The free data of North Korea’s national DNS leaked to free access.
Access to the Internet in North Korea has only government officials and some government organizations. As of the end of 2015, the number of active IP addresses that have access to the global network does not exceed 1,500. This is despite the fact that the number of the country's population in 2013 exceeded 25 million. The only available source of information other than the media is the Gwangmyeong national information network.

The Kwangmyeong People’s Network was launched in 2000 and is a kind of Internet emulation within a particular state. As of the end of 2015, there were about 5 thousand sites on the Gwangmyeon network, and its full audience was about 100 thousand people.
Today, September 20, 2016, by a strange coincidence, the zone of one of the national servers of North Korea has become available for transmission to the whole world.
As a result, in order to read previously closed information from the national Korean top-level domain server, it is enough to execute an AXFR request to the name server ns2.kptc.kp.
')
A corresponding project was created on GitHub - TL; DR Project. Every 2 hours, information from the Korean server is read and written to the repository.
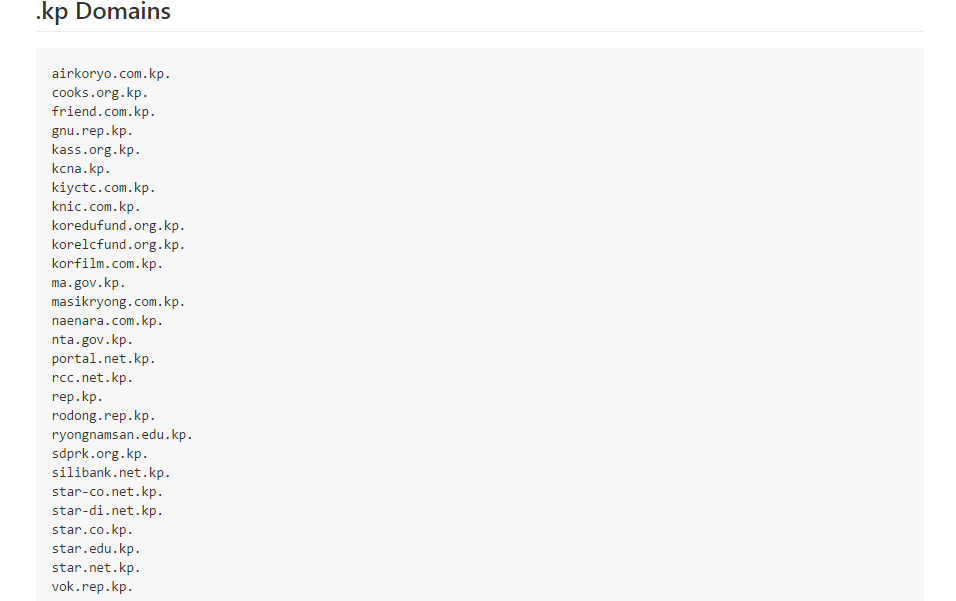
Previously, we had a bad idea even of the approximate structure of the Korean DNS. And now it became known what resources are visited by the few people in Korea who have access to the Internet.
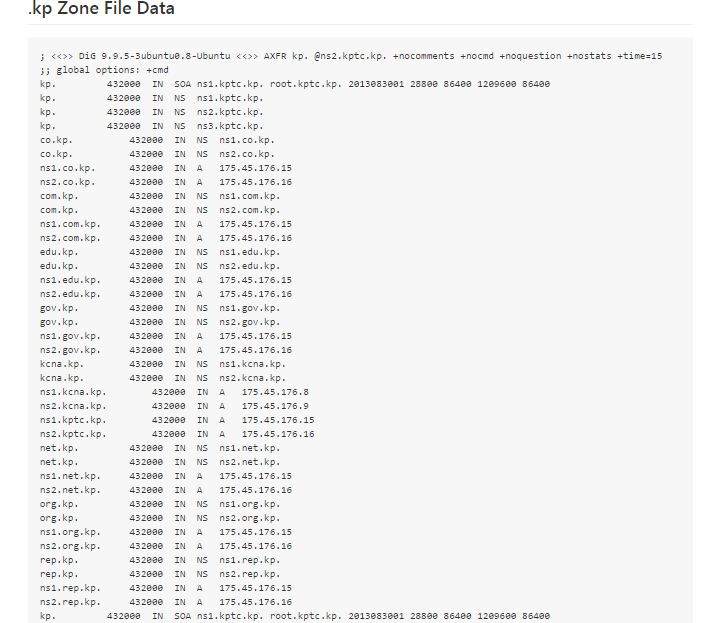
It turned out that the Korean Internet consists of several dozen domains and 5 name servers.
Information contained in a DNS zone can be considered confidential from an operational security point of view. For example, resource records may contain server role information or SSH key fingerprints (RFC 4255).
Individual domains immediately attracted the attention of specialists, for example gnu.rep.kp.

The Kwangmyeong People’s Network was launched in 2000 and is a kind of Internet emulation within a particular state. As of the end of 2015, there were about 5 thousand sites on the Gwangmyeon network, and its full audience was about 100 thousand people.
Today, September 20, 2016, by a strange coincidence, the zone of one of the national servers of North Korea has become available for transmission to the whole world.
As a result, in order to read previously closed information from the national Korean top-level domain server, it is enough to execute an AXFR request to the name server ns2.kptc.kp.
')
dig AXFR kp. @ns2.kptc.kp A corresponding project was created on GitHub - TL; DR Project. Every 2 hours, information from the Korean server is read and written to the repository.

Previously, we had a bad idea even of the approximate structure of the Korean DNS. And now it became known what resources are visited by the few people in Korea who have access to the Internet.

It turned out that the Korean Internet consists of several dozen domains and 5 name servers.
Information contained in a DNS zone can be considered confidential from an operational security point of view. For example, resource records may contain server role information or SSH key fingerprints (RFC 4255).
Individual domains immediately attracted the attention of specialists, for example gnu.rep.kp.
Source: https://habr.com/ru/post/310550/
All Articles