CCTV vulnerabilities allow hackers to create large-scale botnets

According to the US-CERT statement , the AVer Information EH6108H + has revealed serious vulnerabilities in the firmware of digital video surveillance devices (DVR) AVer Information that allow attackers to easily access them remotely and even create botnets.
Vulnerabilities
Security researchers were able to detect three critical vulnerabilities. The first one (CVE-2016-6535) consists of two hidden accounts for remote connection. Each of them has root-rights, passwords for access are registered in the firmware code - as a result, accounts cannot be disabled or deleted from the system. As a result, an attacker who knows the IP of a particular camera can easily connect to it via Telnet.
')

AVer Information EH6108H + hybrid DVR
In addition, attackers can gain access to the administrative panel and without administrator passwords due to an error in the authentication system (CVE-2016-6536). In order to gain access to the control panel, the hacker simply needs to go to the [IP devices] / setup address and select the “handle” parameter - after that the administrative page will open without entering a password. Having access to it, an attacker can change device parameters and even change passwords for all users of the system.
The third vulnerability (CVE-2016-6537) leads to the disclosure of confidential information - a problem arises due to an error in the mechanism for processing user credentials.
How to protect
According to the US-CERT statement, there are currently no patches to fix the vulnerabilities found. The manufacturer AVer firmware on its website describes it as “no longer supported” (discontinued).
The only effective way to prevent an attack using these holes is to limit access to devices — using a firewall or network equipment settings.
Extent of the problem
The presence of easy-to-use vulnerabilities and “backdoors” in DVR devices is far from news. Previously, experts from Positive Technologies found critical vulnerabilities and so-called “master passwords”, which allow attackers to easily gain access to such devices, hundreds of thousands of which are accessible from the Internet. For example, problems were found in Samsung video surveillance systems , as well as the popular DVR firmware used by many vendors.
In addition, more recently it became known that over 1 million DVR devices had been infected by the BASHLITE worm - the attackers had created botnets for them to conduct DDoS attacks.
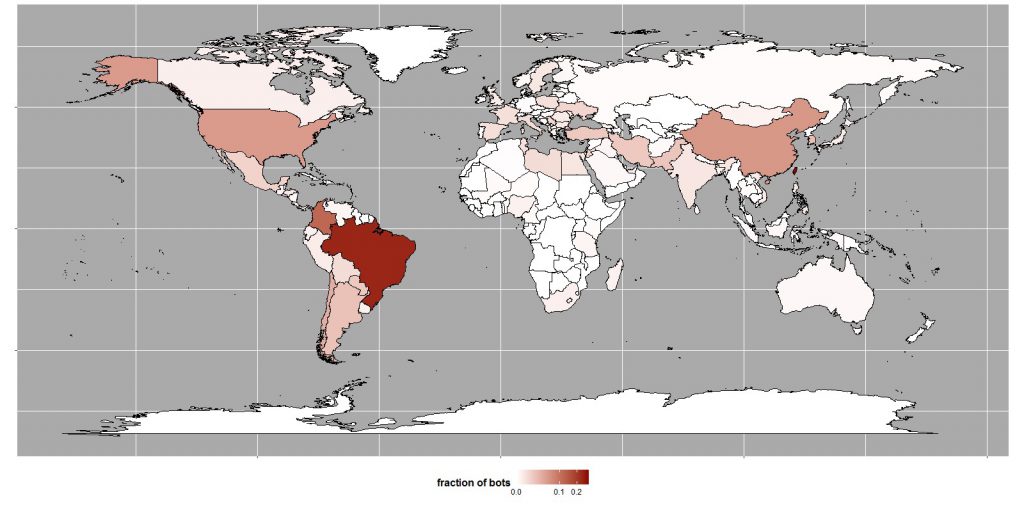
Geographical distribution of attacks
Also earlier this year, researchers at Sucuri discovered a botnet of 25,000 Internet-connected video surveillance devices. In addition, a botnet for DDoS attacks consisting of infected webcams was found by experts from Arbor's Security Engineering and Response Team (ASERT).
It is important to understand that attackers often do not need to make special efforts to detect security gaps in video surveillance systems, because, as a rule, their vulnerabilities are extremely primitive.
The situation is aggravated by the fact that manufacturers of DVR-systems often do not themselves completely create firmware for their devices, but use third-party developments. Such firmware can be distributed in various dubious ways, potentially, they may contain hidden undocumented logic, about which the manufacturers of the final DVR may be completely unaware.
For example, vulnerabilities discovered by our experts were present in the popular firmware that was used and supplemented in its own way by many DVR manufacturers. Accordingly, vulnerabilities in these firmware threatened many different devices from different manufacturers at once.
However, many manufacturers do not pay enough attention to the release of updates and the development of mechanisms for their centralized deployment to end devices or to notify users. In the case of using third-party firmware, the repair process becomes even more complicated: in such cases, the DVR manufacturer may not fully control the firmware - and not be able to change it.
For example, with one of the manufacturers of such a popular and vulnerable firmware, we were never able to establish contact so that they could fix the problems found. More information was presented in a report during the Forum Positive Hack Days III:
Vulnerabilities and hacking of DVR-devices are a serious threat to private companies. Having gained access to video surveillance systems, an attacker can use them as a springboard for further unnoticed attacks within the company's network (APT). Typical remedies that are used in companies often cannot detect such penetration (for example, the classical antivirus approach is powerless here).
In fact, a malicious minicomputer device appears in the corporate network, within which an attacker can install his software. The backdoor in such devices can exist for a very long time and imperceptibly.
What to do
In order to defend themselves, Positive Technologies experts advise isolating access to digital video surveillance systems from the Internet (for example, settings of a router and / or a firewall). It is desirable for devices from the internal network to also restrict access to the DVR and give access only to those addresses that need it (for example, only administrators). And it is similar to restrict access to the network of the DVR itself, giving it access only to the necessary addresses. It is best to place such devices in a separate isolated network.
In general, with the development of the “Internet of Things”, the possibilities for creating such botnets increase significantly: many new gadgets are being developed and released to the market without any regard for security (even the opposite: Internet connection schemes are simplified as much as possible). In this situation, it is possible to advise both individuals and companies to be more discriminating in the purchase of equipment and, if possible, to analyze the security of new devices.
The detection of botnets and the investigation of incidents are also complicated in a situation where the infected are not personal computers, but many automatic systems that nobody specifically follows the behavior of.
You can listen to how to detect compromised assets, assess the capabilities of attackers and respond to security incidents in corporate networks on September 22 at 14:00 on Vladimir Kropotov's free webinar “Incident Response”.
»To participate you must register: www.ptsecurity.ru/research/webinar/106986
Source: https://habr.com/ru/post/310548/
All Articles