classy ZeroNights conference.
- From the internship remember the microcontroller TMS320LS2407 and tons of technical documentation. Since the topics could be chosen, the expectations coincided.
- The TMS320LF2407 is a Texas Instruments digital signal processor that is used very often. The task is to add support for the microcontroller architecture in IDA Pro and radare2 in order to disassemble the firmware for an electric meter equipped with PLC modems and designed for organizing data acquisition networks. The microcontroller also performs a network search for electricity meters, routing information packets, storing and transmitting data through a selected communication channel to the central control center. Having written the processor module, we can understand the logic of the microcontroller, try to identify weak points.
- The task is interesting, but at the moment has not yet been solved.
- Ready
Alexander Pykhov
Theme: “Add TMS 320LF2407 Microcontroller Architecture Support to the Radare2 Framework”
Interview:
- Best IT security company in Russia. It is always a pleasure to work with professionals.
- Internship very much. It was a nice personal acquaintance. Coincided completely.
- The task was to study and analyze the firmware under the MC TMS 320LF2407. As a first step, it was decided to integrate this MC into Radare 2. For this, the documentation on the processor was studied, trying to find a native compiler and / or toolchain to work with this processor. According to the documentation, assembler instructions were restored and tests were performed on the received firmware. At the moment, the module is being debugged and tested.
- The task turned out to be interesting, but difficult to implement. I would like to do more directly by reverse and analysis :)
- Yes with pleasure.
Conclusion
For our department, this was the first such large-scale internship. We have improved a lot in the process. But we are very glad how everything as a result passed, that the guys themselves are satisfied. We plan to continue this practice in the future.
Source: https://habr.com/ru/post/311374/
All Articles